May 2013 virus activity review from Doctor Web
Virus reviews | Hot news | All the news | Virus alerts
June 3, 2013
Viruses
According to statistics collected by Dr.Web CureIt!, Trojan.Hosts.6815 was the undisputed leader in terms of number of infections (2.53% of the total). It was followed by Trojan.Mods.1 which replaces the content of web pages loaded in the browser—a detailed review of this threat can be found on Doctor Web's site. In the past month, Dr.Web CureIt! found 15,830 copies of the Trojan, which is 1.95% of the total number of identified threats. Trojan.Mayachok programs were often detected in RAM, and BackDoor.IRC.NgrBot.42 and Trojan.Redirect malware were also discovered frequently on infected PCs. The twenty most common threats in May, according to information collected by Dr.Web CureIt!, are listed in the table below.
| Name | % |
|---|---|
| Trojan.Hosts.6815 | 2.55 |
| Trojan.Mods.1 | 2.01 |
| Trojan.MayachokMEM.7 | 1.50 |
| BackDoor.IRC.NgrBot.42 | 1.41 |
| Trojan.Redirect.147 | 1.36 |
| Trojan.Redirect.140 | 1.35 |
| Trojan.Hosts.6838 | 1.22 |
| Trojan.Mods.2 | 1.01 |
| Trojan.Packed.24079 | 0.97 |
| Trojan.DownLoader8.48947 | 0.85 |
| Trojan.Zekos | 0.85 |
| Trojan.PWS.Stealer.1932 | 0.74 |
| Win32.HLLP.Neshta | 0.71 |
| BackDoor.Gurl.2 | 0.69 |
| Trojan.Hosts.6708 | 0.59 |
| Trojan.SMSSend.2363 | 0.51 |
| Trojan.Packed.142 | 0.49 |
| Trojan.Packed.142 | 0.44 |
| Trojan.Packed.142 | 0.42 |
| Trojan.DownLoader9.19157 | 0.41 |
Botnets
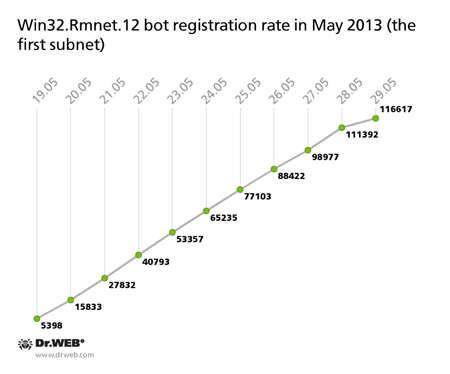
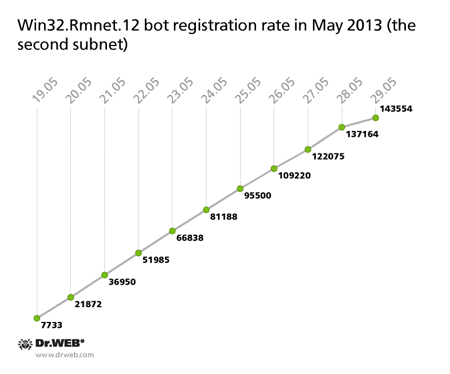
Currently, Doctor Web's analysts control two subnets of the botnet which was created with the file infector Win32.Rmnet.12. Each subnet has its own C&C server. In May, the number of active bots in one of the Win32.Rmnet.12 subnets reached 619,346, while another grew as large as 459,524 infected hosts, with 116,617 bots joining the first one and 143,554 zombies connecting to the second one in the last ten days. The average daily number of bots connecting to each of the networks is 14,000 and 11,000 infected hosts, respectively. This is how the botnets grew from May 19 till May 29:
Yet the botnet Win32.Rmnet.16 is growing at a very slow rate: as few as 181 infected hosts joined it in the period between May 19 and May 29, and the total number of nodes in the network was 5,220. Thus, we can conclude that today the file infector Win32.Rmnet.16 does not pose a serious epidemiological threat.
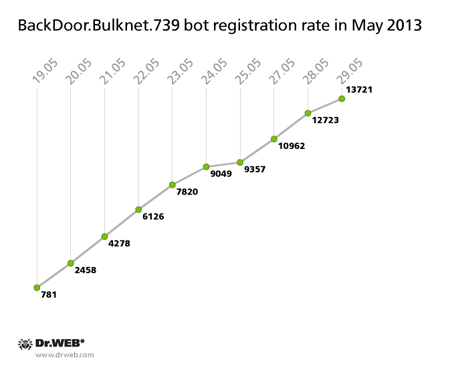
In early April 2013, Doctor Web reported athat it had managed to hijack a C&C server belonging to the botnet created with the malicious program BackDoor.Bulknet.739. Designed to send bulks of spam, this program is mostly spread on machines located in Italy, France, Turkey, the USA, Mexico and Thailand. If, at the beginning of April, only about 7,000 infected computers connected to this C&C server, by the end of May, the number of active bots grew to 17,242. Botnet growth from May 19 to May 29 can be traced in the chart below.
