September 2013 Virus Activity Overview
Virus reviews | Hot news | All the news | Virus alerts
October 1, 2013
Viruses
According to statistics collected by Dr.Web CureIt!, in September 2013, Trojan.LoadMoney.1 leads among the most frequently detected malware on users' computers. This application is used to download files that are automatically generated under the affiliate program Loadmoney. Trojan.Hosts.6815 ranks second. This sinister program modifies the hosts file to redirect the user's browser to fraudulent or phishing sites. Trojan.InstallMonster.28 ranks third. It is another file downloader, but this one gets files under the affiliate program Installmonster. They are followed by an advertising Trojan dubbed Trojan.Packed.24524 and Trojan.Mods.3 which is designed to replace loaded pages in a browser window. The 20 most relevant threats discovered on computers by Dr.Web CureIt! in September are listed in the table below.
| Name | Quantity | % |
|---|---|---|
| Trojan.LoadMoney.1 | 16987 | 3.75 |
| Trojan.Hosts.6815 | 11088 | 2.45 |
| Trojan.InstallMonster.28 | 7174 | 1.58 |
| Trojan.Packed.24524 | 6118 | 1.35 |
| Trojan.Mods.3 | 6040 | 1.33 |
| Trojan.MayachokMEM.8 | 5716 | 1.26 |
| Trojan.Fraudster.524 | 4753 | 1.05 |
| Trojan.BtcMine.142 | 4532 | 1.00 |
| Trojan.DownLoad3.26006 | 4467 | 0.99 |
| BackDoor.IRC.NgrBot.42 | 4420 | 0.98 |
| Trojan.Mayachok.18634 | 4288 | 0.95 |
| BackDoor.IRC.Cirilico.119 | 4067 | 0.90 |
| Trojan.Mods.2 | 3985 | 0.88 |
| Trojan.Mods.1 | 3630 | 0.80 |
| BackDoor.Maxplus.24 | 3531 | 0.78 |
| Trojan.DownLoader9.19157 | 3457 | 0.76 |
| Trojan.Hosts.6838 | 3415 | 0.75 |
| Trojan.SMSSend.4196 | 3300 | 0.73 |
| Trojan.MayachokMEM.9 | 3197 | 0.71 |
| Win32.HLLP.Neshta | 3158 | 0.70 |
Botnets
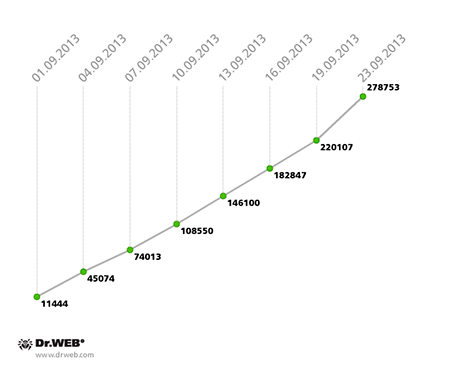
The botnet, consisting of Windows PCs infected with the file virus Win32.Rmnet.12, is still growing. While in August the number of new joiners connecting to one of the Win32.Rmnet.12 subnets on a daily basis approximated 12,000, in September the figure increased to 16,000 infected hosts. The growth of Win32.Rmnet.12 subnet #1 in September 2013 is illustrated in the graph below.
Win32.Rmnet.12 botnet growth in September 2013 (1st subnet)
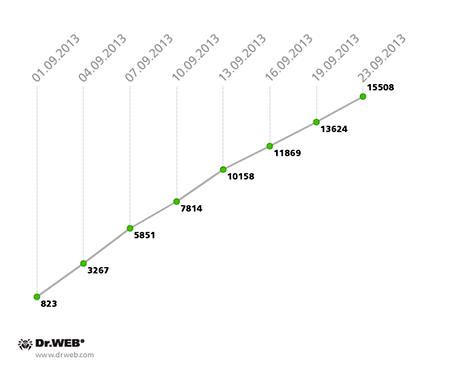
In contrast to the previous month, the average daily number of new joiners in the second Win32.Rmnet.12 subnet also increased slightly—from 10,500 infections in August to 11,500 incidents in September. The growth of the second Win32.Rmnet.12 subnet can be tracked using the following graph.
