Doctor Web’s Q4 2024 virus activity review
December 26, 2024
Users whose files were affected by encoder trojans most commonly encountered Trojan.Encoder.35534, Trojan.Encoder.35067, and Trojan.Encoder.26996.
Once again, the most widespread threats observed on Android devices were Android.HiddenAds ad-displaying trojans. At the same time, our malware analysts discovered many new threats.
Principal trends in Q4 2024
- Adware software and adware trojans were once again the most commonly detected threats.
- The number of unique threats increased, compared to the previous quarter.
- Increased activity on the part of spyware trojans in email traffic.
- The distribution of many trojan apps through Google Play.
According to Doctor Web’s statistics service
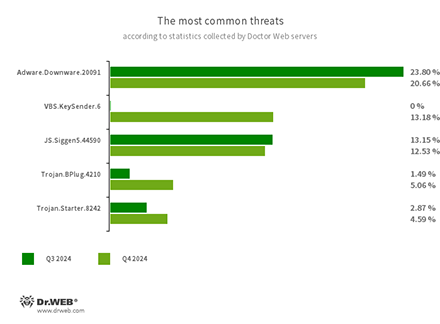
The most common threats in Q4 2024:
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- VBS.KeySender.6
- A malicious script that, in an infinite loop, searches for windows containing the text mode extensions, разработчика, and розробника and sends them an Escape key press event, forcibly closing them.
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- Trojan.BPlug.4210
- The detection name for malicious components of the WinSafe browser extension. These components are JavaScript files that display intrusive ads in browsers.
- Trojan.Starter.8242
- A malicious program that launches a mining trojan.
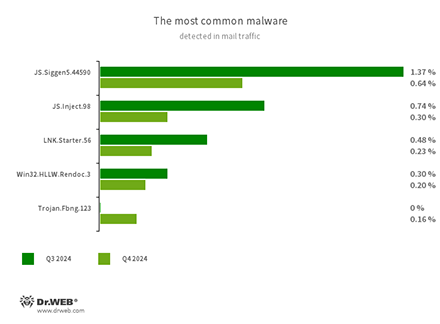
Statistics for malware discovered in email traffic
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- LNK.Starter.56
- The detection name for a shortcut that is crafted in a specific way. This shortcut is distributed through removable media, like USB flash drives. To mislead users and conceal its activities, it has a default icon of a disk. When launched, it executes malicious VBS scripts from a hidden directory located on the same drive as the shortcut itself.
- Win32.HLLW.Rendoc.3
- A network worm that spreads via removeable storage media and other channels.
- Trojan.Fbng.123
- A spyware trojan also known as Formbook. Designed to steal various data from infected devices, it hijacks passwords saved in web browsers, email clients, online messengers, and other software; intercepts input data in web forms; monitors keystrokes (it executes a keylogger functionality); and takes screenshots. In addition, it can download and run other programs and execute various commands, operating as a backdoor.
Encryption ransomware
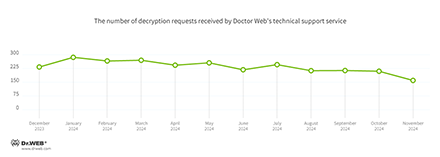
In Q4 2024, the number of requests made to decrypt files affected by encoder trojans decreased by 18.96%, compared to Q3 2024.
The dynamics of the decryption requests received by Doctor Web’s technical service:
The most common encoders of Q4 2024:
- Trojan.Encoder.35534 — 22.63% of user requests
- Trojan.Encoder. 35067 — 3.91% of user requests
- Trojan.Encoder.26996 — 3.35% of user requests
- Trojan.Encoder.35209 — 3.07% of user requests
- Trojan.Encoder.38200 — 3.07% of user requests
Network fraud
In Q4 2024, threat actors continued exploiting a popular fraudulent scheme in which they used specially crafted websites to offer potential victims opportunities to make money through different investments. To “access” the investing service, users are asked to register an account by providing personal data that subsequently ends up in the fraudsters’ hands. Residents of various countries have encountered such websites.
