New Trojan.Winlock extorts credit card data
Real-time threat news | All the news | Virus alerts
12 июля 2011 года
The first instances of infection by Trojan.Winlocks were registered in 2007. The period from November 2009 till February 2010 saw massive spreading of these programs comparable to a full-scale epidemic. Trojan.Winlock.3794 has an interface and operates similarly to earlier versions of Windows lockers well-known in Russia but targets users all over the world.
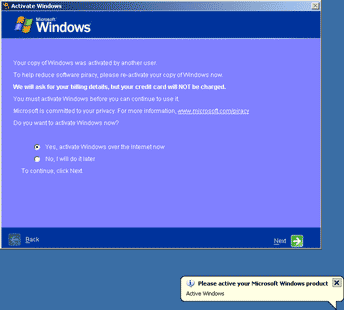
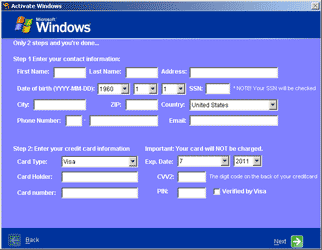
Like its many predecessors, this Trojan horse mimics the built-in Windows XP activation interface. The program window blocks the Windows desktop and notifies a user that the copy of Windows has already been activated by another user and offers them to re-activate the system. If the user selects No, I will do it later, they see the blue screen of death. If the user agrees to re-activate their copy of Windows, they will be prompted to enter their credit card information including the owner's full name, card number CVV2 and even the pin-code in corresponding fields of a form that appears on the screen. It is quite obvious which consequences may arise from divulging such information to criminals.
From the engineering point of view, the organisation of Trojan.Winlock.3794 is a primitive one which is typical of all species in the family. Once it gets into the system, it adds a link pointing to its own self into the autorun section of the Windows registry. As a consequence, access to Windows is blocked both in the standard and safe modes. Besides, the Trojan horse prevents launching of any Windows applications including the Task Manager, System Restore, etc. which complicates its neutralization with easy-to-access tools.
It should be noted that this is the first instance of the blocker Trojan horse that collects credit card information. Windows lockers attacking Russian users usually demanded that they send paid short messages at a specified number or refill a mobile account. Apparently, with Trojan.Winlock.3794 its authors decided on going globally and emergence of more sophisticated programs of the same type is to be expected in the nearest future including Trojan horses modifying the MBR.
Dr.Web anti-viruses neutralize any Trojan.Winlock modifications including the latest one successfully. In any case, following several simple rules will help you avoid any problems related to such Trojan horses:
- Use up-to-date anti-virus software.
- Scan your computer for viruses and other malware regularly.
- Update viruses databases in a timely manner to keep them up-to-date.
- Regularly install security updates, recommended by the manufacturer of your operating system.
- Do not run suspicious applications or self-extracting archives downloaded from the Internet or obtained from unreliable sources.
- If despite all the efforts your system has been compromised by such a Trojan horse, use Dr.Web LiveCD for emergency system restoring and the Dr.Web CureIt! utility.