July 2013 Virus Activity Overview
Virus reviews | Hot news | All the news | Virus alerts
August 5, 2013
Viruses
According to data collected by Dr.Web CureIt! in July 2013, Trojan.LoadMoney.1 ranked first in the statistics—this program installs adware in an infected system. Second place among the most frequently detected malware is occupied by Trojan.Hosts.6815 which modifies the hosts file in infected systems. As a result of its activity, when a user tries to go to one of the sites specified in the file, the browser is automatically redirected to a specially crafted malicious web page. Trojan.Mods.2 comes in third—this Trojan replaces web pages loaded by browsers in the infected system. As a consequence, instead of visiting the sites they want, users end up on fraudulent web pages where they are prompted to enter their mobile phone number and reply to a received SMS message. If they comply, a certain amount will be debited from their account. The top 20 most common malware in July 2013, according to statistics collected by Dr.Web CureIt!, are presented in the table below:
| Name | Quantity | % |
|---|---|---|
| Trojan.LoadMoney.1 | 22921 | 3.05 |
| Trojan.Hosts.6815 | 20641 | 2.74 |
| Trojan.Mods.2 | 16088 | 2.14 |
| Trojan.DownLoader9.19157 | 8624 | 1.15 |
| BackDoor.IRC.NgrBot.42 | 7414 | 0.99 |
| Trojan.Mods.1 | 7197 | 0.96 |
| BackDoor.Andromeda.178 | 6130 | 0.81 |
| Trojan.Hosts.6838 | 5828 | 0.77 |
| Trojan.MayachokMEM.7 | 5741 | 0.76 |
| BackDoor.Maxplus.24 | 5696 | 0.76 |
| Trojan.PWS.Panda.2401 | 5347 | 0.71 |
| Win32.HLLP.Neshta | 5265 | 0.70 |
| BackDoor.Bulknet.963 | 5227 | 0.69 |
| Win32.HLLW.Autoruner1.45469 | 5114 | 0.68 |
| Trojan.MulDrop4.25343 | 4588 | 0.61 |
| Trojan.Packed.24079 | 4174 | 0.55 |
| Win32.HLLW.Autoruner1.40792 | 3653 | 0.49 |
| Win32.HLLW.Gavir.ini | 3434 | 0.46 |
| Win32.Sector.22 | 3369 | 0.45 |
| Trojan.AVKill.31324 | 3307 | 0.44 |
Encoders and Winlockers
In the first days of July, Doctor Web's technical support received 550 requests from people whose systems were affected by encoder Trojans. You may recall that malware of this category is designed solely for one purpose, namely, to encrypt files on a hard drive and extort money for their decryption. Encoders can encrypt a variety of file types: archives, images, documents, music, movies, and many others. The amount extorted by criminals for decoding can vary from a few dozen to several thousand dollars.
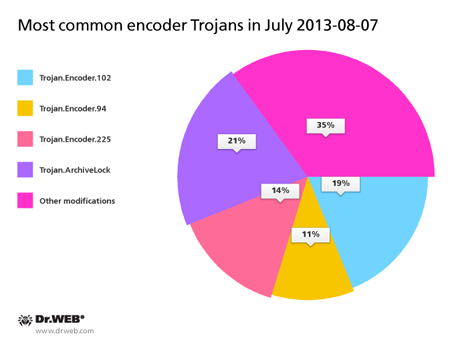
The diagram below provides a list of Trojan encoder modifications that, according to Doctor Web's anti-virus laboratory, most frequently infected computers in July.
The largest number of machines affected by Trojan encoders (75%) resided in Russia, and somewhat fewer —15% — in Ukraine. Oddly enough, quite a number of encoder-compromised machines were found in Brazil. A few infection incidents were registered in Venezuela, Estonia, the USA and the EU countries. During July, Doctor Web technical support received similar requests from five residents of Colombia and Argentina, as well as from three citizens of Chile.
Several hundred users requested Doctor Web's assistance in the aftermath of their systems becoming infected with Trojan.Winlock programs: 79.5% of them were Russians; Ukrainians accounted for 16%; and 1.67% were residents of Kazakhstan. Also registered were individual Winlock infection incidents in Sweden, Colombia, the USA, Belarus and the European Union.
