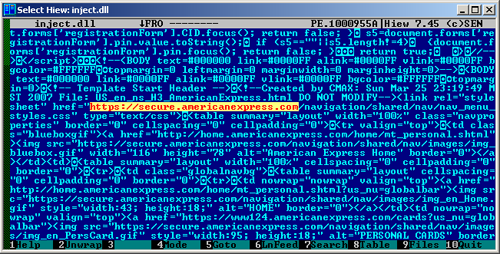
Trojan.PWS.Banker.64540 replaces web content
Real-time threat news | All the news | Virus alerts
June 6, 2012
Trojan.PWS.Banker.64540 consists of two components: an executable file and a dynamic library file, and yet it is rather small—about 80 Kbytes. This malware spreads via the well-known Andromeda botnet. When launched on an infected machine, Trojan.PWS.Banker.64540 copies itself into a folder as msvcrt.exe and adds a link to the file into the registry branch responsible for launching applications automatically. The Trojan checks whether the file is installed in the system. After this, the malware launches itself and injects a self-removal code into the svchost.exe process. It stores all the information about its own actions in a log file.
When launched, the Trojan searches, according to a predefined template, for data in the files stored on all the drives of the infected computer except for the A disk. It encrypts all the information it manages to find and sends the data to one of the criminals' servers whose addresses are embedded in the malware.
The main objective of Trojan.PWS.Banker.64540 is to inject its component into Internet Explorer. It includes web injections that allow the web content of certain sites such as visa.com, mastercard.com, americanexpress.com, and discovercard.com, to be replaced. The Trojan's signature has been added to Dr.Web virus databases.