World’s largest botnet of 200,000 infected Android devices discovered
Real-time threat news | Hot news | Threats to mobile devices | All the news
September 20, 2013
Criminals have used several malignant programs to infect devices and hook them onto the botnet: the recently discovered program Android.SmsSend.754.origin, Android.SmsSend.412 (known to Dr.Web since March 2013 and spread as a mobile browser), Android.SmsSend.468.origin (known since April, 2013), and Android.SmsSend.585.origin, which has been known to Dr.Web since June 2013. The earliest version of the Trojan related to investigation of this incident is Android.SmsSend.233.origin. It was added to the Dr.Web virus database in November 2012. In most cases, websites owned by criminals and those that have been compromised and used to distribute malware are the sources of infection.
Trojan Android.SmsSend.754.origin is an apk application named Flow_Player.apk. During installation, it prompts the user to run it with administrator privileges—this will allow the malicious application to lock and unlock the screen. In addition, Android.SmsSend.754.origin later hides its icon from the home screen.
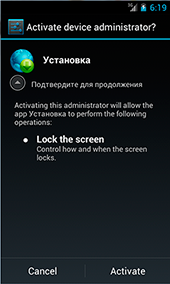
Once installation is completed, the Trojan sends information to the attackers about the infected device, including its IMEI, available account balance, country code, phone number, operator code, mobile phone model and OS version. Android.SmsSend.754.origin then waits for the intruders to issue a command, in response to which it can send an SMS message with a certain text to a specified number, send a bulk of short messages to numbers on the contacts list, open a specified URL in the browser, or show a message with a specific headline and text on the device's screen.
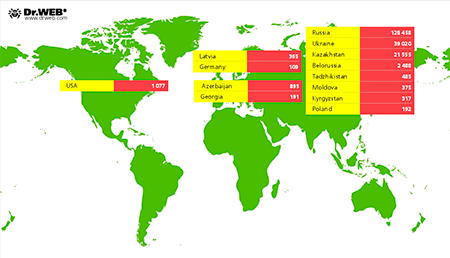
According to information collected by Doctor Web's analysts, to date the botnet includes more than 200,000 mobile devices running Android. Most of them (128,458) belong to Russian users; Ukraine ranks second with 39,020 infection incidents; and Kazakhstan comes in third—21,555 devices were compromised there. The image below provides information about the geographic distribution of the infection.
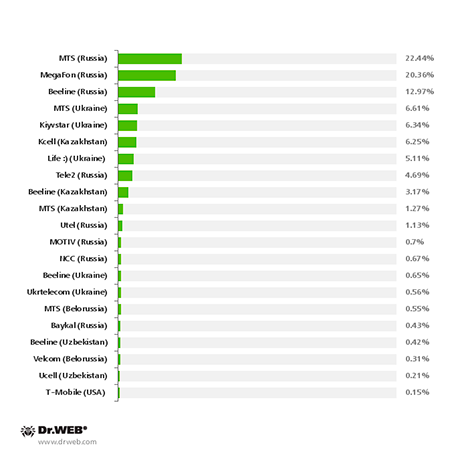
The diagram below shows the distribution of each mobile operator’s infected devices.
This is one of the largest-scale incidents involving the infection of Android devices in the past six months. Preliminary estimates suggest that the damage caused by malware as a result of this incident could amount to hundreds of thousands of dollars.
Currently, all of the above-mentioned threats are detected and removed by Dr.Web anti-virus software. To avoid infection, Doctor Web strongly recommends that users avoid downloading and installing software from suspicious websites. Doctor Web analysts are continuing to monitor the situation closely.