August 2012 virus activity review: growing botnets, a Java vulnerability, and new threats to Android
Virus reviews | Real-time threat news | All the news | Virus alerts
September 3, 2012
Viruses
According to statistics gathered by Dr.Web CureIt! in August 2012, Trojan.Mayachok.1 is still the most common malicious software on computers, but the number of its detections increased by 6.5% against the previous month’s figure. Criminals began incorporating Trojan.Mayachok.1 into fake installers detected by Dr.Web anti-virus software as Trojan.SMSSend, which may be contributing to the number's rise. Trojan.Mayachok.1 is the statistical leader by a wide margin, followed by BackDoor.Butirat.91 which can execute commands from a remote server and download and launch various applications on an infected machine. In terms of detection frequency, it is 87.1% behind Trojan.Mayachok.1. At the same time, the total number of computers infected with BackDoor.Butirat.91 grew by 41.8% in the past month.
The number of detected Trojan.SMSSend programs remained the same, but it should be noted that though until recently such Trojans were considered relatively harmless, they have become a significant threat to system security. TheTrojan.SMSSend malware family includes archive files that imitate the installation wizard incorporated into popular applications. When a user runs the program, they are prompted to send a paid short message or specify their cell phone number to receive a code which they then enter and thus subscribe to a useless but chargeable service. The archive, as a rule, contains nothing but "junk"; in other words, the fraud victim does not get what they paid for.
However, the number of gullible Internet users appears to gradually be declining, and profits from the "fake installer business" are going down too. Otherwise, it is difficult to explain why the authors of a partner fake installer distribution program—ZIPPRO—began to install malicious software such as Trojan.Mayachok.1 in systems where the archive file is opened. The main danger here lies in the fact that a system can get infected upon launching the fake installer even if the user eventually discards the installation.
The most widely spread malware detected on user machines by Dr.Web CureIt! in August are listed in the following table:
| # | Threat name | Threat type | Detections | percent |
|---|---|---|---|---|
| 1 | Trojan.Mayachok.1 | virus | 74701 | 6,90% |
| 2 | BackDoor.Butirat.91 | virus | 9667 | 0,89% |
| 3 | Trojan.SMSSend.2363 | virus | 5667 | 0,52% |
| 4 | Trojan.Carberp.30 | virus | 5421 | 0,50% |
| 5 | Trojan.Hosts.5940 | virus | 4025 | 0,37% |
| 6 | Trojan.Fraudster.292 | virus | 3772 | 0,35% |
| 7 | Win32.HLLW.Gavir.ini | virus | 3458 | 0,32% |
| 8 | BackDoor.Ddoser.131 | virus | 3180 | 0,29% |
| 9 | Win32.HLLP.Neshta | virus | 2941 | 0,27% |
| 10 | Win32.HLLM.Reset.395 | virus | 2580 | 0,24% |
BackDoor.Andromeda.22 leads among malware detected in mail traffic. The second and third positions are occupied by Trojan.Oficla.zip and Trojan.Necurs.21, respectively. Win32.HLLM.MyDoom.54464, Win32.HLLM.MyDoom.33808, and Win32.HLLM.Netsky.35328 are found in large quantities too.
Botnets
Despite the fact that more than four months have passed since the discovery of the largest-ever Mac botnet, comprised of machines infected with Backdoor.Flashback.39, it would be premature to talk about its dissolution. At the moment, the botnet consists of 126,781 infected machines, which is 21,711 fewer hosts than at the end of July. In general, the rate of the BackDoor.Flashback.39 botnet’s reduction has declined noticeably (the malicious network was losing 76,524 machines a month until August).
