October 2013 virus activity overview
Virus reviews | Hot news | All the news | Virus alerts
November 5, 2013
Viruses
Statistics collected in October by Dr.Web CureIt! indicate that the downloader Trojan.LoadMoney.1 tops the list of detected threats. One of its modifications, which is dubbed Trojan.LoadMoney.76, is also among the leaders. Quite a number of computers are infected with Trojan.Hosts.6815 which modifies the hosts file to redirect a browser to fraudulent and phishing sites. The downloader Trojan.InstallMonster.28 and the advertising malware Trojan.Lyrics.11 are also among the most frequently detected programs. The 20 most common threats detected by Dr.Web CureIt! in October are listed in the following table:
| Name | Quantity | % |
|---|---|---|
| Trojan.LoadMoney.1 | 4794 | 3.84 |
| Trojan.Packed.24524 | 3716 | 2.98 |
| Trojan.LoadMoney.76 | 3237 | 2.60 |
| Trojan.Hosts.6815 | 2192 | 1.76 |
| Trojan.InstallMonster.28 | 2061 | 1.65 |
| Trojan.Lyrics.11 | 1441 | 1.16 |
| Trojan.InstallMonster.33 | 1226 | 0.98 |
| Win32.HLLP.Neshta | 1192 | 0.96 |
| BackDoor.Andromeda.178 | 982 | 0.79 |
| Trojan.Fraudster.524 | 961 | 0.77 |
| BackDoor.IRC.NgrBot.42 | 947 | 0.76 |
| Trojan.Winlock.8811 | 881 | 0.71 |
| BackDoor.Maxplus.24 | 878 | 0.70 |
| Trojan.Hosts.6838 | 862 | 0.69 |
| Win32.Sector.22 | 829 | 0.66 |
| VBS.Rmnet.2 | 777 | 0.62 |
| Trojan.Fraudster.502 | 738 | 0.59 |
| Win32.HLLW.Gavir.ini | 710 | 0.57 |
| Trojan.Crossrider.1 | 708 | 0.57 |
| Trojan.DownLoader9.19157 | 683 | 0.55 |
Botnets
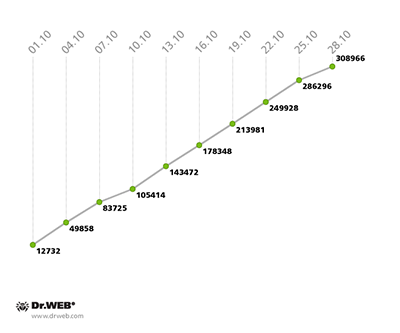
Compared to September, the botnet comprised of computers infected with the file infector Win32.Rmnet.12 file showed an almost unchanged growth rate, with an average of 15,000 newly infected PCs joining the first subnet and 11,000 computers connecting to the second one on a daily basis. The change in numbers of Wind32.Rmnet.12 bots in October 2013 can be traced on the graph below.
Win32.Rmnet.12 botnet growth in October 2013 (1st subnet)
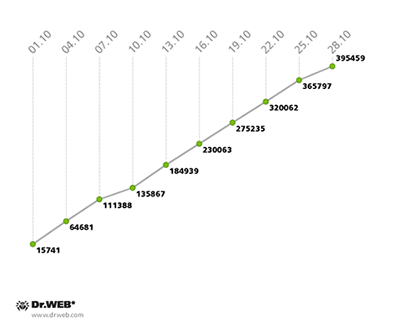
Win32.Rmnet.12 botnet growth in October 2013 (2nd subnet)
The number of computers on which anti-virus software is detecting Trojan.Rmnet.19 has continued to decline: while at the beginning of October, 4,640 hosts were infected with the malware, by the end of the month that number dropped to 3,851.
The size of the BackDoor.Bulknet.739 botnet didn't change: as of October 28, the network was comprised of 1,539 infected computers.
The number of Macs infected with BackDoor.Flashback.39 is gradually decreasing. At the end of September, the number of infections was 38,288, and a month later it dropped to 31,553.
Threats to Android
Last month, Doctor Web's analysts discovered several new malignant applications that steal confidential data from Android users. For example, Android.Spy.40.origin, Android.Spy.49.origin and Android.SmsForward.14.origin have been targeting South Korean users. Criminals have been spreading these programs by sending SMS messages containing links for downloading malicious apk files. Cybercriminals adopted this spreading technique a long time ago, and its popularity is steadily increasing, which suggests its relatively high efficiency.
