2013 Virus Activity Overview
Virus reviews | Hot news | All the news | Virus alerts
February 12, 2014
Viruses
According to statistics compiled with Dr.Web CureIt! over the course of the year, Trojan.Hosts programs were the most common threats of 2013. Trojan.Hosts.6815, which in an infected system modifies the hosts file containing DNS-server IP addresses, proved to be the most common Trojan of that family. As a result of its activity, when a user tries to go to one of the sites specified in the file, the browser is automatically redirected to a specially crafted malicious web page. Trojan.LoadMoney.1 is a downloader application that ranks second among the year’s top threats. This program downloads and installs various unwanted applications on compromised computers. BackDoor.IRC.NgrBot.42 is a malicious program that has been well known to information security experts since 2011, and it ranks third. Trojans of this family communicate with a remote server via the IRC protocol and can execute a vast variety of commands issued by criminals. The malicious payload of BackDoor.IRC.NgrBot.42 allows it to destroy the boot record if the malware's integrity has been compromised, block access to anti-virus company websites, and intercept logins and passwords used to log on to various sites. BackDoor.IRC.NgrBot.42 infects all removable data storage devices connected to a computer and then hides the folders on the infected device and creates corresponding shortcuts that lead to its executable file. Thus, when trying to open any folder on the infected device, the user runs the malicious application.
Twenty threats most often found on computers by the end of 2013 (according to statistics from Dr.Web CureIt!) are listed in the table below.
| № | Name | % |
|---|---|---|
| 1 | Trojan.Hosts.6815 | 1.74 |
| 2 | Trojan.LoadMoney.1 | 1.38 |
| 3 | BackDoor.IRC.NgrBot.42 | 1.14 |
| 4 | Trojan.Mods.2 | 0.94 |
| 5 | Trojan.MayachokMEM.4 | 0.72 |
| 6 | Trojan.Hosts.6838 | 0.71 |
| 7 | Win32.HLLP.Neshta | 0.70 |
| 8 | Trojan.SMSSend.2363 | 0.69 |
| 9 | Trojan.Packed.24524 | 0.64 |
| 10 | Trojan.Redirect.140 | 0.64 |
| 11 | Trojan.Mods.1 | 0.57 |
| 12 | Trojan.Packed.24079 | 0.56 |
| 13 | Trojan.DownLoader9.19157 | 0.52 |
| 14 | Trojan.MayachokMEM.7 | 0.52 |
| 15 | Trojan.InstallMonster.38 | 0.50 |
| 16 | Win32.HLLW.Gavir.ini | 0.47 |
| 17 | Win32.Sector.22 | 0.46 |
| 18 | Trojan.StartPage.48148 | 0.44 |
| 19 | Trojan.Zekos | 0.43 |
| 20 | BackDoor.Maxplus.24 | 0.40 |
Botnets
Throughout the year, Doctor Web's analysts monitored the activity of several botnets organized by cybercriminals with the aid of Trojans and file infectors. One of them virtually ceased to exist in the second half of 2013. At the same time, some botnets are still operating and growing in number.
Since September 2011, Doctor Web's analysts have been monitoring two botnets created by the multi-component file infector Win32.Rmnet.12. This program is capable of self-replication without user intervention. Once on an infected computer, it infects executable files and can perform commands sent from a remote server (including a directive to render the system non-operational); it can also steal passwords stored by popular FTP-client programs. In addition, the virus can embed content into loaded web pages (i.e., make web injections), redirect a browser to a site specified by criminals, and send user-entered information from web forms to remote hosts.
