March 2014 virus activity review from Doctor Web
Virus reviews | All the news
April 2, 2014
Viruses
According to data collected in March 2014 with Dr.Web CureIt!, Trojan.Packed.24524, which installs adware and riskware in compromised systems, was the most frequent "guest" on user PCs. The advertising Trojans— Trojan.InstallMonster.51 and Trojan.LoadMoney.15 — ranked second and third respectively, with another advertising piece of malware — Trojan.LoadMoney.1 — following close behind. Also detected in March were several Trojan.BPlugprograms. These are implemented as browser plug-ins that display ads in loaded webpages or promote various bogus sites. The twenty Trojans most frequently detected in March by Dr.Web CureIt! are listed in the table below:
| Name | Quantity | % |
|---|---|---|
| Trojan.Packed.24524 | 68640 | 6.50 |
| Trojan.InstallMonster.51 | 21415 | 2.03 |
| Trojan.LoadMoney.15 | 18405 | 1.74 |
| Trojan.LoadMoney.1 | 16450 | 1.56 |
| Trojan.Siggen5.64541 | 16395 | 1.55 |
| Trojan.InstallMonster.61 | 15076 | 1.43 |
| Trojan.Triosir.1 | 14257 | 1.35 |
| Trojan.DownLoader11.3101 | 12510 | 1.18 |
| Trojan.BPlug.28 | 11664 | 1.10 |
| Trojan.Packed.24814 | 8646 | 0.82 |
| Trojan.Fraudster.524 | 8318 | 0.79 |
| Trojan.BPlug.10 | 8289 | 0.79 |
| BackDoor.IRC.NgrBot.42 | 8036 | 0.76 |
| BackDoor.Maxplus.24 | 7912 | 0.75 |
| Trojan.BPlug.17 | 7814 | 0.74 |
| Trojan.InstallMonster.38 | 7802 | 0.74 |
| Trojan.Hosts.6815 | 7248 | 0.69 |
| Trojan.MulDrop5.10078 | 6924 | 0.66 |
| Trojan.StartPage.59964 | 6889 | 0.65 |
| Trojan.Triosir.2 | 6237 | 0.59 |
Botnets
The botnet comprised of Windows machines compromised by the file infector Win32.Rmnet.12 has been growing steadily. In March, the average number of bots in its first subnet, which is being monitored by Doctor Web's security researchers, reached 244,430. The second subnet grew somewhat more slowly in March: its average number of bots was 157,343. The number of machines on which Dr.Web software detected Trojan.Rmnet.19 also declined slightly. At the end of March, it reached 2,066—457 fewer PCs than in the previous month.
Meanwhile, the number of Macs infected with the Trojan BackDoor.Flashback.39 fluctuating: in March, the average number of machines in that botnet was 25,912. It should be noted that all the computers that contacted the command and control server in the past month had already been infected earlier.
Other threats in March
In early March, Doctor Web's security researchers reported the discovery of Trojan.Skimer.19, a threat that compromises ATMs.
Once an ATM's OS is infected, Trojan.Skimer.19 monitors EPP (Encrypted Pin Pad) keystrokes for a specific input combination that will help it become activated and then execute whatever command an intruder enters via the EPP. The commands include the following:
- Save the log files onto the card's chip; decrypt PIN codes.
- Remove the Trojan library and log files; "cure" the host file; reboot the system (criminals issue commands twice to infected ATMs; both are issued within a ten-second interval).
- Display statistical information including the number of transactions, banking cards, intercepted encryption keys, etc.
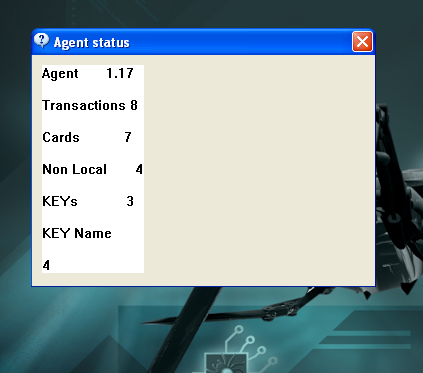
- Delete all the log files.
- Reboot the system.
- Read the executable from the card's chip to update the Trojan.
More information about Trojan.Skimer.19 can be found in a corresponding publication on Doctor Web's site.
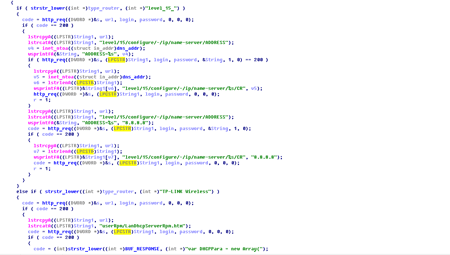
Also in March, Doctor Web's virus analysts examined the program Trojan.Rbrute, which is designed to crack Wi-Fi-router access passwords through brute force attacks and to switch out the DNS server addresses in the settings of these compromised devices. The Trojan can also execute two commands: 1) perform a network scan according to a specified range of IP addresses and 2) mount a dictionary attack. These commands are unrelated and can be performed by the Trojan separately.
Attackers have been using this malware to spread the file infector Win32.Sector. To learn more about how this malicious program operates and spreads, please refer to the corresponding informational material that has been published on our site.
Mobile threats
The first month of spring was stressful for Android. In early March cybercriminals launched the commercial distribution of a new Trojan, dubbed Android.Dendroid.1.origin. This malware, which can be embedded into any harmless Android app, enables attackers to carry out a number of illegal actions on an infected mobile device: intercept calls and SMS messages, get information about the current location of the device, gain access to the phone book and browsing history, activate the device's camera and microphone and send short messages. Android.Dendroid.1.origin is sold on underground hacker forums, which once again indicates that the market for illegal services for the Android is growing.
