November virus activity review: multi-lockers, dangerous downloaders and other threats
Virus reviews | All the news | Virus alerts
December 4, 2012
Viruses
Trojan.Mayachok.1 is malicious program that blocks Internet access on an infected computer. Found in large numbers a few months ago, it dropped to twelfth position among malware most frequently detected by Dr.Web CureIt!. At the same time, its modification Trojan.Mayachok.17994 has become the absolute leader. This version of the Trojan is a next step in the development of Trojan.Mayachok.17727, about which we already reported in one of our news stories.
BackDoor.IRC.NgrBot.42 is among the leaders in terms of the number of infections detected. Trojans of this family communicate with a remote server via the IRC protocol and can execute a vast variety of commands from criminals. The malicious payload of BackDoor.IRC.NgrBot.42 allows it to destroy the boot record if the malware's integrity has been compromised, block access to anti-virus company websites, and intercept logins and passwords used to log on to various online resources. BackDoor.IRC.NgrBot.42 infects all removable data-storage devices connected to a computer by placing its executable into the Recycle Bin folder. After that BackDoor.IRC.NgrBot.42 сhides folders on the infected device and in their place creates shortcuts with the corresponding file names. The shortcuts link to the Trojan executable. Thus, when trying to open any folder on the infected device, the user runs the malicious application. In addition, the Trojan can place the file autorun.inf in the root folder of the device for automatic launch once the device is connected to a computer.
Samples of the Trojan.Carberp, Trojan.SMSSend and Trojan.DownLoader malware families also appear in infection statistics collected by Dr.Web CureIt!. The top 20 most widespread threats detected on PCs by Dr.Web CureIt! in November can be found in the table below.
| Threat | % |
|---|---|
| Trojan.MayachokMEM.5 | 1,94% |
| Trojan.Mayachok.17994 | 1,58% |
| Exploit.CVE2012-1723.13 | 1,17% |
| BackDoor.IRC.NgrBot.42 | 1,13% |
| Trojan.StartPage.48148 | 1,13% |
| Java.Downloader.697 | 1,10% |
| BackDoor.Butirat.201 | 1,10% |
| Trojan.SMSSend.2363 | 1,00% |
| Trojan.Carberp.789 | 1,00% |
| Win32.HLLP.Neshta | 0,99% |
Botnets
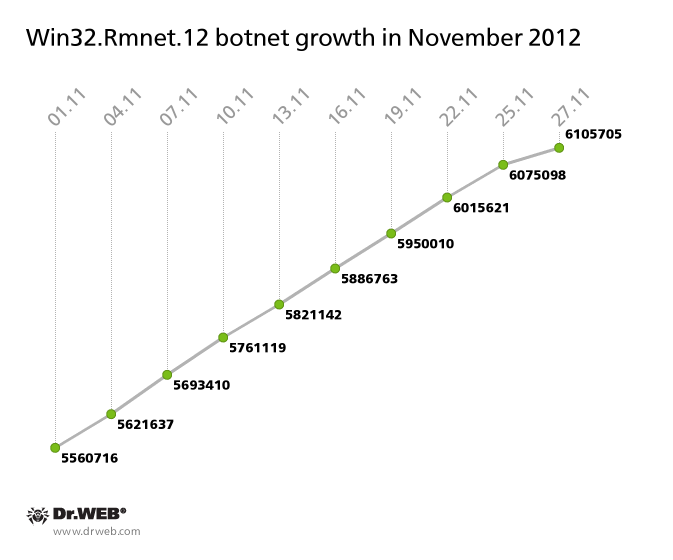
Doctor Web continues to monitor the activities of the most active botnets encompassing computers throughout the world. The botnet that consists of PCs infected with Win32.Rmnet.12. grew steadily through November 2012. The overall number of its bots increased by another 545,000 and exceeded six million. The Win32.Rmnet.12 botnet’s growth in November 2012 is illustrated in the graph below.
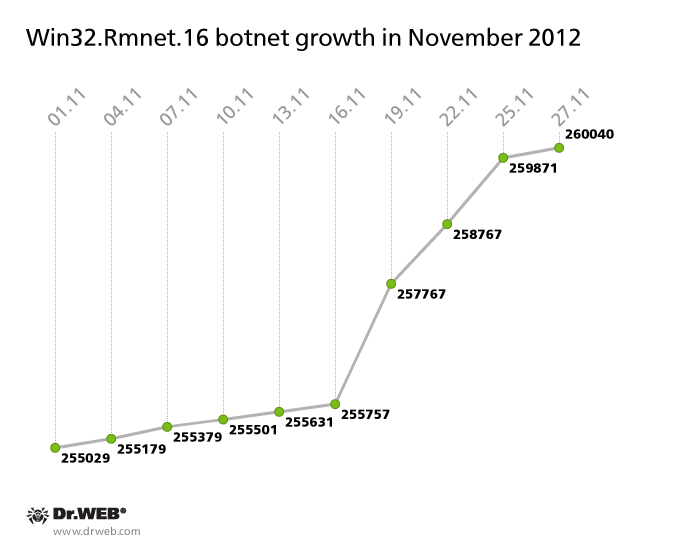
At the same time, the Win32.Rmnet.16 botnet growth rate slowed somewhat. Thus, over the last 30 days this botnet was joined by only 5,011 newly infected computers, which is 70% less than October's figures. Yet in the second half of November, the rate of infection increased. The network’s growth progress is presented in the graph below.