Win32.Rmnet.12 botnet growth in September 2013 (2nd subnet)
Meanwhile, the botnet comprised of computers compromised by the file infector Win32.Rmnet.16 virtually ceased to grow: in August, its average daily gain was 1,500 infected machines; from September 1-20, the network's daily increase on average didn't exceed 20 infected PCs, and in the last days of the month the growth stopped altogether. The malicious module detected by Dr.Web anti-virus software as Trojan.Rmnet.19 follows a similar pattern: its daily gain of the botnet in September was about 15 infected PCs, and the number of active bots decreased from 5,014 to 4,640.
The BackDoor.Bulknet.739 botnet’s growth rate remained virtually unchanged: as in August, the daily average of infected new joiners reached 500-600 hosts. The BackDoor.Bulknet.739 botnet’s growth is presented in the graph below.
Win32.Rmnet.12 botnet growth in September 2013 (2nd subnet)
The size of the BackDoor.Flashback.39 botnet, comprised of infected Macs, also hardly changed. By the end of August, it consisted of 38,822 hosts, and in late September it shrank by another 534 Macs and encompassed 38,288 compromised machines.
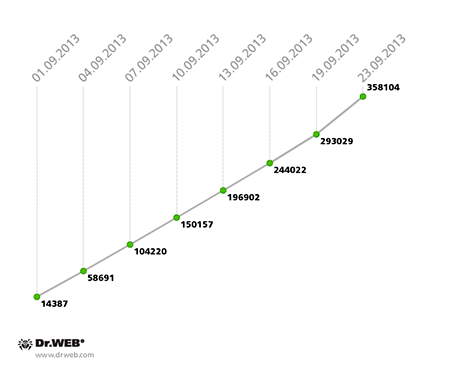
In late September, Doctor Web's virus analysts discovered the largest botnet known to date, consisting of more than 200,000 infected Android devices. Criminals have used several malignant programs to infect devices and hook them onto the botnet: the recently discovered program Android.SmsSend.754.origin, Android.SmsSend.412 (spread as a mobile browser), Android.SmsSend.468.origin (known since April, 2013), and Android.SmsSend.585.origin. The earliest version of the Trojan related to investigation of this incident is Android.SmsSend.233.origin. It was added to the Dr.Web virus database in November 2012. In most cases, websites owned by criminals and those that have been compromised and used to distribute malware are the sources of infection.
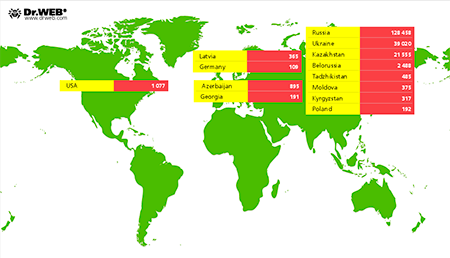
According to information collected by Doctor Web's analysts, to date the botnet includes more than 200,000 mobile devices running Android. Most of them (128,458) belong to Russian users; Ukraine ranks second with 39,020 infection incidents; and Kazakhstan comes in third—21,555 devices were compromised there. The image below provides information about the geographic distribution of the infection.
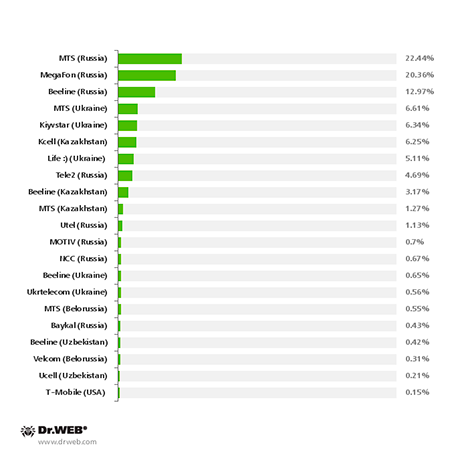
The diagram below shows the distribution of each mobile operator’s infected devices.
This is one of the largest-scale incidents involving the infection of Android devices in the past six months. Preliminary estimates suggest that the damage caused by malware as a result of this incident could amount to hundreds of thousands of dollars.
