Mobile threats in June 2014
Virus reviews | Hot news | Threats to mobile devices | All the news | Virus alerts
July 2, 2014
According to Doctor Web statistics collected via Dr.Web for Android, in June 2014 the anti-virus registered 6,101,306 positives. As before, various advertising modules, used by developers to generate a profit from free applications, became the main cause for concern. These modules can display annoying notifications on the Android notification bar. Such messages often include advertisements for questionable and potentially dangerous websites. June 26 was the most “peaceful day” with only 163,580 threats discovered, while June 8 saw the greatest number of positives registered—226,002.
Traditionally, the number of malicious programs within the total number of advertising and potentially dangerous applications detected was relatively small and rarely exceeded 4%-5%, but in June the situation changed dramatically. Android.SmsBot.120.origin broke into the lead in terms of the number of infections attempted. It was disarmed by Dr.Web over 670,000 times, a figure that accounts for almost 11% of the total volume of identified threats. In addition to sending SMS messages to specified numbers, this malware can transmit information about infected devices (including IMEIs, lists of installed programs, etc.) to servers belonging to cyber criminals, remove installed programs and incoming SMS messages, and display notifications.
 |
 |
 |
|
Once this Trojan was detected, 514,893 users immediately removed it, a figure constituting 76.80% of the total number of incidents. In 13.88% of the cases (93,036 times) the threat was removed before the malware was installed on the device; the Trojan was moved to the quarantine 34,162 times (5.10% of the incidents), and 17,672 users (2.64%) ignored the Dr.Web warning, allowing the Trojan to run on their handhelds.
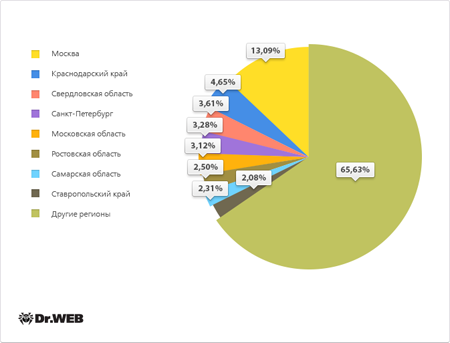
Android.SmsBot.120.origin was most frequently detected in Russia. The figure below illustrates the geographical distribution of this threat.
Android.SmsSend.1215.origin and Android.SmsSend.859.origin rank second and third respectively by number of detections. The ten threats most frequently found on mobile devices by Dr.Web in June are presented in the table below.
| Threat name | %% | |
|---|---|---|
| 1 | Android.SmsBot.120.origin | 10,99 |
| 2 | Android.SmsSend.1215.origin | 1,43 |
| 3 | Android.SmsSend.859.origin | 1,35 |
| 4 | Android.SmsSend.1081.origin | 1,08 |
| 5 | Android.Spy.83.origin | 0,82 |
| 6 | Android.SmsSend.991.origin | 0,68 |
| 7 | Android.SmsSend.914.origin | 0,62 |
| 8 | Android.SmsSend.309.origin | 0,59 |
| 9 | Android.Subser.1.origin | 0,54 |
| 10 | Android.SmsSend.315.origin | 0,52 |
In late May, Doctor Web's security researchers registered incidents involving the first-ever encryption Trojan for Android. Android.Locker.2.origin would search infected devices for files containing the extensions .jpeg, .jpg, .png, .bmp, .gif, .pdf, .doc, .docx, .txt, .avi, .mkv, and .3gp, encrypt them, and then demand a ransom for their decryption. During June Dr.Web for Android prevented 6,858 attempts to infect devices with this dangerous Trojan.
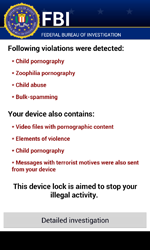
June will also be remembered for the intense distribution of Android blocker Trojans which interfere with the normal operation of infected devices. For instance, Android.Locker.5.origin primarily targets devices in China and locks the smart phone or tablet screen only temporarily, without inflicting severe damage to the information stored on the device. Yet the Trojans Android.Locker.6 .origin and Android.Locker.7.origin lock the touch screen and demand that the victim pay ransom to unlock it. These programs are distributed under the guise of the Adobe Flash Player and target Android handhelds in the U.S.
 |
 |
 |
 |
Learn more about these threats and ways to neutralise them in the informational material published on our website. Doctor Web urges users to be vigilant, to install applications only from trusted sources, and to use anti-virus software on their devices.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live