Trojans and other threats in March
Virus reviews | Hot news | All the news | Virus alerts
April 2, 2013
Viruses
According to statistics collected with Dr.Web CureIt!, Trojan.Hosts programs were the most common threats detected in March 2013. The hosts file containing DNS server IP addresses has been compromised 186,496 times which constitutes over 10% of the detected threat total.
More details about this threat can be found in a Doctor Web publication. One of the most common ways to spread these Trojans is through compromised sites: criminals use a special shell to modify the .htaccess file and then add a malicious script handler into the site's code. As a result, site visitors get a web page that contains links to a variety of malicious applications. Backdoors and downloader Trojans provide an alternative way to spread these programs. Trojan.Hosts.6815 is the most popular version in this malicious family.
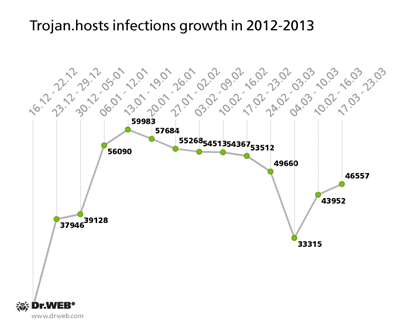
In early 2013, Trojan.Hosts’ rate of spread reached epidemic proportions, with over 9,500 infections detected daily by Dr.Web. The outbreak remained at its peak from January till mid-February. A slight decline was observed in early March, but after two weeks the number of infections started to grow again. The infection’s growth rate is illustrated in the graph below.
The worm Win32.HLLW.Phorpiex.54 is another common threat worth mentioning. This malware spreads with spam or replicates itself to removable data storage devices and provides criminals with unauthorized access to a compromised system.
A fake installer detected by Dr.Web anti-virus software as Trojan.SMSSend.2363 ranks fourth in the statistics. It is followed by BackDoor.IRC.NgrBot.42 and Win32.HLLP.Neshta. March’s top 20 threats, according to statistics gathered by Dr.Web CureIt!, are listed in the table below:
| Name | % |
|---|---|
| Trojan.Hosts | 10.96 |
| Trojan.Hosts.6815 | 1.62 |
| Win32.HLLW.Phorpiex.54 | 1.11 |
| Trojan.SMSSend.2363 | 1.02 |
| BackDoor.IRC.NgrBot.42 | 0.91 |
| Win32.HLLP.Neshta | 0.80 |
| Trojan.StartPage.48148 | 0.69 |
| Trojan.Click2.47013 | 0.66 |
| Trojan.MayachokMEM.4 | 0.59 |
| Win32.Sector.22 | 0.56 |
| Trojan.Mayachok.18024 | 0.56 |
| BackDoor.Andromeda.22 | 0.55 |
| Trojan.Mayachok.18582 | 0.54 |
| BackDoor.Butirat.245 | 0.51 |
| Trojan.Winlock.6426 | 0.47 |
| Exploit.CVE2012-1723.13 | 0.43 |
| Trojan.Popuper.42548 | 0.41 |
| Trojan.PWS.Panda.368 | 0.40 |
| Trojan.Hosts.6708 | 0.40 |
| Trojan.Rmnet | 0.39 |
Botnets
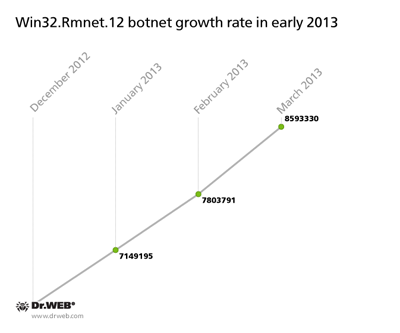
At the end of 2012, Doctor Web's analysts speculated that the botnet consisting of machines infected with Win32.Rmnet.12 would get bigger. As of December 2012, the total number of infected machines was 6.5 million, and by March 27, 2013, it reached 8,593,330, an increase of two million over the first three months of 2013. Thus, in January, the average daily growth of the Win32.Rmnet.12 botnet was about 15-25 thousand infected computers, and in February and March it was roughly 20-22 thousand machines. The botnet’s growth rate is illustrated in the chart below.
The file infector Win32.Rmnet.12 can perform backdoor tasks upon a corresponding command from a remote server. In addition, it can steal passwords stored by popular FTP clients. The stolen information can be used to mount network attacks or infect sites. The virus can embed content into loaded web pages (i.e., make web injections), redirect a browser to a site specified by criminals, and send user information submitted via web forms to remote hosts. Like other file infectors, Win32.Rmnet.12 can self-replicate.