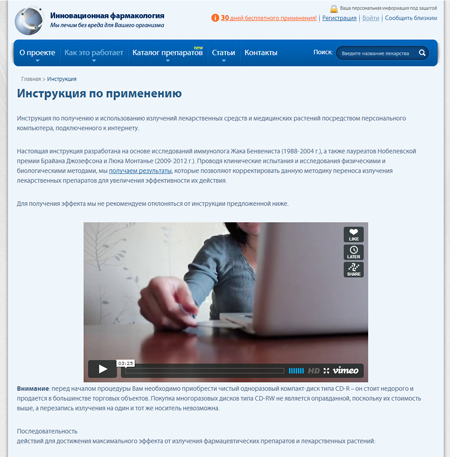
By the end of April 2013, the total number of computers that had ever been infected with Win32.Rmnet.12 was 9,232,024; a 2.5 million increase occurred in the first three months. Of course, occasionally some PCs were cured of the threat, but more and more infected machines kept joining the botnet. In May, the average number of active bots in both subnets of Win32.Rmnet.12 was 1,078,870, with about 25,000 infected computers joining both zombie networks daily. The growth of the two Win32.Rmnet.12 subnets monitored by Doctor Web is illustrated in the diagram below.
Win32.Rmnet.12 botnet growth in 2013 (1st subnet)
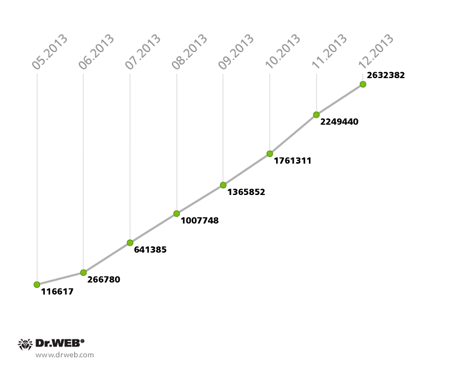
Win32.Rmnet.12 botnet growth in 2013 (2nd subnet)
Another large botnet consisting of computers infected with the file infector Win32.Rmnet.16 — the updated version of Win32.Rmnet.12 — stopped growing in September 2013. In December 2012, the botnet was comprised of 259,458 infected PCs, but by December 31, 2013, it topped out at 1,966 and is still declining gradually.
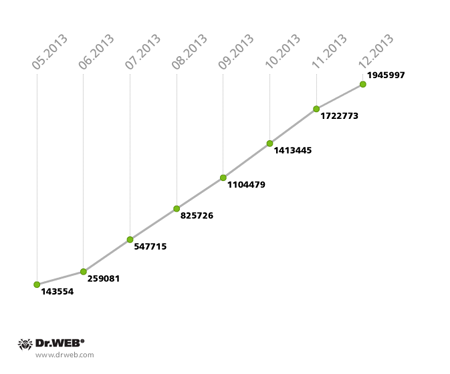
In May 2013, Doctor Web's analysts found two more representatives of the Rmnet family — these malicious modules were distributed with the file infector Win32.Rmnet and were given the shared name Trojan.Rmnet.19. One of them is designed to detect virtual machines in an infected system, and the other enables intruders to disable a variety of anti-virus programs, if installed in the system.
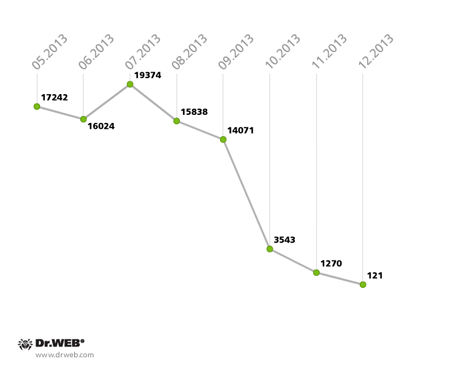
As of May 22, 2013, Trojan.Rmnet.19 modules were found on 18,000 desktops and laptops, but that number declined steadily month after month until it reached 5,456 infected PCs, while the number of active bots was even a little below this value. The process is illustrated in the diagram below.