As of September 25, 2013, this botnet included 226,464 infected Android-powered devices, of which 142,302 were located in Russia, 45,010 were found in Ukraine, 23,608 were known to be in Kazakhstan, and 2,915 resided in Belarus. An average of 2,209 newly infected Android devices connect to the botnet daily.
For more information about this botnet and the malware used by hackers to create it, you can refer to a corresponding review published by Doctor Web.
The threat of the month
In early September, Doctor Web's virus analysts examined the key-logging Trojan dubbed BackDoor.Saker.1. This malignant program can also bypass the UAC protection.
BackDoor.Saker.1 collects information about the compromised system, including the Windows version, CPU frequency, available RAM, computer name, user login and the hard disk serial number, and transmits it to criminals. Next, the Trojan creates a file in a system folder into which user keystrokes are logged. After this, the backdoor awaits a remote server’s response, which may involve commanding the backdoor to reboot, shut down, remove itself, start a separate thread to execute commands via a shell, or even run its own file manager which can upload files from an infected machine, download files via the network, create folders, and delete, move and run files. For more information about this threat, please refer to the review published on Doctor Web's site.
Threats to Android
The first month of autumn 2013 was a rather stressful one for Android and its users. Through the entire month, Doctor Web was identifying a variety of Android malware which included SMS Trojans, fake anti-viruses, Trojans and spyware.
Trojan Android.SmsSend.754.origin is an apk application named Flow_Player.apk. During installation, it prompts the user to run it with administrator privileges—this will allow the malicious application to lock and unlock the screen. In addition, Android.SmsSend.754.origin later hides its icon from the home screen.
Once installed and launched, the Trojan sends various details about the infected device to the attackers and then waits for directives, the main one being to send SMS messages with a specific text to a specified number. Thus infected mobile devices can send any SMS, including expensive messages, regardless of the owner's country of residence or the telephone company they use. This allows botnet makers to not only use the botnet for their own ends but also to conduct criminal activities for third parties. More detailed information about this incident can be found in a corresponding publication at Doctor Web's site.
The benefit cybercriminals get from using SMS Trojans easily explains why malware of this family is so widespread, so it is hardly surprising that the geographical area in which it is being employed is constantly expanding. Thus, In September, Doctor Web's analysts discovered a site inviting Vietnamese users to download bogus games and other applications. The downloads contained Trojans that were subsequently added to the Dr.Web virus database as Android.SmsSend.760.origin.
When launched, the malicious applications send short messages to a premium number, and then open a web browser to download the desired software. However, the trouble did not end there. These resourceful fraudsters modified the programs downloaded later by the user so that when launched, those programs would also send chargeable short messages. That's why some programs are detected by Dr.Web anti-virus software as Android.SmsSend.761.origin.
The malicious program Android.SmsBot.5, discovered in the middle of the month, can be considered a relative of some SMS Trojans. It is distributed under the guise of a social networking client for VKontakte.
Several Android.SmsSpy Trojans spread under the guise of various applications, such as the flash player, were also identified in September. The spies' primary targets are short messages that can contain the mTAN codes used to confirm online banking transactions.

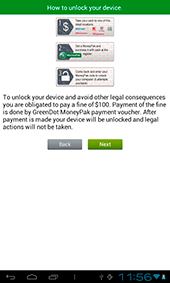
The last month saw some fake anti-viruses for Android, too. Doctor Web's analysts discovered three such programs which were dubbed Android.Fakealert.8.origin, Android.Fakealert9.origin, and Android.Fakealert.10.origin. Recall that these applications are fraudulent products that detect non-existent threats and invite the device's user to pay a certain amount in exchange for their neutralisation. Interestingly, one of these programs, namely Android.Fakealert.10.origin, was spread under the guise of an application for viewing adult videos but in truth mimicked an existing anti-virus and, when launched, showed a warning about the need to scan the mobile device for infection. To eliminate threats, which undoubtedly were found in abundance, it prompted the user to purchase a full version of the program.
