Doctor Web’s annual virus activity review for 2023
May 13, 2024
Compared to the previous year, the number of users requesting to have their files decrypted in 2023 decreased. At the same time, a decrease was also observed in the number of banking trojan detections.
The year 2023 was memorable for the occurrence of a number information security events. In spring, our specialists uncovered Android trojan attacks that were infecting Android TV sets and TV boxes. In summer, Doctor Web’s malware analysts discovered a cryptocurrency-stealing trojan application that was being distributed with some pirated Windows 10 builds. It infiltrated the EFI system partition after infecting the target computers. As early as fall, we detected a spyware-trojan attack on Iranian Android users. These malicious apps were designed to steal victims’ personal data and money. In addition, our company warned users about the spread of malicious plugins for the Openfire messaging server. These plugins exploited one of Openfire’s vulnerabilities and executed attackers’ commands.
In the mobile threat department, the most widespread threats were ad-displaying trojans, malicious spyware apps, and unwanted adware software. At the same time, on Google Play, many new malicious programs were detected, with almost half a billion downloads combined. In addition, more cryptocurrency-stealing trojans were discovered; these targeted both Android and iOS device users.
Doctor Web’s Internet analysts continued identifying phishing web resources. As before, the ones most popular with scammers were fake bank, online store, and oil and gas company websites.
Principal trends of the year
- The widespread distribution of trojans created with the AutoIt scripting language
- The widespread distribution of trojans that display ads
- A decrease in the number of incidents involving encoder ransomware trojans
- The emergence of new banking trojan families
- The emergence of many new threats on Google Play
- Highly active Internet fraudsters
- A predominance of malicious scripts and phishing documents in malicious email traffic
The most notable events of 2023
In May 2023, Doctor Web informed users about the Android.Spy.SpinOk trojan module, which was positioned as a marketing instrument for Android game and app developers but simultaneously possessed spyware functionality. It collected information about files stored on devices and could send them to attackers. It also could substitute and upload the clipboard contents to a remote server and display ads. Our malware analysts found this module in over 100 apps, which had been downloaded more than 421 million times from Google Play. After the corresponding news materials were published, SpinOk’s developer contacted Doctor Web to identify the reasons why this module was classified as malicious. Later, the module was updated to version 2.4.2, and that version no longer had trojan functionality.
In June, our specialists discovered the Trojan.Clipper.231 malicious app, which was designed to steal cryptocurrency. It was plugged into some pirated Windows 10 builds, and, after infecting computers, it would penetrate the EFI system partition. This stealer substituted the crypto-wallet addresses that users had copied into the clipboard with the addresses provided by the fraudsters. At the time of its discovery, threat actors had already managed to steal cryptocurrency in an amount equivalent to about 19,000 USD.
As early as July, Doctor Web uncovered an attack on Windows users involving the Trojan.Fruity.1 modular trojan. With its help threat actors, depending on their goals, could infect computers with different malware. Cybercriminals took measures to increase the odds of their attacks being successful. For example, Trojan.Fruity.1 was distributed with specially crafted installers of popular software that potential victims downloaded from malicious websites. At the same time, thanks to the trojan’s modular architecture, the process of infecting target systems was multi-stage. Moreover, harmless apps were used to launch the Trojan.Fruity.1 components, and once a target system was infected, an attempt was made to bypass the anti-virus protection.
At the beginning of September, our company published a study of the Android.Pandora.2 backdoor, which was mainly attacking Hispanic users. Various modifications of this trojan infect Smart TV sets and TV boxes. They end up there through compromised firmware versions and when users install trojanized versions of software for viewing pirated video content online. Mass cases of attacks involving Android.Pandora.2 were detected in March 2023. The first modifications of this trojan app were added to the Dr.Web virus database back in July 2017.
A bit later, we informed users about trojans from the Android.Spy.Lydia family, whose primary target was Iranian Android users. These malicious programs provided attackers with remote access to infected devices, had spyware functionality, and were used to steal personal information and money.