The Trojan.Rmnet.19 botnet’s fluctuation in size in 2013
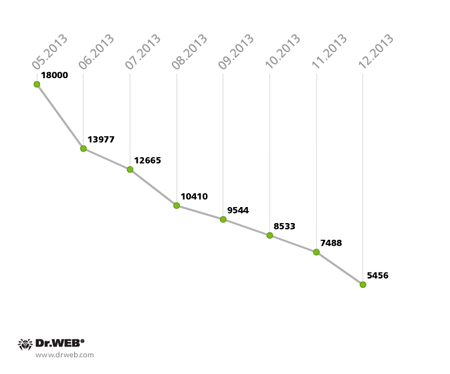
A botnet also exists that consists of computers infected with BackDoor.Bulknet.739. This malicious program is designed for spam mass mailings and was added to the Dr.Web virus database in October 2012. April saw the peak of its distribution, when about 100 computers were getting infected hourly, and at the end of May the total number of infected hosts reached 17,000. The Trojan spread most widely in Italy, France, Turkey, the USA, Mexico and Thailand. The number of computers connected to the botnet grew and declined through the summer, but in the autumn the number of infections was decreasing steadily, and in December the botnet virtually ceased to exist. This process is clearly demonstrated in the chart below.
The BackDoor.Bulknet.739 botnet’s fluctuation in size in 2013
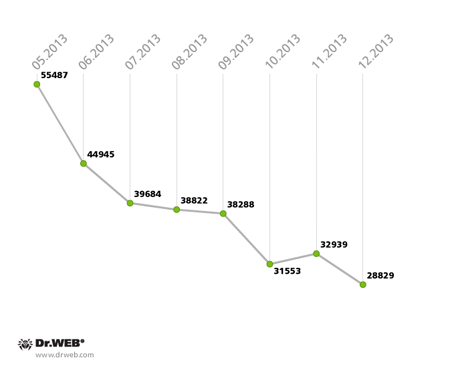
Finally, we should say a few words about the Backdoor.Flashback.39, which infects the Mac OS X operating system. In 2012, it was used by intruders to create the largest botnet in history, which included more than 800,000 infected Macs. Subsequently, news of a severe threat to Apple-manufactured computers was reported by numerous media outlets. It seemed that Mac OS X users worldwide were at least informed about the potential threat, and that one could soon expect the planet to be completely free of infected Macs. However, apparently the carelessness of Apple fans impacted how the threat spread: according to statistics acquired by Doctor Web's analysts, around 75,000 Macs were still infected with the malware by the end of January 2013. Their number was gradually reduced, but at a rather slow pace: in May, the number of Backdoor.Flashback.39 infections was about 55,000, and in June it dropped to 45,000 infected machines, and then the botnet's rate of reduction fell markedly. As of December 31, 2013, the Backdoor.Flashback.39 botnet included 28,829 infected Macs, and it still remains the largest in the world.
The Backdoor.Flashback.39 botnet’s decline in 2013
Trojans encoders
In 2013, Trojan.Encoder programs that encrypt files on computers and demand money for their decryption became a real scourge. During the year, the Dr.Web virus databases were supplemented by definitions for more than 200 new modifications of encoders, and the geography of these threats expanded considerably. And, the technologies used by the attackers evolved, too: above all, more sophisticated encryption was employed, making it virtually impossible to restore data affected by the actions of some Trojan.Encoder modifications. In addition, criminals improved their targeting of potential victims. For example, attackers attached malicious files to forms job hopefuls had to fill out in order to apply for an accountant position and sent out e-mails containing such attachments to companies that were offering such jobs. In such cases, the Trojan could encrypt rather important files that could contain accounting calculations—this increased the probability that the criminals would receive their ransom.
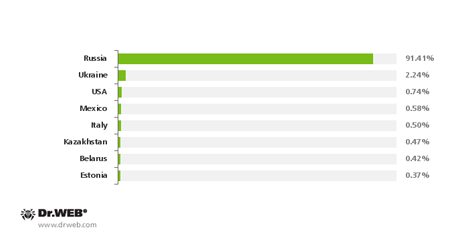
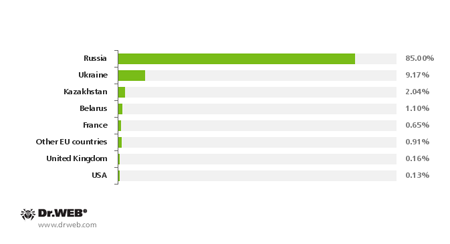
More than 6,700 users whose data was encrypted by encoder Trojans contacted Doctor Web in 2013. Apart from Russian users, in many cases, victims were found in other countries?mainly, the Ukraine and other CIS countries, the U.S., Italy and Latin America?although Russians constituted the overwhelming majority. Statistics showing encoder Trojan-related support requests by country are presented in the diagram below.
