September 2012 virus activity review: new dangerous Trojan family and spyware for mobile devices
Virus reviews | All the news
October 1, 2012
Viruses
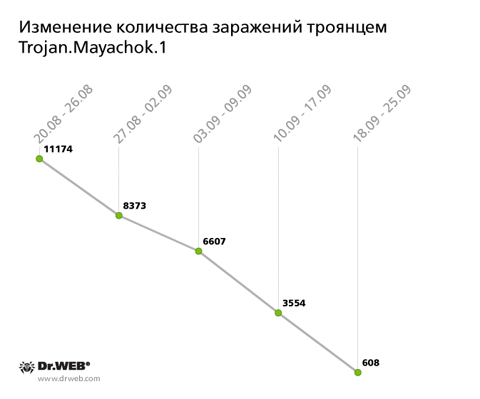
Compared with August, the virus activity pattern has changed, as revealed by Dr.Web CureIt! on user computers in September. So, Trojan Trojan.Mayachok.1 was top-ranked among the most common threats for at least three months. It still holds the top spot, but the total number of its infections has declined over the last month more than 15 times, from 74,701 detected samples in August down to September. Statistics regarding infections per week also indicate a significant decline as indicated in the graph below.
Doctor Web's virus analysts attribute this trend to the emergence of an entire group of modifications of this threat, and these programs are quite different from the first Trojan version. In particular, in September nine entries for programs of this class were added to the Dr.Web virus databases. They mainly differ by some technical details. It is likely that in the near future we can expect the appearance of other versions of this Trojan featuring different payload and design principles. Please bear in mind that the main purpose of the Trojan.Mayachok family is to inject code into the web pages users load in their browsers.
BackDoor.Butirat.91 is still second in popularity in the virus statistics. It should also be noted that the number of infections involving this malware per month declined by 20 percent. One of the main objectives of BackDoor.Butirat.91 is to steal passwords stored by popular FTP clients, such as FlashFXP, Total Commander, FileZilla, FAR, WinSCP, FtpCommander, and SmartFTP, and transfer them to criminals. The Trojan is able to download executables from remote nodes, run them on an infected machine, and adjust various web-traffic counters. The average user whose system has been infected with the Trojan risks having all kinds of confidential data falling into the wrong hands, as well as losing control over their PC. More detailed informationе about this threat can be found in Doctor Web news stories.
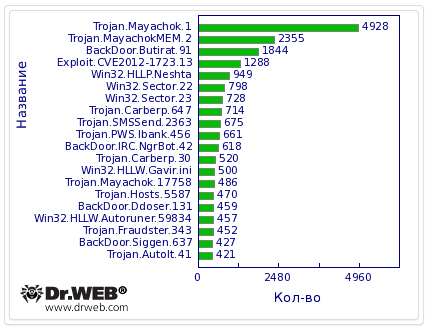
Also, the most common threats include the Delphi-written Win32.HLLP.Neshta, numerous banking Trojans including Trojan.Carberp, and fake installers detected by Dr.Web as Trojan.SMSSend. Statistics regarding the most common threats are shown in the graph below.
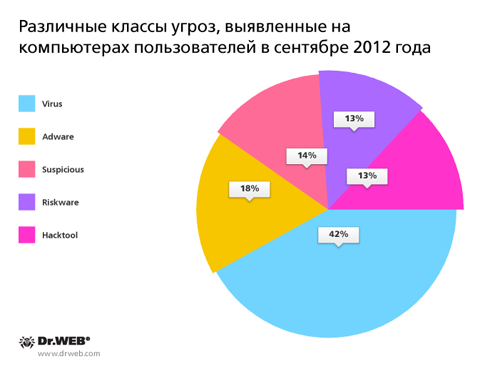
The distribution of the various classes of malware detected over the past month is shown in the diagram.
