Doctor, where did you get these pictures? Using steganography in a cryptocurrency mining campaign.
Real-time threat news | Hot news | All the news | Virus alerts
January 24, 2025
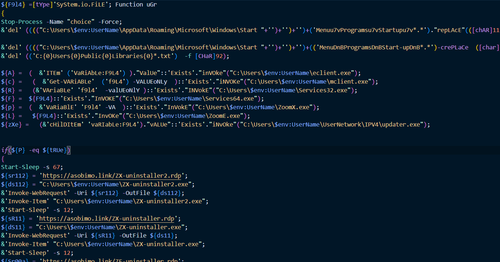
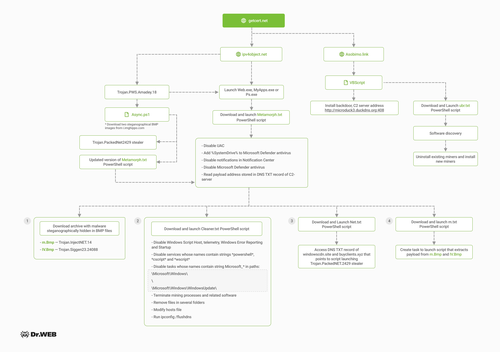
The campaign likely began in 2022 when our analysts first observed Services.exe, a .NET application that launched a malicious VBscript. This script implements backdoor functionality by contacting the attacker's server and executing the scripts and files sent in response. For example, the malicious file ubr.txt, a PowerShell script whose extension was changed from ps1 to txt, was downloaded to the victim's computer.
The ubr.txt script checks for miners that may already be installed on the compromised machine and replaces them with the versions the attackers provide. The files installed by the script are the SilentCryptoMiner miner and its configuration, which the hackers used to mine the Monero cryptocurrency.
We have reported on the use of this miner by attackers who are attracted by its ease of configuration, its advanced capabilities for mining different types of cryptocurrencies and hiding from diagnostic utilities, and its ability to remotely manage all of the miners in the botnet via a web panel.
As part of this campaign, the miner files are disguised as components of various software, such as the Zoom video conferencing application (ZoomE.exe and ZoomX.exe), Windows services (Service32.exe and Service64.exe), etc. Although there exist several sets of malicious modules with different names, they all perform the same tasks: removing other miners, installing a new miner, and delivering updates for it.
PowerShell script ubr.txt
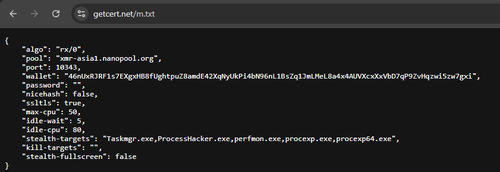
In addition, the miner accesses the getcert[.]net domain, which hosts the m.txt file containing the cryptocurrency mining settings. This domain is also used in other infection chains.
The miner configuration included in the m.txt file
Later, fraudsters modified the attack methodology, making it much more interesting and incorporating steganography tools.
Steganography is a method of hiding information within other information. Unlike cryptography, which can draw attention to encrypted data, steganography allows information to be hidden inconspicuously, such as in an image. Many cybersecurity experts believe that the use of steganography to bypass defenses will grow in popularity.
The image on the left (credit: Marek Piwnicki) contains a hidden image with the Dr.Web logo
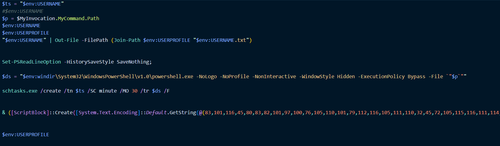
The second, more recent chain employs the Amadey trojan, which runs the PowerShell script Async.ps1. The script downloads BMP images from the legitimate image-hosting site imghippo.com. A steganographic algorithm extracts two executables from the images: the Trojan.PackedNET.2429 stealer and a payload that does the following:
- Disables the UAC prompt for administrators
- Makes numerous exceptions to the built-in Windows Defender antivirus
- Disables notifications in Windows
- Creates a new task in \Microsoft\Windows\WindowsBackup\ with the name 'User'.
Contents of the Async1.ps script
During its execution, the task accesses the attackers' domains whose DNS TXT record contains the address of the payload. After downloading it, the archive containing BMP images is unpacked and the following files are launched:
-
Cleaner.txt, a PowerShell script that removes all other miners,
-
m.txt, a PowerShell script that extracts payloads from m.Bmp and IV.Bmp images. The payload inside the images is SilentCryptoMiner and the injector that runs it,
-
Net.txt, a script that reads a DNS TXT record from the domains windowscdn[.]site and buyclients[.]xyz. This record contains a payload link pointing to raw.githack[.]com.
A DNS TXT record is an extension of the standard DNS record and contains data that helps to verify a domain. However, the domain owner can include any data in it, such as, in this case, a payload link.
Contents of the archive with malicious images
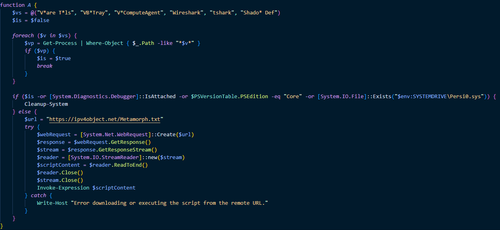
The miner modules are constantly evolving. Recently, the authors switched to using legitimate resources to host malicious images and the GitHub platform to store payloads. Additionally, we have observed modules that verify whether this malware is running in sandboxes and virtual machines.
A module that checks the names of running applications against the names of common tools used by cybersecurity researchers
One of the wallets found in the miner's configuration was created in May 2022, and so far, it has received 340 XMR. However, the exchange rate of this cryptocurrency is experiencing a period of significant volatility, so in this case the fraudsters' profit could be 65–70 thousand USD. Judging by the wave-like shape of the hash rate curve, which indicates that the computers in the botnet are turned on and off regularly, this mining campaign mostly involves ordinary users located in the same group of time zones. On average, the hash rate is 3.3 million hashes per second, which allows compromised machines to earn the attackers 1 XMR every 40 hours or so.
This campaign is just the tip of the iceberg in the world of steganography-based cyber threats and underscores the importance of being vigilant in the digital space. Doctor Web's recommendations remain unchanged: only install software from reliable sources, do not click on suspicious links, and do not disable antivirus protection when downloading files from the Internet.
Attack chain
Read more about SilentCryptoMiner
Read more about PowerShell.Starter.98
Read more about PowerShell.DownLoader.1640
Read more about Trojan.PackedNET.2429
Read more about VBS.DownLoader.2822