August 2013 Virus Activity Overview
Virus reviews | Hot news | All the news | Virus alerts
September 2, 2013
Viruses
According to the statistical information collected on computers by Dr.Web CureIt!, Trojan.Loadmoney.1 became the leader among the threats identified Trojan.Hosts.6815, which in an infected system modifies the file hosts containing DNS-server IP addresses, became the second most common Trojan. The IRC-bot BackDoor.IRC.Cirilico.119 ranks third, followed closely by Trojan.BtcMine.142—the malicious program that uses an infected computer's resources to mine bitcoins. The 20 most widespread threats detected on PCs by Dr.Web CureIt! in August is presented in the table below.
| Name | Quantity | % |
|---|---|---|
| Trojan.LoadMoney.1 | 32564 | 3.94 |
| Trojan.Hosts.6815 | 19553 | 2.37 |
| BackDoor.IRC.Cirilico.119 | 17453 | 2.11 |
| Trojan.BtcMine.142 | 17272 | 2.09 |
| Trojan.Mods.2 | 14618 | 1.77 |
| Trojan.MayachokMEM.7 | 13486 | 1.63 |
| Trojan.DownLoad3.26006 | 9345 | 1.13 |
| BackDoor.IRC.NgrBot.42 | 8018 | 0.97 |
| Trojan.MayachokMEM.8 | 7193 | 0.87 |
| Trojan.DownLoader9.19157 | 6977 | 0.84 |
| Trojan.Mods.1 | 6821 | 0.83 |
| Trojan.Fraudster.524 | 6230 | 0.75 |
| Trojan.Hosts.6838 | 6098 | 0.74 |
| BackDoor.Bulknet.963 | 5815 | 0.70 |
| Win32.HLLP.Neshta | 5673 | 0.69 |
| Trojan.BtcMine.146 | 5416 | 0.66 |
| Trojan.Winlock.8811 | 5409 | 0.65 |
| BackDoor.Maxplus.24 | 5354 | 0.65 |
| Win32.HLLW.Autoruner1.51068 | 5184 | 0.63 |
| Trojan.Inject2.23 | 5160 | 0.62 |
Botnets
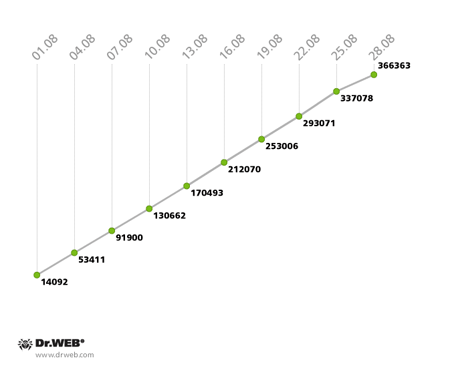
The botnet created by hackers with the file infectorWin32.Rmnet.12 continues to grow. The first subnet is gaining about 12,000 newly infected PCs daily, while the second subnet is growing by 10,500 hosts per day. The infection’s growth rate is illustrated in the graphs below.
Win32.Rmnet.12 botnet growth in August 2013 (1st subnet)
Win32.Rmnet.12 botnet growth in August 2013 (2nd subnet)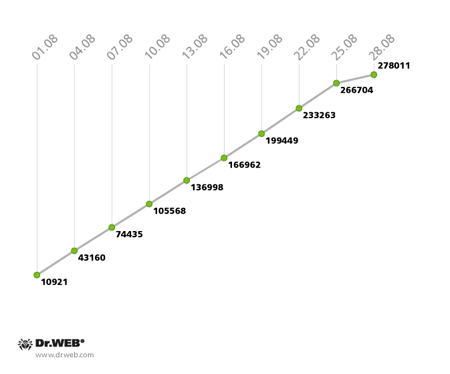
The botnet consisting of machines infected with the file infector Win32.Rmnet.16 is also continuing to grow unabated, with some 1,500 newly infected PCs joining in every day. The diagram below illustrates how the network has expanded:
Win32.Rmnet.16 botnet growth in August 2013 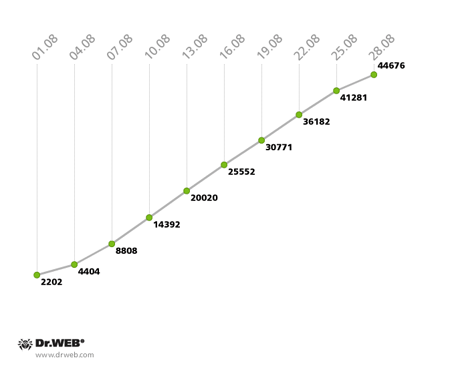
Statistics regarding the malignant module detected by Dr.Web anti-virus software as Trojan.Rmnet.19 also show slight growth: 685 new infection incidents were registered in August, and the total number of bots didn't change much—5,014 infected computers were found in the network on August 28. The quantitative indicators of the spam botnet BackDoor.Bulknet.739 have gradually increased as well. Compared with the previous month, the average daily number of active bots in the network remained virtually unchanged and amounted to 2,500, and the average number of new joiners per 24 hours was 500-600 computers. The botnet’s growth is illustrated in the graph below:
BackDoor.Bulknet.739 botnet growth in August 2013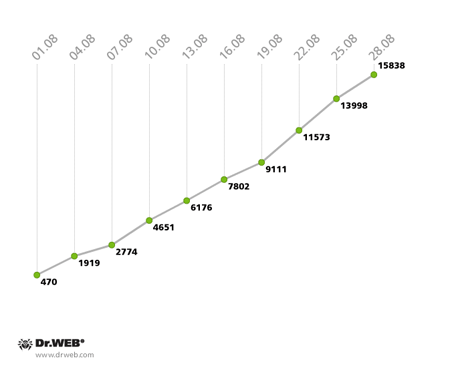
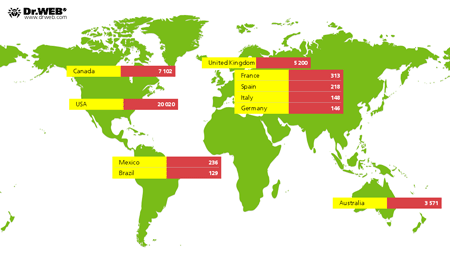
Also unchanged was the number of Macs infected with BackDoor.Flashback.39: at the end of August, it was 38,822. Most infected machines are found in the United States (20,020); Canada ranks second (7,102); and the United Kingdom (5,200) ranks third. They are followed by Australia with 3,571 compromised computers; 313 users of infected Macs live in France, 236 reside in Mexico, 218 are in Spain, 148 dwell in Italy, 146 are citizens of Germany, and 129 are Brazilians. There was only one incident involving infection with BackDoor.Flashback.39 in Russia. The map below indicates the Trojan's spreading geography.