Botnets
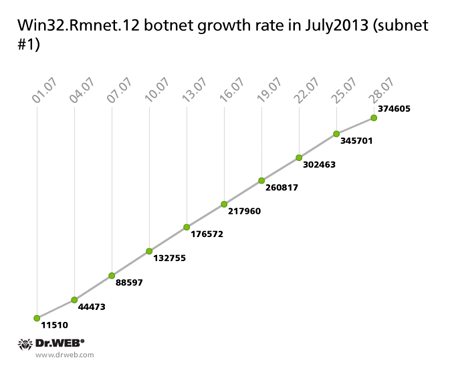
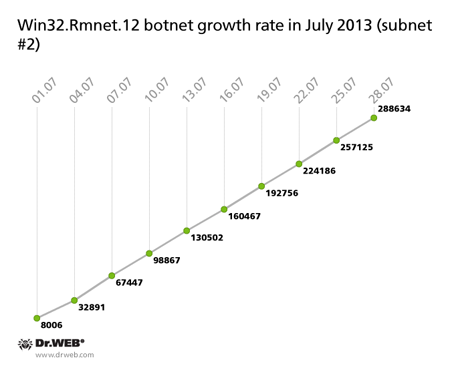
The botnet made with the file infector Win32.Rmnet.12 is shrinking. Thus, as of July 29, 2013, its first subnet included 392,538 infected machines (66,654 fewer than in June) while the second consisted of 532,166 active bots (which is 80,969 fewer bots than the previous month). In just 30 days the subnets gained 374,605 and 288,634 newly infected hosts, respectively. The graph below shows how the number of infected hosts in the botnets changed through July 2013.
The overall strength of the botnet, consisting of computers carrying the file infector Win32.Rmnet.16, fell by more than a half from one month ago; this botnet consisted of an average of 4,674 active bots at that time. By the end of July, the number of infected computers was 2,059. At the same time, the influx of new joiners virtually stopped. The average daily number of new bots connecting to the command and control server is not exceeding 10.
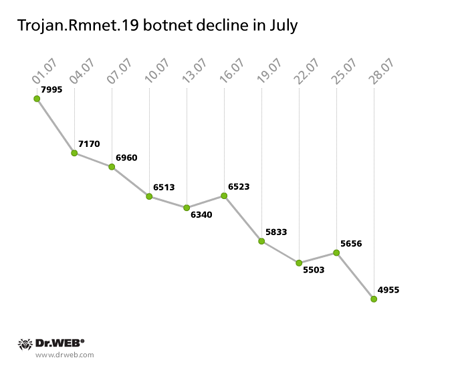
The number of machines on which Dr.Web software detects malware dubbed Trojan.Rmnet.19 is going down too. In early July it diminished to 7,995 discovered malicious samples and, by month's end, it dropped to 4,955 with no more than 40 newly infected hosts appearing on the network daily. The decline in the number of Trojan.Rmnet.19 bots is illustrated in the graph below.
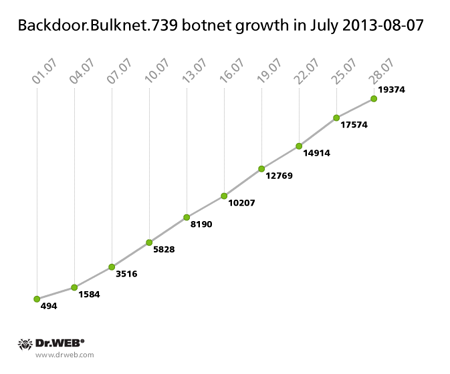
The number of nodes in the botnet created with BackDoor.Bulknet.739 also changed significantly. This malignant application is designed to carry out spam mailings. In July, its botnet contained an average of 2,500 active bots daily, with 500-800 newly infected hosts contacting the BackDoor.Bulknet.739 C&C server every 24 hours. The growth in number of hosts infected with BackDoor.Bulknet.739 is illustrated in the graph below.
