January 2014 virus activity review
Virus reviews | Hot news | All the news | Virus alerts
February 4, 2014
Viruses
According to statistics compiled in January with Dr.Web CureIt!, Trojan.Packed.24524 was the most frequently detected Trojan program. It installs adware and other dubious applications and spreads in the guise of legitimate software. Trojan.LoadMoney.1 and Trojan.InstallMonster.38 rank second and third respectively. BackDoor.Bulknet.1329 the bitcoin miner Trojan.BtcMine.221 are also being detected rather often. The top 20 most common malignant programs detected on hard drives by Dr.Web CureIt! are listed in the table below.
| Name | Quantity | % |
|---|---|---|
| Trojan.Packed.24524 | 50947 | 4.71 |
| Trojan.LoadMoney.1 | 35783 | 3.31 |
| Trojan.InstallMonster.38 | 19558 | 1.81 |
| Trojan.Siggen5.64541 | 17371 | 1.61 |
| BackDoor.Bulknet.1329 | 15929 | 1.47 |
| Trojan.BtcMine.221 | 14100 | 1.30 |
| Trojan.Siggen6.685 | 11673 | 1.08 |
| Trojan.BPlug.10 | 10761 | 0.99 |
| BackDoor.Maxplus.24 | 10622 | 0.98 |
| BackDoor.IRC.NgrBot.42 | 10168 | 0.94 |
| Trojan.InstallMonster.28 | 10039 | 0.93 |
| Trojan.DownLoad.64782 | 10008 | 0.93 |
| Trojan.Fraudster.502 | 9897 | 0.91 |
| Trojan.Fraudster.524 | 9739 | 0.90 |
| Trojan.Hosts.6815 | 9692 | 0.90 |
| Trojan.LoadMoney.76 | 8237 | 0.76 |
| Trojan.Packed.24814 | 8189 | 0.76 |
| Trojan.BPlug.4 | 7435 | 0.69 |
| Trojan.DownLoader10.56820 | 7220 | 0.67 |
| Trojan.DownLoader10.28709 | 6971 | 0.64 |
Botnets
The botnet created by hackers using the multi-component file infector Win32.Rmnet.12, which incorporates backdoor features and steals passwords from various applications, is growing gradually. Thus, on average, around 18,000 newly infected machines connected every day in January to one of the subnets controlled by Doctor Web. The botnet's growth is illustrated in the diagram below.
Win32.Rmnet.12 botnet growth in January 2014
(1st subnet)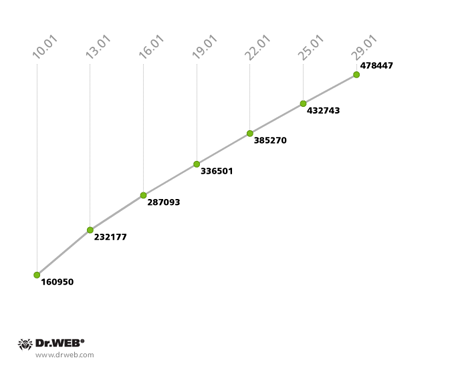
The second Win32.Rmnet.12 subnet followed a similar pattern, but the number of machines connecting to the control server daily gradually decreased: in the beginning of the month, around 20,000 hosts were involved, but at the end of January there were fewer than 12,000. The growth of the second Win32.Rmnet.12 subnet is clearly shown in the following chart.
Win32.Rmnet.12 botnet growth in January 2014
(2nd subnet)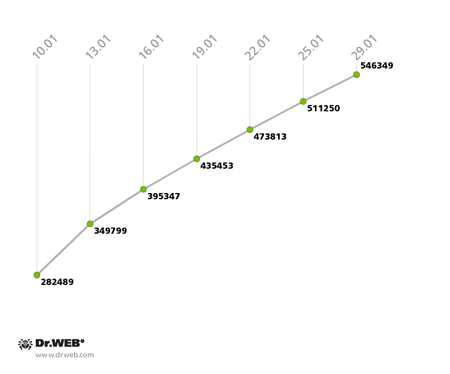
The number of computers on which Dr.Web software detected Trojan.Rmnet.19 remained unchanged over the past month: if at the end of December, 2,607 infected PCs were involved, that number stood at 2,633 on January 29.
