June 2014 Virus Activity Overview
Virus reviews | Hot news | All the news | Virus alerts
July 2, 2014
Viruses
According to statistics collected via Dr.Web CureIt!, Trojan.BPlug.78—a malicious browser plugin that displays annoying ads—was the malware most frequently detected on home PCs. Trojan.Packed.242524, which installs unwanted applications in infected systems, ranked second, while another adware plugin—Trojan.Bplug.48—ranked third. The top twenty most common malicious programs discovered on PCs by Dr.Web CureIt! in June 2014 are listed in the table below:
| Name | Qty | % |
|---|---|---|
| Trojan.BPlug.78 | 85615 | 1.90 |
| Trojan.Packed.24524 | 74869 | 1.66 |
| Trojan.BPlug.48 | 57420 | 1.27 |
| Trojan.BPlug.47 | 49008 | 1.09 |
| Trojan.BPlug.79 | 38406 | 0.85 |
| Trojan.BPlug.28 | 37948 | 0.84 |
| Trojan.MulDrop5.10078 | 36346 | 0.81 |
| Trojan.PWS.Panda.5661 | 33575 | 0.75 |
| Trojan.InstallMonster.209 | 26212 | 0.58 |
| Trojan.BPlug.91 | 25809 | 0.57 |
| Trojan.Admess.4 | 24910 | 0.55 |
| Trojan.BPlug.46 | 22764 | 0.51 |
| Trojan.DownLoader11.3101 | 22438 | 0.50 |
| Trojan.Click3.8365 | 22308 | 0.50 |
| Trojan.LoadMoney.262 | 20117 | 0.45 |
| Trojan.InstallMonster.51 | 17468 | 0.39 |
| Trojan.Popupads.15 | 16734 | 0.37 |
| 14310 | 0.32 | |
| Trojan.BPlug.61 | 13758 | 0.31 |
| Trojan.Zadved.5 | 13575 | 0.30 |
Botnets
The botnet consisting of computers compromised by the file infector Win32.Rmnet.12 is still active. As in the last month, the first of two Win32.Rmnet.12 subnets being monitored by Doctor Web's virus analysts experienced a daily average of 165,500 connections being made to it by infected computers. A diagram of that subnet’s activity is presented below:
Win32.Rmnet.12 botnet activity in June 2014
(1st subnet)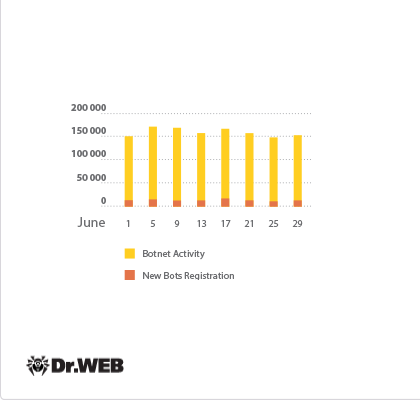
In the second subnet, on average 270,000 bots were operating daily which is a bit more than in the previous month.
The botnet comprised of machines infected with Trojan.Rmnet.19 is also still operational. The diagram below shows the average daily number of PCs (infected with this malware) that communicated with a command and control (C&C) server over the course of the month.
