April 2014 virus activity review from Doctor Web
Virus reviews | Hot news | All the news | Virus alerts
April 30, 2014
Viruses
According to statistics gathered by Dr.Web CureIt!, in April 2014, Trojan.Packed.24524, which installs unwanted and dubious applications in compromised systems, was most frequently detected on PCs. As in the previous month, Trojan.BPlug programs ranked second and third. Implemented as browser plugins, they advertise dubious websites on loaded web pages. The 20 threats most frequently detected by Dr.Web CureIt! in April 2014 are listed in the table below:
| Name | Quantity | % |
|---|---|---|
| Trojan.Packed.24524 | 82889 | 6.18 |
| Trojan.BPlug.35 | 40183 | 3.00 |
| Trojan.BPlug.28 | 36799 | 2.74 |
| Trojan.InstallMonster.51 | 35536 | 2.65 |
| Trojan.BPlug.17 | 23664 | 1.77 |
| Trojan.InstallMonster.61 | 19183 | 1.43 |
| Trojan.LoadMoney.1 | 13636 | 1.02 |
| Trojan.LoadMoney.15 | 12975 | 0.97 |
| Trojan.Triosir.1 | 12596 | 0.94 |
| Trojan.Siggen5.64541 | 12452 | 0.93 |
| Trojan.DownLoader11.3101 | 12104 | 0.90 |
| Trojan.Wprot.3 | 10228 | 0.76 |
| Trojan.BPlug.48 | 8807 | 0.66 |
| Trojan.Packed.25266 | 8694 | 0.65 |
| Trojan.Ormes.2 | 8346 | 0.62 |
| Trojan.BPlug.33 | 8139 | 0.61 |
| BackDoor.IRC.NgrBot.42 | 8040 | 0.60 |
| BackDoor.Maxplus.24 | 7276 | 0.54 |
| Trojan.BPlug.47 | 7193 | 0.54 |
| Trojan.Packed.24814 | 7098 | 0.53 |
Botnets
The botnet created by hackers using the file infector Win32.Rmnet.12 is still operational. The first of its two subnets, which are monitored by Doctor Web's virus analysts, experienced a daily average of 165,500 connections being made to it by infected computers, while roughly 13,000 newly infected workstations were joining the botnet each day. The diagram below illustrates how the network expanded:
Win32.Rmnet.12 botnet growth in April 2014
(1st subnet)
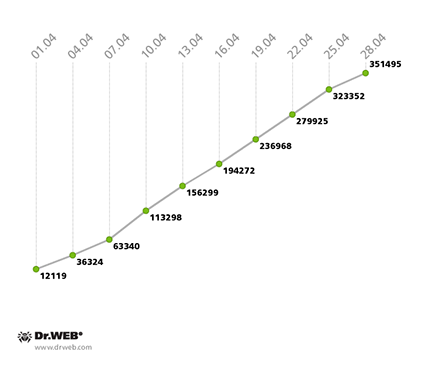
In the second Win32.Rmnet.12 subnet, on average 270,000 bots were operating daily, and about 12,000 newly infected PCs were joining the network every 24 hours. The second Win32.Rmnet.12 subnet’s growth can be traced in the following diagram:
Win32.Rmnet.12 botnet growth in April 2014
(2nd subnet)
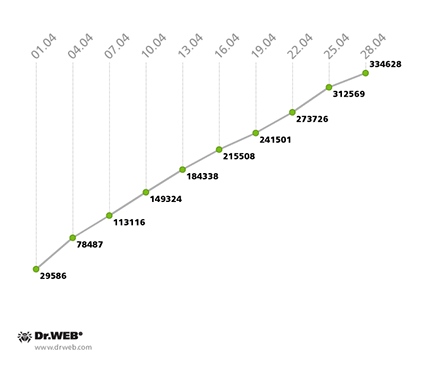
The number of machines on which Dr.Web anti-virus software has been detecting the malware module Trojan.Rmnet.19 decreased slightly—from 2,066 bots at the end of March to 1,866 in the last days of April.
The number of computers running Mac OS X and infected with BackDoor.Flashback.39 is declining gradually too. Over the past month the botnet shrank by another 30%—from 25,912 at the end of March to the current figure of 18,305 infected Macs.
Other threats in April
In early April, Doctor Web reported the discovery of a multi-component backdoor bootkit dubbed BackDoor.Gootkit.112. For their piece of craftsmanship, the virus writers behind the malware have borrowed bootkit features from programs in the Trojan.Mayachok family, but the attackers introduced significant changes to the source code.
