May 2012 virus activity review: Trojan.Mayachok in the lead, Trojan.Matsnu encoder, and new threats to Android
Virus reviews | All the news | Virus alerts
June 4, 2012
May 2012 was a fairly quiet month in terms of information security with no serious outbreaks registered. Nevertheless, the number of Trojan encoder victims among European users is increasing, and new threats to Android are emerging.
Viruses
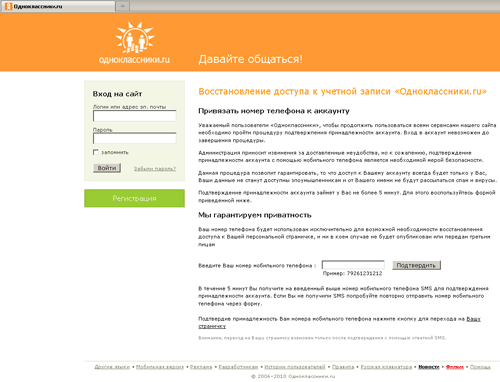
According to statistics gathered by Dr.Web CureIt!, Trojan.Mayachok.1, which mimics the pages of the most popular sites, topped the list of major threats. It made up 3.73% of the total number of malware detections. Such high popularity is quite understandable. The program spreads via false file-sharing services under the guise of drivers and useful applications as well as in spam mailings. Trojan.Mayachok.1 brings a good profit to its makers by requiring users to pay for access to a particular site. To do so, the fraud victim has to enter into a corresponding field their mobile phone number and a code received in a reply SMS. Thus the user is subscribed to a pseudo service, and the service fee is debited from their account on a monthly basis. This is an incomplete list of online resources whose pages can be replaced by this Trojan horse: youtube.com, vkontakte.ru, vk.com, odnoklassniki.ru, and my.mail.ru.
Keeping pace with Trojan.Mayachok.1 was Trojan.Carberp (1.3% of detections), which targets online banking users. Various malicious downloaders—Trojan.SMSSend malware (1.5%), Trojan.Hosts (about 0.5%), and numerous IRC bots—were also found in relatively large numbers.
If we compare these statistics with those for the previous month, we can see that the number of infections by Trojan.Mayachok.1 increased by 1.36%. In May, detections of this malware increased by 10,500. Yet the number of Trojan.Carberp detections decreased almost by a quarter. Incidents involving systems getting infected by Trojan.Hosts malware, which modify the Windows/System32/Drivers/etc/hosts file containing DNS server addresses, increased insignificantly. Trojan.Hosts.5858 is one of the most popular malware variations; its mass distribution outside was mentioned in one of our recent news posts.
The Trojan is spread via the BackDoor.Andromeda botnet. When trying to visit a popular online resource, such as Facebook, Google, Yahoo, etc., a browser in the infected system is automatically redirected to a webpage specially created by attackers to display a message in German stating that Internet access has been blocked. To resolve the issue, the user is prompted to provide virus writers with their banking card details.
The number of other threats detected in the past month remained the same.
Spam
The malicious script Trojan.SMSSend.2856, which redirects browsers to bogus sites, became the leader among malware found in mail traffic. Other malicious programs found in mailings include Trojan.Mayachok.1 and Trojan.Carberp. The Win32.HLLW.Shadow worm (also known as Kido) is often found in e-mail attachments—this program can download a variety of applications from remote servers, and install and run them on the compromised machine. Various Trojan downloaders and the rootkit Trojan.NtRootKit.6725 are also often attached to messages. It should be noted that, compared with April 2012, the volume of malicious attachments in e-mail messages decreased slightly, while the malware enclosed with e-mails remained the same.
Botnets
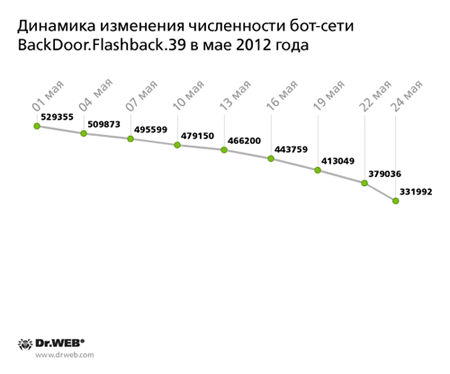
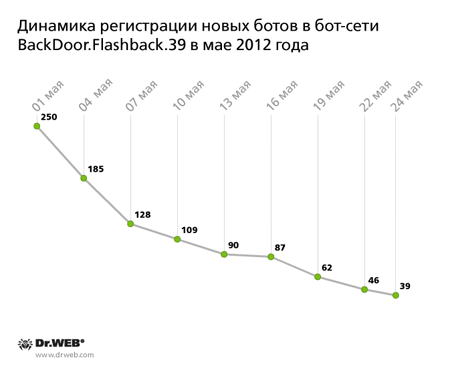
Discovered in early April by Doctor Web's virus analysts, the BackDoor.Flashback.39 botnet encompassed more than 800,000 Apple computers running Mac OS X. It still exists, although the total number of infected machines has decreased markedly and is still declining. At the beginning of May, the number of bots in the network declined to 529,355. As of May 24, the network consisted of 331,992 infected hosts, while the average daily number of new joiners was 110. This figure was also going down steadily through the month. The below graph shows how the total number of BackDoor.Flashback.39 bots changed through May 2012.
