Nasty Trojan infects 100 hosts in sixty minutes
Real-time threat news | Hot news | All the news | Virus alerts
April 8, 2013
The first time BackDoor.Bulknet.739 drew the interest of Doctor Web's analysts was in October 2012. They discovered that the Trojan was being used to connect computers into botnets and was enabling criminals to carry out mass spam mailings.
When the malicious code is executed in a compromised system, a Trojan downloader is extracted, after which another program, detected by Dr.Web as BackDoor.Bulknet.739, downloads BackDoor.Bulknet.847. The program uses its hardcoded encrypted list of domain names to pick an address to download the spam module. In response, the Trojan obtains the site's main web page and parses the HTML code in search for the image tag. The encrypted code of the main BackDoor.Bulknet.739 module is stored inside the image tag pair. The module is designed to send huge volumes of unsolicited e-mails.
BackDoor.Bulknet.739 receives from a remote server addresses to which it can send spam, an e-mail template file and a configuration file. BackDoor.Bulknet.739 utilizes a binary protocol to communicate with criminals. It can be directed to carry out updates, download new message templates and spam address lists, or stop sending messages. If the Trojan process terminates abnormally, it can generate a report and send it to the intruders.
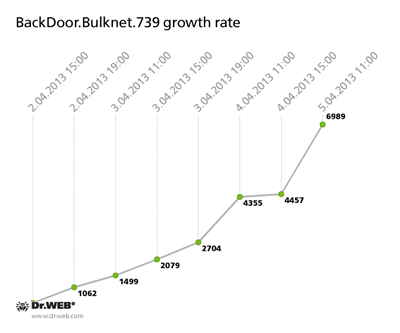
Doctor Web's analysts managed to hijack a server used to control the BackDoor.Bulknet.739 botnet and gathered statistics. As of April 5, 2013, over 7,000 bots were connected to the server. The graph below illustrates how the number increased in the period from April 2 to 5:
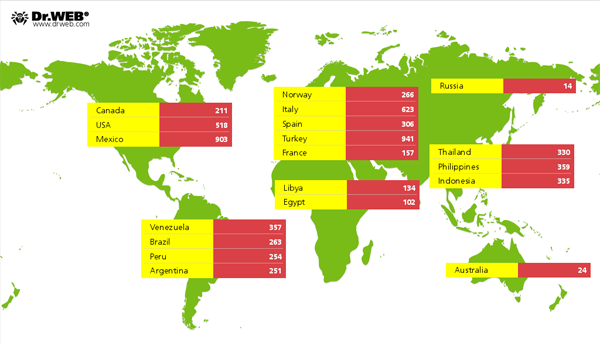
At the moment, the botnet BackDoor.Bulknet.739 is continuing to grow quite rapidly—an average of 100 machines are being infected every hour. The Trojan is spreading most widely in Italy, France, Turkey, the USA, Mexico and Thailand. The smallest number of compromised hosts is found in Russia and Australia. Here's how the infection is spreading across countries and continents:
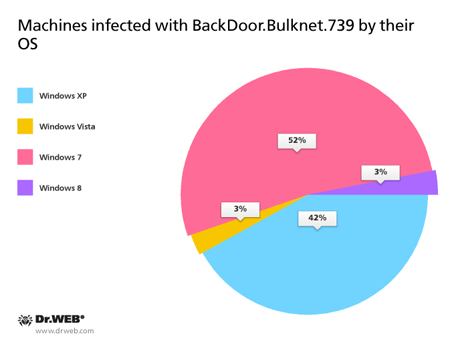
And here are the statistics regarding the operating systems of infected computers:
Doctor Web analysts are continuing to monitor the situation closely. BackDoor.Bulknet.739 poses no threat to systems protected with Dr.Web software since the malware's signature is present in the anti-virus's databases.