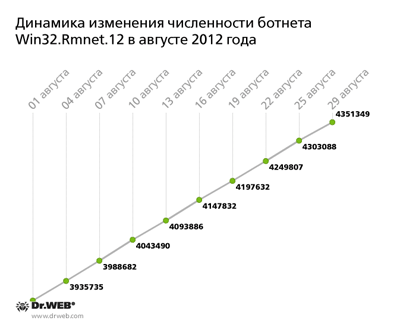
The Win32.Rmnet.12 botnet exceeded four million nodes during August and reached 4,351,349 infected computers. One can say that this dangerous file infector is spreading as fast as before: If in July 480,000 infected systems joined the network, in August about 500,000 compromised hosts connected to the net. Win32.Rmnet.12 network’s growth rate is illustrated in the graph below:
Please note that the program poses a threat mainly to systems located in Southeast Asia; the largest number of infections are being discovered in such countries as Indonesia, Bangladesh, Vietnam, and India. To date, in Russia 105,268 infected machines have been found, which accounts for 2.4% of the total number of infected computers.
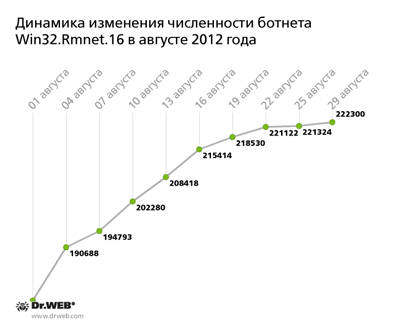
The Win32.Rmnet.16 botnet is growing gradually, too, but not as rapidly as before. Thus, in August about 67,000 infected PCs joined this botnet, while the total number of bots was 222,300. The average daily growth rate was approximately 1.5-2 thousand infected hosts, but by the end of the month, the rate fell sharply. The graph below shows the growth rate for the number of computers infected with Win32.Rmnet.16.
Note that though similar to Win32.Rmnet.12, the file infector Win32.Rmnet.16 has some distinguishing features. For example, Win32.Rmnet.16 uses a digital signature to sign the IP address of its control server, while the server addresses themselves are generated according to a special algorithm. The malware can execute commands received from the remote server, particularly those that download and run arbitrary files, update the virus, take screenshots and send them to the criminals, and even render the operating system non-operationa. In addition, Win32.Rmnet.16 can end processes of the majority of popular anti-virus programs, which makes the program even more dangerous.
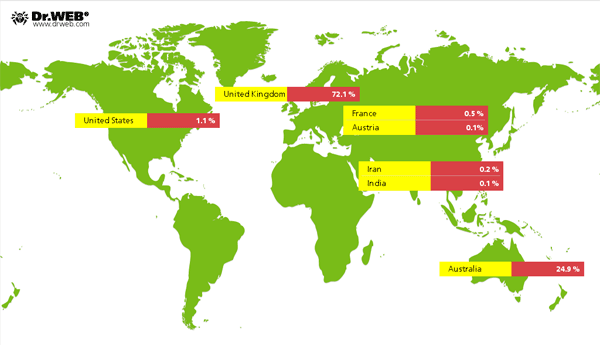
Most systems compromised by the virus are located in the United Kingdom (72.1%) and Australia (24.9%). There are few machines infected with Win32.Rmnet.16 in Russia. Countries affected by the greatest number of system infections are marked on the map below.
A critical Java vulnerability
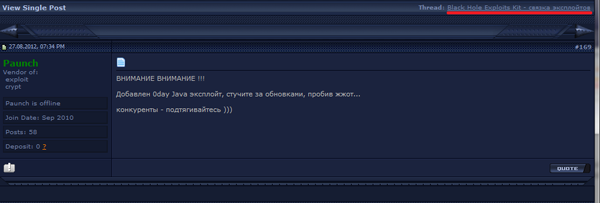
At the end of August, the company FireEye, followed by other developers of anti-virus software, reported finding the critical vulnerability CVE-2012-4681 in Java Runtime Environment versions 1.7x. Initial descriptions of this vulnerability were published on August 26, and the next day a corresponding exploit appeared in the BlackHole Exploit Kit widely distributed among criminals. A respective security update from Oracle was released on August 30. Therefore, systems running Java were vulnerable to hackers for at least four days.