Android.Backdoor.53.origin was discovered by Doctor Web's security researchers in mid-March. It should be noted that in order to spread this program, the criminals behind it modified Webkey, a legitimate application that lets users control their mobile devices remotely. Unlike the original version, the compromised application doesn't have a GUI and after installation hides its presence in the system by removing its icon from the main screen. When launched, Android.Backdoor.53.origin sends the device's ID to a remote server, signalling that the infection was initiated successfully. Consequently, the intruders can get full control over the device and gain access to the personal data and hardware features.
 |  |
At month’s end, Doctor Web's analysts discovered an entire group of Android.DownLoader programs primarily targeting devices in China. On compromised mobile devices, these Trojans can download and install other malicious programs, as well as a number of legitimate applications, to generate a profit from the programs’ illegal promotion. These Trojans can be particularly dangerous, because if root access is available in a system, the downloaded programs can be installed without user consent. The malware can also generate a lot of traffic which can result in financial losses for subscribers whose service packages do not include unlimited Internet connectivity. More information about this incident can be found in a related news publication.
Also in March, the definitions for several Trojans that covertly mine some cryptocurrencies were added to the Dr.Web virus database. These malicious programs were distributed by criminals in modified versions of popular applications and sprang into action whenever the infected mobile device was in standby mode. Ultimately, these Trojans can not only significantly shorten battery life, but can also make users uncomfortable due to the increased heat generated by the device's constantly engaged components, activity that may, in turn, adversely affect their lifespan. Furthermore, because these Trojans actively use Internet connections, many subscribers may experience financial losses. Dr.Web for Android detects these threats as members of the Android.CoinMine family.
 |  |  |
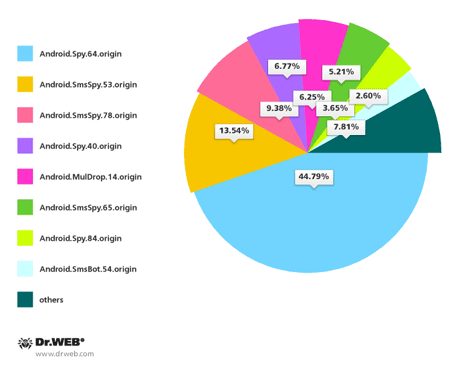
Compared with the previous month, in March, the number of unwanted SMS messages spreading malicious programs for Android in South Korea increased by 113.3%. In total, Doctor Web's specialists registered 192 incidents involving SMS spam spreading such Trojans. Android.Spy.64.origin (86 incidents), Android.SmsSpy.53.origin (26 incidents), Android.SmsSpy.78.origin (18 incidents), Android.Spy.40.origin (13 incidents) as well as Android.MulDrop.14.origin (12 incidents) and Android.SmsSpy.65.origin (10 incidents).
Malicious files detected in mail traffic in March
| 01.03.2014 00:00 - 31.03.2014 23:00 | ||
| 1 | Trojan.DownLoad3.28161 | 0.75% |
| 2 | Trojan.PWS.Panda.2401 | 0.65% |
| 3 | Trojan.PWS.Panda.4795 | 0.61% |
| 4 | BackDoor.Andromeda.267 | 0.60% |
| 5 | Trojan.DownLoader9.40182 | 0.57% |
| 6 | Trojan.Fraudster.778 | 0.56% |
| 7 | Trojan.PWS.Panda.5676 | 0.52% |
| 8 | Trojan.Oficla.zip | 0.46% |
| 9 | Trojan.DownLoader9.39262 | 0.44% |
| 10 | Trojan.Siggen6.11194 | 0.41% |
| 11 | Trojan.PWS.Panda.547 | 0.41% |
| 12 | Trojan.Inject1.38258 | 0.38% |
| 13 | Trojan.PWS.Stealer.4118 | 0.35% |
| 14 | Trojan.Fraudster.517 | 0.35% |
| 15 | BackDoor.Kuluoz.4 | 0.34% |
| 16 | Trojan.DownLoader9.39539 | 0.34% |
| 17 | Exploit.Rtf.36 | 0.33% |
| 18 | Win32.HLLM.MyDoom.33808 | 0.33% |
| 19 | Win32.HLLM.Graz | 0.31% |
| 20 | Trojan.DownLoader9.44784 | 0.29% |
Malicious files detected on user computers in March
| 01.03.2014 00:00 - 31.03.2014 23:00 | ||
| 1 | SCRIPT.Virus | 1.29% |
| 2 | Trojan.Packed.24524 | 0.62% |
| 3 | Trojan.InstallMonster.51 | 0.61% |
| 4 | Trojan.Fraudster.524 | 0.54% |
| 5 | Tool.Skymonk.14 | 0.43% |
| 6 | Trojan.LoadMoney.15 | 0.43% |
| 7 | Adware.NextLive.2 | 0.39% |
| 8 | JS.IFrame.566 | 0.38% |
| 9 | Adware.OpenCandy.3 | 0.35% |
| 10 | BackDoor.IRC.NgrBot.42 | 0.35% |
| 11 | Adware.Downware.179 | 0.35% |
| 12 | Adware.OpenCandy.4 | 0.34% |
| 13 | Tool.Unwanted.JS.SMSFraud.26 | 0.34% |
| 14 | Adware.Toolbar.240 | 0.33% |
| 15 | Adware.Webalta.13 | 0.33% |
| 16 | Adware.Downware.2232 | 0.33% |
| 17 | Tool.Skymonk.17 | 0.33% |
| 18 | Adware.Conduit.33 | 0.31% |
| 19 | JS.Redirector.209 | 0.30% |
| 20 | Trojan.MulDrop5.10078 | 0.30% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live