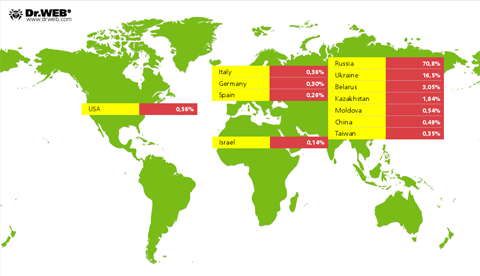
Statistics on the number of threats identified with Dr.Web anti-virus software in different regions of the world are presented below.
Botnets
Statistics regarding the Backdoor.Flashback.39 botnet, consisting of infected Mac OS X machines, demonstrates the reduction in the number of infections. In September, the number of infected Macs decreased by 10 percent, from 127,681 to 115,179, while the growth of the botnet has virtually stopped with one or two new joiners per day. More detailed information about the current state of the botnet can be found on a special website created by Doctor Web.
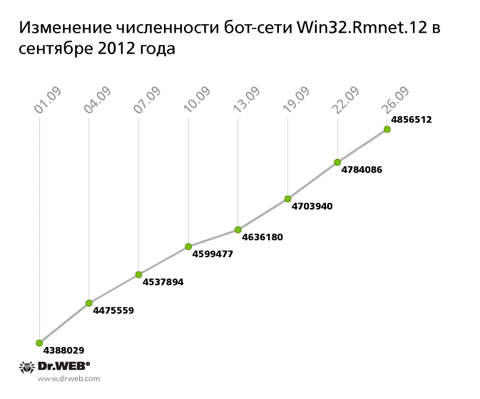
At the same time, the botnet that consists of computers compromised by the file infector Win32.Rmnet.12 keeps breaking all records. In the past month, it increased by another 500,000 infected hosts, so soon it will exceed 5 million. The growth of this botnet is shown in the graph below.
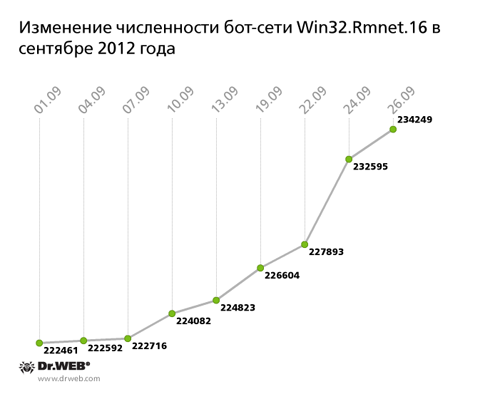
A related botnet built with another file infector Win32.Rmnet.16 also demonstrates steady growth. On average, it grows by several hundred newly infected PCs per day, and its total number of bots has exceeded 230,000. The botnet's growth rate is shown on the graph below.
The new version of BackDoor.BlackEnergy
BackDoor.BlackEnergy malware have been known to analysts since March 2011 and are often found in the wild. BackDoor.BlackEnergy programs are multifunctional backdoors that can, among other things, download executables from a malicious server and run them in the infected system. BackDoor.BlackEnergy supports a large number of plug-ins and for a long time was used to maintain one of the largest botnets employed to send out spam. A combined effort of several companies and security experts resulted in shutting down several of its control servers in July 2012. The servers controlled a large portion of the infected hosts, so the worldwide bulk of spam decreased substantially. Apparently, people behind this network of zombie computers keep trying to restore its capacity, as evidenced by the emergence of a new version of the Trojan.
