Annual virus activity review from Doctor Web
Virus reviews | All the news | Virus alerts
December 15, 2008
As the year comes to an end, Doctor Web sums up all events related to malware and outlines trends in its development for 2009. The share of malicious code of the total number of files scanned on user machines doubled this year while the amount of spam messages spreading malware dropped significantly due to the widely discussed closure of McColo. At the same time phishing attacks became more frequent. E-mail, removable data storage devices and web-sites have been used to spread malicious code over the Internet.
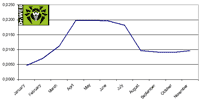
The number of files with malicious code found by anti-viruses on user machines increased steadily at the beginning of 2008 and by April it more than quadrupled. The figure didn’t change till July when the number halved reaching 0.01% of the total number of scanned files in August. It has remained virtually unchanged till the end of the year which means that one scanned file out of ten thousand is infected. The diagram below illustrates dependency between the share of infected files and the total number of scanned files.
The subsequent diagram shows how a number of messages containing malicious code changed through the year with their average share amounting to 0,2-0,25 % of the total number of e-mails (meaning that one message in five hundred had malicious code attached or embedded as a script). Following the closure of the company hosting spammers it has reduced to 0.02% (one message in five thousand contains malicious code).
Most notorious species
BackDoor.MaosBoot, Win32.Ntldrbot (Rustock.C) and numerous modifications of Trojan.Encoder have become the most remarkable malicious programs of this year.
BackDoor.MaosBoot places its code in the boot sector and hides its presence in the system using rootkit technologies. Several modifications of this virus have been found since March.
Win32.Ntldrbot turned out to be the hide master with its numerous techniques to conceal its presence that allowed it to elude virus analysts for several months. The rootkit was so good at hiding that many anti-virus vendors considered it to be no more than a myth.
Win32.Ntldrbot features powerful polymorphic protector implemented as a kernel-level driver and special self-protection and anti-debugging mechanisms. The rootkit also has features of a file virus, it filters all calls to an infected file, injects its code into system processes and starts sending out spam.
Developers of Doctor Web updated anti-virus software in timely manger to ensure its efficient operation against BackDoor.MaosBoot and Win32.Ntldrbot. Eventually Dr.Web turned out to be the first anti-virus capable to counteract the malicious programs without resorting to utilities from a third-party developer.
Trojan.Encoder has also become famous in 2008. The Trojan encrypts documents in a compromised system and offers a victim to purchase a decryption utility. Doctor Web registered several modifications of this malicious program that differed in length of encryption keys and in their visual manifestation in the system. Dr.Web analysts developed a free decryption utility that can be obtained from the web-site of Doctor Web.
Malicious e-mails
Messages spreading Trojan.DownLoad.4419 and Trojan.PWS.GoldSpy were the most typically cases of distribution of malicious code via e-mail in 2008.
Trojan.DownLoad.4419 got into a system as a “codec” required to view a supposed pornographic video. Authors of the malicious program often modified its executable and changed packers used to compress the file every now and then. It made detection of the Trojan more difficult for anti-viruses. As usual prompt updating of the Dr.Web virus database by analysts allowed Dr.Web software to detect numerous variations of Trojan.DownLoad.4419.
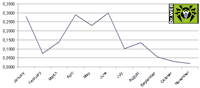
A wide variety of techniques was applied to spread Trojan.PWS.GoldSpy that came as a an e-card or as an attachment to a threatening message. In particular such messages warned a user that he would be disconnected from the Internet due to his violation of a copyright. In latest months Trojan.PWS.GoldSpy increased the number of e-mailed Trojans that featured password stealing. The diagram below represents how share of Trojan.PWS of the total amount of malicious e-mail changed in 2008.
Social networks
Increased popularity of social networks among users in Russia also attracted attention of virus makers who used fake accounts on social networking web-sites to trick users into downloading malicious code.
Now owners of social networking web-resources employ various techniques to secure their customers. Sometimes links sent with messages are displayed as plain text so a user has to copy a link to the address bar of a browser. Another option is displaying a warning to a user who clicks on a link leading to an external web-page. By now such measures have not allowed to solve the problem. Doctor Web offers all registered visitors of social networking web-sites to use high-quality anti-virus software or the free link-checker plugin from Doctor Web to scan linked content for viruses.
ICQ as another tool spreading malware
ICQ instant messaging service was also used to distribute malicious code this year. Malefactors created new accounts or used trusted UINs of ordinary users whose machines were compromised by malware capable of using the ICQ contact list to send messages.
Removable disks
As removable disks became the most common means to move information from one computer to another they were also put to use by virus makers as carriers of malicious code that entered Dr.Web database as Win32.HLLW.Autoruner. Authors of the malware exploited the autorun mechanism of Windows for execution of its code.
Removable data storage devices circulated widely among employees of large companies and so did the infection. Companies and governmental establishments were forced to restrict or even ban usage of removable disks.
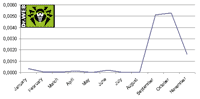
The next diagram shows how Win32.HLLW.Autoruner Trojans were rated among most common viruses through 2008. It suggests that virus makers tend to shift their preferences towards removable disks as means to spread malware. They employ various techniques making it harder to detect, analyze or remove a piece of malicious code from a flash drive.
Win32.Sector
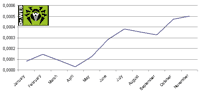
The file virus got an entire subsection of the review to itself as one of the biggest troublemakers of 2008. It infected executables, injected its code into system processes, disabled UAC in Windows Vista and downloaded other malicious programs from the Internet. See how Win32.Sector was detected by Dr.Web scanner in 2008 on the graph below.
The last months of the year have been marked by the increased number of phishing attacks. A user received a message that looked like an e-mail from a legitimate financial institution and was offered to follow a link to a bogus web-site that also looked like a genuine web-site of a corresponding company. As a user got to such a site, he was lured into submitting personal information including his credit card number and PIN code or login and password used to access a paid service via the Internet. Such messages were received by customers of such respected banks and service providers as JPMorgan Chase Bank, RBC Royal Bank, Google AdWords, PayPal and eBay.
In 2009 Instant massagers, removable disks and other alternative channels for distribution of malware will become even more popular among virus makers.
Authors of viruses will be perfecting their techniques that will provide them with even more complex polymorphic packers and other means to make analysis even more difficult. Numerous vulnerabilities found in operating systems and other software will be exploited by malefactors just as well. Doctor Web also expects that a number of e-mails containing malicious code will be rising at the beginning of 2009.
Detection and curing features of anti-viruses are also improved. That’s why some cyber criminals have to change their activities. For example, distributors of Trojan.DownLoad.4419 start sending e-mails providing links to advertising web-resources instead of malware.