The number of computers running Mac OS X, and infected with BackDoor.Flashback.39, also remained virtually unchanged through January: if at the end of December 2013 the number amounted to 28,829 infected Macs, then a month later it was 28,160. As before, the accounted for the highest number of infections—14,733; they were followed by (5,564 incidents), the (4,120 cases) and (1,582 incidents). In , only two infected Macs were discovered.
New ad Trojan
In January, Doctor Web's analysts found in the wild a new advertising Trojan spread by means of Facebook spam: Trojan.Zipvideom.1. This malicious program consists of several components, one of which downloads and installs malicious plug-ins for Mozilla Firefox and Google Chrome on a computer.
The plug-ins impede web browsing, display ads and can also download other unwanted software onto a computer. It has been discovered that when web pages of popular social networking websites (Twitter, Facebook, Google, YouTube, and VKontakte) are loaded into a browser window, these plug-ins also download dubious Java scripts. More information about this malware can be found in a review published on Doctor Web's site.
Threats to Android
Android users will above all remember January for the appearance of the first-ever bootkit for this OS. The malware, entered into the Dr.Web virus database as Android.Oldboot.1, would lodge itself into the protected memory area of infected devices which allowed it to run in the early stages of OS loading and also significantly complicated its complete removal. Once activated, Android.Oldboot.1 would extract several components into system directories and then install them as regular applications. Then, these Trojan components, detected by Dr.Web for Android as Android.Oldboot.2 and Android.Oldboot.1.origin, connect to a remote server, and in response to any commands received, can perform various malicious actions which may include downloading, installing and removing various programs.
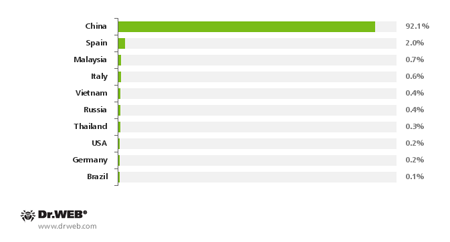
According to Doctor Web's security researchers, in late January the number of mobile devices infected with Android.Oldboot.1 exceeded 826,000, and geographically, the bootkit had appeared on devices located in Europe, Southeast Asia, and North and South America. It should be noted though that most of them resided in China whose market was the primary target of the criminals behind the malware.
Countries by number of infections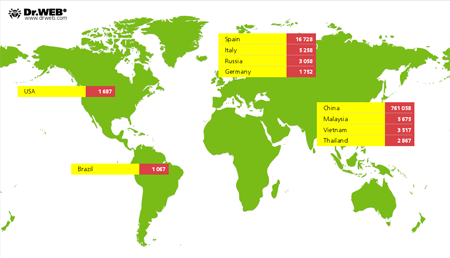
More information about this threat can be found in a corresponding publication on Doctor Web's site.
Android.Spy.67.origin was another malignant application that targeted devices in China in January. It was spread as a software update or as a popular application. It even created corresponding shortcuts on the main screen of mobile devices.

When launched, the Trojan would delete the shortcuts and collect personal information, including the SMS history, the call log and GPS coordinates. In addition, the malware could activate the mobile device’s camera and microphone; it would also index images and create thumbnails for them. All the acquired information was uploaded to an intruder-controlled server. On top of all that, if able to gain root access, Android.Spy.67.origin would disrupt the operation of popular Chinese anti-viruses, remove their virus databases, and install a malicious program that could, in turn, covertly install other applications. This malignant program was added to the virus database as Android.RootInst.1.origin.
Also discovered in the past month was a malicious program on Google Play. In particular, the Trojan dubbed Android.Click.3.origin was disguised as the game Real Basketball, but in truth was a worthless piece of nonsense containing malicious features.
