New Windows locker changes system access passwords
Real-time threat news | All the news | Virus alerts
March 13, 2011
Traditionally ransomware use a special application to replaces the Windows shell or userinit.exe, block access to the system and display ransom text. Simultaneously, malware usually monitor and block launching of various system utilities such as Task Manager, Command Prompt, Registry Editor, etc. Makers of Trojan.Winlock.5729 chose a completely different and simpler approach.
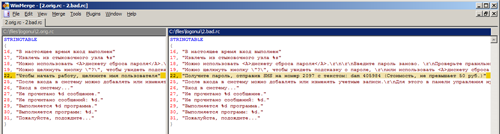
The Trojan horse code is spread with the Artmoney program used to adjust various parameters in computer games. In addition to the Artmoney, the installer also incorporates three files: the modified logonui.exe file named iogonui.exe (responsible for displaying Windows XP logon screen) and two self-extracting archives containing bat-files. Starting an infected installer executes the password_on.bat file. This file contains a set of commands that search the hard drive for the c:\users folder which is found under Windows Vista and Windows 7. If discovered, the harmful components are removed, if the folder is not found, the Trojan horse believes that it is running under Windows XP. In this case Trojan.Winlock.5729 modifies the system registry to replace the logonui.exe file with iogonui.exe, and changes the password for the current user Windows account and local users named admin, administrator, админ and администратор. If the current user account has restricted permissions, the Trojan horse process ends. Another bat-file— password_off.bat—sets the original UIHost value in the registry.
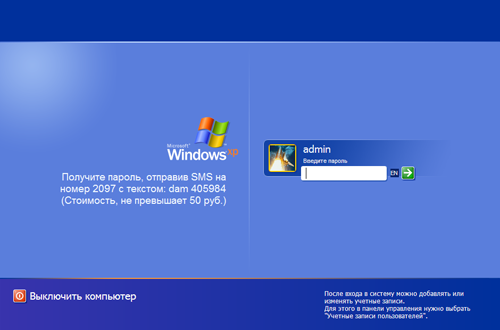
The iogonui.exe file is a genuine logonui.exe file that comes with the Windows XP distribution but a resource editor was used to change the standard Windows welcome screen for a demand to send a paid SMS.
Once the user logs off or reboots the system, they will not be able to log in as the passwords for all user accounts will have been changed.
The Trojan horse's signature is added to the Dr.Web virus databases. If your system has been blocked by the Trojan horse, you can manually change the value in the registry branch а HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon for logonui.exe.