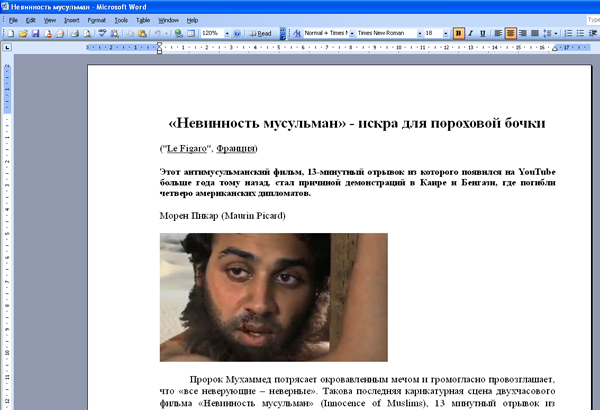
The latest backdoor modification, added to the Dr.Web virus databases as BackDoor.BlackEnergy.18, is distributed by means of e-mails with an attached Microsoft Word document. To draw users' attention to the message, criminals use the topic of the scandal-ridden Innocence of Muslims film, which triggered a wave of protests around the world resulting in human casualties. The attached document, detected by Dr.Web anti-virus software as Exploit.CVE2012-0158.14, contains code that exploits an ActiveX vulnerability. ActiveX is used by Microsoft Word and some other products for Windows. If you try to open the document, two files will be saved into a temporary folder. One of them is a dropper for BackDoor.BlackEnergy.18 that installs a malicious driver into the system folder.
Threat of the month: Trojan.Mayachok.17727
It's already been mentioned that Trojan.Mayachok.1 is gradually losing ground to new modifications of the threat. Trojan.Mayachok.17727 is one of these modifications; its signature was added to the Dr.Web virus database in September 2012.
The Trojan program consists of two components: a dropper and a dynamic link library that carries the payload. In the directory %MYDOCUMENTS%, the Trojan-library-containing dropper creates a folder called IntMayak. It is in this folder that the decrypted library and a REG-file used to register the library in the system are temporarily stored. Then the dropper searches the memory for explorer.exe and injects its code into the process. This code copies the malignant library into the system directory % SYSTEM32%. Trojan.Mayachok.17727 imports the REG-file into the registry branch to load the library code into all processes. Then the dropper removes its temporary files and the IntMayak folder, deletes cookies, and clears the Internet Explorer cache to hide how it managed to get into the system.
The malicious library works with Microsoft Internet Explorer, Opera, Mozilla Firefox, and Google Chrome. While running in the system, Trojan.Mayachok.17727 saves onto the disk its encrypted configuration file, which stores a list of control servers, a script injected into the code of web pages loaded in the browser, and other parameters.
Compared with Trojan.Mayachok.1, the Trojan code incorporates significant changes: the routine checking for the presence of virtualization software in the system has been removed, as have the number of supported processes and the procedure for comparing their names, and there is no configuration file integrity verification. It is worth mentioning that Trojan.Mayachok was one of the first Trojans technically capable of infecting the VBR; it later became known that this capability had been purchased from other virus writers rather than created by the Trojan’s designers themselves. For example, similar code was found in Trojan.Carberp.
Threats to Android
In September 2012, the Dr.Web virus databases expanded with a set of entries for threats to Google Android. Android.EmailSpy.origin is one such program targeting devices of Japanese users. The Trojan steals contact information from the Android address book, particularly e-mail addresses which can then be used by criminals to organize mass mailings. In the second half of the month, Trojan Android.SmsSpy.6.origin, which intercepts short messages on an infected device, was added to the virus database. The Trojan was distributed in France: mass SMS messages offered users the opportunity to download a Flash player update from a malicious site. The update disguised the malignant program.
Other additions to the database include Android.Iconos.3.origin, distributed under the guise of Call Cheater Lite. In addition to having basic features, Android.Iconos.3.origin collected personal information stored on a mobile device and sent it without the user's consent to a remote server along with chargeable short messages. In early September, Android.Loozfon.origin and (a bit later) Android.Loozfon.2.origin spyware were added to the virus database. Those mainly target devices belonging to Japanese users. These applications are also used to compromise personal data on mobile devices running Android. These fangerous spyware programs include Program.AccuTrack.origin and Program.Spycontrol.2.origin, which are also capable of transmitting sensitive data from the device to a remote server.