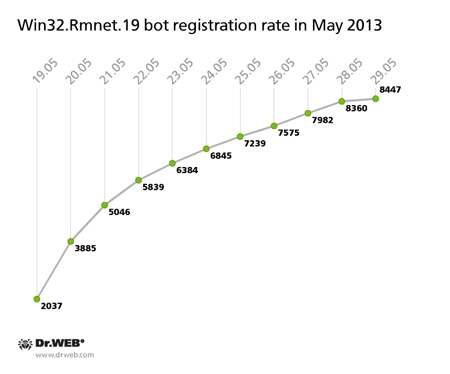
At the end of May, Doctor Web's analysts gained control over another Rmnet C&C server. They discovered that two new malware modules, both dubbed Trojan.Rmnet.19, were spread between nodes connected to the subnet. One of them is designed to detect virtual machine software on an infected computer, and the other one allows criminals to disable the following anti-viruses in a compromised system: Microsoft Security Essential, Norton Antivisus, Eset NOD32, Avast, Bitdefender, and AVG. To end anti-virus processes, the component emulates user actions, namely clicking on the appropriate icons. As of May 29, 20,235 active bots were connected to the C&C server, and from May 19 to May 29, 8,447 newly infected machines registered on the server controlled by Doctor Web's analysts. The process is illustrated in the diagram below.
More detailed information about this threat can be found in the news story published by Doctor Web.
Despite the fact that the botnet BackDoor.Flashback.39, comprised of Macs, was discovered more than a year ago, this botnet continues to operate today. Currently it consists of 65,987 infected machines.
In February 2013, Doctor Web reported the discovery of the Linux.Sshdkit which targets Linux servers. The malware is a library file available for 32- and 64-bit versions of Linux distributions. After successful installation, the Trojan injects its code into the process sshd and uses this process’s authorization routines. Once a user enters their login and password, the Trojan sends this information to a remote server.
Doctor Web's analysts used a sinkhole to hijack one Linux.Sshdkit control server and thus confirmed that the Trojan transmits stolen logins and passwords to remote hosts. In May 2013, the Trojan sent access data for 562 infected Linux servers to criminals. Some of these servers belong to major hosting providers.
Threat of the month: Trojan.Facebook.311
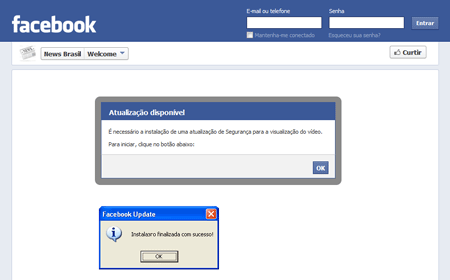
Users of social networking sites have repeatedly been targeted by cybercriminals and malware distributors. For example, in mid-May virus analysts registered the mass distribution of Trojan.Facebook.311 malware, implemented as a JavaScript plugin for Google Chrome and Mozilla Firefox. To spread the malignant plugin, the criminals created a web page on which users were prompted to download the application installer under the guise of a video security update.
Once the installation is completed and a browser is launched, Trojan.Facebook.311 tries to download a configuration file that contains the set of commands the hackers need. Then the malicious browser plug-ins wait for the user to authenticate on a social networking site, and start performing a variety of actions on their behalf. These actions include updating the user’s status, marking a post with "like", posting messages on the wall, sending private messages, etc. This malware works not only on Facebook but also interacts with Twitter and Google Plus—in particular, it can send spam. A more detailed review of this threat can be found on Doctor Web's site.
Skype attack
On May 23, numerous online media outlets reported the massive distribution of spam via Skype, predominantly targeting Russian users. Criminals lured users into downloading a malicious program that could send messages via various IM messengers.
The signature of Trojan.SkypeSpam.11 was added to the Dr.Web virus databases on May 22.
Threats to Android
Android saw another rough period in May. Doctor Web's analysts recorded the emergence of several malicious spy programs that steal confidential information on compromised devices.
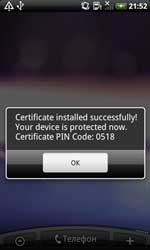
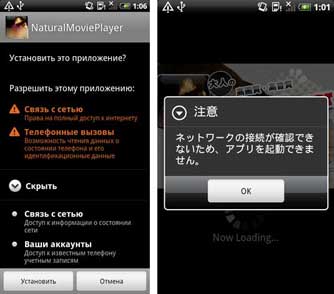
In particular, Android.Pincer.2.origin, found in the middle of the month, turned out to be a rather dangerous Trojan. It’s designed to intercept incoming short messages and forward them to a remote server. Makers of Android.Pincer.2.origin also implemented the feature that enables the malware to track messages sent from a specific number. To use it, they send it the appropriate command in a short message. Distributed as a security-certificate installer, the malware poses a severe threat to Android devices because it can intercept messages containing sensitive information such as mTAN codes. More information about this threat can be found in the relevant publication on Doctor Web's site.