Doctor Web analysts conducted their own investigation into the incident and revealed a number of TDSs (Traffic Direction System) being used to redirect users to specially created web sites that spread malware. In one of the confirmed cases, intruders modified the .htaccess files on compromised sites to redirect users to resources spreading malware. Special scripts generate destination addresses which change every hour. The final URL in the redirection chain depends on the target operating system. Thus, Mac OS X users reached a website from whichBackDoor.Flashback.39 could be downloaded (the site is no longer operational); owners of mobile devices and Linux users arrived at a page of the search engine Find-and-Go; while under Windows, a web page containing code invoking various exploits was loaded.
Currently Java vulnerabilities are being exploited to spread Trojan.Rodricter.21 which can fake search engine result pages and increase site hit counts. Also discovered was another redirection chain leading users to a site spreading Trojan.DownLoader6.29607.
Doctor Web believes such Java vulnerability exploits pose a severe threat and may cause serious damage. Analysts strongly recommend that users install the latest software security updates.
Threats to Android
August saw an abundance of threats targeting Google Android. During the month, a record high number of sites were compromised to spread malicious programs for mobile platforms. Criminals changed website settings to ensure that after opening a page, users were redirected to another site—a malignant one spreading Android.SmsSend.
Android.SmsSend.186.origin was another piece of malware for Android discovered in August. Unlike most other Android.SmsSend malware families, the Trojan is downloaded to a mobile device by a special dropper. Another distinguishing feature of Android.SmsSend.186.origin is its ability to resist attempts to remove it.
Threats to Android that were added to the Dr.Web database in August also include Android.Luckycat.1.origin which is designed to steal user information (such as the device IMEI, phone number, and stored files) and transfer the data to a server belonging to criminals. In addition, Android.Luckycat.1.origin can execute incoming commands from attackers. A group of malicious programs for mobile platforms that is related to the famous family of Zeus/SpyEye malware was also discovered. These are Trojans, designed to steal passwords. A version for Android has been added to the database as Android.Panda.2.origin. BlackBerry versions were registered as BlackBerry.Panda.1, BlackBerry.Panda.2 and BlackBerry.Panda.3.
In addition, a new Trojan downloader for Android—dubbed Android.DownLoader.5.origin —was discovered in August Trojans spread in large numbers on devices belonging to Japanese Android users—in August, these users came under several massive spam attacks. Finally, it should be noted that in August a large number of commercial spyware applications were revealed and added to the Dr.Web virus database. These programs include FinSpy for Android, Symbian OS, and iOS.
Threat of the month: Trojan.Mayachok.17516
Another modification of a widespread and rather dangerous malicious program Trojan.Mayachok is probably the most unusual piece of malware found in August. It was dubbed Trojan.Mayachok.17516 This malicious program is implemented as a dynamic library delivered into a system by a dropper, which—as an executable—decrypts and copies the library to the disk. If UAC (User Accounts Control) is enabled in the system, the dropper copies itself to a temporary folder as flash_player_update_1_12.exe and launches itself.
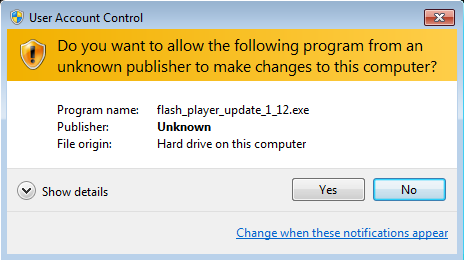
If launched successfully, the executable file decrypts the library file containing the Trojan code and copies it into one of the system folders with a random name. There are 32- and 64-bit versions of this library. Then the dropper adds the library entry into the registry and restarts the computer.
The main functions of Trojan.Mayachok.17516 include downloading and running executable files and using web-browser features to perform malicious tasks. By exploiting the explorer.exe process, Trojan.Mayachok.17516 covertly launches browsers to increase hit counts for certain sites. An infected svchost.exe process is responsible for communicating with a remote command server, as well as for downloading configuration files and updates. Attackers receive information about the infected computer, including the operating system version, which browsers are installed, etc.
