Forty-nine botnets in four months with BackDoor.DarkNess
Real-time threat news
August 5, 2011
BackDoor.DarkNess is not just a backdoor allowing anyone to create a bot network and carry out DDoS-attack on a chosen target. It is a versatile tool for various tasks. For example, BackDoor.DarkNess.25 can steal user data from such popular programs as Total Commander (the FTP connection settings), FlashFXP, FileZilla, WS_FTP, QIP, CuteFTP, The Bat!, But the main purpose of the backdoor is DDoS-attacks on command from a remote server.
BackDoor.DarkNess is written in Delphi, the administrative part is implemented in PHP. Here is the login page for the botnet control system:
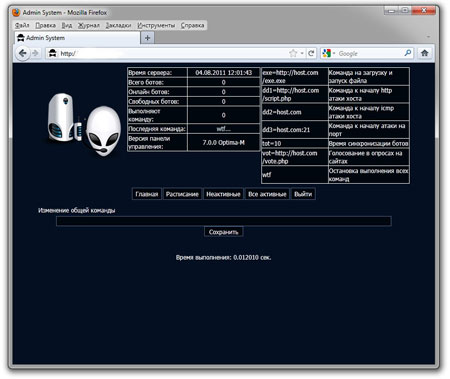
And this is the admin panel from the inside:
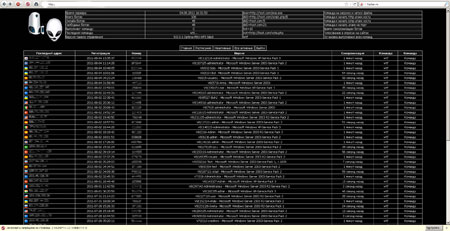
The actual control panel of an active botnet. The owners don't suspect they are being watched closely.
The backdoor runs in the operating system as a standard service and disables the Windows Firewall. After this, it contacts a remote command center and receives instructions, which among other things, may contain an order to download an executable file or to launch a DDoS-attack on a specified server. This is accomplished by repeated sending of GET-requests at an URL in several streams (up to 100) over a specified time interval. Multi-stream ICMP attacks or attacks on any chosen port on the remote node are also possible. A significant network load on the infected machine and absence of any disguise for its process in the operating system is a significant drawback in the backdoor design allowing its relatively easy detection and removal by anti-virus software.
Over the past four months, Doctor Web's virus analysts discovered 49 botnets created using BackDoor.DarkNess. About ten of them are still operational, and Doctor Web continues to monitor their activity closely. During this period bots received 329 unique commands, most of which initiated DDoS-attacks. Victims include mass media sites and online stores selling counterfeit copies of Swiss watches. Attack targets also include a large number of online game servers—apparently, availability of BackDoor.DarkNess in public domain gives an opportunity to would-be-"hackers" to control a large number of the botnets.
We can assume that due to the wide availability of this backdoor the number of botnets and their activity in the near future is unlikely to diminish. Despite the fact that BackDoor.DarkNess has been known for a long time, it still enjoys a certain popularity: Doctor Web's virus laboratory gets 30 new samples of this backdoor per month which gives an average of one sample per day. We also expect new versions of BackDoor.DarkNess with additional payload beside the basic DDoS-bot function. This backdoor program is detected by Dr.Web and removed while the anti-virusscans computer hard drives.