February virus activity review from Doctor Web
Virus reviews | All the news | Virus alerts
Doctor Web presents the virus activity review for February 2009. As a traditional January “vacation” came to an end, cyber criminals got back to their work. The last month saw a significantly increased number of malicious programs used to turn computers into zombies.
Botnets
A large number of malicious programs are spread in order to increase the number of zombie computers in botnets. Tdss and Virut are common examples of rapidly growing zombie networks.
Let’s take a closer look at one of the methods of infection used by owners of the Tdss botnet. They disguise malicious code as a video codec typically copied to a hard drive from a removable media. The malicious program is detected by Dr.Web as Win32.HLLW.Autoruner.4612. If launched the virus will infect available hard and removable drives and create its additional component also detected by Dr.Web as Win32.HLLW.Autoruner.4612
In order to launch the second malicious file the virus makes a modified copy of a system library that entered the Dr.Web virus database as Trojan.Starter.896. One of system services is restarted in order to make the system use the modified library.
Win32.HLLW.Autoruner.4612 is a backdoor – a remote administration program installed in a system without an authorization of the user and controlled by a cyber-criminal. Luckily actions performed by this particular backdoor are limited to downloading of executable files from a server. Win32.HLLW.Autoruner.4612 initiates a file transfer and receives encrypted files and instructions required to download and launch other malicious programs.
One of such programs is Trojan.DnsChange.1008 that changes DNS settings on the computer that may allow a virus maker to intercept Internet traffic of a user and block access to the Internet.
Owners of Virut use the Win32.Virut polymorphic virus that infects executable files of Windows and adds a special tag at the end of HTML documents. Opening such a document initiates downloading of malicious programs from servers of the botnet. This is the main reason why the virus is often detected in mail traffic as users often attach HTML documents modified by the virus to their messages. Consequently the virus takes top positions in statistic reports on malware in e-mail traffic even if there are no notable mass mailings spreading malicious code.
The latest version of Win32.Virut.56 uses several infection techniques depending on the structure of a file it infects. However, the encrypted code of the virus body is always written at the end of the file. The code for decryption is placed in unused segments of the infected file. The code is polymorphic meaning it differs from file to file. Besides, the polymorphic code may include the code of an infected file if it is required to infect it.
Win32.Virut.56 also features its own IRC-client used to receive commands to download and launch other malicious programs on an infected machine.
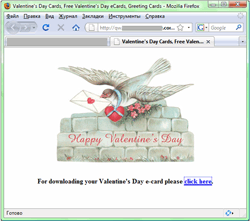
In first two weeks of February many users received messages that contained links to bogus web-sites supposedly offering St. Valentine Day greetings. Instead of a greeting card a user downloaded one of the numerous modifications of Trojan.Spambot – a malicious program that uses an infected machine to send out spam.
Keen to make quick money virus makers often fail to test their works properly and lose profit even though damage is still done to data of a victim. Trojan.Encoder.36 wrote its code into document files on a hard drive of a victim, so the user couldn’t open such files. However, the Trojan didn’t display the account information so that the victim could pay for decryption. Users whose file s were corrupted by the malicioius program can scan such files using Dr.Web software to restore them to their original state.
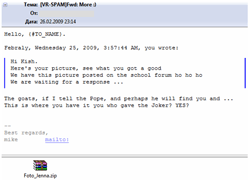
Even though the number of spam messages with attached malicious code moved down, one could still find e-mails with attached malware. At the end of February some users received messages notifying them that a photo of the user was published on a web-site in the Internet. The supposed photo was attached to the message as a zip-archive. The archive contained the file with the name Foto_Jenna.Jpg[series of underscores].exe detected by Dr.Web as Trojan.DownLoad.9125.
Spam
It seems that the worldwide economic slowdown boosted business of spammers .Many companies receive offers to promote their products and services in the Interne. Little wonder that the promotion is limited to spam messages containing information about the company. In last two weeks of February such messages increased amount of spam traffic at such a rate that if the growth continues in the next month, it will exceed amount of spam traffic registered at the beginning of December 2008 prior to the closure of the hosting companies responsible for a large share of spam traffic..