Like many similar malware programs, these Trojans are able to intercept incoming SMS messages, which may contain various valuable information, including one-time mTAN codes and other transaction details, as well as personal or business correspondence. However, in this case, the program Android.Spy.40.origin, which exploits an Android error to avoid being scanned by anti-viruses, is the most interesting one. To achieve this, attackers only had to modify the Trojan apk package so that it could successfully bypass scanning. More detailed information about this threat can be found in a corresponding publication on Doctor Web's site.
The discovery of a multi-purpose Trojan dubbed Android.Zoo.1.origin became another notable event in October. It was spread via a Chinese site as part of a popular game that had been modified by cybercriminals. Once on a mobile device, Android.Zoo.1.origin gathers contact information found in the phone book and uploads it to a remote server. It can also download and install other malicious applications, have messages sent to premium-rate numbers and open web pages in a browser.
October also saw new versions of Android.SmsSend and Android.SmsBot which can send SMS messages to premium numbers. In the past month, entries for several members of these malware families were added to the Dr.Web virus database. They include Android.SmsSend.853.origin, Android.SmsSend.888.origin and Android.SmsBot.7.origin, which spread under the guise of popular applications and their installers.
Other events in October
Upatre spreads CryptoLocker with banking Trojan Gameover ZeuS
There has been a development to the situation, described on October 10 by Dell SecureWorks, concerning the Gameover ZeuS Trojan being spread with the help of a Trojan downloader. Security experts have discovered that the Trojan CryptoLocker, which extorts money from users to decrypt data on infected machines, is spread with the downloader, too.
The program, which is from the Trojan.DownLoad family, is a small file that simply downloads other malware onto an infected host. Disguised as a zip or pdf file, it is distributed as an attachment in spam messages. As soon as a user opens such an attachment, malware (first, Zbot/ZeuS banking Trojans, and now CryptoLocker, too) is downloaded to the computer. This encoder not only blocks access to the system, but also forces the user to pay up for the decryption of files.
Security experts examined a sample of this type of spam message. The malicious attachment contains a Trojan.DownLoad program that downloads Trojan.PWS.Panda. It is actually this program that downloads CryptoLocker.
Thus, a user whose computer is infected with these malicious programs risks losing not only their online bank account information and money due to unauthorized transactions but also other files encrypted by CryptoLocker. The complexity of the encryption method employed by malware makes it impossible for a user to restore their files on their own.
CryptoLocker is detected by Dr.Web as Trojan.Encoder.304 (a sample was added to the virus database on October 25, 2013).
Systems with installed Dr.Web software are protected from these threats. Nevertheless, these malicious programs pose a severe danger, so Doctor Web recommends that users observe extra precautions: do not open attachments to emails received from untrusted sources. Avoid opening links that haven't been checked. Back up your files regularly. Use legal copies of software and update them promptly.
Dexter: new threats to cardholders
A new version of the Dexter malware has caused multi-million dollar damages to the majority of South African banks. Hundreds of thousands of credit and debit cards have been compromised. Dexter infects computers connected to POS terminals in retail chains and restaurants, steals card data from the computer memory, and encrypts and uploads it to the intruders' server.
According to security researchers, Dexter was identified as early as 2012. Modifications of the Trojan are also known as Alina, BlackPOS, and Vskimmer. Hundreds of terminal computers in 40 countries were infected within a few months. Most of the infected systems were found in North America and the UK.
Samples of this malware are detected by Dr.Web as Trojan.Packed.23683, Trojan.Packed.23684 and Trojan.Packed.23685. They were added to the virus database on September 27, 2012.
P2P Zeus mailing: the address is known
Numerous websites that track samples of spam and phishing emails are reporting on the spread via spam in early October of new versions of malware (presumably the banking Trojan P2P Zeus). According to a major Australian site, the specified spam got into over 135,000 mailboxes.
Scammers take advantage of SMTP features to send out emails with forged sender addresses. It is assumed that their real address is fraud@aexp.com, registered on a server located in the region of Trinidad and Tobago with an IP address of 190.213.190.211. For subject headers of messages (sent allegedly from government agencies, banks, etc.), criminals indicate the names of financial statements, security warnings, etc., to incite a potential victim to avoid material losses by opening the attachment.
