Virus activity review for July 2009 from Doctor Web
Virus reviews | All the news
July 31, 2009
Doctor Web presents the virus activity review for July 2009. New exploits for Windows and several popular applications became the main trend of the past month . Even though in July malicious code was least likely to be found in e-mails, cyber-criminals never stopped adopting new techniques to attract attention of users to their messages.
JS.Gumblar
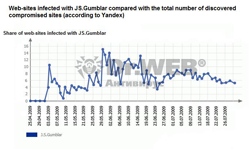
The six month review from Doctor Web provided information about this severe threat and the high rate of spreading of JS.Gumblar. In July it came to Russia (see the graph below).
As you can see it reached its peak of activity on May 28 with 13.7% of compromised web-sites infected by JS.Gumblar. Now its spreading rate is declining but it still poses threat to web-resources.
FlashBack
Mid-July 2009 was marked by unexpected surge in malicious activities of several modifications of Win32.HLLM.MyDoom which were among most common viruses in the wild in 2004!
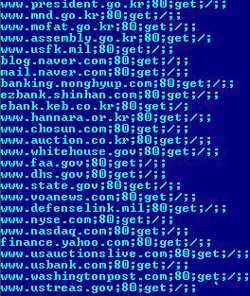
Now they are used to carry out DDoS attacks on South Korean and American web-sites. Below you can see the dump of strings constants from the configuration file of a component of the virus that performed a DDoS attack (detected by Dr.Web as DDoS Config).
The number of compromised machines used for attacks has reached dozens of thousands. Attacked web-resources include sites of various governmental institutions of the United States and South Korea: whitehouse.gov, nsa.gov, president.go.kr and many others. Modifications of Win32.HLLM.MyDoom spread mainly in spam attachments and it turns out that the threat of days departed leaved up to the present and managed to become a nuisance in our days.
Mobile botnet
A worm for the mobile platform Symbian Series 60 3rd Edition was discovered in July It spreads as a piece of software offered for downloading on web-sites. Devices infected with the worm send SMS-spam using a contact list found on the device. The body of such an SMS contains intriguing test prompting a user to follow a link that points to the web-site that spreads the virus .
The threat is assigned to the new Symbian.Worm family. Dr.Web anti-viruses detect it as Symbian.Worm.1.
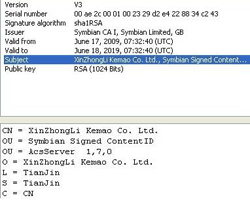
It should also be noted that the worm installer is signed by Symbian Signed portal. This certificate has already been revoked by Symbian. See the corresponding post in the company blog.
Symbian.Worm.1 steals user personal data and sends it to a remote server. The worm can update its message templates using an established internet connection. So it works as a mobile botnet with bots able to communicate with cyber-criminals and provide them with personal information collected on infected devices.
Exploits
In the first two weeks of July a severe “zero day” vulnerability was found in a component of Microsoft DirectX used by Internet Explorer 6 and 7. Vulnerable operating systems include 2000/2003/XP with all released updates installed (including x64 versions of the systems) incorreect procession of a video stream by the msVidCtl.dll component of ActiveX can be used to spread malicious programs from web-sites that cause stack overflow and launch a malicious program on the target machine. All exploits of this vulnerability are members of the Exploit.DirectShow family.
A similar vulnerability was found in an ActiveX component of Office Web Components Spreadsheet. The cause of the vulnerability is incorrect data bounds check in msDataSourceObject(). Under the Dr.Web classification all exploits of this type belong to the Exploit.SpreadSheet family.
Virus-makers didn’t leave the last version of Firefox unnoticed either. A java-script execution error that could damage the memory of the Just-in-Time compiler after its functions returned data has been discovered in the second week of July. All exploits of this type belong to the Exploit.Mozilla family under the Dr.Web classification.
By the end of July a zero-day vulnerability was found in Adobe products (Reader, Acrobat и Flash Player). The authplay.dll file that processed SWF-files turned out to be vulnerable. The vulnerability can be exploited when one opens a special PDF-document or simply visits malicious web-sites that exploit the vulnerability. All detected malicious PDF files are included in the Exploit.PDF family. As of the review date the vulnerability has not been closed.
All vulnerabilities listed above are used by cyber-criminals to spread malware from bogus web-sites.
Security updates closing all the vulnerabilities are already available. Doctor Web strongly recommends installing updates for corresponding applications.
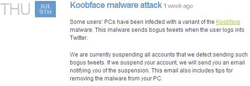
Win32.HLLW.Facebook worm in Twitter
July also saw increased activity of Win32.HLLW.Facebook (Koobface) in Twitter.
Creators of the social networking web-site posted a corresponding warning in their blog.
Doctor Web virus analysts found out that there were few differences between modifications Win32.HLLW.Facebook and they all had the same basic functions. This allowed Doctor Web to ensure reliable detection of variations of Win32.HLLW.Facebook using Origins Tracing. Now most new modifications of the malicious program are detected as Win32.HLLW.Facebook.origin.
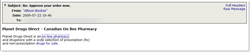
Trojan.Winlock
Trojan horses that block access to the desktop in Windows were also found in abundance in the wild. Yet again Trojans disguised as anti-viruses came into the spotlight.
