Linux.BackDoor.Gates.5 — yet another Linux Trojan
Real-time threat news | Hot news | All the news | Virus alerts
June 5, 2014
Linux.BackDoor.Gates programs incorporate backdoor features and can also be employed to attacks. In this review, we would like to talk at length about one of the family members, Linux.BackDoor.Gates.5. This program targets 32-bit Linux distributions, and some of its properties allow us to conclude that the malware has been designed by the same criminals who crafted Linux.DnsAmp and Linux.DDos. The malware consists of two modules: the principal module performs backdoor tasks and can execute commands received from criminals, while the second (saved to the disk by the principal module during its installation) is designed to attacks. In the course of its operation, Linux.BackDoor.Gates.5 collects and transmits to the attackers the following information about an infected computer:
- The number of CPU cores (from /proc/cpuinfo).
- CPU frequency (from /proc/cpuinfo).
- CPU usage (from /proc/stat).
- The host's IP (from /proc/net/route).
- The gate MAC address (from /proc/net/arp).
- Information about network interfaces (from proc/net/dev).
- The network adapter MAC address.
- The amount of RAM (MemTotal of /proc/meminfo).
- The volume of data transmitted and received (from /proc/net/dev).
- The OS name and version (using uname).
After its launch Linux.BackDoor.Gates.5 checks the path to the directory from which it has been launched, and, depending on the results, can follow four possible behaviour patterns.
If the path to the backdoor's executable file is different from those of netstat, lsof, and ps, it then launches itself in the background and starts the initialization procedure, during which it extracts the configuration file from its body. The file contains information that the malware needs to operate including the port and IP address of the command and control (C&C) server and the installation parameters.
Depending on the value of the parameter g_iGatsIsFx, the backdoor either connects to the C&C server or waits for an incoming connection—once the connection is established, the program verifies the remote host's IP address, and, if the verification is passed, it will consider the node to be its command server.
During its installation, the Trojan checks the file /tmp/moni.lock for the process PID. And, if the PID is found, the backdoor "kills" the corresponding process. Then Linux.BackDoor.Gates.5 checks whether its DDoS and backdoor modules are running (if they are, these processes are also "killed"). If the option g_iIsService is present in its configuration file, the Trojan adds the string #!/bin/bash\n<path_to_backdoor> in the file /etc/init.d/ to be launched at system startup, and then Linux.BackDoor.Gates.5 creates the following symlinks:
ln -s /etc/init.d/DbSecuritySpt /etc/rc1.d/S97DbSecuritySpt
ln -s /etc/init.d/DbSecuritySpt /etc/rc2.d/S97DbSecuritySpt
ln -s /etc/init.d/DbSecuritySpt /etc/rc3.d/S97DbSecuritySpt
ln -s /etc/init.d/DbSecuritySpt /etc/rc4.d/S97DbSecuritySptIf the option g_bDoBackdoor is available in the configuration file, the Trojan attempts to open the file /root/.profile to check whether root privileges are available for its process. Then the Trojan copies itself to /usr/bin/bsd-port/getty and launches the executable. At the final stage of installation, Linux.BackDoor.Gates.5 creates another copy of itself in /usr/bin/ under the name specified in the configuration file, and replaces the following utilities:
/bin/netstat
/bin/lsof
/bin/ps
/usr/bin/netstat
/usr/bin/lsof
/usr/bin/ps
/usr/sbin/netstat
/usr/sbin/lsof
/usr/sbin/psThe Trojan installation process is now complete, and a routine begins for the Trojan to perform its primary duties.
Following the other two behaviour patterns, the Trojan also starts as a daemon process on an infected computer, checks the relevant .lock-file to determine whether its components have started (if not, it starts them). However, the backdoor uses different names to save the files and modify the startup scripts.
Once the backdoor has connected to the C&C server, Linux.BackDoor.Gates.5 receives information about the task it needs to perform. When commanded by criminals, the program can update itself, start and stop a DDoS attack on a remote node with a specified IP address and port, or establish a connection and execute commands from another remote node at a specified IP address.
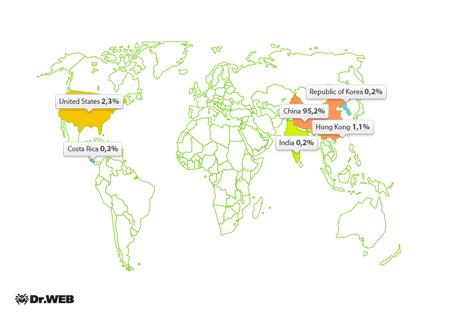
Chinese servers are typical targets for DDoS attacks mounted by means of the backdoor. However, sometimes criminals pick targets in other countries, too–the geographical distribution of DDoS attacks implemented using the Trojan is illustrated below.
This malicious program has been added to the Dr.Web virus database and poses no threat to systems protected by Doctor Web anti-viruses.