Other threats in August
In the second half of the month, the BackDoor.IRC.Codex.1 program, which communicates with intruders via the IRC protocol, was found in the wild. This malware can download from a remote server and run on an infected computer a variety of applications, participate in DDoS attacks, forward data entered by users in web forms to attackers, and steal passwords stored by popular FTP clients.
An investigation into an incident involving the spread of dangerous Trojans along with fake software installers revealed that criminals who design fake installers also developed a special malicious program dubbed Trojan.Zipro to facilitate the installation of other malignant applications in compromised systems.
On August 22, Doctor Web reported the discovery of the cross-platform Trojan BackDoor.Wirenet.1, designed to steal passwords under both Linux and Mac OS X. The developers sell this software as spyware, and versions of BackDoor.Wirenet.1 for Solaris and Microsoft Windows also exist.
Chinese virus writers managed to surprise security experts by making the complex and multi-component Trojan.Xytets program which can be considered both a bootkit and a rootkit. The Trojan horse incorporates eight modules that perform specific functions and anti-debugging routines, and can infect MBRs and hide its presence in the system. It should be noted that Trojan.Xytets has a particularly diverse payload which also distinguishes it among malware.
Malicious files detected in mail traffic in August
| 01.08.2012 00:00 - 31.08.2012 15:00 | ||
| 1 | BackDoor.Andromeda.22 | 1.97% |
| 2 | Trojan.Oficla.zip | 1.70% |
| 3 | Exploit.BlackHole.12 | 1.45% |
| 4 | JS.Redirector.130 | 1.00% |
| 5 | Trojan.Necurs.21 | 0.90% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.90% |
| 7 | Win32.HLLM.MyDoom.33808 | 0.69% |
| 8 | Win32.HLLM.Netsky.35328 | 0.45% |
| 9 | SCRIPT.Virus | 0.42% |
| 10 | Win32.HLLM.Beagle | 0.42% |
| 11 | Trojan.Fakealert.32747 | 0.31% |
| 12 | Trojan.PWS.Panda.655 | 0.31% |
| 13 | Exploit.IframeBO | 0.24% |
| 14 | Win32.HLLM.Netsky.18516 | 0.24% |
| 15 | Trojan.PWS.Panda.786 | 0.24% |
| 16 | W97M.Keylog.1 | 0.24% |
| 17 | Trojan.DownLoader1.64229 | 0.24% |
| 18 | Trojan.Winlock.3020 | 0.24% |
| 19 | BackDoor.Bebloh.17 | 0.24% |
| 20 | Trojan.PWS.Panda.547 | 0.21% |
Malicious files detected on user computers in August
| 01.08.2012 00:00 - 31.08.2012 15:00 | ||
| 1 | SCRIPT.Virus | 0.50% |
| 2 | Trojan.Fraudster.329 | 0.48% |
| 3 | Trojan.Fraudster.256 | 0.44% |
| 4 | Adware.Downware.179 | 0.42% |
| 5 | Tool.Unwanted.JS.SMSFraud.10 | 0.38% |
| 6 | Trojan.Mayachok.1 | 0.36% |
| 7 | Trojan.SMSSend.2925 | 0.36% |
| 8 | Trojan.Fraudster.296 | 0.34% |
| 9 | Win32.HLLM.Graz | 0.33% |
| 10 | Trojan.Fraudster.320 | 0.29% |
| 11 | Win32.HLLW.Autoruner.59834 | 0.29% |
| 12 | Win32.HLLW.Shadow | 0.28% |
| 13 | Adware.Downware.316 | 0.26% |
| 14 | Adware.Downware.426 | 0.25% |
| 15 | Tool.Unwanted.JS.SMSFraud.15 | 0.24% |
| 16 | Trojan.Fraudster.261 | 0.24% |
| 17 | Tool.Skymonk.1 | 0.23% |
| 18 | Exploit.CVE2012-1723.13 | 0.22% |
| 19 | Tool.InstallToolbar.88 | 0.22% |
| 20 | Adware.Downware.353 | 0.22% |