Encoder Trojan-related support requests by country
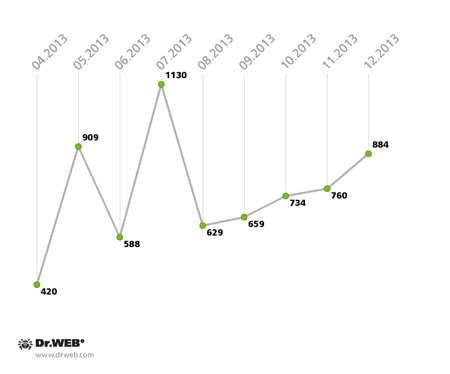
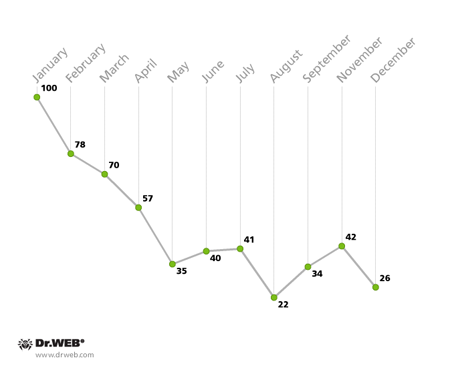
On average, Doctor Web's analysts received 20-50 file decryption requests daily. Fluctuations in the number of requests for help with file decryption, received by Doctor Web between April and December 2013, are illustrated in the graph below.
Support requests received from users whose systems were infected with encoder Trojans in 2013
Trojan.Archivelock, Trojan.Encoder.94, Trojan.Encoder.102, Trojan.Encoder.293, Trojan.Encoder.225, Trojan.Encoder.263, Trojan.Encoder.145 and Trojan.Encoder.215 were the most common encoder modifications in 2013. Of those, the most common encoder — Trojan.Encoder.94 — has been known to security experts since 2010. It encrypts only certain types of files on hard drives and has the largest (more than 400) number of modifications. Trojan.Archivelock, discovered in April 2012, is another quite common encoder. This malware uses WinRAR to encrypt files—a rather unusual feature. To spread the malware, criminals mount a brute force attack via the RDP protocol on target machines. Once the attackers have connected to the compromised host, they launch a Trojan onto it that uses the console version of WinRAR to place files on a previously compiled list into password-protected, self-extracting archives, and employs a special utility to delete original files that subsequently can never be restored. Many computers compromised by the malware reside in Spain and France.
Trojan.Encoder.102 (responsible for more than 17% of infections) is also a rather old malignant program whose first iterations were discovered in 2011. Trojan.Encoder.225, also a widespread threat, can penetrate a system by means of modified RTF files that exploit the vulnerability CVE-2012-0158. Such files are distributed as email attachments. While encrypting files, the Trojan tried to disguise itself as a Windows update process and displayed a corresponding dialogue box.
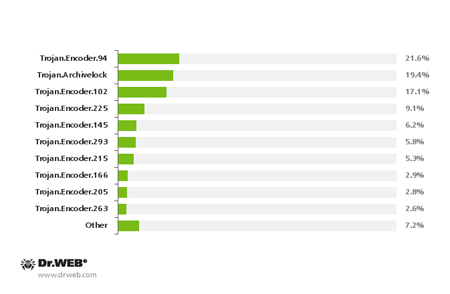
Many requests were received from users whose systems were infected with Trojan.Encoder.205 and Trojan.Encoder.215—together, they account for more than 8% of the total number of incidents. Typically, infection occurs via mass mailings containing an exploit for one of the vulnerabilities (CVE-2012-0158). This exploit creates a loophole through which a downloader Trojan can enter and then download and install the encoder. Both Trojan modifications use a primitive encryption routine, and yet errors in the program's code sometimes prevent even the criminals themselves from deciphering the encrypted data. However, Doctor Web's analysts crack the cipher easily. The most common encoder modifications in 2013 are presented in the diagram below.
