December virus activity review from Doctor Web
Virus reviews | Hot news | All the news | Virus alerts
January 13, 2014
Viruses
According to statistics compiled by means of the utility Dr.Web CureIt!, as before, the advertising Trojans Trojan.InstallMonster.38 and Trojan.LoadMoney.1 became the absolute leaders among the threats detected on computers in December 2013. Also among the most common threats in December’s statistics are advertising malware dubbed Trojan.Packed.24524 and Trojan.Siggen5.64541 — dynamic libraries designed to intercept various browser routines. The twenty malicious programs most frequently detected by Dr.Web CureIt! in December 2013 are listed below.
| Name | Quantity | % |
|---|---|---|
| Trojan.InstallMonster.38 | 26886 | 2.85 |
| Trojan.LoadMoney.1 | 24227 | 2.57 |
| Trojan.Packed.24524 | 23867 | 2.53 |
| Trojan.Siggen5.64541 | 12130 | 1.29 |
| BackDoor.IRC.NgrBot.42 | 12004 | 1.27 |
| Trojan.Hosts.6815 | 11092 | 1.18 |
| Trojan.LoadMoney.76 | 9670 | 1.03 |
| Trojan.InstallMonster.28 | 9652 | 1.02 |
| Trojan.LoadMoney.225 | 9601 | 1.02 |
| Trojan.Fraudster.502 | 9178 | 0.97 |
| BackDoor.Maxplus.24 | 8910 | 0.95 |
| Trojan.Fraudster.524 | 8249 | 0.88 |
| Trojan.DownLoader10.56820 | 8089 | 0.86 |
| Trojan.BtcMine.221 | 7965 | 0.84 |
| Trojan.StartPage.56734 | 7322 | 0.78 |
| Trojan.Siggen5.63980 | 6587 | 0.70 |
| Trojan.BPlug.1 | 6385 | 0.68 |
| Trojan.BPlug.4 | 6111 | 0.65 |
| Win32.HLLP.Neshta | 5705 | 0.61 |
| BackDoor.Andromeda.178 | 4712 | 0.46 |
Botnets
December 2013 saw the expansion of the botnet created with the file infector Win32.Rmnet.12. Its first subnet, monitored by Doctor Web's analysts, gained about 20,000 newly infected computers daily, which is 5,000 more than the November figures. The botnet's growth can be traced on the diagram below.
The Win32.Rmnet.12 botnet’s growth in December 2013 (1st subnet)
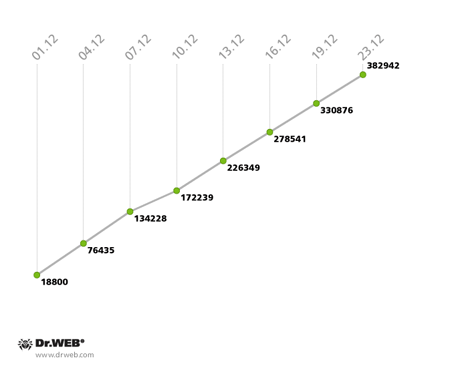
In the second subnet, Win32.Rmnet.12, the growth rate remained the same: as in the previous month, 12,000 newly infected computers connected to the subnet every 24 hours.
The Win32.Rmnet.12 botnet’s growth in December 2013 (2nd subnet)
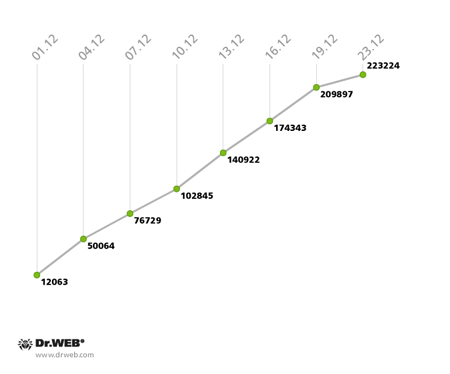
The number of machines on which Dr.Web anti-virus software is detecting the malware module Trojan.Rmnet.19 decreased significantly—from 3,345 bots at the end of November to 2,607 in the last week of December. Also in December, the botnet BackDoor.Bulknet.739 virtually ceased to exist. At the end of November, it included a total of 1,270 infected computers, but by December 23 their number had fallen to 121. It should also be noted that the botnet comprised of Macs infected with BackDoor.Flashback.39 is losing its bulk rather slowly—in December, it included 28,829 infected hosts which was 4,110 Macs fewer than in the previous month.
The threat of the month
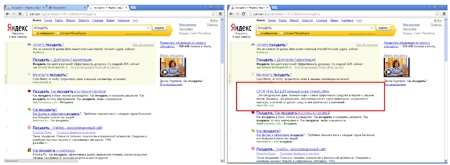
In December, Doctor Web's analysts examined the malware Trojan.Zadved.1 whose first samples were added to the virus database in early November. The Trojan is disguised as a browser extension for secure web surfing, but it performs the exact opposite function.
