Trojan.Skimer.19 threatens banks
Real-time threat news | Hot news | All the news | Virus alerts
March 4, 2014
Similar to its predecessors, the Trojan has its main payload incorporated into a dynamic link library stored in the NTFS stream of another malicious program that is detected by Dr.Web anti-virus software as Trojan.Starter.2971. If NTFS is used in the compromised system, Trojan.Skimer.19 also stores its logs in data streams. In these files, the program stores acquired bank card data and decryption keys.
Once an ATM's OS is infected, Trojan.Skimer.19 monitors Encrypted Pin Pad (EPP) keystrokes for a specific input combination that can initiate the execution of a command entered by an intruder via EPP. The commands include the following:
- Save the log files onto the card's chip; decrypt PIN codes;
- Remove the Trojan library and log files, "cure" the host file, and reboot the system (criminals issue the command twice to an infected ATM; the second command comes no later than 10 seconds after the first);
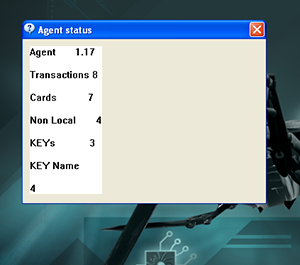
- Display statistical information including the number of transactions, banking cards, intercepted encryption keys, etc.;
- Delete all the log files;
- Reboot the system;
- Read the executable from the card's chip to update the Trojan.
Similar to earlier versions of malware from this family, recent versions of Trojan.Skimer.19 can be activated not only via the ATM's keypad, but also using special cards.
To decrypt intercepted data, Trojan.Skimer.19 uses the software installed on the ATM, or its own version of the symmetric key algorithm DES, and encryption keys that were intercepted and saved into the log file earlier.
Doctor Web's specialists know about several versions of the library bearing the Trojan payload. They differ in terms of the set of available features. All of them are successfully detected and removed by Dr.Web anti-virus software.