A review of iOS spyware that threatens user privacy
Virus reviews | Hot news | Threats to mobile devices | All the news | Virus alerts
August 22, 2013
Owners of mobile devices running iOS have gotten used to the fact that their devices are protected from malware and cyber attacks, but in many ways this level of security only exists for devices whose operating system hasn't been modified by their users. If the device is jailbroken (i.e., access to the file system is available), personal information stored on the phone can be compromised by commercial spyware—a threat most users are unaware of.
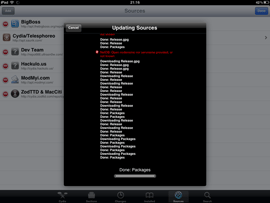
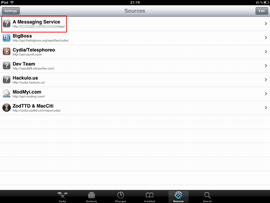
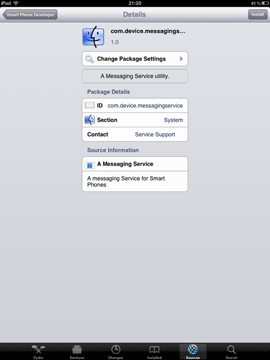
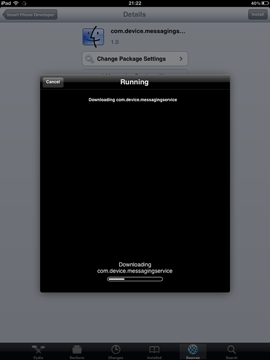
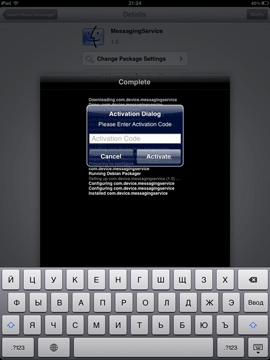
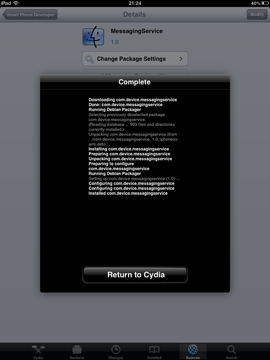
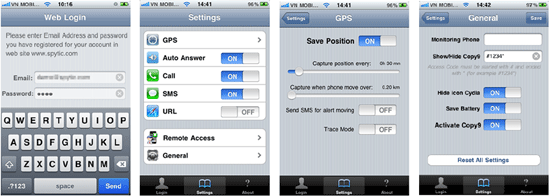
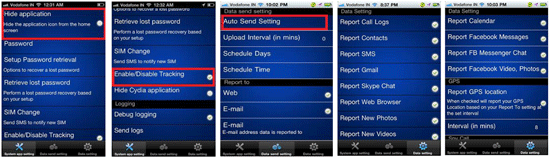
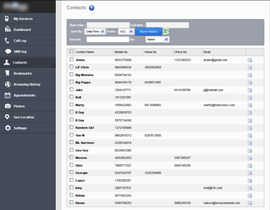
An intruder will need very little time to install such a spy application. All they need is to get physical access to the device, use Cydia (which is almost always automatically installed during jailbreaking) to download the software from the Internet, and configure the spy. Such applications do not interfere with the user experience and covertly send all the information they gather to a remote server. People who are interested in such information access the server under their personal accounts to get the data they need. The screenshots below show how such spyware is installed.
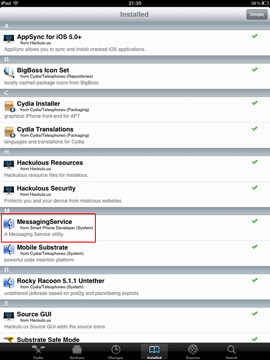
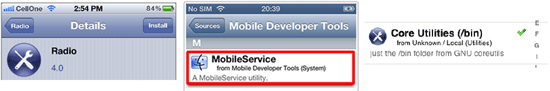
As seen in the last image, the successfully installed spyware is found on the Cydia list under the name MessagingService, which is meant to confuse inexperienced owners of jailbroken devices. It is possible that more experienced users will also mistake the application for a system component or simply won't notice it. Virtually all developers of spyware do their best to reduce the risk of their applications being discovered easily and use application names that are similar to those listed above. For example, the spyware can appear on the list as Radio, MobileService or Core Utilities.
It should also be noted that commercial iOS spyware does not create shortcuts on the desktop or provide an option to hide them. Moreover, there are ways to hide the Cydia icon, too, so intruders can carry out a well-planned attack by performing a jailbreak on a secure device and covertly installing the spyware.