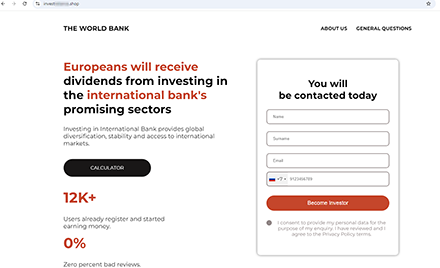
On this fraudulent site, supposedly affiliated with the World Bank, European users are assured that they will get dividends for investing in promising economic sectors
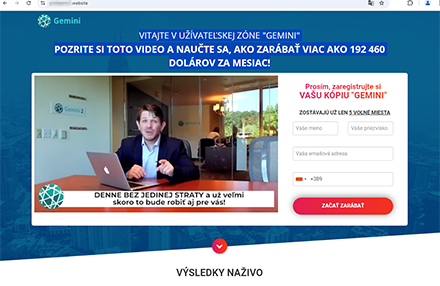
A fraudulent website offers Slovak users the chance to “earn more than $192,460 per month” with the help of some investing service
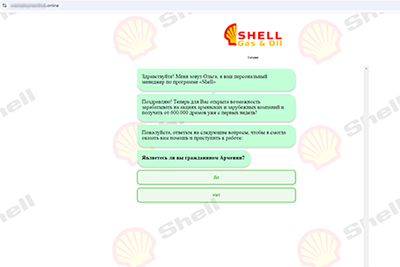
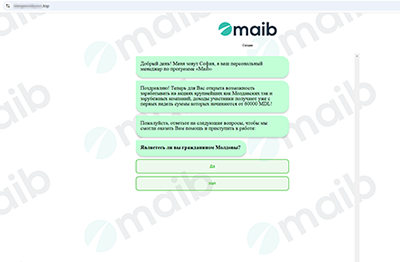
Fraudsters pose as large banks and oil and gas companies and offer users from Armenia and Moldova opportunities to “make money on stocks”
The fake website of an Azerbaijani oil and gas company on which visitors are promised income starting from 1,000 manat per month
The website of a “new Google investing platform” offers the opportunity to take a survey and get access to a service that will supposedly allow users to make at least €1,000
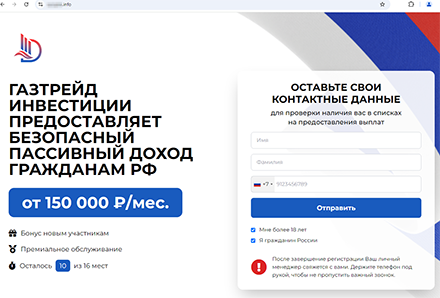
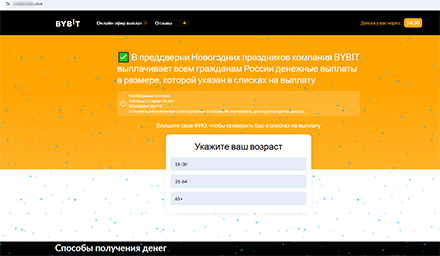
One of the fraudulent sites promises Russian users “a safe passive income”, starting from 150,000 rubles per month
Doctor Web’s experts noted a seasonal change in the contents of such sites. Ahead of the New Year holidays, scammers began exploiting the gifts theme, allegedly acting on behalf of banks, oil and gas companies, crypto exchanges, and other organizations. On one such fake site, Russian users supposedly could receive payments from a crypto exchange in accordance with some “lists”. And to check whether such payments are available to them, potential victims were asked to take a survey and provide personal data.
A fake crypto exchange website offers Russian users the chance to get “New Year payments”
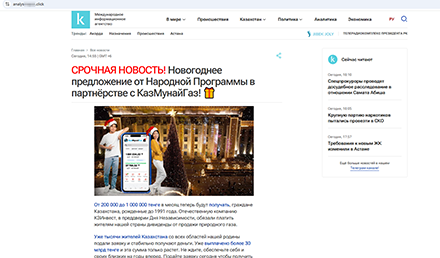
Another fake site informed visitors about some “New Year’s offer” from an oil and gas company, whereby many Kazakhstani users could allegedly start receiving from 200,000 to 1,000,000 tenge per month in honor of the country’s Independence Day. To “receive” payments, potential victims had to submit an “application” by providing their personal information on this website.