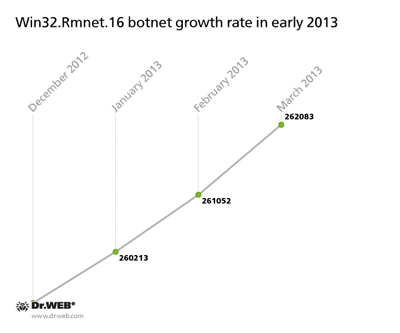
A botnet comprised of machines infected with Win32.Rmnet.16 — another file infector in the Win32.Rmnet — is growing too. In December, it included 259,458 infected hosts, and at the end of March, the number reached 262,083. In three months, it increased by only 2,625 nodes. The average daily growth totalled 20-30 infections. Follow the botnet’s growth rate in the chart below.
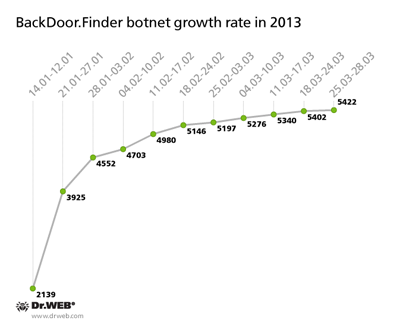
In January 2013, Doctor Web warned users about the malware BackDoor.Finder (mainly spread in the U.S.) which replaces search results in the following browsers: Microsoft Internet Explorer, Mozilla Firefox, Maxtron, Google Chrome, Safari, Opera, Netscape and Avant. To date, 5,422 bots have connected to control servers hijacked by Doctor Web. The botnet growth rate is as follows:
The threat of the month
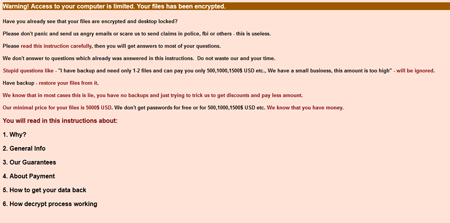
March also saw a large number of encryption Trojans, particularly Trojan.ArchiveLock.20 which places files into password-protected WinRAR archives. Earlier the Trojan targeted only Russian users, but in March multiple incidents involving the program were registered in European countries such as France and Spain. In the short period from March 23 to 26, 150 Italian users whose systems were compromised by the malware contacted Doctor Web's technical support and that number is rising.
To spread the Trojan, attackers launch a brute force attack on a target machine via RDP. When launched in an infected system, it uses the console version of WinRAR to place files on the compiled list into password-protected, self-extracting archives and employs a special utility to delete original files, after which they simply can't be restored.
More information about this malware can be found in a review published at Doctor Web's site.
In some cases, Doctor Web's analysts can restore files compressed by Trojan.ArchiveLock.20. If your files have been compromised by the Trojan, submit a request for curing via Doctor Web's site.
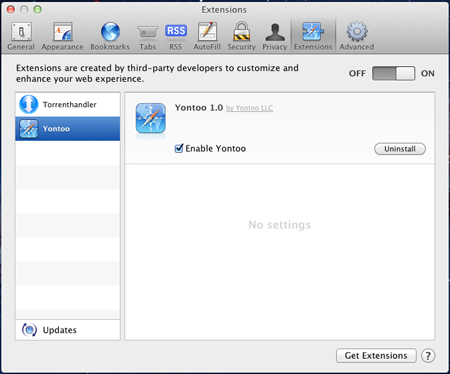
Advertising Trojan for Mac OS X
Adware for Windows is a common phenomenon, but such applications have recently been appearing for other platforms, in particular, Mac OS X. Trojan.Yontoo.1 is one of them.
This program is spread under the guise of video codecs, media players, video quality enhancement programs or download accelerators. On an infected Mac, Trojan.Yontoo.1 installs browser plugins for Safari, Google Chrome and Mozilla Firefox.
The plugin downloads a special file to embed advertising content under third-party affiliate programs into web pages loaded by users and transmits information about sites visited to a remote server. You can learn more about this threat from an analytical review published at Doctor Web's site.
