New Windows lockers and the new threats to Android
Virus reviews | All the news | Virus alerts
August 2, 2011
Windows lockers target users worldwide
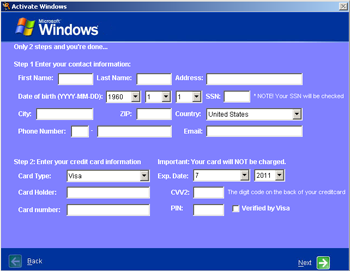
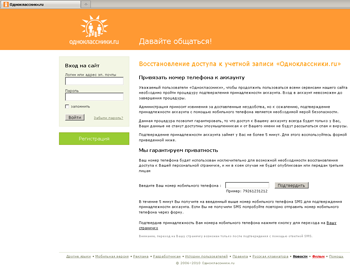
Russian computer users experienced two major waves of malware infection that blocked access to Windows: the first one took place from late 2009 to early 2010; the second swept the Russian segment of the Internet in the summer of 2010. Since then the number of infections has been falling steadily: nearly all anti-virus software manufacturers have learned to deal effectively with such threats, and users seem to have learned the basic safety rules. However, instances of extortionist programs targeting users outside Russia have been registered since May. One such program, Trojan.Winlock.3794, collects credit card information.
Credit card details that the Trojan horse sends to criminals include the holder's name, date of birth, address, phone number, card expiry date, card number, the CVV2 code, and even the pin code. With this information, the criminals will empty the compromised account of all funds with little effort. It should be noted that this is the first instance of a blocker Trojan horse that collects credit card information. Previous Windows lockers attacking Russian users usually required them to send paid short messages to a specific number or refill a mobile account.
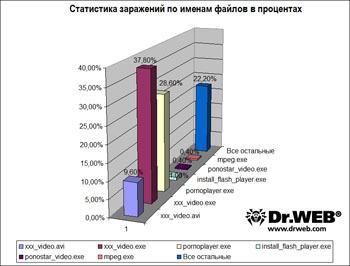
Using statistics collected since the end of January 2011, Doctor Web analysed the distribution of blocker program on the Internet. xxx_video.exe (37.8% instances of infection) was the most popular file name for the Trojan horses; pornoplayer.exe was the second most popular (28.6%), and xxx_video.avi (9,6%)was third. Notably, in the last case, it is a malicious link that has a file name with the .avi extension. The file, which contains a Trojan horse, can have a different name and extension. Malicious file names such as install_flash_player.exe (1%), ponostar_video.exe, and mpeg.exe (0.4%) modestly took the last few places in the ranking.
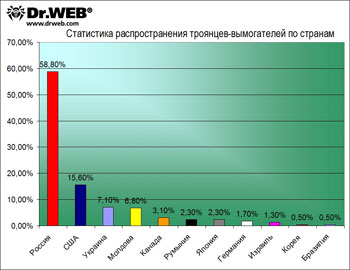
But figures for countries whose servers host sites spreading malware are somewhat different. Russia is the leader by a wide margin, with 58.8%. The USAis catching up but is still far behind with only 15.6% of Trojan horses downloaded from its servers. Ukraine (7.1%) takes third place, narrowly surpassing Moldova (6.8%) which in turn outstrips Canada (3,1%). They are followed by Romania (2,3%), Japan (2,3%), and Germany (1,7%), Israel (1.3%), and Korea and Brazil (both 0.5%) are at the bottom of the list.
The above shows that downloading malware in the guise of video players or films from adult content websites remains the most popular way to spread Trojan.Winlock horses.
Bank details in danger
In the past month Doctor Web virus analysts discovered a lot of malware designed to steal user information, including information for accessing online banking systems. Among them we should mention the Trojan horse whose description was added to the virus database under the name Trojan.Carberp.1.