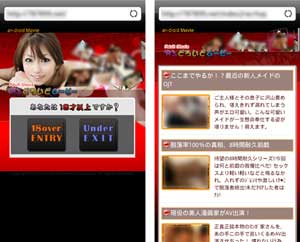
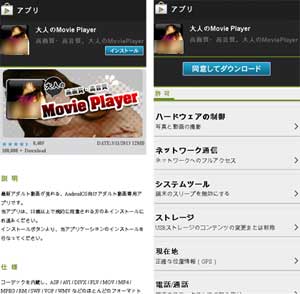
Also found in May was a Trojan stealing confidential information from Japanese Android users. Similar to its predecessors, the program dubbed Android.AccSteal.1.origin spread as an application from the Adult category. When launched, it sent the following information to a remote server: the Google Mail account name, the device's IMEI and model as well as the subscriber's mobile phone number.
It's worth mentioning that unlike other similar programs, the Trojan does perform the tasks expected of the application: it displays adult videos but only if the device is connected to the Internet, and notifies users to that effect. Given that Android.AccSteal.1.origin is spread from a site that imitates the now outdated look and feel of Google Play, the criminals must be trying to do their best not to raise users' suspicions while maintaining relatively high efficiency in collecting their personal data.
Criminals didn't pass by Chinese users either. Android.Roids.1.origin was a spy program distributed via Chinese forums as a system utility. It can transmit to the remote server a substantial volume of personal information, including the list of installed applications, information on SMS correspondence and calls, address book contacts, and еру list of files stored on the memory card. The Trojan can also record phone calls and acquire a device's GPS coordinates.
Malicious files detected in mail traffic in May
| 01.05.2013 00:00 - 30.05.2013 18:00 | ||
| 1 | Trojan.PWS.Panda.3734 | 1.49% |
| 2 | Trojan.PWS.Panda.4379 | 1.20% |
| 3 | Trojan.Oficla.zip | 0.90% |
| 4 | Trojan.Packed.196 | 0.80% |
| 5 | Trojan.Inject2.23 | 0.75% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.63% |
| 7 | Trojan.DownLoader9.17531 | 0.58% |
| 8 | Trojan.PWS.Stealer.2877 | 0.54% |
| 9 | Trojan.PWS.Panda.655 | 0.54% |
| 10 | Trojan.PWS.Stealer.946 | 0.53% |
| 11 | Trojan.Packed.666 | 0.53% |
| 12 | Exploit.CVE2012-0158.28 | 0.49% |
| 13 | Trojan.PWS.Stealer.2833 | 0.46% |
| 14 | Win32.HLLM.MyDoom.33808 | 0.44% |
| 15 | Trojan.PWS.Stealer.2824 | 0.39% |
| 16 | Trojan.PWS.Stealer.2861 | 0.39% |
| 17 | Trojan.PWS.Stealer.2864 | 0.37% |
| 18 | Exploit.CVE2012-0158.27 | 0.34% |
| 19 | BackDoor.IRC.NgrBot.42 | 0.34% |
| 20 | VBS.Rmnet.2 | 0.32% |
Malicious files detected on user computers in May
| 01.05.2013 00:00 - 30.05.2013 18:00 | ||
| 1 | SCRIPT.Virus | 0.71% |
| 2 | Adware.Downware.915 | 0.71% |
| 3 | Tool.Unwanted.JS.SMSFraud.26 | 0.50% |
| 4 | Win32.HLLW.MyBot | 0.48% |
| 5 | Adware.InstallCore.115 | 0.47% |
| 6 | Adware.Downware.179 | 0.45% |
| 7 | Adware.InstallCore.114 | 0.45% |
| 8 | Adware.Downware.1157 | 0.44% |
| 9 | Adware.InstallCore.101 | 0.36% |
| 10 | Tool.Unwanted.JS.SMSFraud.29 | 0.33% |
| 11 | Adware.Webalta.11 | 0.33% |
| 12 | Adware.Downware.1132 | 0.32% |
| 13 | Tool.Unwanted.JS.SMSFraud.10 | 0.31% |
| 14 | Trojan.Hosts.6708 | 0.30% |
| 15 | BackDoor.IRC.NgrBot.42 | 0.28% |
| 16 | Trojan.DownLoader9.19157 | 0.28% |
| 17 | Tool.Skymonk.11 | 0.28% |
| 18 | Trojan.Hosts.6838 | 0.28% |
| 19 | Win32.HLLW.Shadow | 0.27% |
| 20 | Win32.HLLW.Autoruner.59834 | 0.26% |