Number of phishing messages and other scams in English also went down while the number of scams in native languages of recipients increased. In February phishing attacks offering messages in native languages of users were received by customers of the Praveks bank (Ukraine) and customers of the Raiffeisen Bank in Romania.
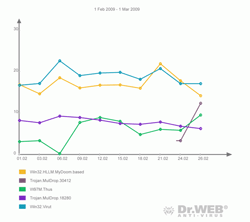
Malicious programs detected in mail traffic in February
| 01.02.2009 00:00 - 01.03.2009 00:00 | ||
| 1 | Win32.Virut | 13836 (18.60%) |
| 2 | Win32.HLLM.MyDoom.based | 12512 (16.82%) |
| 3 | Trojan.MulDrop.18280 | 5777 (7.77%) |
| 4 | Trojan.MulDrop.13408 | 4829 (6.49%) |
| 5 | W97M.Thus | 4276 (5.75%) |
| 6 | Trojan.MulDrop.16727 | 3896 (5.24%) |
| 7 | Win32.HLLM.Alaxala | 3608 (4.85%) |
| 8 | Win32.HLLM.Netsky | 2222 (2.99%) |
| 9 | Win32.HLLM.Beagle | 2130 (2.86%) |
| 10 | Trojan.MulDrop.19648 | 1254 (1.69%) |
| 11 | Win32.HLLM.Netsky.35328 | 1142 (1.54%) |
| 12 | Win32.HLLM.Mailbot | 1101 (1.48%) |
| 13 | Trojan.MulDrop.30412 | 1046 (1.41%) |
| 14 | Win32.HLLM.MyDoom.33 | 1020 (1.37%) |
| 15 | JS.Nimda | 901 (1.21%) |
| 16 | BackDoor.Poison.78 | 821 (1.10%) |
| 17 | Trojan.MulDrop.17431 | 811 (1.09%) |
| 18 | Win32.Virut.5 | 804 (1.08%) |
| 19 | Win32.HLLW.Shadow.3 | 783 (1.05%) |
| 20 | Win32.HLLM.Netsky.based | 651 (0.88%) |
| Total scanned: | 315,981,994 |
| Infected: | 74,379 (0.02%) |
Malicious programs detected on user machines in February
| 01.02.2009 00:00 - 01.03.2009 00:00 | ||
| 1 | Win32.HLLW.Gavir.ini | 1556095 (15.68%) |
| 2 | Win32.HLLW.Shadow.based | 560465 (5.65%) |
| 3 | VBS.Redlof | 407678 (4.11%) |
| 4 | Win32.Alman | 386225 (3.89%) |
| 5 | Exploit.PDF.56 | 353381 (3.56%) |
| 6 | Win32.HLLW.Autoruner.5555 | 341004 (3.44%) |
| 7 | Trojan.MulDrop.30306 | 281284 (2.83%) |
| 8 | Win32.Virut.5 | 268992 (2.71%) |
| 9 | Win32.HLLW.Recycler.3 | 251237 (2.53%) |
| 10 | Trojan.Packed.2352 | 247824 (2.50%) |
| 11 | Win32.Sector.17 | 214765 (2.16%) |
| 12 | Trojan.Starter.881 | 207379 (2.09%) |
| 13 | Win32.HLLM.Lovgate.2 | 142409 (1.43%) |
| 14 | Win32.HLLW.Autoruner.6126 | 138424 (1.39%) |
| 15 | Win32.HLLP.Jeefo.36352 | 125123 (1.26%) |
| 16 | Trojan.PWS.Wsgame.4983 | 114527 (1.15%) |
| 17 | Trojan.DownLoader.42350 | 113574 (1.14%) |
| 18 | Trojan.Siggen.2002 | 112159 (1.13%) |
| 19 | Win32.HLLP.Neshta | 111203 (1.12%) |
| 20 | DDoS.Kardraw | 109968 (1.11%) |
| Total scanned: | 68,834,531,277 |
| Infected: | 9,924,181 (0.01%) |