Threat of the month: Linux.Hanthie
A year ago, before the outbreak of BackDoor.Flashback.39, users were confident that Mac OS X was completely secure, and now it is widely believed that no threats to Linux exist. However, in August Doctor Web analysed another Trojan dubbed Linux.Hanthie.
Linux.Hanthie (aka Hand of Thief) is a FormGrabber bot and a Linux BackDoor. It features anti-detection technologies and routines for its covert startup, does not require administrator privileges, and uses strong encryption (256-bit) for communicating with the control panel. The bot's configuration file contains a large number of parameters for its flexible configuration.
When the Trojan is launched, it blocks access to sites from which anti-virus software and updates are downloaded. It also makes use of routines to impede its analysis and launch in isolated and virtual environments. The latest version of Linux.Hanthie is unable to replicate itself, so its developers recommend that intruders employ social engineering techniques to spread it. The Trojan can operate under various Linux distributions, including Ubuntu, Fedora and Debian, and supports eight desktop environments such as GNOME and KDE.
The main purpose of Linux.Hanthie is to intercept information submitted by users via forms and to then send it to criminals. The Trojan can inject the grabber into Mozilla Firefox, Google Chrome, Opera, Chromium and Ice Weasel. It also performs backdoor tasks; traffic is encrypted during communication with the C&C server. More information about this malicious program can be found in a corresponding review published by Doctor Web on its site.
Other events during the month
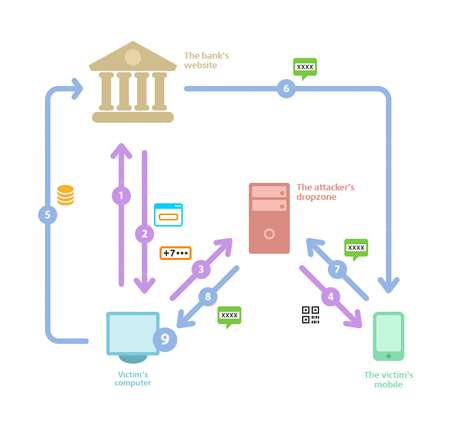
The last month also yielded some insights into banking security. On August 19, Brian Krebs, a well-known expert on information security, published a detailed blog post about attacks being carried out against bank customers via their Android phones and PCs. Trojans designed with the crimeware kit Perkele can bypass the multi-factor authentication that is used by many banks. Numerous clients of German banks became victims of fraud by installing malware they had received from criminals under the guise of a bank security certificate. The scheme in detail is as follows.
When a victim visits their bank's website (see figure, arrow 1), a Trojan (Zeus, Citadel, or any other) injects code into the victim's browser (arrow 2) which prompts the user to enter their mobile phone number and the type of operating system (item 9). This information is sent to the malicious server (arrow 3) which sends a request to the victim's browser (arrow 4), prompting the victim to read the QR code ostensibly to install an additional security module, which is actually a malicious program. Once the victim reads the QR code, malware is downloaded and installed on the mobile phone and attackers get an opportunity to intercept incoming SMS. At this point, the malware on the victim's computer automatically initiates financial transactions that involve the victim's account (arrow 5). When the bank sends an SMS message with a one-time code (arrow 6), the Trojan intercepts it and sends it to the attacker's server (arrow 7), and the malicious script on the device gets the code (arrow 8) and finalises the unauthorized transaction.