Average daily activity of the Trojan.Rmnet.19 botnet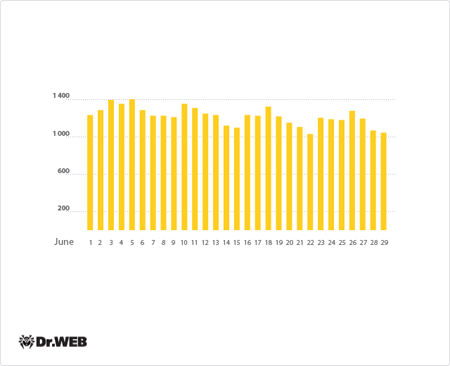
The largest botnet to date, which encompasses machines running Mac OS X that are infected with BackDoor.Flashback.39, is also still in operation. In June, the average number of infected Macs decreased by about 1,000 and totalled 14,216. The botnet’s activity is presented in the following diagram:
Average daily activity of the Backdoor.Flashback.39 botnet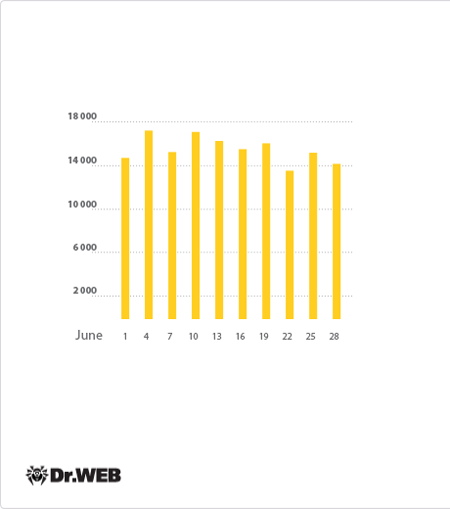
Doctor Web's security researchers continue to monitor the large botnet created by criminals using the file infector Win32.Sector. This program downloads various malicious programs via P2P networks and launches them on infected computers. By no means over the past month did this botnet’s activity decline; nor did the file infector's rate of spread. Below you can find a graph illustrating the activity of the Win32.Sector botnet in June 2014:
Average daily activity in the Win32.Sector botnet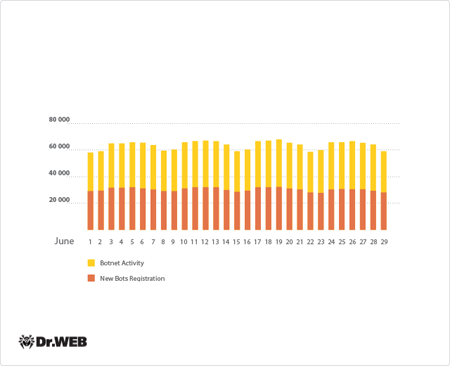
Other June threats
Doctor Web’s security researchers are discovering increasingly more malicious programs for Linux. For example, in June, the entry for Trojan Linux.BackDoor.Gates.5 , which is designed to mount DDoS attacks and perform classic backdoor functions, was added to the Dr.Web virus database. This Trojan targets 32-bit Linux distributions. It collects information about infected computers and sends it to criminals. Such information includes the number of CPU cores and the processor’s clock frequency, operational parameters, memory size, network interface data, and the MAC addresses of network devices, etc. This malicious program runs on infected computers as a daemon. It establishes a connection to a C&C server to receive instructions. When commanded by criminals, the program can update itself, start and stop a DDoS attack on a remote node with a specified IP address and port, or establish a connection and execute commands from another remote node at a specified IP address. More details about Linux.BackDoor.Gates.5’s architecture and principles of operation can be found in a corresponding Doctor Web review.
Another malware program studied by Doctor Web's security researchers at the beginning of June was given the name BackDoor.Zetbo.1. And, judging by some of its features, it has been devised by Turkish virus writers. The main objective of this malicious program is to execute various C&C server commands on an infected machine. The server address is hardcoded in the bot's body, and the instructions the Trojan carries out include updating and deleting files, searching for its own components on the hard drive and shutting down the system. This Trojan can transmit a variety of information about an infected machine to attackers. As a backdoor, it uses quite an unusual technique to acquire instructions from the server: BackDoor.Zetbo.1 searches the server for a special web page featuring several buttons, and by analysing the buttons' HTML code, the Trojan acquires the operational parameters needed in order for it to do its work.
More detailed information about this threat is presented in informational material posted in the news section of Doctor Web's site.
In the second half of June, Doctor Web's virus experts finished studying the multi-component Trojan.Tofsee and discovered that its payload incorporates a rather peculiar feature. Trojan.Tofsee’s main objective is to send spam, but in addition, it can perform other tasks such as protecting an infected computer from other malicious software. One of this Trojan’s modules enables it to search through files on the disk and running Windows processes, and remove certain objects it finds. Thus, Trojan.Tofsee rids an infected machine of its "competitors".
This malware spreads in several different ways, such as with removable storage media, as well as via Twitter, Facebook, and VKontakte, and through Skype. Trojan.Tofsee informs potential victims that shocking content related to them has been found in the public domain and that to view the material, they must install a special plugin. This threat reaches computers under the guise of this application.