Threats to Android
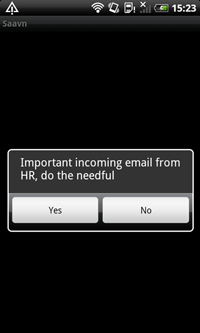
March turned out to be rich in Android viral events. A primitively designed Trojan dubbed Android.Biggboss was added to the Dr.Web virus database in the beginning of the month. This malware is embedded into other applications by criminals and spreads from sites hosting Android software catalogues. This Trojan targets users in India. When installed on a mobile device, Android.Biggboss loads as a system service at startup and displays a dialogue box informing the user that they have received an important message from an HR department. If the user agrees to view the message, the Trojan uses a browser to load an image containing a fake message from an HR department within the company TATA India Limited, which has nothing to do with the real TATA corporation. The message includes a tempting job description and prompts the user to transfer a certain amount of money to the criminals' account to hold the job for them.
 |
 |
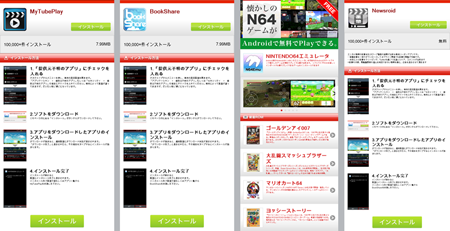
Trojan spyware programs designed to steal contact information on Android devices belonging to Japanese users were also found in large numbers in March. Dr.Web named them Android.EmailSpy.2.origin, Android.EmailSpy.3.origin and Android.EmailSpy.4.origin. As usual, they spread under the guise of various harmless applications such as media players, emulators and X-ray camera apps.
 | |
 |
 |
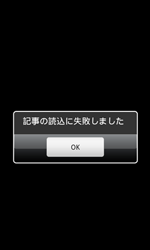
When launched, these programs imitate program initialization and then display an error message or notify the user that a requested operation can't be performed. At the same time, the Trojans collect information from the user's address book and covertly send this data to a remote server.
 |
 |
 |
It should be noted, that some versions of these malicious programs can send short messages to numbers found in the address book. Such messages contain links to download the Trojans and thus accelerate their spread.
Also discovered in March were several new versions of Android.SmsSend as well as commercial spyware, Android.Recon.3.origin and Program.Childtrack.1.origin in particular.
Malicious files detected in mail traffic in March
| 01.03.2013 00:00 - 31.03.2013 23:00 | ||
| 1 | Trojan.Packed | 1.32% |
| 2 | Trojan.Inject2.23 | 1.28% |
| 3 | Trojan.Necurs.97 | 1.27% |
| 4 | JS.Redirector.155 | 1.07% |
| 5 | Trojan.PWS.Stealer.1932 | 0.92% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.63% |
| 7 | BackDoor.Slym.1498 | 0.54% |
| 8 | Win32.HLLM.MyDoom.33808 | 0.48% |
| 9 | Trojan.PWS.Panda.547 | 0.44% |
| 10 | JS.Redirector.186 | 0.41% |
| 11 | Trojan.Packed.196 | 0.40% |
| 12 | SCRIPT.Virus | 0.33% |
| 13 | BackDoor.IRC.NgrBot.42 | 0.33% |
| 14 | Trojan.PWS.Panda.655 | 0.31% |
| 15 | Trojan.Siggen5.528 | 0.30% |
| 16 | Trojan.DownLoader1.64229 | 0.28% |
| 17 | Exploit.CVE2012-0158.19 | 0.26% |
| 18 | Trojan.KillProc.22394 | 0.26% |
| 19 | Win32.HLLM.Graz | 0.26% |
| 20 | Win32.HLLM.Beagle | 0.25% |
Malicious files detected on user computers in March
| 01.03.2013 00:00 - 31.03.2013 23:00 | ||
| 1 | SCRIPT.Virus | 0.65% |
| 2 | Adware.Downware.915 | 0.63% |
| 3 | Tool.Unwanted.JS.SMSFraud.26 | 0.54% |
| 4 | JS.IFrame.387 | 0.44% |
| 5 | Adware.Downware.179 | 0.44% |
| 6 | Tool.Unwanted.JS.SMSFraud.10 | 0.37% |
| 7 | JS.Redirector.175 | 0.34% |
| 8 | Trojan.Fraudster.407 | 0.33% |
| 9 | Trojan.Fraudster.394 | 0.33% |
| 10 | Adware.Webalta.11 | 0.33% |
| 11 | Trojan.Fraudster.424 | 0.31% |
| 12 | Adware.Downware.910 | 0.30% |
| 13 | Win32.HLLW.Shadow | 0.28% |
| 14 | Adware.InstallCore.99 | 0.28% |
| 15 | Trojan.PWS.SpySweep.389 | 0.27% |
| 16 | Tool.Skymonk.12 | 0.26% |
| 17 | Win32.HLLW.Autoruner.59834 | 0.26% |
| 18 | Adware.InstallCore.53 | 0.26% |
| 19 | Tool.Skymonk.11 | 0.25% |
| 20 | JS.Redirector.179 | 0.24% |