After completing the installation, it appears on the list of browser extensions and downloads several scripts from remote servers to carry out malicious tasks. One of the scripts generates fake search results containing links to third-party sites.
Another script displays a fake message pop-up supposedly from vk.com. And, apparently, in order to make the ruse appear more credible, attackers display similar messages only if the victim browses a web page on the site vk.com. In addition, the Trojan replaces vk.com ads with those of its own. Another script makes use of click-under advertising: whenever a user clicks somewhere on the web page, the script opens a new browser window to load a website advertised by hackers.
Mining month
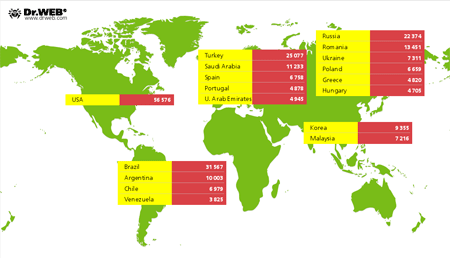
December was fairly prolific in terms of new malignant programs that mine bitcoins and litecoins. In that regard, in early December, Doctor Web's analysts added the signature of Trojan.BtcMine.221, which is distributed from several malignant sites in the guise of browser extensions for online shopping, to the virus database. The program's developers claim that the extension, whose title is Shopping Suggestion, automatically acquires information about the goods users are viewing in their browsers and searches the Internet for the same goods at lower prices. Also, this Trojan is often disguised as other applications such as the VLC player or software for anonymous surfing on the Internet. In fact, Trojan.BtcMine.221 mines litecoin by using a computer’s hardware resources without the user's knowledge. When the Trojan was discovered, the bot had already been installed 311,477 times. Its distribution is illustrated on the image below. More information about this program can be found in a corresponding review from Doctor Web.
Another miner Trojan analysed by Doctor Web in December was added to the database as Trojan.BtcMine.218. Curiously, the program’s authors left their 'signatures' in the debug information. Trojan.BtcMine.218 installer is written in AutoIt, and its code contains the following strings:
FILEINSTALL("C:\Users\Antonio\Desktop\Glue\SmallWeatherSetup.exe", @TEMPDIR & "\Setup_1.exe")
FILEINSTALL("C:\Users\Antonio\Desktop\Glue\Install.exe", @TEMPDIR & "\Setup_2.exe")
And the Trojan's code ends with this line:
c:\Users\Кошевой Дмитрий\Documents\Visual Studio 2012\Projects\Miner\Instal\obj\Debug\Instal.pdb
Finally, in late December, Doctor Web published a review that concerned a new program in the Trojan.Mods family that was dubbed Trojan.Mods.10. The main distinguishing feature of this malware, compared with its predecessors, is a bitcoin mining component. Trojan.Mods.10 is chiefly designed to replace web pages visited by users with malicious web pages by intercepting the system functions responsible for translating DNS names to IP addresses.
It should be noted that the upsurge in mining malware is by no means accidental because such Trojans yield a significant profit for their authors. According to information gathered by Doctor Web's analysts, the daily illegal income obtained from Trojan.BtcMine.221 amounts to 1,454,350 U.S. dollars.
Threats to Android
The last month in 2013 was rather stressful for Android and witnessed the emergence of a variety of new spying Trojans and other dangerous programs that came as unpleasant surprises on the eve of the Christmas and New Year’s holidays.
In particular, the Dr.Web virus database in December acquired more than a dozen entries for malicious applications belonging to the families Android.SmsSpy and Android.Spy. Most of these were being distributed in South Korea by means of unwanted SMS messages containing links to download the Trojans. Compared to the previous month, the number of such SMS bulk dispatches increased by 18% and reached 132 reported incidents. South Korean users most frequently encountered threats from Android.Spy.45.origin (51% of cases), Android.SmsSpy.51.origin (19%), as well as from Android.SmsSpy.53.origin (9%) and Android.Spy.67 (9%). The percentage of identified malware is shown on the following diagram.
Android malware spread in December in South Korea via SMS spam
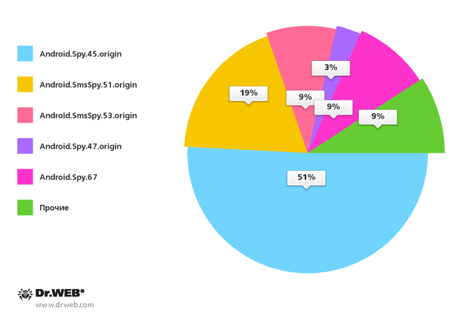
The discovery of the Trojan WhatsAppCopy on Google Play in December was no less remarkable. This program steals the message history from the popular messenger service WhatsApp for the Android OS. This program entered the Dr.Web virus database as Android.WhatsappSpy.1.origin. It was disguised as a game that covertly uploaded the messenger's database containing the message history to the server controlled by the Trojan's author. The program also transmitted images and the phone number associated with the user's account to the server.