The most common Trojan encoder modifications in 2013
Winlockers
In 2013, blockers that interfere with the normal inner workings of operating systems and demand money from their victims to unlock Windows, gradually lost in popularity among virus writers. These blockers were superseded by encryption Trojans and more "advanced" malware, like representatives of the Trojan.Mayachok family which use web-injects to block access to certain sites. Overall, in the past year, 3,087 users contacted Doctor Web's technical support about Winlock incidents—71% fewer users than in the previous year. The greatest number of requests came in during the first six months of the year, but by the end of 2013, their number was declining steadily.
The fluctuation in the number of technical support requests related to blocker Trojans in 2013 (as a percentage of the total of 633 incidents)
As with encoder Trojans, most computers that have been compromised with Windows blockers reside in Russia. The Ukraine ranks second, followed by Belarus and Kazakhstan. Trojan blocker incidents on computers found in France and other EU countries were registered, too.
Blocker Trojan-related support requests by country
Financial affairs
Remote banking software is the constant focus of intruders' attention. In addition to previously known banking Trojans found in the wild, new threats were identified in 2013. In particular, attacks on payment terminals persisted throughout the year. A new version of Trojan.Dexter (also known as Alina, BlackPOS, Dexter, and Vskimmer) inflicted multi-million dollar damages on banks in 40 countries. This malicious program works like a skimmer—a device that is attached to an ATM and copies data from the magnetic strips on plastic bank cards. But rather than acquiring data from the card reader, Dexter copies it from the memory of the terminal (point-of-sale, POS-terminal). Hundreds of thousands of credit and debit cards were compromised this way.
In autumn 2013, Doctor Web's analysts discovered a modification of a Trojan.Ibank program that was targeting SAP (Systems, Applications and Products) enterprise software (accounting, trade, production, finance, personnel management, warehouse management, etc.). The Trojan operates in both 32-bit and 64-bit versions of Windows and uses various methods to compromise different platforms. Security experts find the increased interest of virus writers in SAP and ERP rather disturbing: attackers can employ such technologies to steal business-critical information processed by these solutions.
Also in November, Doctor Web reported incidents involving the banking Trojan BackDoor.Caphaw spreading via Skype. To infect computers via Skype, criminals sent out messages under accounts used in previously infected systems. This Trojan has a very extensive range of features; for example, it keeps track of user activity and tries to detect attempts being made to connect to various online banking systems. If it does detect such connections, BackDoor.Caphaw can embed arbitrary content into web pages loaded by users and intercept information entered by them in various web forms.
Advertising and mining Trojans as the trend of the season
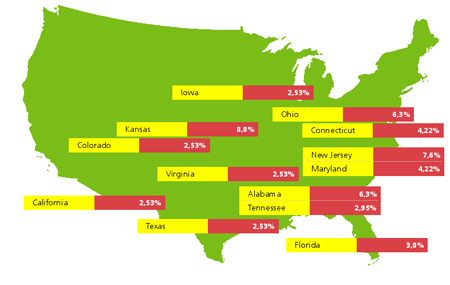
During 2013, Trojans displaying annoying ads regularly appeared on the list of programs most frequently detected on desktops and laptops. Because many such threats spread using affiliate programs that allow attackers to capitalize on the quantity of adware installations, their number is steadily increasing. Trojan.LoadMoney.1 downloads and installs various unwanted software programs in a compromised system. This application is always among the leaders in terms of the number of detections. BackDoor.Finder was another threat that helped attackers profit from increased traffic on certain sites. It was discovered in early 2013. The main purpose of this malware is to generate fake search results: when a user tries to search the web via google.com, bing.com, yahoo.com, ask.com, search.aol.com, search.icq.com, search.xxx , www.wiki.com, www.alexa.com or yandex.com from an infected machine, they will see website links specified by criminals rather than actual search results. BackDoor.Finder is most prevalent in the U.S., where Kansas takes top spot, followed by Pennsylvania, and then Alabama.