Mail viruses and phishing
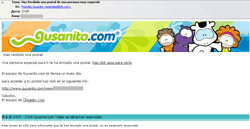
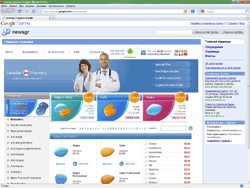
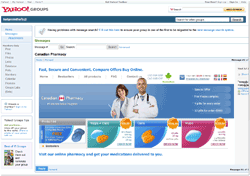
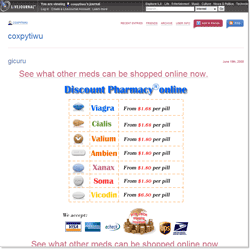
It has already been mentioned that few cases of spreading malware via e-mail were registered in July. At the same time the number of spam messages promoting health-care products has increased. Spammers also made their ads available to a wide audience using Google Groups, Yahoo Groups, LiveJournal services.
 |
 |
 |
 |
 | |
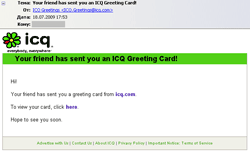
IRC.Flood.702 spread as an e-card from an ICQ user turned out to be the only malicious program distributed using spam messages.
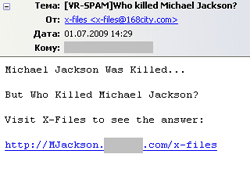
The death of Michael Jackson also was a too notable event for cyber-criminals not to take advantage of. Messages supposedly containing exclusive information about this event provided would-be-victims with a link to a web-site spreading Trojan.PWS.Panda.122.
BAT.Hosts malicious programs were offered to users as e-cards. Such programs added several strings to the hosts file so a user willing to visit certain web-sites was redirected to phishing resources target customers of Spanish banks. Messages informing users about an “e-card” were also in Spanish.
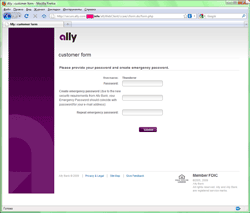
Traditionally targets of phishing attacks also included eBay users and customers that use the America Online banking system. Customers of Comerica Bank, Ally Bank and USAA also became victims of phishing attacks in July.
 |
 |
 | |
Viruses detected in e-mail traffic in July
| 01.07.2009 00:00 - 31.07.2009 00:00 | ||
| 1 | Win32.HLLM.Netsky.35328 | 8166826 (22.65%) |
| 2 | Win32.HLLM.Beagle | 5909675 (16.39%) |
| 3 | Trojan.DownLoad.36339 | 5504479 (15.27%) |
| 4 | Trojan.PWS.Panda.122 | 2103096 (5.83%) |
| 5 | Win32.HLLM.MyDoom.based | 1982009 (5.50%) |
| 6 | Trojan.Botnetlog.9 | 1813173 (5.03%) |
| 7 | Win32.HLLM.MyDoom.33808 | 1418521 (3.93%) |
| 8 | Trojan.MulDrop.19648 | 1369527 (3.80%) |
| 9 | Win32.HLLM.MyDoom.44 | 1071356 (2.97%) |
| 10 | Win32.HLLM.Netsky | 742919 (2.06%) |
| 11 | Win32.HLLM.Beagle.32768 | 722449 (2.00%) |
| 12 | Trojan.MulDrop.13408 | 658883 (1.83%) |
| 13 | Win32.HLLM.Perf | 587196 (1.63%) |
| 14 | Win32.HLLM.MyDoom.49 | 561190 (1.56%) |
| 15 | Win32.HLLM.Beagle.27136 | 476340 (1.32%) |
| 16 | Win32.HLLM.Netsky.based | 444932 (1.23%) |
| 17 | Exploit.IframeBO | 443541 (1.23%) |
| 18 | Exploit.IFrame.43 | 360002 (1.00%) |
| 19 | Trojan.PWS.Panda.114 | 335392 (0.93%) |
| 20 | W97M.Dig | 238968 (0.66%) |
| Total scanned: | 137,012,732,015 |
| Infected: | 36,051,605 (0.0263%) |
Viruses detected on user machines in July
| 01.07.2009 00:00 - 31.07.2009 00:00 | ||
| 1 | Trojan.DownLoad.36339 | 2503920 (10.23%) |
| 2 | Win32.HLLM.Beagle | 2334712 (9.54%) |
| 3 | Trojan.WinSpy.176 | 1304339 (5.33%) |
| 4 | Win32.Virut.14 | 1171115 (4.78%) |
| 5 | Win32.HLLW.Gavir.ini | 1163586 (4.75%) |
| 6 | Win32.HLLM.Netsky.35328 | 1027107 (4.20%) |
| 7 | Trojan.WinSpy.180 | 971590 (3.97%) |
| 8 | Win32.HLLM.MyDoom.49 | 899655 (3.68%) |
| 9 | Trojan.MulDrop.16727 | 799252 (3.27%) |
| 10 | Trojan.PWS.Panda.122 | 666798 (2.72%) |
| 11 | Trojan.Botnetlog.9 | 587117 (2.40%) |
| 12 | Win32.HLLW.Shadow.based | 584087 (2.39%) |
| 13 | Trojan.WinSpy.160 | 513468 (2.10%) |
| 14 | Win32.HLLM.MyDoom.33808 | 494072 (2.02%) |
| 15 | Win32.Sector.17 | 383420 (1.57%) |
| 16 | Win32.Alman | 381582 (1.56%) |
| 17 | DDoS.Kardraw | 379553 (1.55%) |
| 18 | Win32.HLLM.Netsky.based | 343624 (1.40%) |
| 19 | W97M.Hana | 283978 (1.16%) |
| 20 | Win32.HLLW.Autoruner.5555 | 267185 (1.09%) |
| Total scanned: | 210,224,776,255 |
| Infected: | 24,478,202 (0.0116%) |