This fraudulent site promised Kazakhstani users large payments in honor of Independence Day as part of a “New Year’s offer”
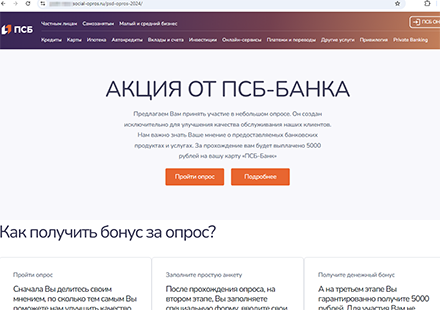
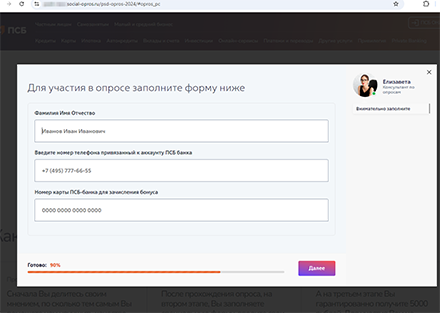
At the same time, our Internet analysts detected the emergence of new fake websites of Russian banks. On these, potential victims are asked to take part in a service-quality survey and then allegedly receive a money reward for doing so. Users are asked to provide personal data, including their full names, the mobile phone number linked to their bank account, as well as their bank card number.
An example of a bogus site that mimics the appearance of a genuine bank website and offers potential victims the opportunity to participate in the survey for a reward
To “participate” in the survey, the user has to fill out the form by providing their personal information
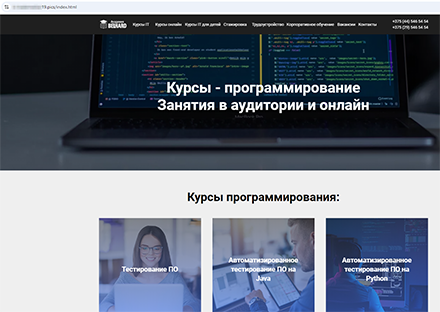
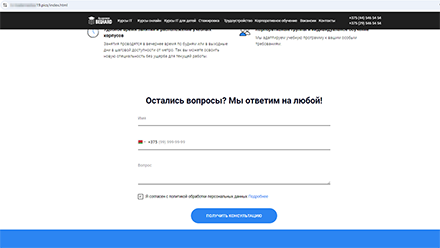
Moreover, fraudulent sites offering online training, such as programming, were identified. Interested visitors were asked to leave their contact information to “receive a consultation”.
A website that offers programming courses online. To “receive a consultation”, users have to provide their personal information.
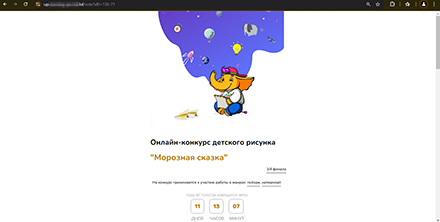
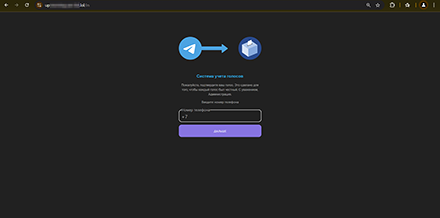
Online scammers keep trying to steal Telegram accounts. In Q4 2024, more phishing sites disguised as various online voting platforms were discovered, for example, for “children’s drawing competitions”. To “confirm” their vote, users are asked to provide their mobile phone number to which a verification code will be sent. However, by typing this code on the bogus website, they are granting fraudsters access to their accounts.
A scammer website on which visitors are asked to vote in the children’s drawing competition
A “vote counting system” demands a mobile phone number for “confirming the vote” and sending a one-time code
When victims enter the received code, they grant the fraudsters access to their Telegram accounts
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web Security Space for mobile devices, in Q4 2024, users most often encountered Android.HiddenAds ad-displaying trojans and the Android.FakeApp and Android.Siggen malicious apps. At the same time, over the past quarter, Doctor Web’s experts discovered many new threats on Google Play.
The following Q4 2024 events involving mobile malware are the most noteworthy:
- High activity on the part of Android.HiddenAds ad-displaying trojans and Android.FakeApp fraudulent malware,
- The emergence of new malicious apps on Google Play.
To find out more about the security-threat landscape for mobile devices in Q4 2024, read our special overview.