Win32.Rmnet.12 botnet exceeds three million hosts
Real-time threat news | All the news | Virus alerts
June 29, 2012
In mid-April 2012 Doctor Web reported that the botnet created by hackers using Win32.Rmnet.12 reached one million compromised computers. Since then, the number of infections has grown steadily: by the end of May, the botnet reached 2.5 million machines, as was reported by Doctor Web in its May virus activity review, and at the end of June, the number of bots broke the 3.2 million mark. The botnet's growth rate is rather high, with 5-8 thousand new joiners connecting to a control server monitored by Doctor Web on a daily basis, and on some days the number reaches 15,000. The graph below illustrates how the number of bots grew in the current month.

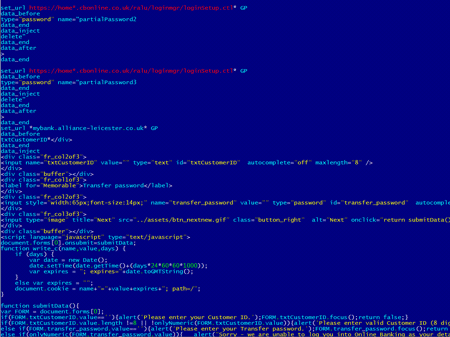
Please note that the virus can replicate itself by infecting executable files and spreads with the help of VBscript code embedded in web pages. The virus consists of several modules and can embed content into loaded web pages (i.e., make web injections), redirect a browser to a site specified by criminals, and send information entered into web forms by a user to remote hosts. The screenshots below provide an example of scripts injected into page code by the malware.
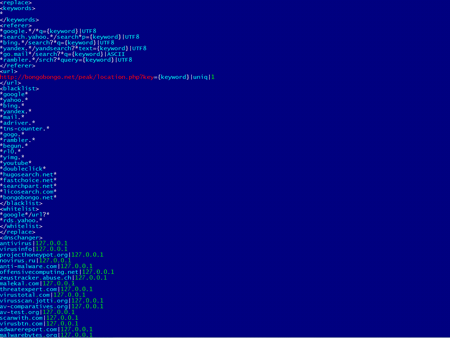
The following image shows the list of web addresses, to which access is blocked by Win32.Rmnet.12, as well as a list of search queries used to redirect the browser to a site belonging to the attackers.
Win32.Rmnet also steals passwords stored by popular FTP clients, such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, and Bullet Proof FTP. In addition, the malicious program runs an FTP server on the infected machine. The virus uses backconnect to access internal services. This enables the malware, for example, to connect to the FTP server running on the infected machine, even if the compromised computer does not have a dedicated external IP address. Another Win32.Rmnet.12 component is able to execute commands received from a remote command center and transfer information gathered in the infected system to criminals.
The Trojan's geographical reach has not changed much in the last few months: the largest number of infected computers resides in Indonesia (22.6%). Bangladesh comes second (15.8%), followed by Vietnam (13.2%), India (7 9%), Pakistan (4.9%), and Egypt (3.5%). Russia accounts for 2.8% of the total botnet, and the respective quantity is much greater than a month ago. Doctor Web continues to closely monitor the botnet’s operation.