Doctor Web analyzes objects downloaded by BackDoor.Flashback onto infected Macs
Real-time threat news | All the news | Virus alerts
April 27, 2012
BackDoor.Flashback.39 exploits a Java vulnerability to save an executable and configuration file, responsible for its automatic launching by launchd, onto a hard drive of the compromised Mac. Then BackDoor.Flashback.39 connects to a control server, downloads an executable onto the infected machine and installs it in the system. At this moment the Trojan brings up a dialogue window prompting the user to enter an administrator password. If the user does enter the password, the malicious program runs with elevated privileges, but even if they don't, the Trojan will be saved in the user's home directory and launched with the current user permissions. It will be enough to perform its malicious tasks.
The downloaded malignant application interacts with two types of control servers. Servers belonging to the first category intercept web search traffic and redirect the user to malicious sites controlled by criminals. The second group issues commands to bots to perform backdoor tasks in the compromised system. Doctor Web analysts managed to take over control server domain names known to BackDoor.Flashback payload malware and analysed requests sent by bots to servers.
Control server names of the first group are generated using the list found in the Trojan’s configuration data; in addition, another domain name list is created where resulting names are determined by the current date. The second level domain name is the same, while a top-level domain name can be org,. com,. co.uk,. cn,. in. The Trojan horse sends consecutive requests to control servers according to its generated list. An /owncheck/ or /scheck/ GET request sent to a server contains the infected Mac's UUID in the useragent field. If the reply contains a SHA1 hash value of the domain name, this domain will become trusted and from this moment on will be considered to be a command server name. First domains in this category have been successfully taken over by Doctor Web since April 12, 2012.
Once the malicious program has determined a domain of the first category, it begins to search for a second type domain. The bot uses the list found in its configuration data to send the /auupdate/ GET-request to a number of control servers. The useragent field in these requests contains detailed information on the infected system. The request example can be found below:
20|i386|9.8.0|4DE360BE-E79E-5AD6-91CF-D943761B3785|6bbbbfb49b1659ebaaadffa20215bfc787577bd8|001|007|0
Where:
- bot version
- hw.machine)
- kern.osrelease
- Hardware UUID
- payload file SHA1 value
- third-party browser availability bitmask
- constant
- value indicating bot privileges 0 — ordinary user, 1 — privileged user
If the control server does not return a correct reply, the Trojan uses the current date to generate a string that serves as a hash tag in a search using http://mobile.twitter.com/searches?q=<string>. For example, some Trojan versions generate a string of the "rgdgkpshxeoa" format for the date 04.13.2012 (other bot versions can generate a different string). If the Trojan manages to find aTwitter message containing bumpbegin and endbump tags enclosing a control server address, it will be used as a domain name. Doctor Web began to take over domains of this category on April 13, but on the following day, Saturday, April 14, the Twitter account registered by Doctor Web analysts for this purpose was blocked.
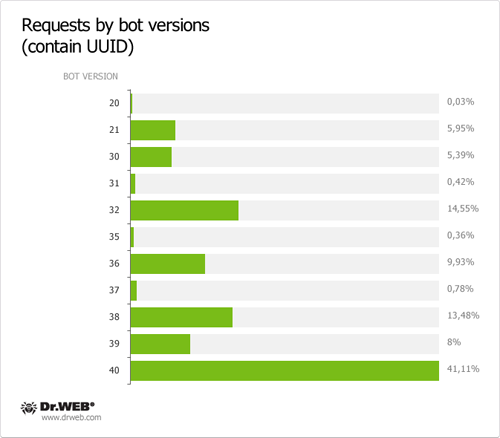
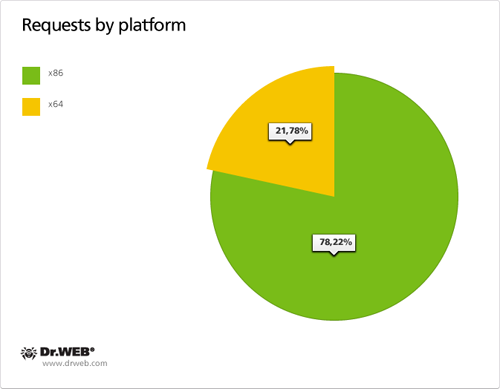
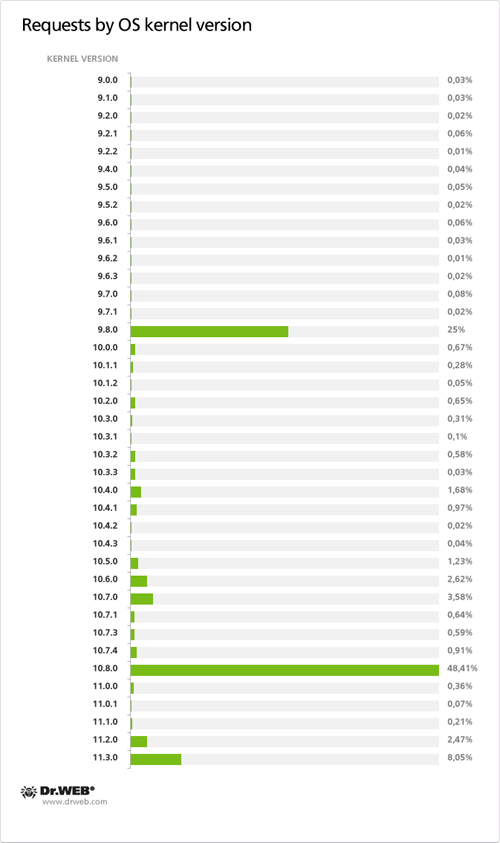
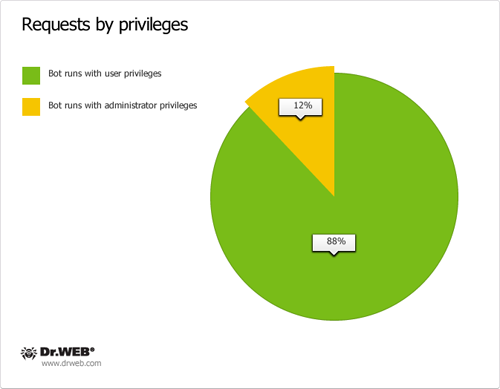
As of April 13, 2012, 30 549 requests containing a UUID were sent to control servers of the first domain name category in 24 hours and 28,284 requests containing a UUID were transmitted to control servers of the second domain name category in the same period of time. Total 95 563 requests containing a UUID were sent to servers meant to control BackDoor.Flashback payload from April 12 till 26, 2012. Other statistical data obtained during the 24 hour analysis of requests sent by BackDoor.Flashback payload to control servers on April 13, 2012, is presented on the graph below.