And in late September, Doctor Web alerted users to the spread of malicious JSP.BackDoor.8 plugins for the Openfire messaging server. These plugins exploited this product’s CVE-2023-32315 vulnerability, which allowed hackers to gain access to the file system of the infected servers and to use them as part of a botnet. Doctor Web’s specialists discovered these trojan plugins while investigating an encoder trojan attack on the infrastructure of one of our company’s clients. It was namely one such plugin that facilitated a successful encoder attack on a server that had the vulnerable Openfire software installed on it. JSP.BackDoor.8 trojan plugins, backdoors written in the Java programming language, facilitate the execution of a number of commands that come as GET and POST requests sent by attackers. Threat actors can also use them to collect information about a compromised server, including information about network connections, the IP address, users, and the system kernel version.
The malware landscape
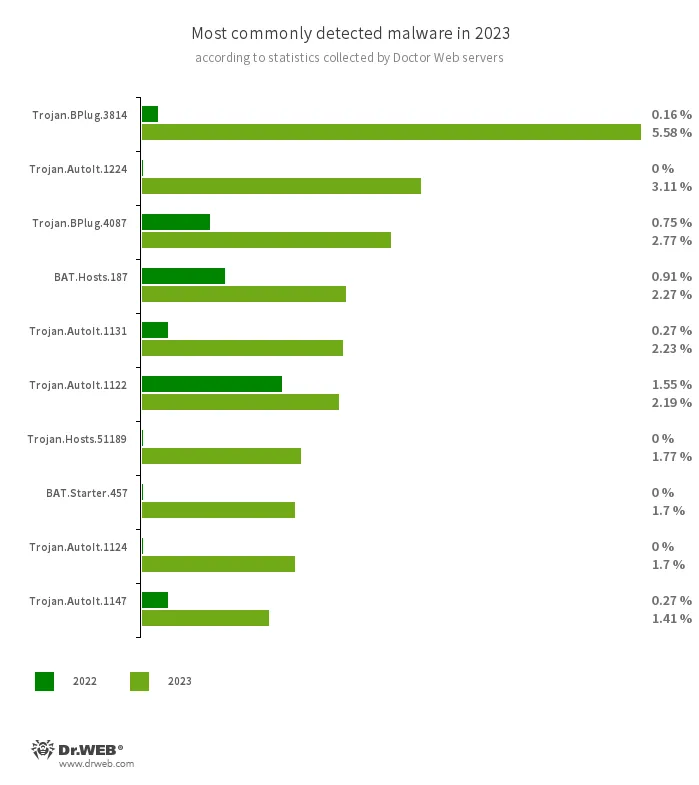
An analysis of Dr.Web 2023 detection statistics revealed a 12.27% increase in the total number of threats detected, compared to 2022. At the same time, the number of unique threats increased by 21.70%. The most active were trojans that are distributed with other malware in order to make the latter more difficult to detect. In addition, users often encountered adware trojans and various malicious scripts.
- Trojan.BPlug.3814
- Trojan.BPlug.4087
- The detection name for malicious components of the WinSafe browser extension. These components are JavaScript files that display intrusive ads in browsers.
- Trojan.AutoIt.1224
- Trojan.AutoIt.1131
- Trojan.AutoIt.1124
- Trojan.AutoIt.1122
- Trojan.AutoIt.1147
- The detection name for packed versions of the Trojan.AutoIt.289 malicious app that are written in the AutoIt scripting language. This trojan is distributed as part of a group of several malicious applications, including a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs various malicious actions that make it difficult for the main payload to be detected.
- BAT.Hosts.187
- A malicious script written in the Windows command interpreter language. It modifies the hosts file of systems by adding a certain list of domains to it.
- Trojan.Hosts.51189
- A trojan app that changes the contents of the hosts file on computers running Microsoft Windows.
- BAT.Starter.457
- A malicious script written in the Windows command interpreter language. It is designed to launch other malware on target computers.