Similar features were found in two other Trojans discovered in 2013 — Trojan.Mods.1 and Trojan.Zekos. Trojan.Mods.1 is chiefly designed to replace web pages visited by users with malicious web pages; it accomplishes this by intercepting the system functions responsible for translating DNS names to IP addresses. As a result of the Trojan's activity, users end up visiting bogus sites instead of those they actually intended to go to. Trojan.Zekos carries an extremely sophisticated malicious payload. One of its features enables this malware to intercept DNS queries sent by popular browsers from an infected computer and instead display web pages provided by criminals. Meanwhile, the correct URL will be displayed in the address bar. In addition, Trojan.Zekos blocks access to the Internet sites of most anti-virus companies and to Microsoft’s servers.
Trojan.Lyrics can certainly be classified as an advertising Trojan—it shows annoying ads on the screen and directs browsers to dubious websites without the user's knowledge. With this program, music lovers are supposedly able to play any song posted on YouTube and read the lyrics at the same time—i.e., it turns watching videos into a karaoke experience. Links to download this program can be found on various torrent, music and social networking sites. If installed on a computer, the program will display annoying pop-ups as well as various advertising messages in rather unexpected places in the browser window. Also, when the user clicks on various links, the Trojan can redirect them to dubious and fraudulent sites. Some of them spread other malware, particularly, fake anti-viruses that Dr.Web detects as Trojan.Fakealert programs.
Mac OS X users didn’t go unnoticed by criminals either. For them, attackers developed Trojan.Yontoo.1 which downloads and installs extensions for Safari, Chrome and Firefox. These extensions are used to display ads while a user browses the web.
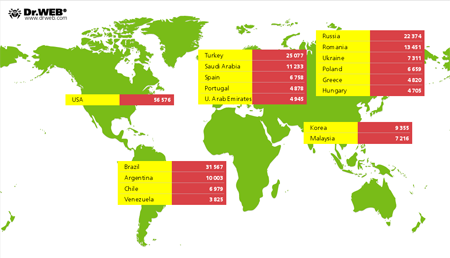
Virus-makers who chose to profit from Bitcoin and Litecoin mining sprang into action in the second half of 2013. Discovered by Doctor Web's analysts, Trojan.BtcMine.221 was the first threat of this kind. It was distributed from several criminal-owned websites in the guise of add-ins for popular browsers that ostensibly help users find cheaper offers in online stores, while they are actually intended to mine Litecoin (a Bitcoin alternative) by utilising system hardware resources without the user's knowledge. The largest number of hosts infected by Trojan.BtcMine.221 (56,576) are located in the United States. Brazil ranks second with 31,567 bots, and Turkey ranks third with 25,077 compromised machines. Russia, with 22,374 registered installations, is in fourth place. The average daily income for the criminals involved was 1,454.53 U.S. dollars. The malware’s geographical distribution by country is illustrated below.
Trojan.BtcMine.218, another similar Trojan, was discovered shortly thereafter. Security experts will remember it for strings in the program's code containing the names of its developers. Apparently, the authors merely forgot to delete them. Also discovered at the end of the year was a Trojan.Mods modification dubbed Trojan.Mods.10. Criminals equipped it with a bitcoin mining module. However, its main purpose is to replace browser window content with web pages crafted by criminals.