Contrary to the expectations of users who wanted to install and play the game, the Trojan was installed under the guise of an application for accessing Google Play. At the same time, it would covertly load web pages using addresses from a predefined list, thus helping enterprising criminals generate a profit from the artificial increase in traffic to those sites and from taps on ads. The application was downloaded at least 10,000, times, so even if it was promptly removed by disappointed users, Android.Click.3.origin could significantly boost the budget of its authors.
 |
 |
In addition, in January criminals continued to spread a malicious application for Android in South Korea. Over the past month, Doctor Web's security researchers registered over 140 such incidents, slightly fewer than during the same period in December 2013. The most common Trojans in January included Android.Backdoor.31.origin (55%), Android.Spy.71 (9%), Android.Spy.45.origin (8%), Android.Spy.47.origin (4%) and Android.Spy.74 (3%). It should be noted that the discovered malware included many new versions of known programs which indicates the great interest cybercriminals have in the South Korean mobile market.
Malware for Android spread during January in South Korea via SMS spam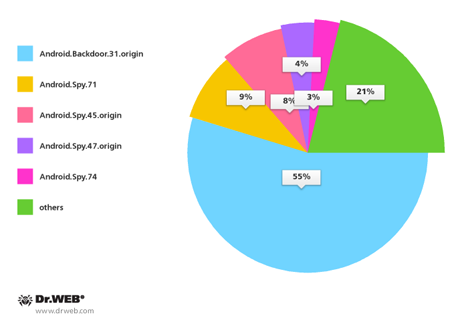
Malicious files detected in mail traffic in January
| 01.01.2014 00:00 - 31.01.2014 23:00 | ||
|---|---|---|
| 1 | Trojan.DownLoad3.28161 | 0.84% |
| 2 | Trojan.DownLoader9.22851 | 0.78% |
| 3 | Trojan.Inject2.23 | 0.68% |
| 4 | Trojan.DownLoad3.31532 | 0.66% |
| 5 | Trojan.DownLoader9.15291 | 0.64% |
| 6 | Trojan.DownLoad3.31401 | 0.61% |
| 7 | Trojan.DownLoad3.30075 | 0.59% |
| 8 | Trojan.DownLoader9.14962 | 0.50% |
| 9 | Trojan.Siggen6.1747 | 0.48% |
| 10 | Trojan.DownLoad.64857 | 0.40% |
| 11 | Trojan.DownLoad3.31541 | 0.38% |
| 12 | Trojan.DownLoader9.15295 | 0.38% |
| 13 | Trojan.Siggen6.5311 | 0.36% |
| 14 | Trojan.DownLoad3.31617 | 0.36% |
| 15 | Trojan.PWS.Panda.4795 | 0.35% |
| 16 | Trojan.DownLoad3.31533 | 0.30% |
| 17 | Trojan.DownLoad3.31534 | 0.30% |
| 18 | Trojan.PWS.Panda.547 | 0.30% |
| 19 | Trojan.Packed.666 | 0.30% |
| 20 | Trojan.DownLoader9.13584 | 0.29% |
Malicious files detected on user computers in January
| 01.01.2014 00:00 - 31.01.2014 23:00 | ||
|---|---|---|
| 1 | SCRIPT.Virus | 1.00% |
| 2 | Adware.Downware.915 | 0.63% |
| 3 | Trojan.Fraudster.524 | 0.58% |
| 4 | Tool.Unwanted.JS.SMSFraud.26 | 0.57% |
| 5 | Trojan.Packed.24524 | 0.55% |
| 6 | Trojan.LoadMoney.1 | 0.55% |
| 7 | Tool.Skymonk.14 | 0.53% |
| 8 | Adware.NextLive.2 | 0.52% |
| 9 | Adware.Downware.179 | 0.48% |
| 10 | Trojan.LoadMoney.15 | 0.45% |
| 11 | Trojan.Fraudster.502 | 0.41% |
| 12 | JS.Redirector.209 | 0.41% |
| 13 | Trojan.InstallMonster.47 | 0.40% |
| 14 | Tool.Skymonk.17 | 0.39% |
| 15 | BackDoor.IRC.NgrBot.42 | 0.37% |
| 16 | Trojan.Packed.24814 | 0.37% |
| 17 | Adware.InstallCore.90 | 0.36% |
| 18 | BackDoor.PHP.Shell.6 | 0.34% |
| 19 | Adware.NextLive.1 | 0.31% |
| 20 | Adware.Downware.1655 | 0.31% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live