Contactless banking for thee (and for thief): NFC money theft scheme reaches Russian users
Real-time threat news | Hot news | All the news | Virus alerts
December 26, 2024
The NGate banker first appeared on the radar of antivirus vendors in the autumn of 2023, when reports of attacks on customers of major Czech banks began to appear in specialized media. The attackers' strategy involved a combination of social engineering, phishing and the use of malware. When used together, these standard tactics created a rather innovative scenario: after interacting with the victim, the hackers gained remote access to the NFC capabilities of their payment method. Law enforcement in the Czech Republic was able to stop this campaign, but its concept was adapted to the Russian context and used there for illegal enrichment.
The event that initiates the chain of attack is likely to be a phone call from fraudsters claiming that the victim is eligible for a social benefit or other financial gain. To receive it, the victim must tap on the link, which leads to a fraudulent website, that hosts a malicious APK containing the NGate trojan. The APK is disguised as an application for the Gosuslugi (government services) portal, the Bank of Russia or one of the other popular banks.
Icons of fake applications, made to look like their official counterparts
The NGate banking trojan is a malicious modification of the open source NFCGate application, which was developed to debug NFC data transfer protocols. NFCGate supports a number of functions, but of most interest to attackers is the ability to capture NFC traffic and send it to a remote device, which could be either an intermediary server or the attacker's own smartphone. The criminals have modified the source code by adding user interfaces similar to the official applications and enabling the NFC data relay mode. In addition, the application includes the nfc-card-reader library, which allows the hackers to remotely obtain the card number and its expiry date.