Threats to Linux
IT security experts will also remember 2013 for the increased number of threats to Linux. Linux.Hanthie also known as the Hand of Thief, was the most remarkable of them. The criminals who promoted it on underground forums positioned the malware as a FormGrabber bot and a Linux BackDoor. It features anti-detection technologies and routines for its covert startup, does not require administrator privileges, and uses strong encryption (256-bit) for communicating with the control panel. The Trojan can operate under various Linux distributions, including Ubuntu, Fedora and Debian, and supports eight desktop environments such as GNOME and KDE. Linux.Hanthie embeds a special grabber in Firefox, Google Chrome, Opera, Chromium and Ice Wease to intercept HTTP and HTTPS sessions and transmit data entered by users in web forms. The program also performs backdoor tasks; when communicating with the command and control (C&C) server, traffic is encrypted. If one tries to access the running script bind or bc, the Trojan displays the following message in the console:
Another malware program, Linux.Sshdkit, is designed to compromise Linux servers. Linux.Sshdkit is a library file available for 32- and 64-bit versions of Linux distributions. After successful installation, the Trojan injects its code into the sshd process and uses this process’s authorization routines. Once a session is started and a user enters their login and password, the Trojan sends them to a remote server via UDP. Doctor Web's analysts used a sinkhole to hijack one of Linux.Sshdkit’s control servers and thus confirmed that the Trojan sends stolen logins and passwords to remote hosts. In May 2013, the Trojan sent access data for 562 infected Linux servers to the C&C server controlled by Doctor Web. Some of these servers belong to major hosting providers.
Another modification of this threat — Linux.Sshdkit.6 — was discovered a bit later. It incorporated a modified routine for determining the addresses of the servers to which the Trojan transmits stolen information. This was supposed to make it more difficult for virus analysts to intercept stolen passwords.
Linux.Fokirtor.1 is a GNU/Linux backdoor that, in May 2013, attacked the servers of a large hosting provider in an attempt to steal confidential information of its clients. Since the target was well protected, the attackers disguised the backdoor as server processes (SSH, etc.) to hide suspicious network traffic and malicious files from a security inspection. The signature of the malware was added to the Dr.Web virus database.
Apart from the above threats, also added to the Dr.Web virus database were entries for several modifications of Linux-Trojans designed for organized DDoS-attacks—these malicious programs were dubbed Linux.DDoS. Furthermore, threats to Linux discovered over the past 12 months include Linux.Darlloz — a worm that exploits a PHP vulnerability, Linux.Cdorked — a backdoor infecting web servers, and Linux.Trolomod which targets Apache.
Threats to Android
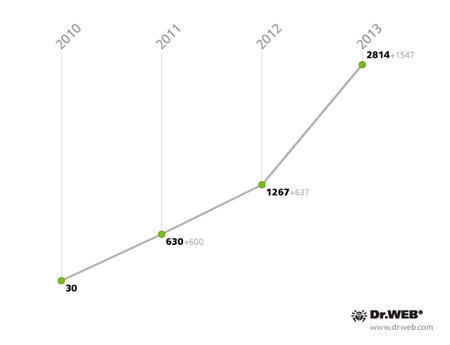
As in the past few years, 2013 was particularly threatening for devices running Android. During this period, the Dr.Web virus database received 1,547 new entries corresponding to malignant, unwanted and potentially dangerous programs, resulting in a total of 2,814 virus definitions. Thus, since the emergence in 2010 of the first malignant Android applications, which at that time numbered 30, their number has increased almost 94 times.
Android virus definitions’ growth in numbers from 2010 till 2013
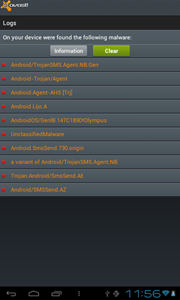
Traditionally, Trojans that send expensive SMS messages and sign up subscribers to chargeable services have posed the greatest threat to users. In particular, such threats include numerous Android.SmsSend and Android.SmsBot programs.
Malignant programs that steal confidential information were no less dangerous. Android.Spy and Android.SmsSpy are typical examples of such malware. Many programs of these families are banking Trojans that can steal authentication information and short messages containing transaction-related information.
