Malware trends: eBPF exploitation, malware configurations stored in unexpected places, and increased use of custom post-exploitation tools
Real-time threat news | Hot news | All the news | Virus alerts
December 10, 2024
A client approached Doctor Web after suspecting that their computer infrastructure had been compromised. While analyzing the client’s data, our virus analysts identified a number of similar cases, leading them to conclude that an active campaign was underway. It appears that the hackers' efforts are primarily concentrated in Southeast Asia. During the attacks, they utilize a comprehensive suite of malware that is deployed at various stages. Unfortunately, it was impossible for our analysts to determine how initial access to the compromised machines was obtained. However, they were able to reconstruct the rest of the attack chain. Notably, the threat actors managed to maliciously exploit eBPF (extended Berkeley Packet Filter) technology.
eBPF technology was developed to enhance control over the network subsystem of the Linux operating system and its processes. It has demonstrated significant potential, attracting the attention of major IT companies: almost from the moment of its inception, giants like Google, Huawei, Intel, and Netflix joined the eBPF Foundation to participate in its further development. Unfortunately, hackers have also taken an interest in eBPF.
By providing extensive low-level capabilities, eBPF can be used by malicious actors to conceal network activity and processes, gather confidential information, and bypass firewalls and intrusion detection systems. The amount of effort needed to detect such malware allows hackers to use it in APT (advanced persistence threat) attacks and to mask their presence for extended periods.
These are the capabilities that the attackers decided to exploit by loading two rootkits onto the compromised machine. The first was an eBPF rootkit that concealed the operation of another rootkit, implemented as a kernel module, which in turn prepared the system for the installation of a remote access trojan. A notable feature of the trojan is its support for various traffic-tunneling technologies that allow it to communicate with the attackers from private network segments and conceal the transmission of commands.
Overall, since 2023, the use of malicious eBPF software has been gaining momentum. This is evidenced by the emergence of several families of malware based on this technology, including Boopkit, BPFDoor, and Symbiote. New vulnerabilities, routinely found in this technology, only exacerbate the situation. As of now, 217 BPF vulnerabilities are known to exist, with about 100 of them discovered in 2024.
Another notable feature of the campaign is the rather creative approach taken by the threat actors with regards to storing the trojan's settings. Previously, they were likely to use dedicated servers for such purposes, but now instances where the malware configurations are being stored openly on public platforms are increasing. For example, the malware in question accessed platforms like GitHub and even a Chinese blog on information security. This helps draw less attention to the traffic coming from the compromised machine, as to an unsuspecting observer, the machine appears to be interacting with a safe network host. This negates the need to ensure access to a control server where settings are stored. Overall, the idea of leveraging publicly available services as a control infrastructure is not new; hackers are known to have previously used Dropbox, Google Drive, OneDrive, and even Discord for this purpose. However, regional restrictions on these services in several countries, particularly in China, make them less attractive in terms of ensuring availability. Meanwhile, access to GitHub remains available to most providers, making it preferred in the eyes of hackers.
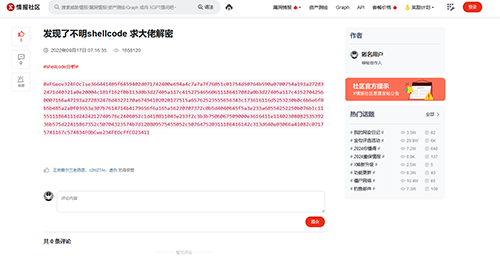
Settings stored on GitLab and in a security blog. Curiously, in the latter case, the hacker asks for help decrypting third-party code. The code will later be sent to the trojan as an argument for one of the commands.
Another feature of this campaign is that the trojan is starting to be adapted for later use as a component for a post-exploitation framework, which is a suite of software used after a computer has been accessed. Such frameworks are not inherently illegal; they are used by companies that officially provide security-audit services. The most popular tools are Cobalt Strike and Metasploit, which allow a large number of checks to be automated and have a built-in vulnerability database.
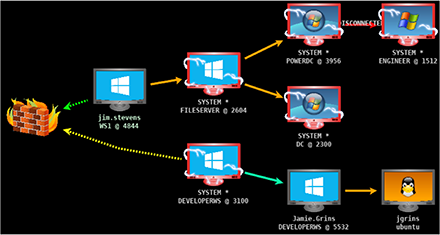
An example of a network map created by Cobalt Strike (source: official website)
Of course, such capabilities are highly sought after by threat actors. In 2022, a cracked version of Cobalt Strike became available to a wide audience, leading to a surge in hacker activity. Geographically, the Cobalt Strike infrastructure has a significant presence in China. It is worth noting that the developer aims to track all Cobalt Strike installations, and servers with cracked versions are routinely shut down by law enforcement. Therefore, hackers are steadily trending towards using open-source frameworks that support extensions out of the box and are able to modify the network communication between the infected host and its control server. They prefer this strategy as it does not draw additional attention to their infrastructure.
As a result of the investigation, our analysts added all identified threats to our malware databases and incorporated additional heuristic rules to ensure that malicious eBPF programs are recognized.
More about Trojan.Siggen28.58279