Trojan.Tofsee also has other unusual features such as the ability to generate messages for a subsequent mass mailing using a special macro language, which is very rare in the world of malware. Detailed information about this Trojan’s architecture and principles of operation can be found in one of our reviews.
Malicious mailings
In the second half of June, intruders were significantly more active distributing malware via mass spam mailings. On June 27, virus writers dispatched a mass spam mailing on behalf of Amazon.
The emails included an attached ZIP archive containing the Trojan downloader known as BackDoor.Tishop.122. This program can download other malicious applications from the attacker's servers and install them on an infected computer. We described this incident in detail in one of our news posts. Doctor Web urges users to be vigilant and refrain from opening email attachments from unknown senders.
Threats to Android
One of the main mobile security events of recent weeks was the emergence of various lockers and Trojans encoders of the Android.Locker family. The first samples of these malicious applications were documented by Doctor Web in May with the discovery of Android.Locker.1.Origin and the extremely dangerous Android.Locker.2.Origin. When launched on an infected device, the latter would search the memory card for file names containing the extensions .jpeg, .jpg, .png, .bmp, .gif, .pdf, .doc, .docx, .txt, .avi, .mkv, and .3gp, encrypt the files, and lock the screen before displaying a ransom demand for their decryption.
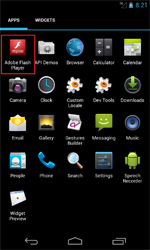
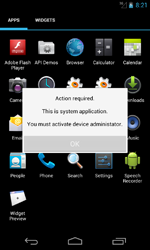
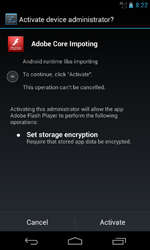
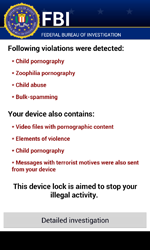
However, it was namely during the first month of summer that Android.Locker programs started appearing en masse. In June, Doctor Web's security researchers discovered as many as five malicious applications locking the operation of mobile devices and, in many cases, demanding a ransom to restore handhelds to their normal state of operation. For example, Android.Locker.6.origin and Android.Locker.7.origin, which are targeted toward mobile devices in the U.S., were distributed under the guise of Adobe Flash Player. When launched, they would lock mobile device screens, claiming that illegal content had been found and that $200 was required for unlocking services.
 |
 |
 |
In addition, these Trojans would steal data from the phone's address book (including contact names, phone numbers and email addresses), track incoming and outgoing calls, and, if necessary, lock them. Furthermore, during their installation Android.Locker.6.origin and Android.Locker.7.origin would check whether the following applications belonging to various credit and financial institutions were present on the infected device.
- com.usaa.mobile.android.usaa;
- com.citi.citimobile;
- com.americanexpress.android.acctsvcs.us;
- com.wf.wellsfargomobile;
- com.tablet.bofa;
- com.infonow.bofa;
- com.tdbank;
- com.chase.sig.android;
- com.bbt.androidapp.activity;
- com.regions.mobbanking.
All the information collected, including phone call data and the available programs discovered, was transmitted to the C&C server.
 |
 |
 |
 |
Another Trojan added to the virus database as Android.Locker.5.origin targeted devices in China. After its launch, it would lock the mobile device and inform the user that the phone needed to “get some rest”. At the bottom of the screen it displayed a 24-hour countdown clock. When time was up, the device would be unlocked automatically. Thus, unlike most currently known Android lockers, Android.Locker.5.origin does not demand any payment to return infected smartphones or tablets to normal operation, but has apparently been created as a joke. Nevertheless, the Trojan doesn't allow device owners to use their handhelds properly, and in some cases, users may pay dearly for that.
The observed trend showing a growing number of different Android lockers and ransomware and the already noticeably wide geography of their targets leads us to conclude that this trend is very likely to persist. Users who do not use modern anti-virus software for mobile devices risk encountering not only relatively harmless locking, but also something that can be far more dangerous—and that is losing important data and money.