Also discovered in September was a modification of Trojan Obad, which was added to the Dr.Web virus database as Android.Siggen.3.origin. This malware can send SMS messages to premium numbers and download other malicious applications to a mobile device. However, its exploitation of an Android error, which allows the Trojan to avoid removal, is among its most distinguishing features. During installation it requests access to features available to the device's administrator and, if privileges are granted, hides itself from the Apps list to prevent the user from modifying system settings and to minimise the risk of its removal by standard means. Dr.Web products for Android incorporate special routines to neutralise these types of threats and easily remove this Trojan from mobile devices.
Other events
G20 backdoor spam
According to a security report, scammers ill-used the wide publicity of the upcoming G20 summit in St. Petersburg to send messages with an attached RAR archive containing malignant files.
The archive included a .lnk file and two binaries. Researchers found that these binary files do not pose a threat, if run separately. But, in fact, they are a single file, split into two parts. The .lnk shortcut contains commands that merge them into a single executable file and then run that file on the infected computer. In turn, the backdoor communicates with the attackers‘ server to execute their malicious commands in the affected system and downloads plug-ins for keylogging and taking screen shots. The plug-ins' code is run in the backdoor's process and, therefore, the plugins do not appear on the list of running applications, making them harder to detect. This malware is detected by Dr.Web anti-virus software as Win32.HLLW.Autoruner1.54698.
Banking Trojan: Southern Europe, Turkey and the United Kingdom are under attack
According to security experts, a new Trojan has compromised the computers of bank customers in Turkey, the Czech Republic, Portugal and the UK. Its payload is similar to that of Zeus and SpyEye (keylogging, taking screen shots, capturing video, configuring a remote proxy server to intercept traffic, web-injections), but unlike the malware mentioned above, this Trojan can create a hidden VNC server in an infected system.
Criminals use the Trojan to get the victim's account information and prompt the user to install a malignant program as a software component for Symbian, Blackberry or Android. Victims received emails with the malicious file *.Pdf.exe attached to them that were supposedly sent by postal services and telecom providers (interestingly, Czechs who visited the fake postal service site ceskaposta.net were redirected to Czech Post’s real site ceskaposta.cz.
Doctor Web's analysts are aware of several versions of this Trojan: Trojan.Inject1.27640, Trojan.DownLoader10.3567, Trojan.DownLoader9.22851, Trojan.DownLoader10.10165. The earliest signature was added to the Dr.Web virus databases on July 31, 2013.
Trojan spread with pirated version of GTA V
In September many sites reported that a Trojan was being spread with an illegal version of the popular computer game Grand Theft Auto V (GTA V). The game is quite popular, so criminals didn't hesitate to take advantage of it. A file containing malware is spread via torrent trackers under the guise of this game.
The file conceals a Trojan that prompts a gamer to enter into a form their phone number and the confirmation code received via SMS in response. If the victim sends an SMS with the code, they are subscribed to some sort of service for which 1 euro is debited from their mobile account every day until the service is cancelled. This malware is a typical representative of the Trojan.SmsSend family.
Banking Trojan attempts to control transactions in the Middle East and Asia
An anti-virus lab outside Russia registered a small but highly effective spam mailing that was spreading a malicious ZIP attachment. Financial institutions in the UAE, Pakistan, Nepal and, perhaps other countries of the region were among the victims. Presumably, the messages were sent from compromised mailboxes of financial companies in India and Pakistan, and were meant to spread malware of the family Trojan.PWS.Panda, also known as Zeus. Dr.Web software detects this program as Trojan.PWS.Panda.2401. Its entry was added to the virus database on September 10, 2013. The program is dangerous because it can steal online banking data.
Trojan for Mac OS X: made in SEA?
In mid-September, security experts discovered a malicious program dubbed BackDoor.Leverage.1. A user from Belarus sent a sample of this program to VirusTotal, an online service, for analysis.
It is unknown how the malware got into the user's system. Probably, they received it via email or while visiting a compromised website. By September 17, the attackers’ C&C server stopped sending commands to compromised systems.
This malicious application is disguised as a JPEG file and poses a threat to Mac OS X if the option to hide extensions for known file types is enabled on the Mac. Files that the program downloads onto an infected computer include the logo of the Syrian Electronic Army (SEA).