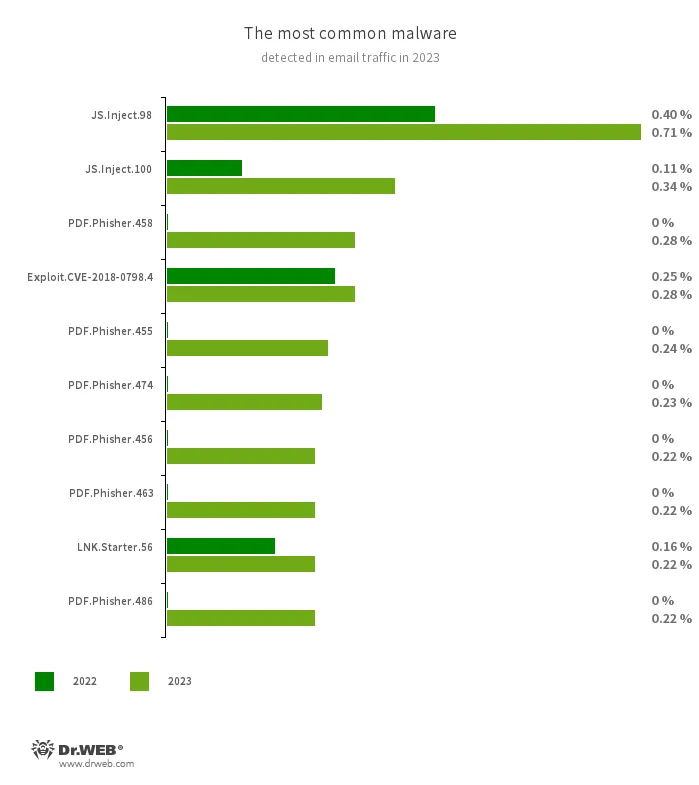
The most widespread threats detected in email traffic in 2023 were malicious scripts and phishing documents that often come as fraudulent login forms. Such documents imitate the authorization process on popular websites and send the data provided by victims to scammers. Malicious programs that exploit vulnerabilities in Microsoft Office documents were also being widely distributed once again.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- PDF.Phisher.458
- PDF.Phisher.455
- PDF.Phisher.474
- PDF.Phisher.456
- PDF.Phisher.486
- PDF.Phisher.463
- These are PDF documents used in phishing newsletters.
- Exploit.CVE-2018-0798.4
- An exploit designed to take advantage of Microsoft Office software vulnerabilities so that an attacker can run arbitrary code.
- LNK.Starter.56
- The detection name for a shortcut that is crafted in a specific way. This shortcut is distributed through removable media, like USB flash drives. To mislead users and conceal its activities, it has a default icon of a disk. When launched, it executes malicious VBS scripts from a hidden directory located on the same drive as the shortcut itself.
Encryption ransomware
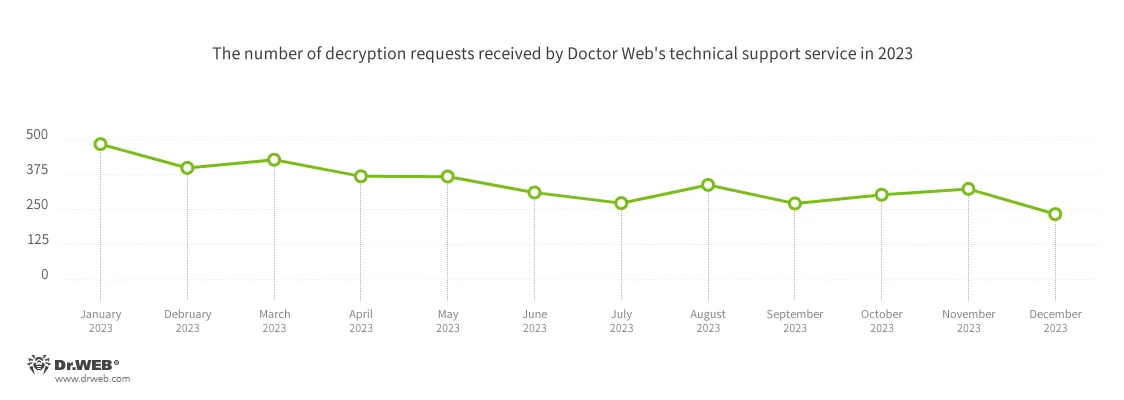
Compared with 2022, in 2023, Doctor Web’s virus laboratory registered 28.84% fewer requests to decrypt files affected by encryption trojans. The dynamics of when those requests were registered is shown in the graph below:
The most common encoders of 2023:
- Trojan.Encoder.26996 (21.35% of user requests)
- A trojan encoder known as STOP Ransomware. It attempts to obtain a private key from a server. If unsuccessful, it uses the hardcoded one. It is one of the few encoders that encrypts user data with the Salsa20 stream cipher.