To bypass the UAC and elevate its privileges in an infected system, BackDoor.Gootkit.112 employs a shim (Microsoft Windows Application Compatibility Infrastructure). Overall, the UAC bypass scheme looks as follows:
- The Trojan creates and installs a new fix database (shim);
- It then launches cliconfg.exe with elevated privileges;
- The shim unloads the original process and uses RedirectEXE to launch the Trojan.
The Trojan can execute the following commands:
- Intercept http traffic;
- Inject code into other processes;
- Block specific URLs;
- Take screenshots;
- Acquire the list of running processes;
- Acquire the list of local users and groups;
- End specified processes;
- Execute shell commands;
- Launch executables;
- Auto update.
A detailed analysis of the architecture, payload and operating principles of the Trojan BackDoor.Gootkit.112 can be found in our review.
The second half of April witnessed frequent complaints from Mac OS X users about annoying ads, which they periodically observed on web pages loaded in popular browsers. The cause behind this nuisance is multiple browser extensions that are installed into the system along with some legitimate programs.
One such program is Downlite which can be downloaded on a popular torrent tracker site by clicking on Download. As a result, the user is redirected to another site from which the Downlite installer (Dr.Web Anti-virus identifies it as Trojan.Downlite.1) is downloaded. The executable installs the legitimate application DlLite.app and several browser plugins. Also installed is the application dev.Jack which is designed to control Mozilla Firefox, Google Chrome and Safari. It is detected by Dr.Web anti-virus software as Trojan.Downlite.2. In addition, advertising plugins are bundled with other applications (MacVideoTunes, MediaCenter_XBMC, Popcorn-Time, and VideoPlayer_MPlayerX). The outcome of all these manipulations is that annoying ads of the following types appear in browser windows:
- Underlined keywords; hovering the mouse cursor over such words invokes advertising pop-ups;
- A small window with the Hide Ad button displayed in the bottom left corner;
- Banners on search engine result pages and on popular sites.
More information about this malicious program can be found in a corresponding review published by Doctor Web on its site.
Threats to handhelds
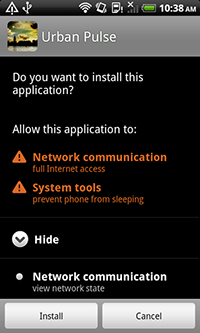
As far as new malware for Android is concerned, April wasn't exceptional—it even delivered several unpleasant surprises. Thus, the emergence of a new modification of the bootkit Android.Oldboot, which gained its notoriety in January 2014, became a major Android security event. The payload of this updated Trojan hardly differs from that of its predecessor: the program's main purpose is to covertly download and install other applications. However, it also incorporates several new features. In particular, when launched, several bootkit components delete the original files and only operate in the device's memory. This can significantly complicate the detection and neutralisation of this threat. Furthermore, to complicate the neutralisation of the updated Android.Oldboot, attackers have resorted to code obfuscation for some of its modules. They have also enhanced it with the ability to delete a number of anti-virus applications.
Google Play didn't go unnoticed by criminals either: several Trojan applications for covert Bitcoin mining appeared in the catalogue in the last month. The discovered Trojans were added to the Dr.Web virus database as Android.CoinMine.1. Concealed in harmless "live wallpaper", they would begin their malicious activities provided the infected mobile device was inactive for a certain period of time.
Similarly to the malicious programs discovered in March, the new Trojan miners could cause not only financial losses because of the substantial consumption of Internet traffic, but also adversely impact the operation of the mobile device itself.
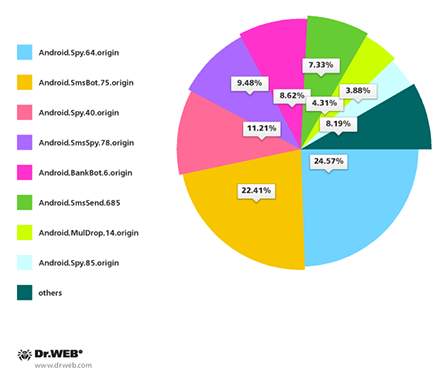
Also in April, attacks involving unwanted SMS messages containing malware download links persisted against South Korean Android users. Doctor Web's security researchers registered 232 such spamming attacks, and the most frequently detected Trojans included Android.Spy.64.origin, Android.SmsBot.75.origin, Android.Spy.40.origin, Android.SmsSpy.78.origin, Android.BankBot.6.origin and Android.SmsSend.685.