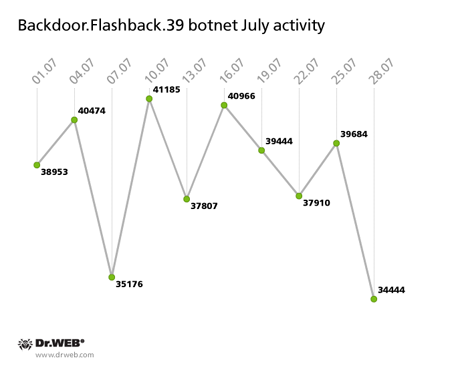
The botnet BackDoor.Flashback.39, consisting of machines running Mac OS X, is still operational with around 40,000 infected Macs contacting its C&C servers on a daily basis. The botnet's activity is illustrated in the graph below.
These figures suggest that the botnet BackDoor.Flashback.39 has ceased growing, but it isn’t shrinking either. The main reason behind such persistence is carelessness on the part of Mac OS X users.
Threats to handhelds
The remarkable regularity with which the Dr.Web virus database is acquiring new entries for a variety of mobile device commercial spyware once again proves the fact that such services are not only in demand, but also increasing in popularity in today's high-tech market. Last month, Doctor Web's analysts found a large number of new versions of known spyware programs such as Android.MobileSpy and Program.Mobimon, as well as the new families Program.Topspy and Program.Tracer. Such applications enable intruders to monitor various user activities and are often available for several mobile platforms including Android, BlackBerry and Symbian OS.
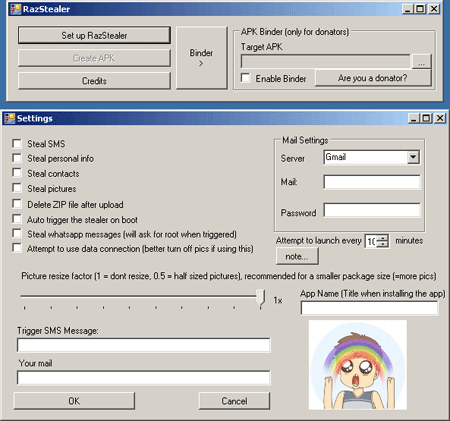
While the stock of commercial software for monitoring, which can be used both legally and in violation of the law, is increasing, purely cybercrime-related services designed to obtain sensitive information from mobile devices are becoming mass market too. Special programs that enable criminals to embed Trojan features in any Android application serve as a good example. Tool.Androrat and Tool.Raziel are two such "products" discovered by Doctor Web's analysts. The first utility uses for its operation the source code of AndroRat, a freely distributed program for remote access and administration, which has been known since 2012 and is detected by Dr.Web as Program.Androrat.1.origin. In the second case, the utility's author makes use of their own Trojan spy program, which can either be built into an Android app or compiled into a separate apk-package. This malware has been added to the virus database as Android.Raziel.1.origin.
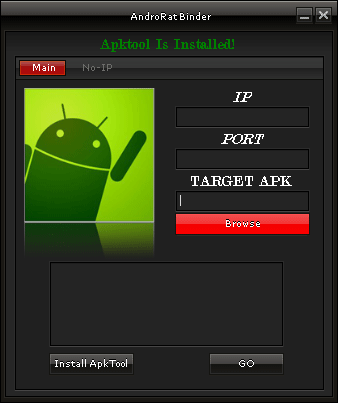
Such utilities are relatively easy to use and enable people with low programming skills to create Trojans for Android. The number of such toolkits is likely to increase in the near future.
In the second month of summer, Android also saw the discovery of several vulnerabilities, with Master Key being among the most notable. The flaw in Android security routines enabled installation of unsigned applications from packages containing files with identical names. Thanks to prompt action on the part of Doctor Web's virus analysts, routines to detect the applications that exploited this vulnerability were implemented in the Dr.Web for Android anti-virus: regardless of whether the software flaw is exploited deliberately or as a result of unforeseen technical errors, the program in question will be detected as Exploit. APKDuplicateName.
