The seasonal trend — blockers and encoders for Android
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
June 20, 2014
Android.Locker.2.origin became the first representative of this class of threats. According to Doctor Web's statistics, since May 22, 2014, when the corresponding definition was added into the virus database, Dr.Web for Android has prevented over 21,276 infection incidents involving Android.Locker.2.origin. Android.Locker.2.origin poses severe danger to Android smart phones and tablets that are not protected by anti-virus software. On an infected mobile device, the Trojan searches available memory cards for files with the following extensions: .jpeg, .jpg, .png, .bmp, .gif, .pdf, .doc, .docx, .txt, .avi, .mkv, and .3gp. It encrypts the files and adds the extension .enc to the filenames. Then the device's screen is locked and displays a ransom demand for the decryption of the files.
Photos, videos and documents stored on memory cards can be compromised by this malicious program. In addition, the encoder steals and transmits to the intruders’ server various information about the infected device (including, for example, its IMEI). The encoder uses AES encryption and connects over the TOR network to its command and control (C&C) server which is run by a .onion host. This allows the attackers to maintain a high level of secrecy.
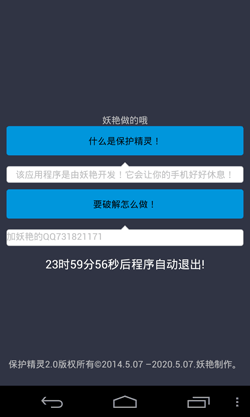
Unlike many other similar programs, Android.Locker.5.origin primarily targets devices in . There are some indications that the virus writers have not developed it for illicit profit but rather just for laughs, wanting to make fun of careless users. After its launch, Android.Locker.5.origin locks the mobile device and displays the following message:
The text says that the application will block the phone to let it "rest a little". At the bottom of the window the program displays a 24-hour countdown timer—once time is up, the mobile device will automatically be unlocked. Android.Locker.5.origin uses system functions to check the status of its process and automatically restarts the process if it has stopped. It also prevents attempts to launch other applications on the device, which greatly complicates its removal. Otherwise Android.Locker.5.origin does not have any dangerous malicious features that would enable it to encrypt files on an infected tablet or smart phone.
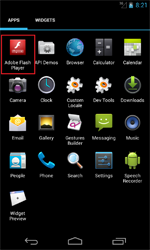
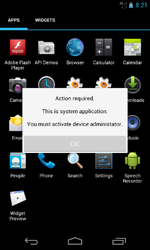
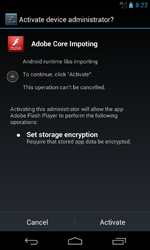
In June, this family of ransomware for Android was joined by Android.Locker.6.origin and Android.Locker.7.origin, programs geared toward mobile devices in the that lock the screen and demand a ransom from the victim to unlock it. These programs are distributed under the guise of the Adobe Flash Player and during installation demand that users grant the application administrator privileges.
 |
 |
 |
Then the Trojan pretends to scan the device and blocks the screen on which it subsequently displays a message about the discovery of allegedly unlawful content.
 |
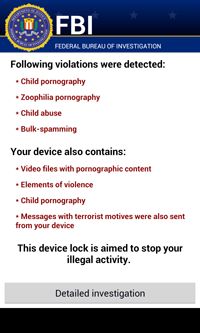 |
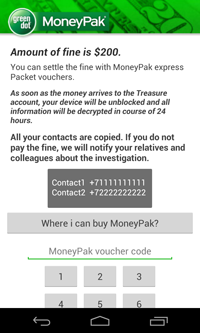
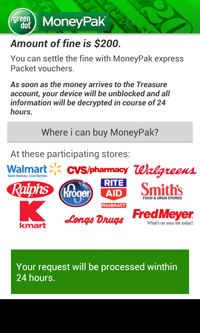
To unlock the phone, the malware demands 200 dollars to be paid via MoneyPack.
 |
 |
During their installation, Android.Locker.6.origin and Android.Locker.7.origin check whether the following applications are installed on the infected device:
- com.usaa.mobile.android.usaa;
- com.citi.citimobile;
- com.americanexpress.android.acctsvcs.us;
- com.wf.wellsfargomobile;
- com.tablet.bofa;
- com.infonow.bofa;
- com.tdbank;
- com.chase.sig.android;
- com.bbt.androidapp.activity;
- com.regions.mobbanking.
If they are present, the Trojan reports back to the attackers' server. Android.Locker.6.origin and Android.Locker.7.origin also steal information from the infected device’s phone book (contact names, phone numbers and email addresses). They monitor incoming and outgoing communications and can bar those communications if desired. All the information collected, including phone call data, is also transmitted to the C&C server.
Dr.Web for Android detects and removes Android.Locker.2.origin, Android.Locker.5.origin, Android.Locker.6 .origin and Android.Locker.7.origin, whenever they try to penetrate a protected device. Doctor Web once again reminds users that using a modern, reliable anti-virus is the surest way to prevent any of these dangerous Trojans from causing an infection.
Use Data Loss Prevention to protect your files from encryption ransomware
| Only available in Dr.Web Security Space 9 and 10 |
| More about encryption ransomware |  |
What should I do if… |
 |
Configuration presentations tutorial |  |
Free decryption |