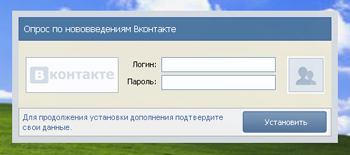
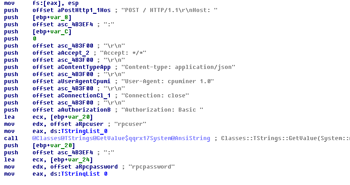
Like some other Trojan horse programs of this type, Trojan.Carberp.1 has built-in protection from analysis that utilizes a debugger. Data hashing and injecting code into several system processes are characteristic of this Trojan horse. When launched on an infected computer, the Trojan horse checks whether the process op_mon.exe , which belongs to Outpost Firewall, is running, and if so, ends it. Then the Trojan starts explorer.exe, injects its code into it, and tries to inject a malicious object into the instances of the explorer.exe process that controls the taskbar and Windows desktop. If it fails, Trojan.Carberp.1 tries to integrate into the svchost.exe process, and if this attempt fails, too, then it tries to infect any browser that lets you open files with the html extension. Then the malware copies itself into the Start-up folder, ends its dropper process, and starts several infected svchost.exeprocesses. One of the infected processes on the user's computer downloads the program miniav to seek out and remove rival Trojan horses (BarracudaAndBlackEnergy, Zeus, Limbo, Adrenalin, Generetic, and MyLoader); another process installs Trojan.PWS.Stealer.338 onto the machine to steal passwords stored by various applications.
Trojan.Carberp.1 sends intruders banking service access information, steals keys and passwords from various programs, works as a key logger, and takes screenshots, et cetera. In addition, the Trojan horse has a built-in module that allows it to receive and follow instructions from a remote command center. With this Trojan.Carberp.1 feature, attackers can visit websites anonymously by turning the victim's computer into a proxy server, download and run different files, send screen shots to a remote host, and even destroy the operating system.
July threat to Android
Makers of malicious programs for Android never stop "delighting" users with malicious novelties and keep anti-virus analysts alert and on their toes. In July Doctor Web's analysts added the definitions of 29 new malignant programs for this platform including two new Android.Gongfu modifications and Android.Ggtrack.1-2 that steals money from mobile accounts by subscribing their owners to various paid services.
In addition, in July, the spyware Android.GoldDream.1 was discovered and added to the virus databases.
This malware for Android, like its predecessor, is built into legitimate applications for mobile devices such as Drag Racing and Draw Slasher games and spreads through sites providing access to collections of software. When launched on a device, the Trojan horse runs as a background service and collects information such as the owner's phone number and the device’s IMEI number, and then sends it to the criminals' remote server. After that Android.GoldDream.1 starts monitoring all incoming SMS messages, as well as incoming and outgoing phone calls, and logs information about these events (including telephone numbers from which or to which you call or send messages, and also short message content) in a file stored locally. Later this file can be transferred to the authors of the spy software. In addition, Android.GoldDream.1 is able to execute commands coming from a remote command center to carry out the unauthorized sending of SMS spam, make phone calls as well as install various programs.
Doctor Web again urges users to download applications only from known and trusted sources (such as sites belonging to software developers and the official Android Market), pay attention to the privilege requests during installation, and use Dr.Web for Android Anti-virus&Anti-spam and Dr.Web for Android Light on your devices.
Other notable threats in July
At the end of July 2011, virus analysts registered a surge of infections by Trojan.Mayachok.1, and many users abruptly became unable to browse the web. When they tried to load a web page in a browser window, the Trojan horse redirected them to a certain address showing a web page that asked them to "activate" or "confirm" their account by specifying their phone number and replying to the incoming SMS. If the user followed the instructions, an amount of money was withdrawn from their account.
The most probable cause for the large-scale spreading of this program is carelessness on the part of users who followed links received with.
Virus analysts also discovered a malicious program that doesn't steal files or account information but utilizes system resources for criminals' needs. To date, there are several malicious programs that mine the electronic currency Bitcoin, in particular Trojan.Coinbit and some versions of Trojan.Vkbase. The new Trojan horse, Trojan.BtcMine.1, uses two legitimate mining programs to utilize resources of the victim's computer in order to "mine" virtual coins. This malware spreads from a variety of sites unrelated to the official Bitcoin project site.
The 48th modification in a row of Trojan.VkBase keeps up with Trojan.BtcMine.1. This malicious program, dubbed Trojan.VkBase.48, launches a Bitcoin miner on the infected computer. It enables the attackers to use the computing resources of the infected machine for their personal enrichment.