Android.Temai.origin, registered in the virus database in September 2012, was intended to adjust installation counters on websites distributing mobile software. The Trojan downloaded an application to the infected device, sent a successful installation notification to the site, and then deleted the downloaded package. In addition to the malware, entries concerning new versions of commercial adware, such as Adware.Leadbolt.2.origin and Adware.Startapp.5.origin, appeared in the database used by Dr.Web for Android and Dr.Web for Android Light.
Other threats in September
On August 26, FireEye reported the discovery of a critical vulnerability in Java Runtime Environment versions 1.7x; this vulnerability was designated as CVE-2012-4681. Oracle released a security patch only on August 30, and, therefore, the vulnerability remained unclosed for at least four days—an opportunity that criminals were quick to take advantage of. Doctor Web determined that a related exploit was used to spread some malicious software, including Trojan.Rodricter. More information about this threat can be obtained from the material published by Doctor Web.
Malicious files detected in mail traffic in October
| 01.09.2012 00:00 - 30.09.2012 23:00 | ||
| 1 | Trojan.SMSSend.3245 | 1.07% |
| 2 | Trojan.Necurs.97 | 0.96% |
| 3 | BackDoor.Andromeda.22 | 0.72% |
| 4 | Win32.HLLM.MyDoom.54464 | 0.54% |
| 5 | Exploit.CVE2010-3333.6 | 0.51% |
| 6 | Trojan.Oficla.zip | 0.48% |
| 7 | Win32.HLLM.MyDoom.33808 | 0.43% |
| 8 | Exploit.BlackHole.12 | 0.37% |
| 9 | Trojan.PWS.Panda.2401 | 0.32% |
| 10 | SCRIPT.Virus | 0.29% |
| 11 | Win32.HLLM.Netsky.35328 | 0.27% |
| 12 | Win32.HLLM.Beagle | 0.27% |
| 13 | Trojan.DownLoad2.39083 | 0.27% |
| 14 | Trojan.PWS.Panda.547 | 0.21% |
| 15 | W97M.Keylog.1 | 0.21% |
| 16 | Exploit.PDF.2990 | 0.21% |
| 17 | Trojan.DownLoader6.56603 | 0.21% |
| 18 | Trojan.Siggen4.19531 | 0.21% |
| 19 | Win32.HLLM.Netsky.18401 | 0.19% |
| 20 | Trojan.PWS.Panda.786 | 0.16% |
Malicious files detected on user computers in October
| 01.09.2012 00:00 - 30.09.2012 23:00 | ||
| 1 | SCRIPT.Virus | 0.50% |
| 2 | Trojan.Fraudster.343 | 0.48% |
| 3 | Trojan.Inject1.9025 | 0.47% |
| 4 | Trojan.Fraudster.329 | 0.37% |
| 5 | Tool.Unwanted.JS.SMSFraud.10 | 0.37% |
| 6 | Adware.Downware.179 | 0.36% |
| 7 | Trojan.Fraudster.296 | 0.31% |
| 8 | Adware.Downware.426 | 0.30% |
| 9 | Trojan.Fraudster.256 | 0.30% |
| 10 | Trojan.SMSSend.3249 | 0.28% |
| 11 | Win32.HLLW.Autoruner.59834 | 0.27% |
| 12 | Exploit.CVE2012-1723.13 | 0.27% |
| 13 | Trojan.Fraudster.320 | 0.27% |
| 14 | Win32.HLLW.Shadow | 0.27% |
| 15 | Trojan.Fraudster.344 | 0.26% |
| 16 | JS.IFrame.317 | 0.26% |
| 17 | Adware.Downware.316 | 0.25% |
| 18 | Trojan.Mayachok.1 | 0.24% |
| 19 | Tool.Unwanted.JS.SMSFraud.15 | 0.24% |
| 20 | Tool.Skymonk.3 | 0.23% |