After installing the spy, the attacker needs to configure it. In particular, they can launch the application or activate only necessary features. Also, at this stage, it is often possible to set the interval at which the application will communicate with a remote server to upload the collected information.
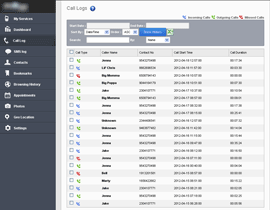
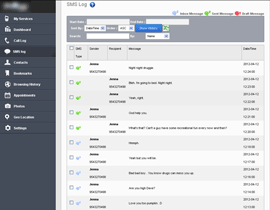
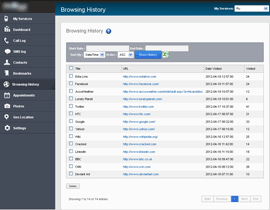
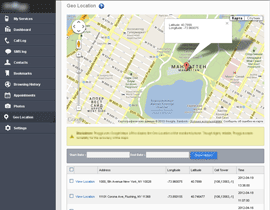
After all these steps, the spy program begins its covert activities: it keeps a record of all important user activities and uploads the collected data to the server. The image below provides an example of the web control panel which contains information that can be obtained by means of such surveillance.
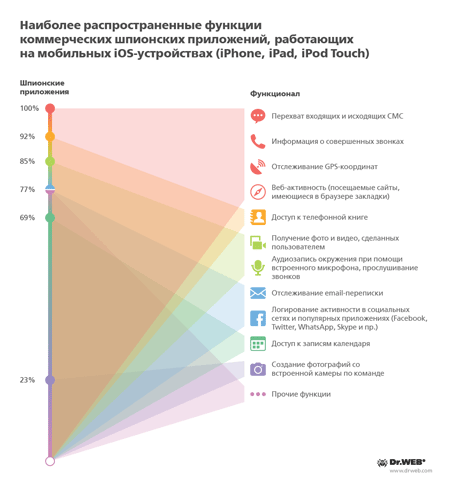
Spyware of different versions and from different developers incorporate various sets of features. The diagram below contains information about the most common spyware features.
The most common features of commercial spyware for iPhone, IPad, and iPod Touch
| Spyware | Feature |
| Intercepts incoming and outgoing SMS messages | |
| Acquires information about calls | |
| Records GPS coordinates | |
| Monitors web-surfing (information about visited sites and browser bookmarks) | |
| Accesses the address book | |
| Acquires user-recorded photos and video | |
| Uses the device’s microphone to record audio and eavesdrop on calls | |
| Monitors email correspondence | |
| Logs social-networking activities and the operation of popular applications (e.g., Facebook, Twitter, WhatsApp, Skype) | |
| Accesses calendar records | |
| Takes pictures with the device’s camera on command |
It indicates that, in most cases, spyware can monitor all the important aspects of a user's activities, ranging from acquiring their text and email messages to obtaining information about their contacts, plans, meetings and environment.
Currently, the Dr.Web virus database contains over 50 entries for iOS spyware that belong to 15 distinct families. The following pie chart indicates how widely each of them has spread.
Popular commercial spyware for iOS (in percentagesPopular commercial iOS spyware percentage
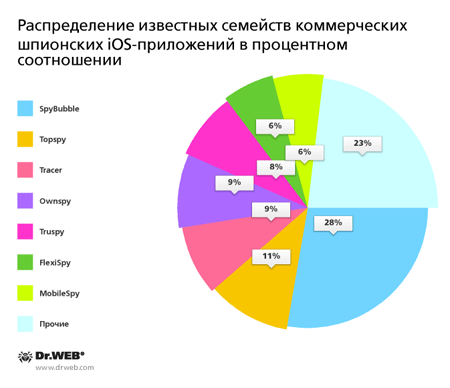
Considering that the number of jailbroken devices may currently exceed 20 million and that there is a high probability that the remaining devices will experience an intrusion that involves jailbreaking, many users of handhelds manufactured by Apple are picking up on the threat spyware applications pose to their personal information. To ensure the security of your personal information, follow these simple but important rules:
- Never leave your mobile device for long in public places even if people you trust are nearby. A professional attacker can find a way to sneak up, get hold of your device and easily install spyware.
- Note suspicious activities on the device, e.g., strange messages or changes in the UI that seemingly happened on their own.
- Back up the content stored on your mobile device: if necessary, you will be able to restore all the important data and the operating system to its original state (in most cases a jailbreak can be fixed by updating or restoring the OS).