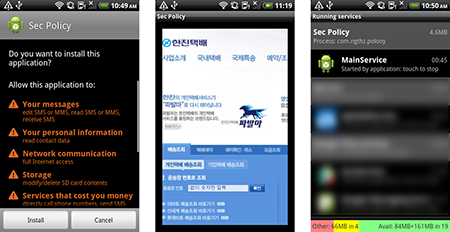
Special attention should be paid to Android.SmsBot.75.origin. To spread this program, criminals orchestrated more than 40 spam attacks in which users were notified about an alleged package delivery failure. If the user opened the link found in the SMS, they were redirected to a bogus blog page where they were offered to download an application that is in fact a Trojan capable of stealing confidential information and executing commands sent by criminals. More information about this threat can be found in a publication on Doctor Web's site.
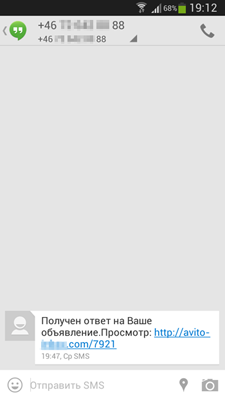
Distributing malware with SMS spam is popular in Russia too. In April such short messages contained a download link for the program Android.SmsSpy.88.origin.
Once the program was installed and launched, it would send some device information to criminals and then stand by for instructions which might include directives to intercept incoming messages, send SMS with specific parameters and forward all inbound phone calls. Thus, Android.SmsSpy.88.origin didn't just generate SMS spam but could also perform espionage activities.
In addition, in April security researchers learned about another Trojan targeting jail-broken devices manufactured by Apple. The malicious program in question is IPhoneOS.PWS.Stealer.1. Discovered on a number of devices in China, it can steal Apple ID information that provides access to most of the company's services, including the App Store, iCloud and others. Thus, the theft of this data could significantly impact the well-being of users.
Malicious files detected in mail traffic in April
| 01.04.2014 00:00 - 30.04.2014 14:00 | ||
| 1 | Trojan.DownLoad3.28161 | 0.95% |
| 2 | Trojan.Fraudster.778 | 0.76% |
| 3 | Trojan.PWS.Panda.5676 | 0.74% |
| 4 | Trojan.DownLoad3.32784 | 0.68% |
| 5 | Trojan.Oficla.zip | 0.67% |
| 6 | Trojan.DownLoader9.61937 | 0.65% |
| 7 | Trojan.Winlock.8811 | 0.57% |
| 8 | Trojan.VbCrypt.150 | 0.50% |
| 9 | Trojan.DownLoad3.30075 | 0.47% |
| 10 | Win32.HLLM.MyDoom.54464 | 0.42% |
| 11 | Trojan.PWS.Panda.547 | 0.41% |
| 12 | Trojan.Siggen6.14201 | 0.39% |
| 13 | Java.Siggen.90 | 0.38% |
| 14 | Win32.HLLM.MyDoom.33808 | 0.36% |
| 15 | Trojan.PWS.Panda.6971 | 0.36% |
| 16 | Trojan.PWS.Panda.4795 | 0.35% |
| 17 | Trojan.Packed.26385 | 0.32% |
| 18 | Trojan.PWS.Panda.2401 | 0.32% |
| 19 | BackDoor.Comet.884 | 0.29% |
| 20 | Trojan.Fraudster.517 | 0.29% |
Malicious files detected on user computers in April
| 01.04.2014 00:00 - 30.04.2014 14:00 | ||
| 1 | SCRIPT.Virus | 1.25% |
| 2 | Trojan.InstallMonster.51 | 0.66% |
| 3 | Trojan.Packed.24524 | 0.65% |
| 4 | Tool.Unwanted.JS.SMSFraud.26 | 0.46% |
| 5 | JS.Redirector.228 | 0.44% |
| 6 | Adware.Downware.2095 | 0.42% |
| 7 | Adware.Downware.179 | 0.38% |
| 8 | Adware.Toolbar.240 | 0.37% |
| 9 | Adware.NextLive.2 | 0.37% |
| 10 | Adware.OpenCandy.3 | 0.35% |
| 11 | Adware.OpenCandy.4 | 0.35% |
| 12 | Tool.Skymonk.14 | 0.33% |
| 13 | JS.IFrame.566 | 0.33% |
| 14 | Adware.Webalta.13 | 0.33% |
| 15 | BackDoor.PHP.Shell.6 | 0.32% |
| 16 | Adware.InstallCore.90 | 0.31% |
| 17 | BackDoor.IRC.NgrBot.42 | 0.30% |
| 18 | Adware.Conduit.33 | 0.30% |
| 19 | Adware.Bandoo.13 | 0.30% |
| 20 | Trojan.LoadMoney.257 | 0.29% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live