Redis honeypot: server with vulnerable Redis database reveals new SkidMap modification used to hide cryptocurrency mining process
Real-time threat news | Hot news | All the news | Virus alerts
October 3, 2024
The Redis database management system is the world’s most popular NoSQL database: Redis servers are used by large companies such as X (formerly Twitter), Airbnb, Amazon and others. Its advantages are obvious: maximum performance, tiny memory footprint, and support for various data types and programming languages. However, this product also has some downsides: since Redis was never intended to be used at the network’s edge, it only supports basic security features in its default configuration, and no access control and encryption mechanisms exist prior to version 6. In addition, cybersecurity publications report numerous Redis vulnerabilities each year. In 2023, for example, there were 12 vulnerabilities, three of which had a “Serious” status. The growing number of reports of compromised servers and the subsequent installation of mining programs sparked the interest of Doctor Web's virus lab staff, who wanted to experience the attack firsthand. For this purpose, they decided to set up their own unprotected Redis server and wait for uninvited guests. The server was active for a year, and during that time it was attacked about 10–14 thousand times a month. Recently, the server was hit with a modification of the SkidMap trojan, as our analysts expected. What came as a surprise, however, was that the cybercriminals used a new method to hide the miner's activity and installed four backdoors at the same time.
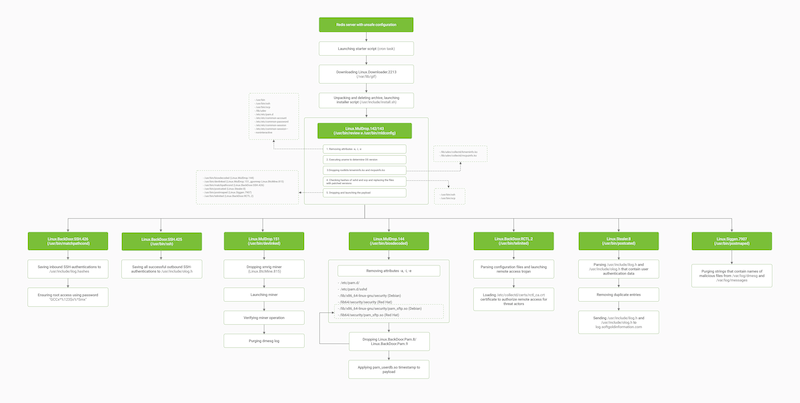
The Skidmap trojan first made headlines in 2019. This trojan-miner is specialized and mainly targets enterprise networks since the greatest stealth mining profits can be achieved in the corporate segment. Despite the fact that five years have passed since the trojan’s debut, the principle of its operation remains unchanged: the trojan is installed on a system by exploiting vulnerabilities or through misconfigured software. In the case of our honeypot server, the hackers added tasks to the system scheduler in which a script downloaded the Linux.MulDrop.142 dropper (or its other modification, Linux.MulDrop.143) every 10 minutes. This executable checks the OS kernel version, disables the SELinux security module, and then unpacks the Linux.Rootkit.400 rootkit, the Linux.BtcMine.815 miner, and the Linux.BackDoor.Pam.8/9 and Linux.BackDoor.SSH.425/426 backdoors on the system. The dropper is remarkable in that it is quite large, as it packs about 60 executables for various Linux distributions. In this case, the dropper contained the files for various versions of Debian and Red Hat Enterprise Linux distributions, which are most commonly encountered on servers.
Once installed, the rootkit intercepts a number of system calls, allowing it to generate fake information in response to diagnostic commands entered by an administrator. Intercepted functions include those that report average CPU usage, network activity on a number of ports, and lists of files in directories. The rootkit also checks all kernel modules when they are loaded and prevents those that can detect its presence from running. All this allows it to thoroughly hide all aspects of the miner's cryptocurrency mining activity: computation, sending hashes, and receiving jobs.
The purpose of the four backdoors installed by the dropper as part of this attack is to collect SSH credentials from a compromised machine and send them to the attackers and to create a master password for all accounts on the system. Note that all passwords are additionally encrypted using the Caesar cipher with a 4-letter offset.
To increase their ability to control a compromised system, the attackers install the Linux.BackDoor.RCTL.2 remote access trojan. It allows commands to be sent to the infected machine and data to be exfiltrated via the encrypted connection that the trojan itself initiates, thus bypassing the routing problem.
The xmrig program is installed as a miner that can mine a number of cryptocurrencies, the most famous of which is Monero, which has gained popularity on the darknet due to its complete anonymity at the transaction level. It should be said that detecting a rootkit-covered miner in a cluster of servers is no trivial task. If the diagnostic data are spoofed, the only thing that might indicate a compromise is excessive power consumption and increased heat generation. However, to somewhat mitigate that, attackers can also tweak the miner's settings to find an optimal balance between mining performance and preserving hardware performance, thus drawing less attention to a compromised system.
The evolution of the Skidmap malware family can be seen in the increasing complexity of the attack chain: the launched programs call each other, disable security systems, interfere with a large number of system utilities and services, download rootkits, etc., which makes it much more difficult to respond to such incidents.
Read more about Linux.MulDrop.142
Read more about Linux.MulDrop.143
Read more about Linux.MulDrop.144
Read more about Linux.Rootkit.400