As for the well-known Backdoor.Flashback.39 that infected over 800,000 Apple-compatible computers worldwide in the spring of this year, we can say with certainty that the number of infected hosts is decreasing rapidly. So, as of November 26, the Backdoor.Flashback.39 botnet consisted of only 90,947 infected machines, which is 14% less than in the previous month. At the same time, the botnet practically stopped growing.
Multi-lockers
The massive spread of Trojan lockers, dubbed multi-lockers, became one of the most significant trends in November 2012. In addition to the traditional ransomware, this month saw a shift towards this type of threat being spread by botnets made up of malicious downloaders. BackDoor.Andromeda programs were extensively used to download multi-lockers into compromised systems.
Trojan.Winlock.7372 is a typical representative of this ransomware category. Its detailed description was the subject of a recent review published on the Doctor Web site. Unlike other ransomware, multi-lockers incorporate no images, texts or other resources necessary to display an extortion message on the screen once access to Windows has been blocked. All the necessary elements are downloaded from a remote server. Some modifications of such blockers bypass the Windows Firewall and do not allow the user to run a variety of applications on an infected computer. Such applications include Task Manager, Notepad, Registry Editor, Command Prompt, System Configuration, Internet Explorer, Google Chrome, Mozilla Firefox, Opera, ProcessHacker and Process Monitor.
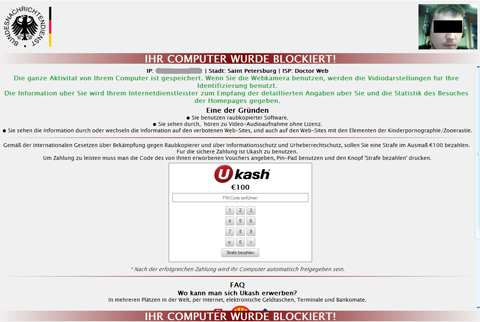
At the end of the month, Doctor Web's analysts discovered Trojan.Winlock.7372 which can capture images from a web camera connected to a computer. The message, allegedly from state law enforcement agencies, informs a victim that all their actions on the computer are logged and their picture, obtained with a web camera, is being stored for later identification and the acquisition of more detailed personal information.
To unlock the computer, the Trojan demands that the victim enter a ransom payment transaction code. The entered code is transmitted to the controlling server and validated. If the payment is confirmed, the control center commands the Trojan to unlock the computer. The amount to be paid for this service is 100 euros or 150 dollars. A detailed description of the threat has also been published in a separate review.
The growing number of multi-locker infections indicates that virus writers are moving away from traditional Windows lockers with the standard architecture, many of which were created with virus creation toolkits. Trojan extortionists are gradually incorporating a more complex payload and tend to target computers outside Russia. According to statistics collected by Doctor Web, multi-lockers are largely found in the U.S. and Western Europe.
Threat of the month: Trojan.Gapz.1
Trojan Trojan.Gapz.1 has been known for quite a long time, but the plugins it installs in an infected system, namely Trojan.Winlock.7384 (mentioned earlier in this review) is garnering attention.
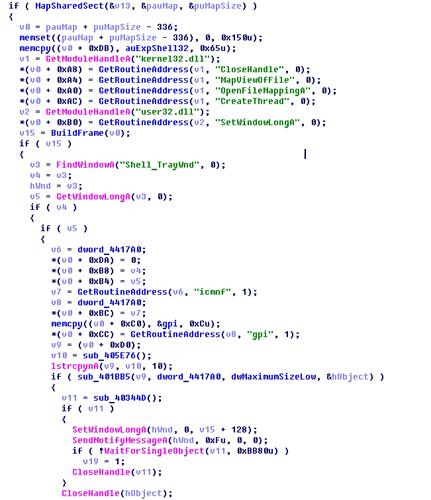
Trojan.Gapz.1 runs under 32- and 64-bit versions of Windows. This malware can bypass the UAC which prevents the unauthorized launch of executables in a system. Trojan.Gapz.1 then analyzes the structure of the infected computer's hard drive, creates a special image, and writes it in the reserved sectors of the disk. The Trojan then makes the system loader load and run a malicious program.