Security experts believe that only earlier versions of Mac OS X are in danger. The malware cannot harm Mac OS X 10.8. In other words, timely updating will ensure a Mac is invulnerable to this malignant program.
This malware was added to Doctor Web's virus database on September 18, 2013. It is supposedly used by criminals to mount targeted attacks and is not found in large numbers in the wild.
Trojans are attacking from the "cloud"
According to expert Thomas Siebert from the company G Data, criminals have begun employing cloud technologies in their attacks on users of online banking. Attackers use a special version of Zeus or Ciavax Trojans. They place its component on a cloud server to deliver up-to-date code onto infected computers to mount attacks on sites. The malware is used to intercept information about payment operations conducted from an attacked computer.
According to Siebert, "It is now impossible to determine which sites cybercriminals are going to attack. At the same time, checking Internet addresses manually on the basis of their subject isn’t an effective solution, as a large number of requests can attract the attention of intruders".
According to G Data experts, using the cloud approach to place malware significantly complicates its analysis and makes it difficult to find effective ways to neutralise it. Dr.Web anti-viruses detect this threat as a Trojan.PWS.Panda program. Ciavax Tis, detected as Trojan.Mayachok.18612, was added to the virus database on April 2013.
Malicious files detected in mail traffic in September
| 01.09.2013 00:00 - 30.09.2013 23:00 | ||
| 1 | Trojan.PWS.Panda.4795 | 0.94% |
| 2 | Trojan.DownLoad3.28161 | 0.78% |
| 3 | Trojan.Packed.24465 | 0.76% |
| 4 | Trojan.DownLoad3.28507 | 0.76% |
| 5 | Trojan.DownLoader10.15301 | 0.69% |
| 6 | Trojan.PWS.Stealer.3243 | 0.65% |
| 7 | Trojan.DownLoader9.22851 | 0.59% |
| 8 | Win32.HLLM.MyDoom.33808 | 0.44% |
| 9 | Trojan.Inject1.27909 | 0.35% |
| 10 | Trojan.DownLoader10.15884 | 0.35% |
| 11 | Trojan.PWS.Panda.4379 | 0.33% |
| 12 | Win32.HLLM.MyDoom.54464 | 0.31% |
| 13 | Trojan.PWS.Panda.547 | 0.30% |
| 14 | Win32.HLLW.Autoruner.25074 | 0.28% |
| 15 | Trojan.Hosts.6838 | 0.28% |
| 16 | BackDoor.Comet.152 | 0.28% |
| 17 | Trojan.Packed.196 | 0.28% |
| 18 | Trojan.DownLoader9.40193 | 0.28% |
| 19 | BackDoor.Comet.700 | 0.26% |
| 20 | Win32.HLLM.Beagle | 0.26% |
Malicious files detected on user computers in September
| 01.09.2013 00:00 - 30.09.2013 23:00 | ||
| 1 | Exploit.SWF.254 | 1.30% |
| 2 | Trojan.LoadMoney.1 | 0.75% |
| 3 | Trojan.Fraudster.524 | 0.69% |
| 4 | Trojan.InstallMonster.28 | 0.55% |
| 5 | Trojan.Packed.24524 | 0.50% |
| 6 | BackDoor.PHP.Shell.6 | 0.42% |
| 7 | Trojan.LoadMoney.76 | 0.37% |
| 8 | Trojan.Fraudster.394 | 0.35% |
| 9 | Trojan.Hosts.6838 | 0.31% |
| 10 | Trojan.SMSSend.4196 | 0.31% |
| 11 | Win32.HLLW.Shadow | 0.31% |
| 12 | Win32.HLLW.Autoruner.59834 | 0.30% |
| 13 | Trojan.MulDrop4.25343 | 0.29% |
| 14 | Trojan.DownLoader10.17667 | 0.28% |
| 15 | BackDoor.IRC.NgrBot.42 | 0.27% |
| 16 | Trojan.Packed.2782 | 0.23% |
| 17 | Win32.HLLW.Shadow.based | 0.22% |
| 18 | Exploit.Cpllnk | 0.22% |
| 19 | Trojan.Fraudster.502 | 0.18% |
| 20 | JS.Redirector.194 | 0.18% |