Later, anyone could get access to the correspondence of a user they were interested in. They just had to enter a corresponding mobile number on the Trojan maker's site. Despite the fact that the application was positioned as a harmless backup tool for WhatsApp messages, the risk involving unauthorised use of the collected data forced Google to remove this program from Google Play. However, it is still available for downloading from the developer's official site, so many users run the risk of becoming targets of espionage.
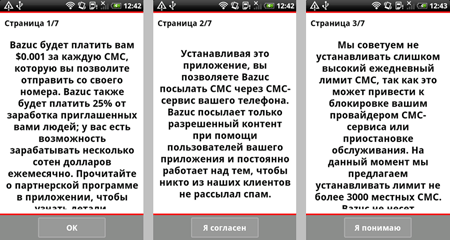
Another incident, widely publicised in online outlets, involved the emergence of the application Bazuc on Google Play. It enabled users to make a profit by allowing the program to send advertising messages and notifications via SMS from their device. The program's developer claimed that the program was meant for subscribers who use service packages providing unlimited outgoing SMS, however, the application never checked whether the package did provide unlimited SMS capability, so users ran the risk of ending up with enormous bills or being disconnected from the carrier's network because Bazuc could send thousands of messages in 24 hours. In addition, the fact that Bazuc's SMS to the target audience came directly from a number belonging to an adventurous subscriber could also lead to unpleasant consequences: recipients of the advertising message could get annoyed to the point that they, for example, call the number and, in the best case scenario, angrily take out their frustration to the newbie spammer.

This program was also removed from Google Play but can still be downloaded from the developer's official site. Considering the potential risks, Doctor Web decided to add the application to the virus database as Program.Bazuc.1.origin, so it poses no threats to devices protected by Dr.Web anti-viruses for Android.
Malicious files detected in mail traffic in December
| 1 | Trojan.Packed.25101 | 1.34% |
| 2 | Trojan.DownLoader9.22851 | 1.01% |
| 3 | Trojan.DownLoad3.30075 | 0.92% |
| 4 | Trojan.DownLoad3.28161 | 0.75% |
| 5 | Trojan.DownLoad3.30703 | 0.74% |
| 6 | Trojan.Inject2.23 | 0.69% |
| 7 | Trojan.DownLoader9.4034 | 0.65% |
| 8 | BackDoor.Comet.152 | 0.60% |
| 9 | Trojan.PWS.Panda.547 | 0.54% |
| 10 | Trojan.DownLoad.64746 | 0.54% |
| 11 | Trojan.PWS.Panda.4795 | 0.50% |
| 12 | BackDoor.Kuluoz.4 | 0.44% |
| 13 | Trojan.Fraudster.517 | 0.44% |
| 14 | Trojan.DownLoader9.3975 | 0.44% |
| 15 | Win32.HLLM.MyDoom.33808 | 0.42% |
| 16 | Trojan.PWS.Panda.2401 | 0.42% |
| 17 | BackDoor.Maxplus.13026 | 0.37% |
| 18 | Tool.MailPassView.225 | 0.30% |
| 19 | Trojan.PWS.Panda.5660 | 0.25% |
| 20 | Trojan.DownLoader10.62084 | 0.23% |
Malicious files detected on user computers in December
| 1 | Trojan.InstallMonster.38 | 0.75% |
| 2 | Trojan.Fraudster.524 | 0.73% |
| 3 | Trojan.DownLoader10.56820 | 0.69% |
| 4 | Trojan.LoadMoney.1 | 0.64% |
| 5 | Trojan.Fraudster.502 | 0.55% |
| 6 | BackDoor.IRC.NgrBot.42 | 0.46% |
| 7 | BackDoor.PHP.Shell.6 | 0.40% |
| 8 | Trojan.Packed.24524 | 0.37% |
| 9 | Win32.HLLW.Shadow | 0.33% |
| 10 | Trojan.StartPage.57459 | 0.32% |
| 11 | Trojan.Fraudster.589 | 0.31% |
| 12 | Win32.HLLW.Autoruner.59834 | 0.30% |
| 13 | Trojan.MulDrop4.25343 | 0.27% |
| 14 | Trojan.Packed.2782 | 0.26% |
| 15 | Trojan.SMSSend.4196 | 0.25% |
| 16 | Trojan.Hosts.6838 | 0.24% |
| 17 | Trojan.Fraudster.430 | 0.24% |
| 18 | Trojan.Packed.24814 | 0.23% |
| 19 | Trojan.DownLoader10.57920 | 0.22% |
| 20 | Trojan.LoadMoney.225 | 0.22% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live