Trojan.Gapz.1’s main objective is to create an environment suitable for loading a binary image containing several modules from the disk. These modules have different payloads; one of them is a malicious UCash application. More information about Trojan.Gapz.1 can be found in a review published previously at news.drweb.com.
Dangerous downloader
On November 14, Doctor Web warned users about a dangerous Trojan downloader dubbed Trojan.DownLoader7.21125 This program enables other malware to get onto an infected computer. Currently Trojan.DownLoader7.21125 downloads and installs onto an infected computer a bitcoin mining program, repacked copies of itself, and the following malware:
- BackDoor.Andromeda.22, a widespread Trojan downloader that can also download other malware and install it on an infected computer.
- Trojan.Rodricter.21, a multi-component rootkit whose dropper is equipped with anti-debugging features. It exploits OS vulnerabilities to elevate its privileges. It also disables UAC in both 32- and 64-bit versions of Windows. It changes Mozilla Firefox and Internet Explorer settings. The main function of its core module is to intercept traffic on an infected PC.
- Trojan.PWS.Multi.879, a malicious program that can steal passwords stored by a number of popular applications, including ICQ, Yahoo! Messenger, FTP Commander, Paltalk, AIM, Google Talk, MSN Messenger, Miranda and Trillian.
- BackDoor.HostBooter.3, a program designed to perform DDoS attacks, as well as download and run files upon command from a control server.
More detailed information about Trojan.DownLoader7.21125 can be found in a corresponding review published by Doctor Web.
Threats to Android
In November the Dr.Web virus databases received records concerning yet another example of commercial spyware; it quickly joined the ranks of other mainstream threats to the Android OS. Program.Jianspy.1.origin and Program.Spyera.1.origin are among such threats. These perform tasks typical of programs of this class: they collect information about SMS correspondence and calls and determine a device's location.
New versions of well-known Android.SmsSend programs, which deplete funds from user accounts by sending chargeable messages at premium numbers, never cease to emerge. Doctor Web's analysts discover such applications regularly. They are all promptly added to the virus databases.
Malicious files detected in mail traffic in November
| 01.11.2012 00:00 - 30.11.2012 23:00 | ||
| 1 | JS.Redirector.162 | 1.13% |
| 2 | Trojan.Winlock.6049 | 1.06% |
| 3 | Trojan.PWS.Stealer.946 | 0.96% |
| 4 | JS.Redirector.166 | 0.96% |
| 5 | Trojan.Necurs.97 | 0.74% |
| 6 | Trojan.PWS.Panda.2401 | 0.74% |
| 7 | JS.Redirector.168 | 0.67% |
| 8 | Trojan.Oficla.zip | 0.59% |
| 9 | Trojan.PWS.Mailer.26 | 0.52% |
| 10 | Win32.HLLM.MyDoom.54464 | 0.50% |
| 11 | BackDoor.Andromeda.22 | 0.50% |
| 12 | BackDoor.IRC.NgrBot.146 | 0.41% |
| 13 | Trojan.DownLoad3.17685 | 0.41% |
| 14 | Trojan.PWS.Panda.786 | 0.33% |
| 15 | Trojan.Packed.196 | 0.33% |
| 16 | SCRIPT.Virus | 0.28% |
| 17 | Trojan.DownLoad3.17030 | 0.28% |
| 18 | Win32.HLLM.MyDoom.33808 | 0.26% |
| 19 | Win32.HLLM.Beagle | 0.24% |
| 20 | Trojan.PWS.Panda.655 | 0.24% |
Malicious files detected on user computers in November
| 01.11.2012 00:00 - 30.11.2012 23:00 | ||
| 1 | Adware.Downware.533 | 0.69% |
| 2 | SCRIPT.Virus | 0.60% |
| 3 | Tool.Unwanted.JS.SMSFraud.26 | 0.57% |
| 4 | JS.IFrame.356 | 0.52% |
| 5 | Adware.Downware.179 | 0.44% |
| 6 | Tool.Unwanted.JS.SMSFraud.10 | 0.42% |
| 7 | Tool.Skymonk.6 | 0.37% |
| 8 | Adware.Downware.426 | 0.33% |
| 9 | Win32.HLLW.Shadow | 0.30% |
| 10 | Win32.HLLW.Autoruner.59834 | 0.30% |
| 11 | Adware.Downware.498 | 0.30% |
| 12 | Trojan.Fraudster.296 | 0.29% |
| 13 | Trojan.Fraudster.329 | 0.29% |
| 14 | Trojan.Fraudster.344 | 0.27% |
| 15 | Adware.InstallCore.53 | 0.27% |
| 16 | Adware.Downware.540 | 0.26% |
| 17 | Adware.Webalta.9 | 0.25% |
| 18 | Adware.Downware.316 | 0.25% |
| 19 | Trojan.SMSSend.2363 | 0.24% |
| 20 | JS.Redirector.153 | 0.24% |