Once it gets onto the infected computer, Trojan.VkBase.48 creates the update.4.1 directory in the Windows installation folder, saves itself into the folder as svchost.exe, and runs as a background service. Then the Trojan horse checks the Internet connection by sending a request via HTTP to Google.com, Microsoft.com and Yandex.ru, and expects to receive a home page for each site as a reply. If it gets a reply, Trojan.VkBase.48 randomly generates a username and password for the Bitcoin system and stores them in the file% AppData% \ Bitcoin \ bitcoin.conf. Following this, the Trojan horse checks its own version (it can update itself), collects information about the infected machine (including the computer name, disk drive serial number, and disk types), and sends the information to a malicious server. Then the malware connects to its command centers and exchanges data with them. On command Trojan.VkBase.48 can download the Bitcoin server and run it as a service.
Malicious files detected in mail traffic in July.
| 01.07.2011 00:00 - 01.08.2011 00:00 | ||
| 1 | Trojan.Tenagour.3 | 21388 (14.56%) |
| 2 | Win32.HLLM.MyDoom.54464 | 17624 (11.99%) |
| 3 | Win32.HLLM.MyDoom.33808 | 15827 (10.77%) |
| 4 | Win32.HLLM.Netsky.18401 | 7746 (5.27%) |
| 5 | Win32.HLLM.MyDoom.based | 7464 (5.08%) |
| 6 | Win32.HLLM.Netsky | 6676 (4.54%) |
| 7 | Win32.HLLM.Netsky.35328 | 5216 (3.55%) |
| 8 | Trojan.PWS.Banker.57999 | 3906 (2.66%) |
| 9 | Trojan.DownLoad2.31588 | 3032 (2.06%) |
| 10 | BackDoor.IRC.Nite.60 | 2646 (1.80%) |
| 11 | Trojan.Packed.21790 | 2579 (1.76%) |
| 12 | Trojan.DownLoader4.3483 | 2421 (1.65%) |
| 13 | Trojan.DownLoader4.372 | 2184 (1.49%) |
| 14 | Trojan.MulDrop1.54160 | 2142 (1.46%) |
| 15 | Win32.HLLM.Beagle | 2071 (1.41%) |
| 16 | Trojan.PWS.Siggen.18719 | 1758 (1.20%) |
| 17 | Win32.HLLM.Perf | 1472 (1.00%) |
| 18 | Win32.HLLW.Autoruner.52856 | 1420 (0.97%) |
| 19 | Exploit.IframeBO | 1350 (0.92%) |
| 20 | Win32.HLLM.MyDoom.33 | 1257 (0.86%) |
Total scanned: 221,764,143
Infected: 146,942 (0.07%)
Malicious files detected on user machines in July
| 01.07.2011 00:00 - 01.08.2011 00:00 | ||
| 1 | JS.Click.218 | 114599272 (60.12%) |
| 2 | Win32.Siggen.8 | 13149524 (6.90%) |
| 3 | JS.IFrame.112 | 11440667 (6.00%) |
| 4 | Win32.Rmnet.12 | 10631422 (5.58%) |
| 5 | JS.IFrame.95 | 8711978 (4.57%) |
| 6 | JS.IFrame.117 | 5662466 (2.97%) |
| 7 | JS.Click.222 | 4025723 (2.11%) |
| 8 | Win32.HLLP.Neshta | 3667732 (1.92%) |
| 9 | Trojan.MulDrop1.48542 | 3646674 (1.91%) |
| 10 | Win32.HLLP.Whboy.101 | 2548789 (1.34%) |
| 11 | JS.Click.223 | 2054152 (1.08%) |
| 12 | Win32.HLLP.Rox | 1763730 (0.93%) |
| 13 | VBS.Redlof | 1121512 (0.59%) |
| 14 | Win32.HLLW.Whboy | 811492 (0.43%) |
| 15 | Win32.Gael.3666 | 648264 (0.34%) |
| 16 | Trojan.NtRootKit.10544 | 507715 (0.27%) |
| 17 | Trojan.PWS.Ibank.300 | 336559 (0.18%) |
| 18 | Win32.HLLP.Whboy | 247904 (0.13%) |
| 19 | Exploit.Cpllnk | 223049 (0.12%) |
| 20 | Trojan.DownLoader4.10788 | 189955 (0.10%) |
Total scanned: 109,063,398,454
Infected: 190,624,133 (0.17%)