Trojan.Skimer.18 infects ATMs
Real-time threat news | Hot news | All the news | Virus alerts
December 16, 2013
Trojan.Skimer.18 is by no means the first backdoor to infect ATM software, but it is the first to target devices so common throughout the world. The malicious program is implemented as a dynamic link library loaded by an infected application. When launched, the backdoor picks the name for the log file that will contain the stolen information about transactions.
Then Trojan.Skimer.18 stands by for a user authorisation, after which it reads and saves the Track 2 data (which includes the card/account number, expiry date, and service code) and the PIN code into its log file. It is noteworthy that in order to maintain confidentiality, ATM manufacturers employ a special technology that facilitates the encrypted transmission of PIN codes entered into ATMs, and the encryption key is regularly updated from the bank's server. Trojan.Skimer.18 bypasses this protection and uses the ATM's software to decrypt PIN codes.
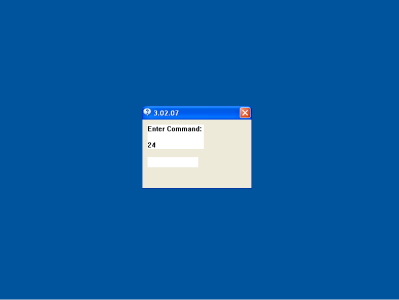
As in earlier versions of similar Trojans, specifically designed master cards are used to control the program. Once an infected ATM recognizes the master card in the reader, it will display a Trojan dialogue box. The XFS (Extensions for Financial Services) interface is used to facilitate interaction with the intruding operator. Since ATMs do not feature a fully functional PC keyboard, the Trojan uses the XFS interface to intercept encrypted PIN-pad input and displays the entered data in its window.
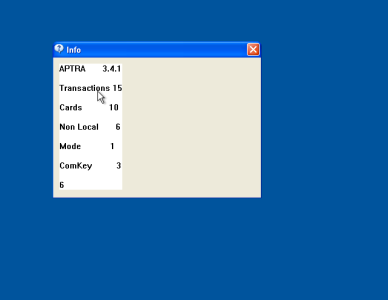
At the criminals’ command, Trojan.Skimer.18 can "cure" an infected ATM, display statistics on stolen data, delete the log file, restart the ATM, change its operation mode or update itself (or just the malicious library) by running the appropriate application from the master card's chip. The hardware indicators, the reader and the process indicator on the screen are used to show that updating is in progress.
Stolen information is also written onto the master card's chip upon a corresponding command from the operator. Prior to writing onto the master card, data from the log file undergoes two-stage compression.
This backdoor is so similar to other malignant programs targeting ATMs that one can assume that all these programs have been written by the same person. The signature of Trojan.Skimer.18 has been added to the virus databases, and the program is successfully detected and neutralised by Dr.Web software.