Apart from money, fraud trade schemes involving virtual commodities such as 'Like' points on social networking sites are growing in popularity among cyber criminals. Some users are willing to pay real money for these virtual ’tokens’. In addition, ‘like’ points help companies to promote their goods and services: the more ‘like’ points a product garners, the more attractive it appears to potential buyers. Attackers sell fake Twitter and Instagram accounts which are created using an unusual version of the malware Trojan.PWS.Panda. Dr.Web anti-virus software detects this threat as Trojan.PWS.Panda.106.
Also in August, analysts discovered a new version of BackDoor.Maxplus, which operates as a keylogger and connects an infected computer to a peer-to-peer network that has been set up by criminals. In order to avoid detection by anti-virus software, the Trojan uses non-trivial ways to conceal itself. When run on an infected device, it copies itself in two directories located in violation of alphabetical order. The names of BackDoor.Maxplus’s executable files are written from right to left in the registry, similar to texts written in Semitic languages (Arabic, Hebrew, etc.). The signature of the malicious program has been added to the Dr.Web virus databases.
Also discovered in August was Trojan.WPCracker.1 which is designed to compromise sites managed with popular CMSs.
Mobile threats
The last month of summer was relatively quiet in terms of threats to mobile devices. However, Dr.Web virus databases received the definitions for several Android.SmsSend Trojan horses that send short messages to premium numbers to sign up subscribers for various paid services. In addition, a large number of spyware was discovered, including programs for jail-broken devices. These applications are dangerous because, when installed by hackers, they can covertly monitor user activities: for example, they may intercept SMS messages, acquire information about calls, track GPS coordinates and forward the data to a remote server. You can read more about these programs in a corresponding publication on Doctor Web's site.
Malicious files detected in mail traffic in August
| 01.08.2013 00:00 - 31.08.2013 23:00 | ||
| 1 | Trojan.Winlock.8811 | 1.11% |
| 2 | Trojan.PWS.Panda.4379 | 1.00% |
| 3 | Trojan.Packed.24465 | 0.86% |
| 4 | Trojan.Inject2.23 | 0.64% |
| 5 | Trojan.PWS.Stealer.3243 | 0.53% |
| 6 | Trojan.PWS.Panda.655 | 0.51% |
| 7 | Trojan.PWS.Panda.547 | 0.46% |
| 8 | Win32.HLLM.MyDoom.33808 | 0.44% |
| 9 | Trojan.Proxy.25849 | 0.35% |
| 10 | Trojan.DownLoader4.56255 | 0.35% |
| 11 | Win32.HLLW.Autoruner.25074 | 0.33% |
| 12 | Trojan.Spambot.12288 | 0.33% |
| 13 | Trojan.PWS.Panda.786 | 0.29% |
| 14 | Win32.HLLM.Beagle | 0.29% |
| 15 | Trojan.PWS.Stealer.946 | 0.26% |
| 16 | Trojan.MulDrop4.35808 | 0.26% |
| 17 | BackDoor.Comet.700 | 0.26% |
| 18 | Win32.HLLM.MyDoom.54464 | 0.26% |
| 19 | Trojan.DownLoad3.28161 | 0.26% |
| 20 | Trojan.DownLoader9.40193 | 0.26% |
Malicious files detected on user computers in August
| 01.08.2013 00:00 - 31.08.2013 23:00 | ||
| 1 | Exploit.SWF.254 | 1.28% |
| 2 | SCRIPT.Virus | 1.11% |
| 3 | Adware.Downware.915 | 0.85% |
| 4 | Trojan.Fraudster.524 | 0.71% |
| 5 | Trojan.LoadMoney.1 | 0.71% |
| 6 | Adware.InstallCore.122 | 0.68% |
| 7 | Adware.Downware.179 | 0.60% |
| 8 | JS.IFrame.482 | 0.57% |
| 9 | Tool.Unwanted.JS.SMSFraud.26 | 0.51% |
| 10 | Adware.Downware.1328 | 0.40% |
| 11 | Adware.Downware.1317 | 0.38% |
| 12 | Trojan.InstallMonster.28 | 0.38% |
| 13 | Adware.InstallCore.124 | 0.37% |
| 14 | Tool.Skymonk.11 | 0.36% |
| 15 | Adware.Toolbar.202 | 0.35% |
| 16 | Adware.InstallCore.114 | 0.35% |
| 17 | Tool.Unwanted.JS.SMSFraud.29 | 0.33% |
| 18 | Trojan.Fraudster.394 | 0.32% |
| 19 | Trojan.LoadMoney.17 | 0.31% |
| 20 | Tool.Unwanted.JS.SMSFraud.10 | 0.30% |