February 2012: Mac OS X exploit and Trojan horse monitoring users via webcam
Virus reviews | Real-time threat news | All the news | Virus alerts
March 1, 2012
Strange but true: in spite of the approaching March 4, 2012, Presidential Elections, spammers did not use the elections as a subject for mailings. A similar trend was observed last December before the Russian State Duma elections. It looks like political operatives gave up on spam as a means of influencing information and switched to social networks. Nowadays mass mailings mainly advertise various seminars, family holiday packages, illegal film and music collections — everything except politics and election-related events.
As far as viruses are concerned, February didn’t bring any unpleasant surprises. Win32.Expiro.23 tops the list of threats Dr.Web CureIt! detected on user computers in the second month of the year. Once in a system, the malicious program elevates its privileges and infects executable files. Its main purpose is to steal passwords stored by INETCOMM Server, Microsoft Outlook, Internet Explorer, Mozilla Firefox, and FileZilla. Apart from Win32.Expiro.23, Trojan.Mayachok.1 was often detected on user machines. This malicious program blocks user access to the Internet or to the most popular sites and demands that the victim enter their mobile phone number into a corresponding form and reply to an incoming short message. By complying, the victim comes to be subscribed to various paid services, and fee amounts will be debited from their account on a regular basis.
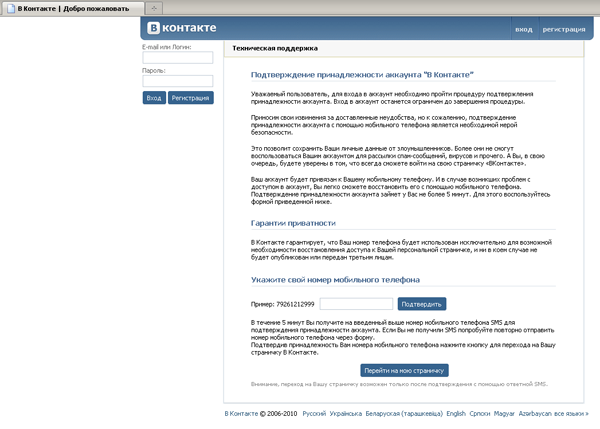
Trojan.Hosts programs remained in the most frequently detected top ten. These Trojan horses modify the \drivers\etc\hosts file, so that when accessing an Internet resource, the victim is redirected to a specially crafted malicious phishing site. And, of course, Trojan.Carberp banking malware were often found on infected machines – over 30,000 detections of their different versions were registered in the past month.
Another Facebook threat
Trojan.OneX is designed to send spam over the world's largest social-networking website Facebook as well as through instant messaging programs.
Trojan.OneX runs only under 32-bit Windows versions. Once launched on an infected machine, Trojan.OneX.1 checks whether its copy is already present in the system, and then decrypts the remote server address which it then uses to download a special text file. This file contains several lines in English such as «hahaha! http://goo.gl[…].jpeg», which will later substitute messages the user posts on Facebook.
Soon after the first modification of the Trojan horse was discovered, Doctor Web's virus analysts got hold of another malware sample dubbed Trojan.OneX.2. Unlike the first version, the second modification uses popular messaging software processes such as skype, pidgin, aim, msnmsgr icq.exe, yahoom, ymsg_tray.exe, googletalk, and xfire.exe, instead of browsers. The mouse and keyboard connected to the infected system are blocked when a message is being sent. Unlike Trojan.OneX.1, Trojan.OneX.2 can parse configuration files in Unicode.
Messages sent by the Trojan horses often contain links to malicious phishing sites. One such site mimics the RapidShare design. This malicious program not only gives attackers access to the infected computer and steals confidential data but also allows intruders to run various commands on the infected computer, and download and install other applications. It is noteworthy that Doctor Web registered cases where BackDoor.IRC.Bot was used to spread Trojan.OneX, which, in turn, contributes to the further spread of BackDoor.IRC.Bot.
Winlocks again
February saw the natural extension of the January trend whereby the number of user requests related to Windows blockers declined steadily—February witnessed an additional 28 percent drop. Apparently, fewer people are complying with intruder demands and are finding other ways to unlock their systems, while criminals are seeking other ways to make a living and new targets among which they can distribute their extortion software. As an example, in February, Doctor Web discovered a Winlock program targeting Arabic speakers.
