Malicious apps on Google Play: how threat actors use the DNS protocol to covertly connect trojans to C&C servers
Real-time threat news | Hot news | Threats to mobile devices | All the news
November 11, 2024
Android.FakeApp.1669 is represented by a large number of modifications that are disguised as various programs on distribution sources that include Google Play. For instance, the currently known trojan variants have been downloaded from the official Android OS digital store at least 2,160,000 times.
Examples of the programs in which Android.FakeApp.1669 was hidden
Below is the list of the Android.FakeApp.1669 variants that Doctor Web’s malware analysts discovered on Google Play. Our experts detected more trojans, but some of them are no longer in this app store.
| App name | Number of downloads |
|---|---|
| Split it: Checks and Tips | 1,000,000+ |
| FlashPage parser | 500,000+ |
| BeYummy - your cookbook | 100,000+ |
| Memogen | 100,000+ |
| Display Moving Message | 100,000+ |
| WordCount | 100,000+ |
| Goal Achievement Planner | 100,000+ |
| DualText Compare | 100,000+ |
| Travel Memo | 100,000+ (is deleted) |
| DessertDreams Recipes | 50,000+ |
| Score Time | 10,000+ |
When launched, Android.FakeApp.1669 sends a DNS request to its C&C server to receive the TXT record associated with the name of a target domain. In turn, the server gives this record to the trojan only if the infected device is connected to the Internet via target providers, which include mobile Internet providers. Such TXT records usually contain domain data and some additional technical information, but in the case of Android.FakeApp.1669, the malware’s configuration is encoded into it.
Android.FakeApp.1669 uses modified code of the dnsjava Open Source library to send DNS requests.
All trojan modifications are tied to specific domain names, which allows the DNS server to send each of them their own configuration. Moreover, the sub-domain names of these target domains are unique to each infected device. They contain encoded data about the device, including sensitive information:
- device model and brand;
- screen size;
- ID (it consists of two numbers: the first is the malware’s installation time, and the second is a random number);
- whether the device’s battery is charging and its current charge percentage;
- whether the developer settings are enabled.
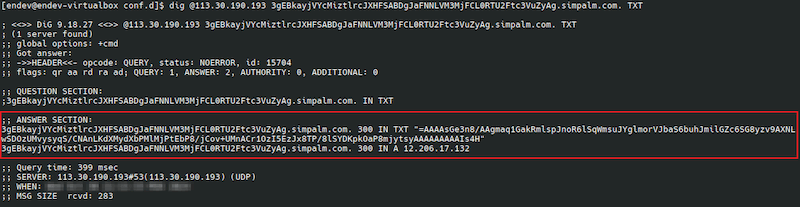
For example, when analyzed, the Android.FakeApp.1669 variant hidden in the Goal Achievement Planner program requested the server to send it the TXT record for the domain 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]simpalm[.]com.; the variant from the Split it: Checks and Tips program requested the record for the domain 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]revolt[.]digital., and the variant from the DessertDreams Recipes app requested the record for the domain 3gEBkayjVYcMiztlrcJXHFWABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]outorigin[.]com..
An example of a target domain’s TXT record, which was sent by the DNS server upon request via the Linux ‘dig’ tool when one of the Android.FakeApp.1669 modifications was undergoing analysis
The contents of these TXT records can be decrypted by doing the following:
- reversing the string;
- decoding the Base64 data;
- decompressing the gzip data;
- splitting it into lines by the character ÷.
The resulting data will look like this (the example below relates to the TXT record for the Goal Achievement Planner app):
url
hxxps[:]//goalachievplan[.]pro
af_id
DF3DgrCPUNxkkx7eiStQ6E
os_id
f109ec36-c6a8-481c-a8ff-3ac6b6131954
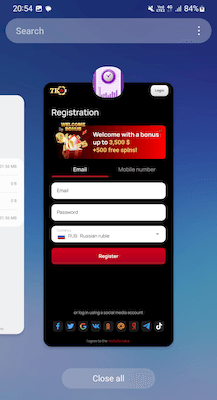
This data contains the link that the trojan loads in WebView inside its window over its main interface. This link leads to the website that starts a long chain of redirects, at the end of which is an online casino site. As a result, Android.FakeApp.1669 literally transforms into a web application that displays the contents of the loaded website and not the functionality declared on the app’s page on Google Play.
Instead of providing the expected functionality, the malicious program displayed the contents of a loaded online casino website
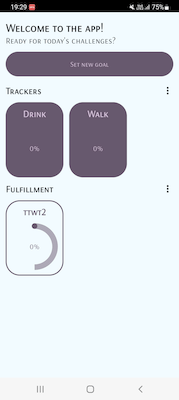
At the same time, when the trojan has Internet access via non-targeted service providers (and also when offline), it operates as the advertized program—on condition that the creators of a particular malware modification provided some functionality for such a case.
The trojan did not receive a configuration from the C&C server and launched as a normal app
Dr.Web Security Space for mobile devices successfully detects and deletes all known Android.FakeApp.1669 modifications, so this trojan does not pose a threat to our users.
More details on Android.FakeApp.1669