In this regard, the continuing increase in the number of proposals related to various illegal services—such as developing and selling malware for Android—is very revealing: in addition to SMS Trojans, which were rather popular on the black market, cybercriminals added spyware Trojans capable of giving many users a hard time.
Compared with 2012, the number of Android.Fakealert applications quintupled. These programs detect non-existent threats on mobile devices and offer to neutralise them for a fee.
 |
 |
In addition, several Android vulnerabilities that could be exploited to spread various malignant applications were discovered. The Trojans that successfully exploited them included Android.Nimefas.1.origin and Android.Spy.40.origin.
More details about these and other threats can be found in corresponding mobile threat reviews posted on the Doctor Web site.
Internet fraud
Employing various techniques to obtain money from Internet users, scammers didn't idle away the year either. They often employed social engineering and other psychological tricks to deceive those down on their luck (e.g., people looking for extra work). For example, in Russia criminals often registered at job search portals as potential employers and promised would-be-workers high salaries to lure them onto a bogus site. There people had to enter their mobile phone number and send an acquired confirmation code with a short message. As the result, the victim ended up subscribed to a chargeable pseudo service.
Also in 2013, Internet swindlers took to launching the most fraudulent and authentic-looking portals promoting a wide range of services. Whenever visitors to such sites refreshed web pages, they would see an advertisement for a different pseudo service. These include an audio course that helps listeners cure their varicose veins, meditation that facilitates teeth whitening, "proven" methods for getting rid of pimples, thousands of non-surgical techniques for lip and breast augmentation, a seduction course for teen-aged girls, and, of course, long-distance fertility treatments for women. It should be noted that while our analysts knew about most of the above "courses", the proposals to become pregnant by listening to a CD, appeared rather recently.
Another trend of 2013 was the appearance of a large number of sites offering to treat serious diseases like tuberculosis with dried mole crickets—insects of the order Orthoptera.
Other entirely traditional online swindles have become widespread. These involve magical rituals for which gullible users are encouraged to buy certificates; magic candles imbued with the energy of love, harmony and happiness; as well as Pharaoh cylinders, allegedly crafted by Russian scientists on the basis of ancient Egyptian manuscripts that have miraculously survived to this day. In addition, fraudsters designed several web pages where visitors were invited to "download" the emanations of different medicines from a special "information center", after which the trusting users were asked to wait while the healing light was being recorded on a CD.
Dating sites also saw their share of fraud. Scammers posing as foreigners offered women expensive gifts (tablets, smart phones or jewellery). However, because the gifts were of great value, they could only be sent via a private courier service. And the sites for those courier services were also designed by the fraudsters. There the victims were informed that the sender had failed to cover the full shipment cost and were asked to pay the shipping charges themselves. Naturally, soon after payment is made, the courier service and the generous suitor vanish.
Doctor Web urges users to be careful and exercise caution when dealing with suspicious offers and casual acquaintances online. Do not submit your phone number on suspicious sites, and do not enter confirmation codes received in SMS messages. Network scammers can be very creative, so there’s no harm in being cautious and slightly suspicious.
Prospects
Based on the current situation in the information security field, we can assume that threats to Android will continue to grow in number. In September 2013, Doctor Web's analysts discovered the largest known botnet comprised of mobile devices infected with several Android.SmsSend modifications. There is sufficient reason to believe that this botnet was not the last in history, and that it’s only a matter of time before new mobile botnets emerge.
The emergence in the public domain of malware construction kits, allowing even inexperienced programmers to create new versions of encoder Trojans, will probably entail a rise in the number of infections being caused by these malicious programs. The geographical spread of encoder Trojans is likely to expand, too.
As Bitcoin-like systems multiply, so will Trojans that utilise the hardware of compromised systems for mining. In all likelihood, the attackers will increasingly make use of the Tor network as well as P2P networks to facilitate communication between malicious programs and C&C servers. The number of advertising Trojans, including those disguised as browser extensions, will increase markedly, too.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live