Trojan.Winlock.5416 is a rather primitive extortion program that has neither the unlock code nor routines for checking the system locale and runs on all Windows machines. A message in Arabic informs a user that their computer has been blocked because it has been used to access adult content and view videos of violence against children, which violates Saudi Arabian law. The user is threatened by the Sharia court and told to pay $300 by buying a Ucash prepaid card and entering its code in the blocker window. This code is then sent to the criminals' site (hosted in Latvia). The Trojan horse performs no other destructive actions. It should be noted that as far as Doctor Web’s specialists are aware, this is the first example of a Trojan horse blocker showing messages in Arabic.
Volk Trojan horse spammer
Trojan.Spamer.46 is distributed through torrents with the WinRAR archiver. As soon as the Trojan horse gains a foothold in the operating system, it begins to filter outbound traffic in search of message sending forms and adds a malicious link to the text entered in those forms by users. The link leads to a bogus website offering a palmistry service in exchange for a paid short message.
In addition, an entire family of malicious programs dubbed BackDoor.Volk was discovered in February. One of them—BackDoor.Volk.1—is written in PHP which is used primarily to create scripts and server applications, and is then converted into executable code using the php2exe utility. This malicious program modifies the “hosts” file, listing available DNS names and their respective IP addresses in the compromised system.
Unlike its predecessor, BackDoor.Volk.2 is written in Visual Basic and uses the POST routine instead of GET when accessing remote hosts to send requests. Apart from downloading and running applications and “hosts” file modifications, this malware can carry out DDoS-attacks and is capable of stealing passwords from FTP-clients installed on the infected computer. It should be noted that the module used by BackDoor.Volk.2 to communicate with a remote server was implemented previously in another malicious program—BackDoor.Herpes—whose source code appeared in the public domain a while ago.
BackDoor.Volk.3 and BackDoor.Volk.4 are also written in Visual Basic, and are BackDoor.Volk.2 modifications featuring different routines for communicating with a remote server. Other features of these Trojan horses are similar. BackDoor.Volk can join botnets that are controlled by a specially designed administration panel.

The “hosts” file modification function of the Trojan horse is the most dangerous one since it can be used by criminals to redirect a potential victim to a phishing site. And meanwhile, stolen FTP server access passwords may be used to get unauthorized access to various websites.
Attackers monitor users via webcam
BackDoor.Webcam.9 can execute various commands received from a remote malicious server on an infected machine and can intercept data transmitted by a computer webcam, thus making the owner's personal life the property of virus writers.
When launched, it copies itself into the system temporary folder and adds its entry into the registry to be launched automatically upon system startup. Then the Trojan horse checks whether its copy is already present on the infected machine. After that it sends a series of requests to a remote server. It transmits information about the infected system including its IP address, user account type, number of available webcams, computer name and OS version, and stands by for further instructions.
The Trojan horse is capable of running commands from a remote server. In particular, it can restart itself, change its management server, and take a screenshot. In addition, BackDoor.Webcam.9 can intercept images obtained from a webcam connected to an infected computer , with the potential of putting the user in a compromised position.
Mac OS X exploits
Java vulnerabilities have been repeatedly exploited by hackers to spread malicious software for a variety of platforms, including Windows. In February, virus writers began to exploit a few previously known cross-platform Java vulnerabilities in order to infect Apple-compatible computers.
It works as follows: When an infected site page is loaded, the user-agent is checked to determine whether the page is loaded in a particular browser version under Mac OS X. If it is, a number of java-applets are loaded.
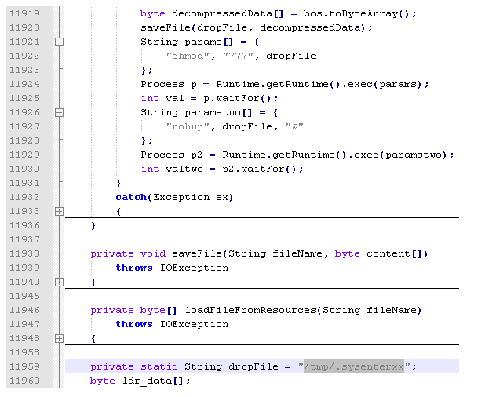
The rhlib.jar module exploits the CVE-2011-3544 vulnerability. It places the .sysenterxx file into the /tmp directory, sets its attributes to serve its needs and launches it.
The launched application checks whether the system files
/Library/LittleSnitch /Developer/Applications/Xcode.app/Contents/MacOS/Xcodeare present, and if they are not, tries to download the BackDoor.Flashback.26 core module. Otherwise, the downloader simply deletes itself. The clclib.jar module exploits the CVE-2008-5353 vulnerability, while the ssign.jar is a Java.Dropper.8 program signed by an invalid signature: criminals expect that the user will add the signature to their trusted list, and thus allow code execution. To date, these vulnerabilities are exploited primarily to spread BackDoor.Flashback which is already familiar to users of Mac OS X.