The first Trojan to exploit this software flaw was discovered less than a month after information about the vulnerability Master Key appeared in the public domain. The malware, dubbed by Dr.Web as Android.Nimefas.1.origin, was spread via a Chinese Internet portal that provided access to Android applications. This Trojan is able to send SMS messages, intercept incoming messages, and send confidential information such as the phone number, as well as information from the phone book of the compromised device, to a remote server. For more information about this threat, please refer to the review published on our website.

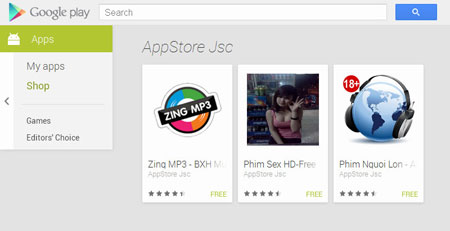
And some threats came from Google Play. At the end of the month, Doctor Web's analysts discovered several malicious applications that could install Android.SmsSend Trojan horses onto infected devices.
This incident once again demonstrates that the current security measures implemented by Google appear to be insufficient, and that users should exercise caution when they download applications available via this distribution platform. You can read more about this incident in a corresponding publication on Doctor Web's site.
Malicious files detected in mail traffic in July
| 01.07.2013 00:00 - 30.07.2013 14:00 | ||
| 1 | Trojan.PWS.Panda.4379 | 1.02% |
| 2 | Trojan.PWS.PandaENT.4379 | 0.71% |
| 3 | Trojan.Packed.196 | 0.71% |
| 4 | Trojan.Inject2.23 | 0.58% |
| 5 | Trojan.Packed.24465 | 0.48% |
| 6 | Trojan.PWS.Panda.547 | 0.47% |
| 7 | BackDoor.Tishop.55 | 0.40% |
| 8 | Win32.HLLM.MyDoom.54464 | 0.38% |
| 9 | Trojan.PWS.Panda.655 | 0.36% |
| 10 | Trojan.Packed.24450 | 0.35% |
| 11 | Win32.HLLM.MyDoom.33808 | 0.31% |
| 12 | Trojan.PWS.Stealer.3128 | 0.29% |
| 13 | Trojan.Proxy.24953 | 0.28% |
| 14 | Trojan.MulDrop4.35808 | 0.25% |
| 15 | BackDoor.Comet.152 | 0.21% |
| 16 | VBS.Rmnet.2 | 0.20% |
| 17 | Trojan.Inor | 0.17% |
| 18 | SCRIPT.Virus | 0.17% |
| 19 | Trojan.DownLoader1.64229 | 0.17% |
| 20 | Trojan.VbCrypt.8 | 0.16% |
Malicious files detected on user computers in July
| 01.07.2013 00:00 - 30.07.2013 14:00 | ||
| 1 | SCRIPT.Virus | 0.96% |
| 2 | Exploit.SWF.254 | 0.73% |
| 3 | Trojan.LoadMoney.1 | 0.72% |
| 4 | Adware.InstallCore.122 | 0.68% |
| 5 | Adware.Downware.915 | 0.55% |
| 6 | Adware.Downware.179 | 0.52% |
| 7 | Tool.Unwanted.JS.SMSFraud.26 | 0.51% |
| 8 | Adware.Downware.1284 | 0.49% |
| 9 | Adware.InstallCore.114 | 0.47% |
| 10 | JS.IFrame.453 | 0.41% |
| 11 | Adware.Toolbar.202 | 0.37% |
| 12 | Adware.InstallCore.115 | 0.34% |
| 13 | Adware.Downware.1132 | 0.34% |
| 14 | Tool.Skymonk.11 | 0.34% |
| 15 | Adware.InstallCore.101 | 0.34% |
| 16 | Tool.Unwanted.JS.SMSFraud.29 | 0.31% |
| 17 | Win32.HLLW.Shadow | 0.31% |
| 18 | Adware.Webalta.11 | 0.31% |
| 19 | Adware.Downware.1317 | 0.30% |
| 20 | Exploit.BlackHole.183 | 0.30% |