February 2013 virus activity review from Doctor Web
Virus reviews | All the news | Virus alerts
March 13, 2013
Viruses
According to statistics gathered by Dr.Web CureIt!, as before the Trojan.Mayachok programs were the most common threat in the last month of winter, with Trojan.Mayachok.18566 being the most frequently detected member of the Trojan family. Fake installers, dubbed Trojan.SMSSend by Dr.Web, were also found in large numbers, with Trojan.SMSSend.2363 topping the list.
Criminals disguise such programs as application installers that prompt users to send chargeable short messages or subscribe to certain services. Such installers normally do not contain the promised program and sometimes facilitate the spread of other malware. Many computers were also infected with BackDoor.IRC.NgrBot.42, Trojan.Click2.47013 and Win32.HLLP.Neshta. Information about the threats detected with Dr.Web CureIt! in February is presented in the following table:Threat %
| Threat | % |
|---|---|
| Trojan.MayachokMEM.4 | 2,00 |
| Trojan.SMSSend.2363 | 1,38 |
| Trojan.Mayachok.18566 | 1,20 |
| BackDoor.IRC.NgrBot.42 | 1,14 |
| Trojan.Click2.47013 | 0,79 |
| Win32.HLLP.Neshta | 0,78 |
| Trojan.StartPage.48148 | 0,77 |
| Trojan.Fraudster.245 | 0,73 |
| Trojan.Hosts.5268 | 0,70 |
| Win32.HLLW.Phorpiex.54 | 0,69 |
| Win32.Sector.22 | 0,65 |
| Trojan.Mayachok.18579 | 0,61 |
| Trojan.Hosts.6814 | 0,59 |
| Trojan.Hosts.6815 | 0,59 |
| Trojan.Hosts.6838 | 0,55 |
| BackDoor.Butirat.245 | 0,54 |
| Trojan.Hosts.6809 | 0,52 |
| Win32.HLLW.Gavir.ini | 0,51 |
| Exploit.CVE2012-1723.13 | 0,51 |
| Trojan.Mayachok.18397 | 0,47 |
Threat of the month: Linux.Sshdkit
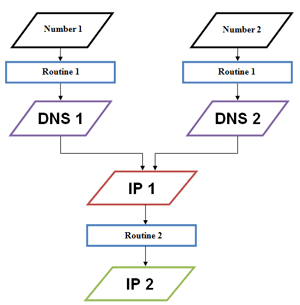
Linux.Sshdkit infects servers running under Linux and can be referred to as the most unusual threat discovered by Doctor Web in February. The Trojan is a library file available for 32- and 64-bit versions of Linux distributions. After successful installation, the Trojan injects its code into the process sshd and uses this process’s authorization routines. Once a session is started and a user enters their login and password, the Trojan sends them to a remote server. The control server IP is hardcoded into the malware, but a new command server address is generated. For this, Linux.Sshdkit uses a non-trivial routine.
Linux.Sshdkit uses a special algorithm to generate two DNS names, and if they both refer to the same IP address, that address is converted to a different IP to which the Trojan sends the stolen information. The routine used to generate command server addresses is outlined in the flowchart below.
Doctor Web's analysts hijacked several Linux.Sshdkit control servers. In early March, 476 infected servers contacted the hijacked control centers, but many of them belong to hosting providers and host a large number of websites to which the criminals now have access. Most of the infected servers (132 of them) are located in the USA. The Ukraine ranks second with 37 instances of infection and the Netherlands ranks third. Overall statistics acquired by Doctor Web using the hijacked Linux.Sshdkit control servers can be found in the table below.
| Country | Infected servers | % |
|---|---|---|
| USA | 132 | 27,7 |
| Ukraine | 37 | 7,8 |
| Netherlands | 29 | 6,1 |
| Thailand | 23 | 4,8 |
| Turkey | 22 | 4,6 |
| Germany | 19 | 4,0 |
| India | 19 | 4,0 |
| United Kingdom | 17 | 3,6 |
| Italy | 17 | 3,6 |
| France | 15 | 3,2 |
| Indonesia | 12 | 2,5 |
| Australia | 10 | 2,1 |
| Russia | 10 | 2,1 |
| Canada | 10 | 2,1 |
| Argentina | 10 | 2,1 |
| Brazil | 10 | 2,1 |
| South Korea | 7 | 1,5 |
| Vietnam | 7 | 1,5 |
| Chile | 6 | 1,3 |
| Spain | 6 | 1,3 |
| China | 5 | 1,1 |
| Romania | 5 | 1,1 |
| Mexico | 5 | 1,1 |
| South Africa | 4 | 0,8 |
| Other countries | 39 | 7,9 |
More information about this threat can be found in this informational material.
Trojan.Hosts and compromised sites
An upsurge of website attacks aimed at spreading malware was registered at the end of February and in early March. Criminals used stolen credentials to access websites via FTP, replaced the .htaccess file, and embedded their handler script into the code. As a result, the machines of users who visited such sites came under the threat of becoming infected by various Trojans. In particular, this technique is known to be employed to spread Trojan.Hosts programs that modify the file %systemroot%/system32/drivers/hosts, so that the browser redirects the user to a malignant page.
Threats to Android
February 2013 also saw quite a few threats to Android. A Trojan, spread via Google Play as a system-optimization utility, was added to the Dr.Web virus database at the beginning of the month and dubbed Android.Claco.1.origin. When launched on a device, the Trojan upon command can send short messages, load a specified web page, and upload the user's personal information (e.g., memory card contents, short messages, photos, and contact information from the address book) to a remote server. However, Android.Claco.1.origin is mostly remarkable for its ability to download other malware from a remote server to the device's memory card from which malignant programs can infect a Windows PC. Such downloaded files include an executable and the file autorun.inf to ensure that the malware will be launched automatically as soon as the infected memory card is connected to a computer. It should be noted, that the autorun feature is disabled by default in Windows Vista and later, so Windows machines are in no serious danger from Android.Claco.1.origin.
Android.Damon.1.origin, spread by criminals in modified applications via Chinese websites, was another notable malware in February. Android.Damon.1.origin can send short messages, make calls and load specified web pages when commanded by a remote server; it can also upload the device owner's personal information (e.g., address book contents, call history, GPS coordinates) to the server.
In addition, entries for new members of the Android.SmsSend malware family were added to the Dr.Web virus databases throughout the month.
Other threats in February
At the end of the long winter, online fraudsters became more active in their search for victims on dating sites. They typically act as emigrants or those of Russian descent which explains their good command of Russian. A scammer wins the confidence of the victim and then tells her of his intention to send his "darling" an expensive gift: a tablet, smart phone, or jewellery. Cybercriminals lure potential victims to a fake courier service site, where they are asked to pay shipping costs. Naturally, soon after payment, the courier service and the generous suitor vanish. More details about this method of fraud can be found in our informational material.
In early February, there were cases of Facebook API being used to spread malware. The incident is described in detail in a review published at news.drweb.com.