New DDoS-bot
In February, Doctor Web discovered a malicious program serving as a very "advanced" tool for DDoS-attacks on various Internet resources. Trojan.Tenagour.9 consists of two components: the injector and the dynamic link library, which stores the payload. Once launched, the Trojan horse checks whether its copy is already present in the system, and if not, it saves its file as smss.exe to the %APPDATA% folder, then adds its entry into the registry branch listing applications that are launched automatically.
Then Trojan.Tenagour.9 sends to a remote server: information about the OS version and type, computer name MD5-hash, and the first partition's volume serial number. A reply incorporates an encrypted string containing the URL of a target site and some auxiliary parameters. In addition, a remote command center may send an update command to the Trojan horse.
The Trojan horse can mount eight types of DDoS-attacks on a variety of Internet resources using GET and POST routines via TCP/IP and UDP. It can also add all links found on a targeted site to the list of attached resources.
Top 20 malware detected in February in mail traffic
| 01.02.2012 00:00 - 29.02.2012 16:00 | ||
| 1 | Trojan.DownLoad2.24758 | 1260889 (23.57%) |
| 2 | Trojan.Oficla.zip | 942938 (17.63%) |
| 3 | Trojan.Tenagour.9 | 608458 (11.37%) |
| 4 | JS.Nimda | 469381 (8.77%) |
| 5 | Trojan.Inject.57506 | 316116 (5.91%) |
| 6 | EICAR Test File (NOT a Virus!) | 240989 (4.50%) |
| 7 | Win32.Rmnet.12 | 201603 (3.77%) |
| 8 | Trojan.DownLoad2.32643 | 144994 (2.71%) |
| 9 | Trojan.Tenagour.3 | 124987 (2.34%) |
| 10 | Trojan.PWS.Ibank.456 | 103213 (1.93%) |
| 11 | Trojan.Siggen2.58686 | 91438 (1.71%) |
| 12 | Trojan.Siggen2.62026 | 86986 (1.63%) |
| 13 | Trojan.Packed.19696 | 59825 (1.12%) |
| 14 | Trojan.DownLoad2.34604 | 58289 (1.09%) |
| 15 | Win32.HLLM.Netsky.18516 | 41365 (0.77%) |
| 16 | Trojan.DownLoader.42350 | 40454 (0.76%) |
| 17 | Program.RemoteAdmin.418 | 38053 (0.71%) |
| 18 | Program.RemoteAdmin | 36979 (0.69%) |
| 19 | Trojan.Siggen.65070 | 32930 (0.62%) |
| 20 | Program.RemoteAdmin.451 | 32100 (0.60%) |
| Total scanned: | 12,997,175,680 |
| Infected: | 5,349,414 (0.04%) |
Top 20 malware detected in February on user PCs
| 01.02.2012 00:00 - 29.02.2012 16:00 | ||
| 1 | Win32.Rmnet.12 | 45439835 (54.15%) |
| 2 | Win32.HLLP.Neshta | 17871611 (21.30%) |
| 3 | JS.IFrame.112 | 8509024 (10.14%) |
| 4 | Trojan.Hosts.5006 | 2171701 (2.59%) |
| 5 | Trojan.DownLoader.42350 | 2167227 (2.58%) |
| 6 | JS.IFrame.167 | 584615 (0.70%) |
| 7 | Trojan.PWS.Ibank.456 | 578969 (0.69%) |
| 8 | Trojan.IFrameClick.3 | 396594 (0.47%) |
| 9 | Trojan.MulDrop1.48542 | 322626 (0.38%) |
| 10 | Trojan.Tenagour.3 | 283463 (0.34%) |
| 11 | Trojan.Fraudster.261 | 241669 (0.29%) |
| 12 | Trojan.DownLoader5.18057 | 232619 (0.28%) |
| 13 | JS.IFrame.132 | 222200 (0.26%) |
| 14 | Win32.Virut | 174800 (0.21%) |
| 15 | Trojan.Hosts.5571 | 136354 (0.16%) |
| 16 | Program.RemoteAdmin | 130009 (0.15%) |
| 17 | Trojan.MulDrop.54146 | 127922 (0.15%) |
| 18 | SCRIPT.Virus | 112282 (0.13%) |
| 19 | Trojan.Qhost.3907 | 110427 (0.13%) |
| 20 | BackDoor.Ddoser.131 | 107935 (0.13%) |
| Total scanned: | 148,537,446,432 |
| Infected: | 83,912,629 (0.06%) |