Trojans covertly installing applications under Android
Real-time threat news | Hot news | Threats to mobile devices | All the news
March 24, 2014
Implemented as an ordinary application for Android, Android.DownLoader.49.originis the most important member of the family. After installation, the Trojan is launched as a system service. It connects to a remote server and retrieves the list of programs it must download onto the compromised device. Some of the downloaded distribution files incorporate dex-files which are placed into the /cache/sysjar/ directory on the memory card. Then, the routine DexClassLoader is used to load their code into the device's memory. One of these binaries incorporates a Trojan downloader classified by Dr.Web as Android.DownLoader.43.origin. It can download various applications, including malware. Another file contains a dropper Trojan, which, depending on its version and the availability of root access, can install other malicious applications into the system directory.
In addition, Android.DownLoader.49.origin can also download other programs that are also installed without the user's consent. If root access is not available, the owner of the mobile device will see a standard system dialogue requesting permission to install the downloaded software.
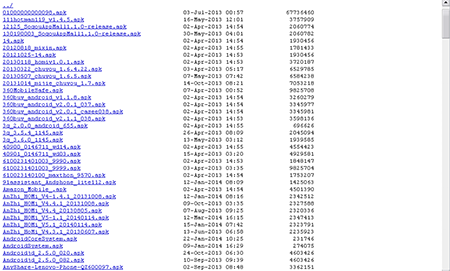
The Trojan Android.DownLoader.43.origin can also connect to a remote server to obtain a list of apps to download and install on an infected device. It is noteworthy that other downloader Trojans capable of performing similar tasks are on this list, too. Thus, virus writers have created a chain of malicious programs that can spread each other and other applications and can install programs selected by criminals to suit a particular purpose. In total, Doctor Web's security researchers found about 10 similar Trojan downloaders, and the attackers' server hosts nearly 600 programs intended for unauthorized installation.
The criminals behind the scheme are most likely interested in having various applications installed surreptitiously on target devices to increase the popularity of those applications and generate a per-installation profit. However, in addition to installing ordinary applications, the dropper can be instructed by the remote server to install other programs such as spying applications or SMS Trojans which can also generate income for their owners.
All the malignant applications described in this review are successfully detected by Dr.Web for Android and pose no threat to devices protected with the anti-virus.