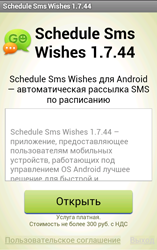
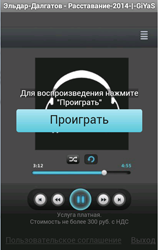
June also saw a significantly increased number of incidents involving Android devices becoming infected with Android.SmsBot.120.origin which can receive various commands from intruders and perform various actions, such as sending, intercepting and deleting SMS messages, acquiring current device coordinates, going to specified web addresses, removing certain applications, etc. Distributed under the guise of legitimate programs, the Trojan has been found on a large number of mobile devices during the past month, which indicates that its authors are seriously interested in the distribution of this Android threat.
 |
 |
Cybercriminals targeting South Korea were as energetic as ever in June. Doctor Web's security researchers registered more than 140 incidents of unsolicited SMS messages containing download links for a malicious Android program. Criminals worked most actively to spread the following Trojans: Android.MulDrop.20.origin (33.10%), Android.MulDrop.21.origin (21.13%), Android.Spy.40.origin (11.27%), Android.Spy.64.origin (9.15%), Android.SmsSpy.78.origin (4.23%), as well as Android.SmsBot.121.origin, Android.SmsSpy.71.origin, Android.Banker.27.origin and Android.MulDrop.14.origin, which accounted for 3.52% of all the discovered incidents.
Malicious files detected in mail traffic in June
| 01.06.2014 00:00 - 30.06.2014 23:00 | ||
| 1 | Trojan.Swrort.1 | 1.47% |
| 2 | Trojan.Hottrend.366 | 1.09% |
| 3 | Trojan.Fraudster.778 | 1.07% |
| 4 | Trojan.PWS.Panda.655 | 0.93% |
| 5 | Trojan.Hottrend | 0.90% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.62% |
| 7 | Trojan.PWS.Papras.295 | 0.62% |
| 8 | BackDoor.Andromeda.22 | 0.62% |
| 9 | BackDoor.Comet.963 | 0.55% |
| 10 | Trojan.PWS.Panda.4795 | 0.55% |
| 11 | BackDoor.Bladabindi.884 | 0.52% |
| 12 | BackDoor.Tishop.122 | 0.52% |
| 13 | SCRIPT.Virus | 0.50% |
| 14 | Trojan.PWS.Siggen.28421 | 0.50% |
| 15 | Java.Adwind.3 | 0.47% |
| 16 | Win32.HLLM.MyDoom.33808 | 0.47% |
| 17 | Trojan.PWS.Multi.911 | 0.45% |
| 18 | Trojan.PWS.Panda.7278 | 0.40% |
| 19 | BackDoor.Comet.884 | 0.38% |
| 20 | BackDoor.Siggen.57639 | 0.38% |
Malicious files detected on user computers in June
| 01.06.2014 00:00 - 30.06.2014 23:00 | ||
| 1 | SCRIPT.Virus | 1.35% |
| 2 | Trojan.InstallMonster.209 | 0.67% |
| 3 | Trojan.Packed.24524 | 0.53% |
| 4 | Trojan.LoadMoney.263 | 0.53% |
| 5 | Trojan.MulDrop5.10078 | 0.45% |
| 6 | Adware.Downware.2095 | 0.42% |
| 7 | Adware.OpenCandy.4 | 0.39% |
| 8 | Adware.Downware.179 | 0.38% |
| 9 | Trojan.Siggen6.19796 | 0.35% |
| 10 | Trojan.LoadMoney.262 | 0.35% |
| 11 | Tool.Unwanted.JS.SMSFraud.26 | 0.35% |
| 12 | BackDoor.IRC.NgrBot.42 | 0.34% |
| 13 | Adware.NextLive.2 | 0.34% |
| 14 | Adware.OpenCandy.3 | 0.34% |
| 15 | Tool.Skymonk.14 | 0.33% |
| 16 | BackDoor.Infector.133 | 0.33% |
| 17 | Adware.Toolbar.240 | 0.32% |
| 18 | Exploit.SWF.296 | 0.30% |
| 19 | Trojan.InstallMonster.146 | 0.30% |
| 20 | Exploit.SWF.295 | 0.29% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live