Infected sites distributing Trojan that generates fake search results
Real-time threat news | Hot news | All the news | Virus alerts
November 13, 2013
Information security experts and users who have fallen victim to cybercriminals are quite familiar with the issue of fake search engine results. This feature is implemented in many malicious programs. Once such a Trojan is Installed on a victim's computer, it can monitor the activity of web browsers and replace search results with links to a variety of bogus sites whenever users seek the aid of search engines. Trojan.Hiloti belongs to this category of malware. Some members of this family appeared in the wild as early as in 2010. To date, the Dr.Web virus database has more than 80 entries corresponding to different versions of this threat. Security experts believe that the emergence of new Trojan.Hiloti modifications is connected with the introduction of the affiliate programme Podmena-2014 to which attackers are trying to attract malware distributors.
Virus writers approach website owners with an offer to place a special script on their sites that will download the Trojan.Hiloti executable at specific intervals. A rootkit module that conceals the operation of the malignant program in an infected system is distributed with the Trojan installer. To complicate the detection of Trojan.Hiloti, the Trojan executable is repacked on the criminals' server at periodic intervals.
The vulnerabilities CVE-2012-4969, CVE-2013-2472, CVE-2013-2465 and CVE-2013-2551 are exploited and social engineering techniques are used to facilitate the downloading of the Trojan on target machines.
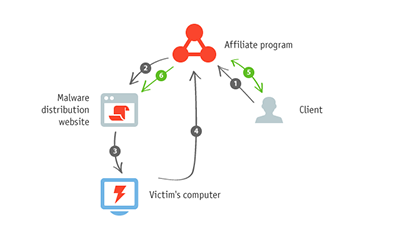
1 - A customer enters into an agreement with the affiliate programme’s organizers to promote certain URLs. 2 - The affiliate programme’s organisers deliver malware to distributors who make sure it can be downloaded from various sites. 3 - When users visit such sites, their computers get infected with the malware. 4 - When the users resort to the help of search engines, they end up clicking on links displayed by the malicious software in the browser window. The information is transmitted to the affiliate programme’s organisers. 5 - The customer pays the affiliate programme’s organisers for clicks on the links. 6 - The malware distributors get their portion of these funds.
Attackers offer malware distributors a relatively simple scheme of work: they facilitate the installation of Trojan.Hiloti on users' computers by embedding certain pieces of code on the sites under their control. After that, whenever users of infected systems try to search the web, instead of the expected search results, the Trojan will display links to sites whose advertisement has been paid for. Sometimes opening such links results in downloading various unwanted applications, such as fake anti-viruses that require payment to "cure" the computer. Distributors get their share of the income gained by criminals under the affiliate programme.
Despite all the tricks of virus writers, Trojans of the Trojan.Hiloti family are detected by Dr.Web, so users who have installed Doctor Web software on their computers can rest assured that their systems are protected from this threat. However, users are advised to be vigilant. Do not save or run executable files downloaded from suspicious sites, and be sure to install timely updates for your operating system and the applications you use.