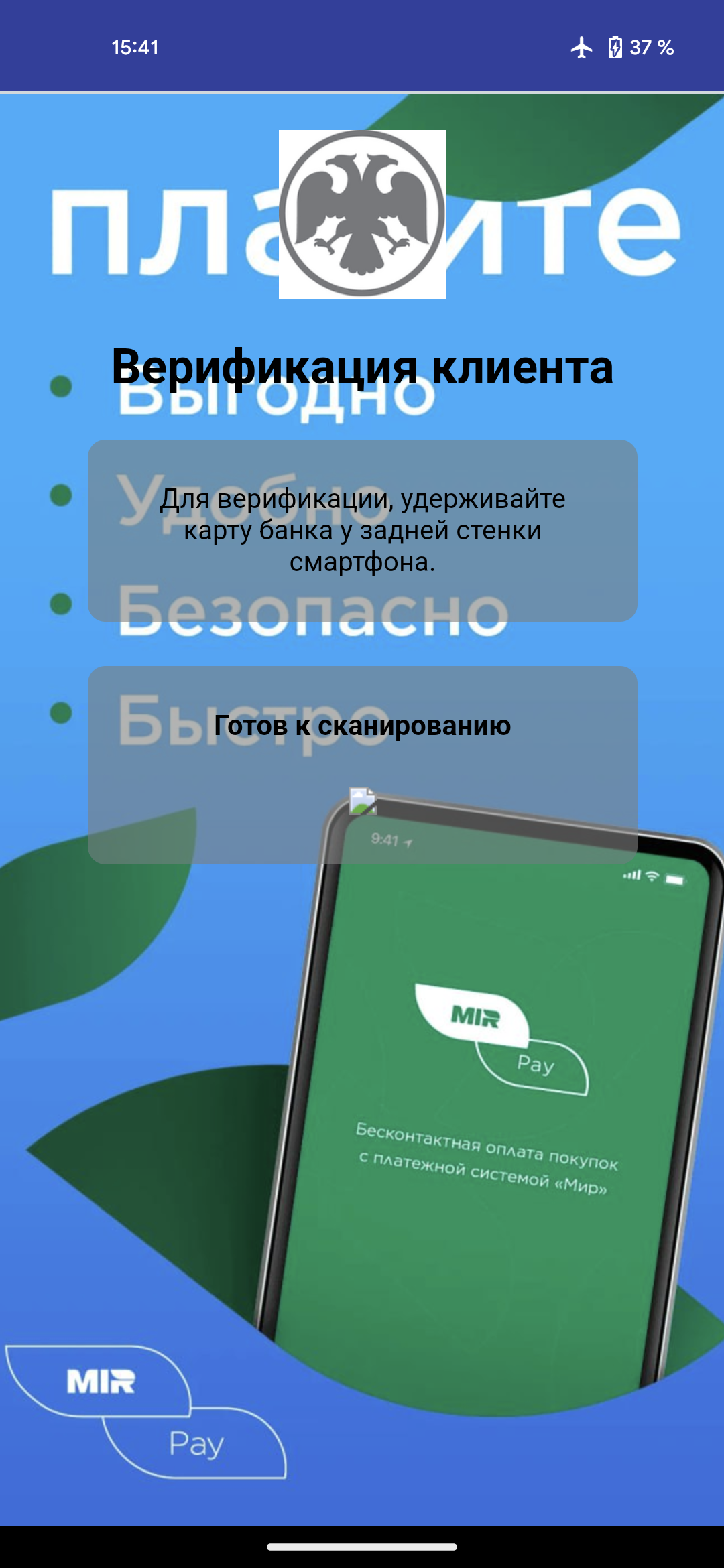
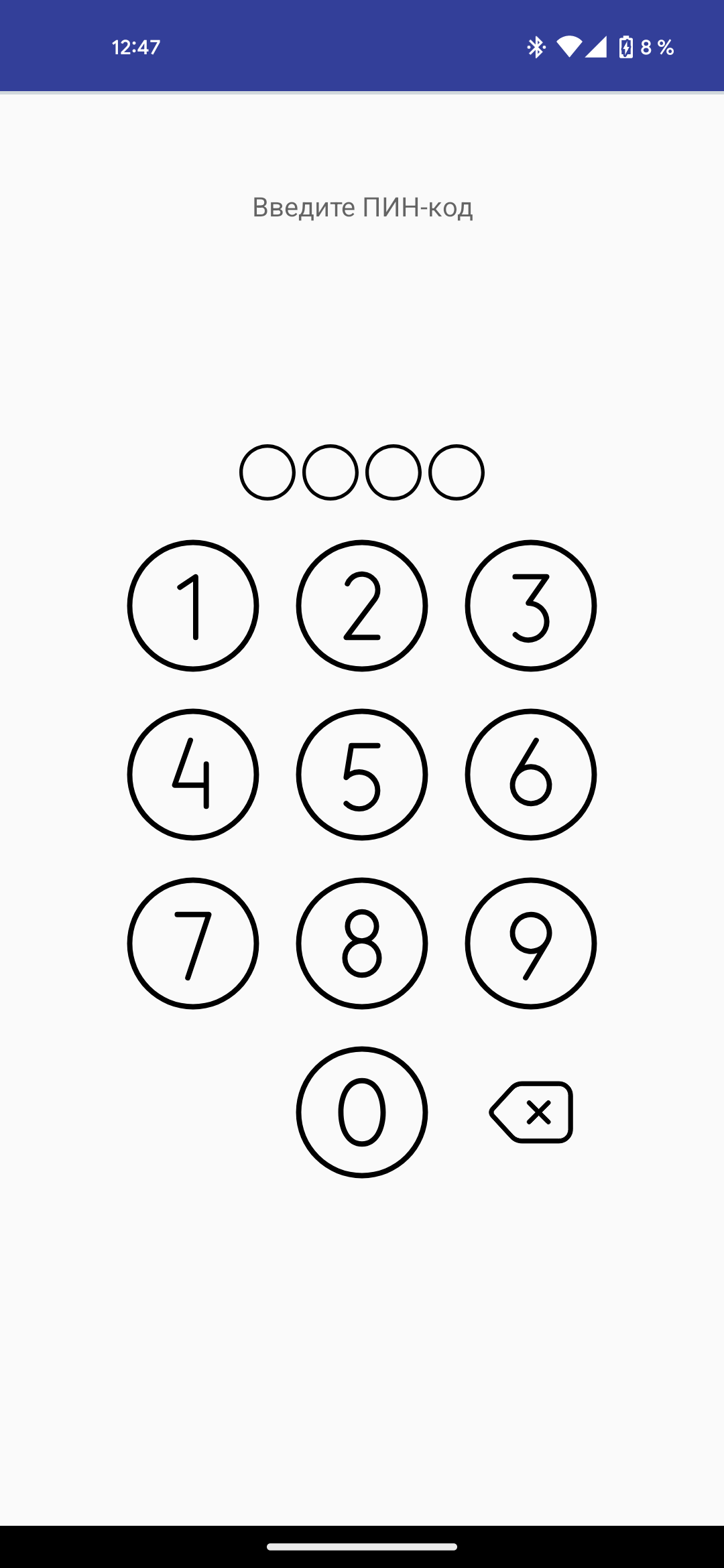
After launching the application, the victim is prompted to place their payment card on the back of the smartphone, enter the PIN and wait for the fake application to verify the card. At this point, all the data on the card is read and transferred to the criminals. Note that the compromised smartphone does not need to be rooted to expose its NFC data.
Screens that ask the victim to place their bank card on the back of their smartphone.
While the victim holds their card close to their smartphone, the attacker is already at the ATM requesting a cash withdrawal. Another option is to use this scheme for contactless payments. When the ATM asks for the bank card, the hacker simply taps their phone, which will transmit the digital thumbprint of the victim's bank card. The transaction is confirmed using the PIN code the victim previously submitted.
To prevent money theft, the analysts at “Doctor Web” have the following recommendations:
- do not share your PIN or CVV codes for your bank cards,
- use an antivirus program, it will block downloading and installation of malicious applications,
- carefully check the addresses of web pages that ask for financial information,
- only install applications from official sources such as AppGallery and Google Play,
- do not talk to scammers. If you receive an unexpected call from the police, a bank or any other organization, simply hang up. If you have any doubts about the legitimacy of the call, find the contact details on the official website and contact the organization yourself.
More about Android.Banker.NGate.1
Indicators of compromise