Attachments to such emails (disguised as *. zip or *. pdf files) are executable files. When one opens the attachment, one of the following versions of the Trojan is downloaded: Trojan.DownLoad3.28161, Trojan.DownLoader10.16610, Trojan.Inject1.27909 (all names appear as recorded in the Dr.Web virus database).
It has been suggested that the malware downloads the banking Trojan P2P Zeus onto compromised machines.
Samples of Trojan.DownLoad3.28161, Trojan.DownLoader10.16610, and Trojan.Inject1.27909, spread with this mailing, were added to the Dr.Web virus database on October 9 and 10, 2013.
P2P Zeus malware is detected by Dr.Web as Trojan.PWS.Panda.4379. This banking Trojan is one of the most common programs of this kind. It transmits bank account information to criminals, steals keys and passwords used by various programs, logs keystrokes, takes screenshots, acts as a bot, executes commands from a malicious server, and redirects the victim to fake (phishing) websites on which attackers can steal confidential information. Doctor Web's analysts believe that the spam campaign is targeting customers of different banks. To avoid danger, users are advised to refrain from opening attachments to emails received from suspicious sources. Never open suspicious links. Protect your device with anti-virus software and update it promptly.
Malicious files detected in mail traffic in October
| 01.10.2013 00:00 - 31.10.2013 23:00 | ||
| 1 | Trojan.DownLoad3.28161 | 1.02% |
| 2 | Trojan.Packed.24872 | 0.77% |
| 3 | Trojan.DownLoader9.22851 | 0.70% |
| 4 | Trojan.Packed.3036 | 0.68% |
| 5 | BackDoor.Maxplus.13275 | 0.60% |
| 6 | Trojan.PWS.StealerENT.3243 | 0.56% |
| 7 | Trojan.Click2.22983 | 0.51% |
| 8 | Trojan.PWS.Panda.547 | 0.49% |
| 9 | Trojan.PWS.Panda.2401 | 0.48% |
| 10 | Trojan.PWS.Multi.911 | 0.44% |
| 11 | Trojan.PWS.Panda.4795 | 0.41% |
| 12 | BackDoor.Comet.152 | 0.39% |
| 13 | Trojan.DownLoader10.34549 | 0.39% |
| 14 | Win32.HLLM.MyDoom.33808 | 0.37% |
| 15 | Trojan.Fraudster.517 | 0.34% |
| 16 | Trojan.Packed.24612 | 0.32% |
| 17 | BackDoor.Maxplus.13119 | 0.32% |
| 18 | BackDoor.Blackshades.17 | 0.31% |
| 19 | Trojan.PWS.Panda.4379 | 0.31% |
| 20 | Win32.HLLM.Beagle | 0.29% |
Malicious files detected on user computers in October
| 01.10.2013 00:00 - 31.10.2013 23:00 | ||
| 1 | Exploit.SWF.254 | 0.98% |
| 2 | Trojan.Fraudster.524 | 0.57% |
| 3 | Trojan.LoadMoney.76 | 0.54% |
| 4 | Trojan.Packed.24524 | 0.53% |
| 5 | BackDoor.PHP.Shell.6 | 0.48% |
| 6 | Trojan.LoadMoney.1 | 0.47% |
| 7 | Trojan.Fraudster.502 | 0.37% |
| 8 | BackDoor.IRC.NgrBot.42 | 0.33% |
| 9 | Trojan.Fraudster.394 | 0.31% |
| 10 | Trojan.InstallMonster.33 | 0.30% |
| 11 | Win32.HLLW.Shadow | 0.28% |
| 12 | Trojan.SMSSend.4196 | 0.27% |
| 13 | Win32.HLLW.Autoruner.59834 | 0.27% |
| 14 | Trojan.MulDrop5.1740 | 0.27% |
| 15 | Trojan.Winlock.9260 | 0.26% |
| 16 | Trojan.MulDrop4.25343 | 0.26% |
| 17 | Trojan.InstallMonster.34 | 0.25% |
| 18 | Trojan.InstallMonster.28 | 0.24% |
| 19 | JS.Redirector.194 | 0.24% |
| 20 | Trojan.LoadMoney.188 | 0.23% |