New Rmnet malware disables anti-virus programs
Real-time threat news | Hot news | All the news | Virus alerts
May 23, 2013
Doctor Web already warned users about the wide distribution of Win32.Rmnet.12 andWin32.Rmnet.16 programs that could connect infected machines to a botnet. Recall that Win32.Rmnet programs are multi-component file infectors capable of self-replication. The virus consists of several modules and can embed content into loaded web pages, redirect a browser to a site specified by criminals, and send information entered into web forms by a user to remote hosts. Win32.Rmnet viruses also steal passwords stored by popular FTP clients such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, and Bullet Proof FTP.
Doctor Web used a DNS sinkhole to hijack another Win32.Rmnet subnet. It was discovered that two new malware modules, both dubbed Trojan.Rmnet.19, were spread between nodes connected to the subnet. One of them can detect whether a virtual machine is running on the infected machine, while the other one is far more peculiar. The module emulates user input (namely, clicking on corresponding icons) to disable Microsoft Security Essential, Norton Antivirus, Eset NOD32, Avast, Bitdefender, and AVG.
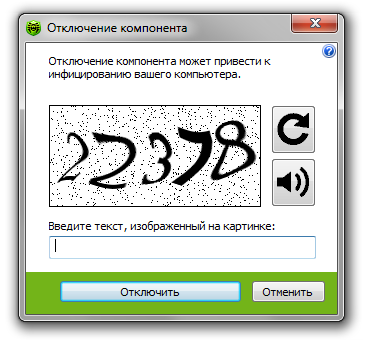
If Dr.Web anti-virus software is used on your computer, your system is in no danger because one has to enter a CAPTCHA code to unload Dr.Web components, and Trojan.Rmnet.19 can't do that.
A total of seven malicious modules are downloaded by the virus from a C&C server to machines on the subnet:
- New module that disables anti-virus software
- Cookie-stealing module
- Local FTP server
- Web-injection module
- FTP password-stealing module
- New module that detects virtual machines
- Module that facilitates remote access to the infected system.
Rmnet file infectors also incorporate the following basic components:
- Module loader;
- Backdoor;
- Anti-virus software removal module.
As of May 22, 2013, over 18,000 bots had contacted the server controlled by Doctor Web's anti-virus laboratory. The gathered statistics indicate that criminals chose Great Britain and Ireland as targets for their attacks: 15,253 infection incidents (84.5%) occurred there, while France ranks second with 1,434 incidents (7.9% of the total). Doctor Web's analysts are closely monitoring the situation.