And here is how the BackDoor.Flashback.39 botnet new joiner registration graph looks:
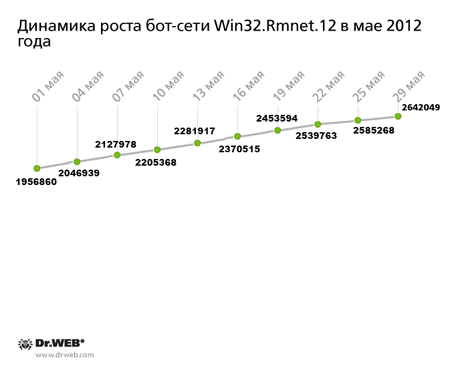
In April, Doctor Web reported the discovery of a large botnet created by hackers using the Win32.Rmnet.12 file infector: even then it encompassed more than a million infected computers located mostly in the Middle East and Asia. Win32.Rmnet.12 is a complex multi-component file infector, consisting of several modules and capable of self-replication. It can perform backdoor tasks and execute commands from a remote control center as well as steal passwords stored by the most popular FTP clients, such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, Bullet Proof FTP, and others.
As of May 29, 2012, the Win32.Rmnet.12 botnet was comprised of 2,641,855 infected machines—that is, it managed to double in size over the last month. The virus's spreading geography didn't change much: the countries most exposed to infection still include Indonesia, Bangladesh, Vietnam, India, and Egypt; a large number of infected PCs can be found in Russia. The Win32.Rmnet.12 botnet’s growth in May 2012 is presented in the graph below.
The graph clearly shows that the average daily number of newly infected machines joining the botnet is about 25,000, and the botnet continues to grow very rapidly.
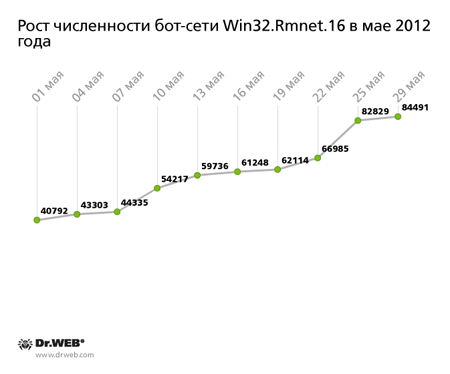
A similar situation exists with respect to another botnet, which is closely monitored by Doctor Web's virus analysts—the Win32.Rmnet.16 botnet. In early May, we reported that the number of infected hosts (as of May 11. 2012) reached 55,310, and the largest share of them was located in the UK. In the following 18 days, the number of infected machines reached 84,491. The graph, showing how the number of new bots in the network has been growing, is found below.
It clearly indicates that new infected machines appear on the Win32.Rmnet.16 network at a varying rate, but their total number, however, is gradually increasing.
The threat of the month: Trojan.Matsnu.1
A large number of systems around the world were compromised by this Trojan horse: numerous requests for technical support came to Doctor Web from many European countries, especially from Germany.
Written in Assembly, the Trojan is distributed as a zipped executable file attached to e-mail spam messages with the subject mentioning the name of the recipient. If the user opens the archive and runs the application, the Trojan encrypts files found on disks and shows a message saying that the system is blocked or has been infected with an encoder Trojan. Criminals ask users not to turn off the computer to avoid data loss. Virus writers prompt victims to use one of the most common European payment systems to pay to get their files restored.
While displaying the message, the Trojan also stands by for commands from a remote control center. Trojan.Matsnu.1 can receive the following directives:
- System kill (delete all files on hard drives)
- Download a specified program from a bogus site and run it
- Download other images to show in a dialog box
- Save a downloaded file on the disk and run it as a background process
- Decrypt files (a decryption key is received from the criminals' site along with the directive)
- Encrypt the files again using a newly generated key
- Update the control server list
- Update the Trojan main module
Given the wide range of options available with the Trojan payload, it is virtually impossible to underestimate its harmful potential. A large number of users in Europe and Latin America have already been affected by its malignant activities.
Threats to Android
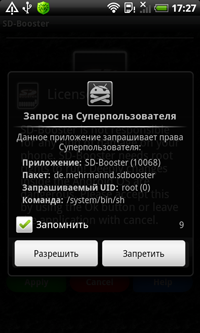
The last month of spring was also marked by the emergence of new threats to Google Android. In early May, we warned users about Trojan horses that pose a threat to rooted phones. These malicious programs utilize the nesting doll principle which is when a modified application incorporates an encrypted apk file. Trojans install a downloader that can retrieve and run other applications on the infected device.
In addition, a malignant application for Android dubbed Android.Proxy.1.origin was discovered in May. It spreads under the guise of a system upgrade from compromised sites. The Trojan runs a simple proxy server on the infected device, thus providing hackers with unauthorized access to private networks to which the device is connected. Trojan downloading starts automatically when one visits a compromised site with an embedded hidden IFRAME, however, the user must install the application for the mobile device to get infected.
Windows lockers and encoders
A significant portion of requests from users received by Doctor Web's technical support service in May concerned blocker programs — 21.2% of the total. This number decreased slightly compared with April; the number of requests for the decryption of files compromised by Trojan.Encoder programs went down, too, and reached 0.71%. Requests concerning other virus threats in the past month amounted to 5.3% of the total.
In brief
Among other information security threats identified in May 2012, we must note the following:
- Cyber-fraudsters have turned their attention to Facebook.
- Win32.HLLW.Autoruner.64548, which spreads by copying itself onto the disk and placing the autorun.inf file into a root directory, searches and infects RAR archives.
- Doctor Web's virus analysts discovered an IRC bot—BackDoor.IRC.Aryan.1—that can retrieve files from a remote malicious server and launch DDoS attacks upon command by an IRC server
- Another IRC bot spreading spam in instant messaging networks uses a non-trivial routine to monitor running processes according to the information it finds in the Windows registry.
Top 20 malware detected in May in mail traffic
| 01.05.2012 00:00 - 31.05.2012 16:00 | ||
| 1 | BackDoor.Andromeda.22 | 10.81% |
| 2 | Trojan.Siggen.65111 | 3.60% |
| 3 | BackDoor.Bulknet.546 | 2.70% |
| 4 | Trojan.DownLoader6.380 | 2.70% |
| 5 | Trojan.Packed.22544 | 2.70% |
| 6 | Win32.HLLM.MyDoom.54464 | 2.70% |
| 7 | Win32.HLLM.MyDoom.33808 | 1.80% |
| 8 | Trojan.DownLoader6.8588 | 1.80% |
| 9 | Trojan.PWS.Banker1.2269 | 1.80% |
| 10 | Trojan.Winlock.6068 | 1.80% |
| 11 | Win32.HLLM.Beagle | 1.80% |
| 12 | Trojan.Inject.12703 | 0.90% |
| 13 | Win32.HLLM.Netsky.18401 | 0.90% |
| 14 | Adware.Downware.235 | 0.90% |
| 15 | Exploit.PDF.2862 | 0.90% |
| 16 | JS.IFrame.117 | 0.90% |
| 17 | Trojan.Siggen4.1047 | 0.90% |
| 18 | X97M.Escape.2 | 0.90% |
| 19 | Trojan.DownLoader6.9595 | 0.90% |
| 20 | Trojan.SMSSend.2666 | 0.90% |
Top 20 malware detected in May on user PCs
| 01.05.2012 00:00 - 31.05.2012 16:00 | ||
| 1 | Trojan.Fraudster.292 | 0.73% |
| 2 | Trojan.Mayachok.1 | 0.68% |
| 3 | Trojan.Fraudster.256 | 0.67% |
| 4 | Tool.Unwanted.JS.SMSFraud.15 | 0.62% |
| 5 | Trojan.Carberp.30 | 0.61% |
| 6 | Trojan.SMSSend.2856 | 0.56% |
| 7 | Win32.HLLW.Shadow | 0.55% |
| 8 | Trojan.SMSSend.2778 | 0.52% |
| 9 | Trojan.Fraudster.296 | 0.51% |
| 10 | SCRIPT.Virus | 0.51% |
| 11 | Trojan.SMSSend.2872 | 0.50% |
| 12 | Win32.HLLW.Shadow.based | 0.50% |
| 13 | Tool.Unwanted.JS.SMSFraud.10 | 0.49% |
| 14 | Trojan.Fraudster.252 | 0.47% |
| 15 | Trojan.NtRootKit.6725 | 0.47% |
| 16 | Trojan.SMSSend.2726 | 0.44% |
| 17 | Trojan.Fraudster.261 | 0.42% |
| 18 | Tool.InstallToolbar.74 | 0.41% |
| 19 | Trojan.MulDrop3.49657 | 0.40% |
| 20 | Adware.Downware.179 | 0.39% |