- Trojan.Encoder.3953 (18.87% of user requests)
- An encoder trojan that has several versions and modifications. It uses the AES-256 algorithm in CBS mode to encrypt files.
- Trojan.Encoder.35534 (6.00% of user requests)
- An encoder trojan also known as Mimic. It uses the everything.dll library from the legitimate software Everything, which is designed to instantly locate files on Windows computers.
- Trojan.Encoder.34027 (2.18% of user requests)
- An encoder trojan also known as TargetCompany or Tohnichi. It uses the AES-128, Curve25519, and ChaCha20 algorithms to encrypt files.
- Trojan.Encoder.35209 (2.01% of user requests)
- An encoder trojan also known as Conti (Trojan.Encoder.33413 is one if its other variants). It uses the AES-256 algorithm to encrypt files.
Network fraud
Throughout 2023, Doctor Web’s Internet analysts observed a great deal of fraudulent activity and detected a large number of phishing websites. The theme of finance was the most popular among threat actors as up to 60% of the unwanted sites discovered were copycats of Internet resources belonging to genuine credit organizations. Commonly encountered among these were fake personal account login pages for accessing online banking systems and pages with bogus surveys. Using such fakes, cybercriminals would try to get hold of users’ personal data and the login information needed to access their victims’ online bank accounts.
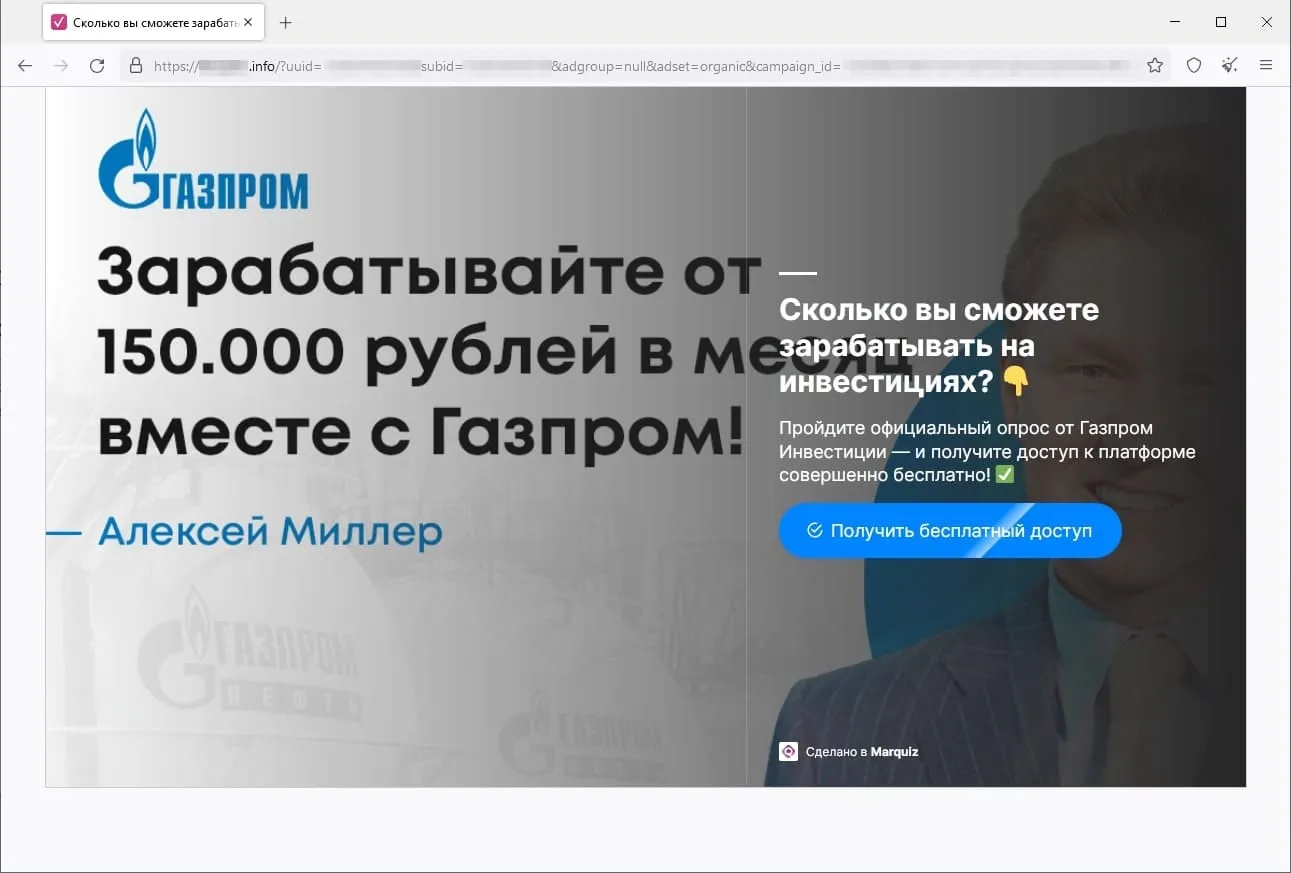
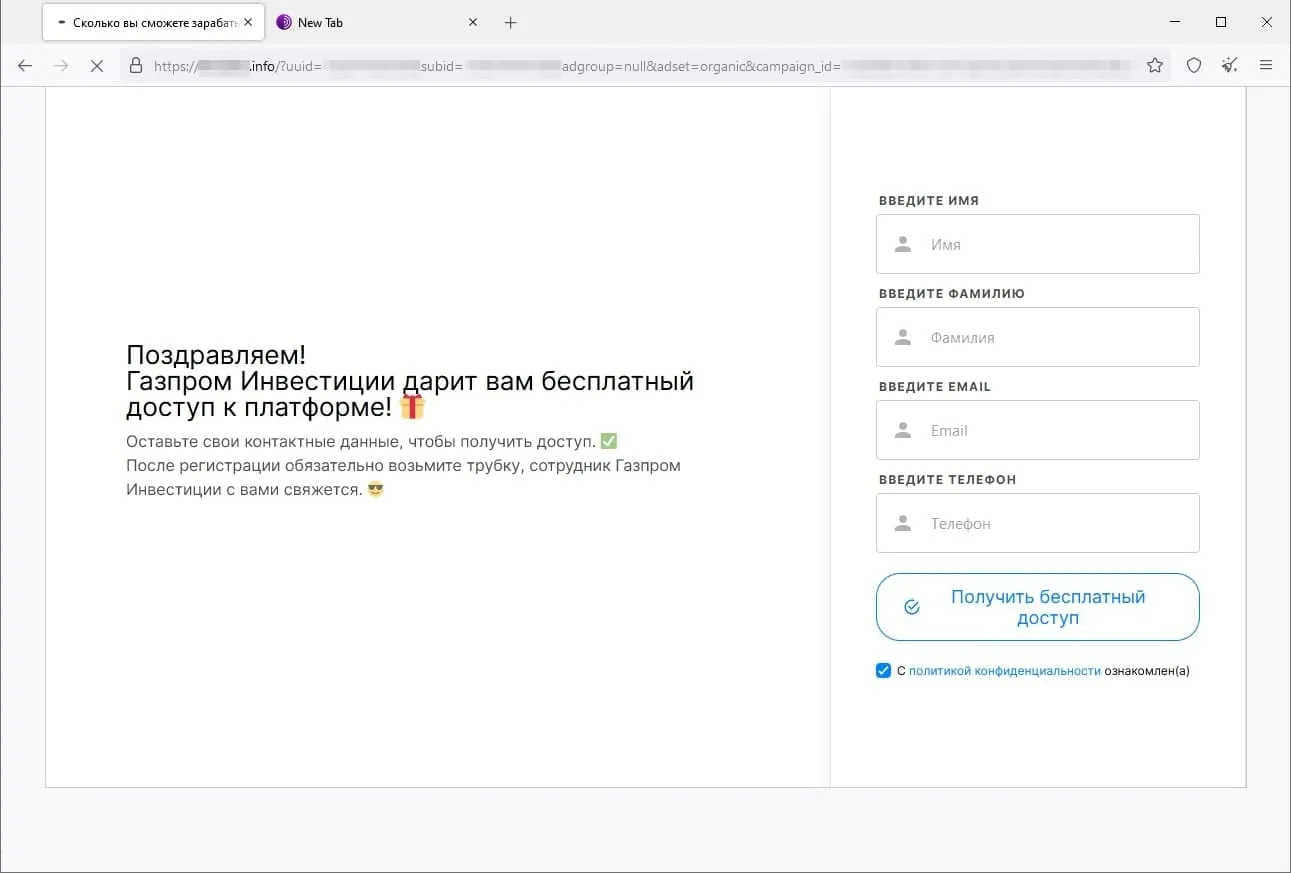
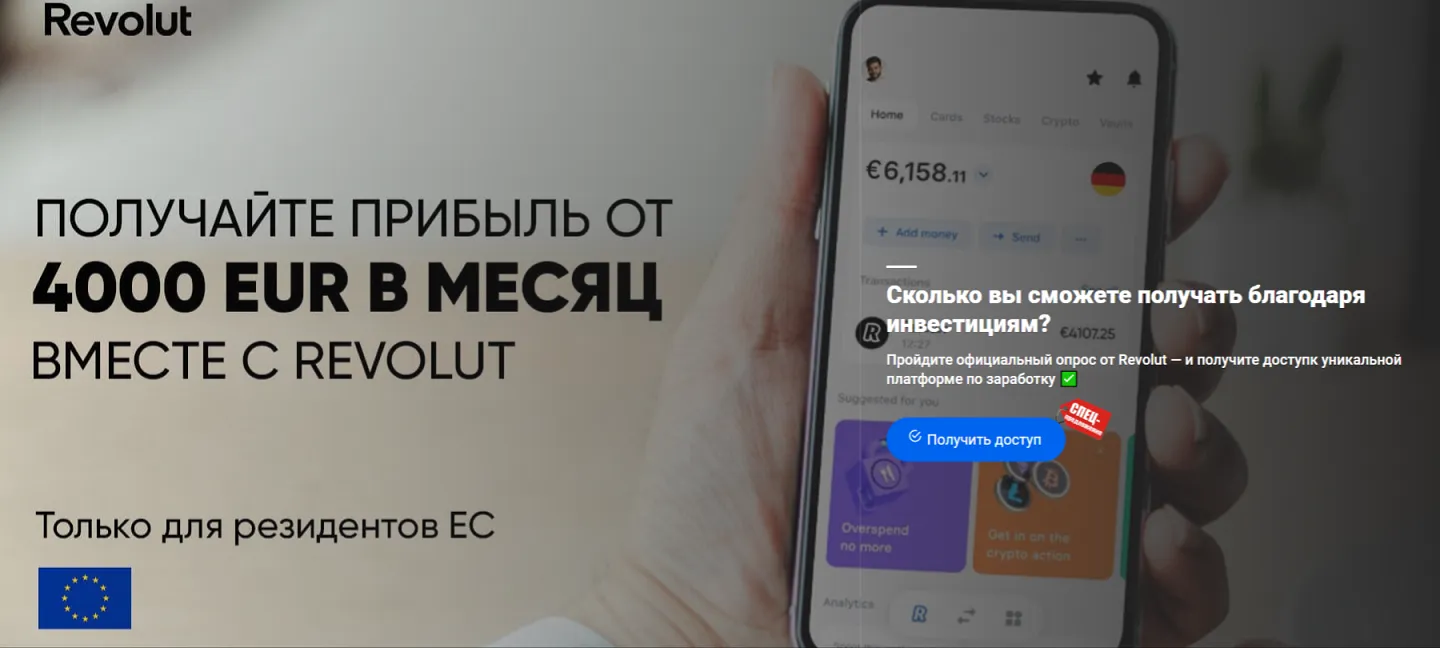
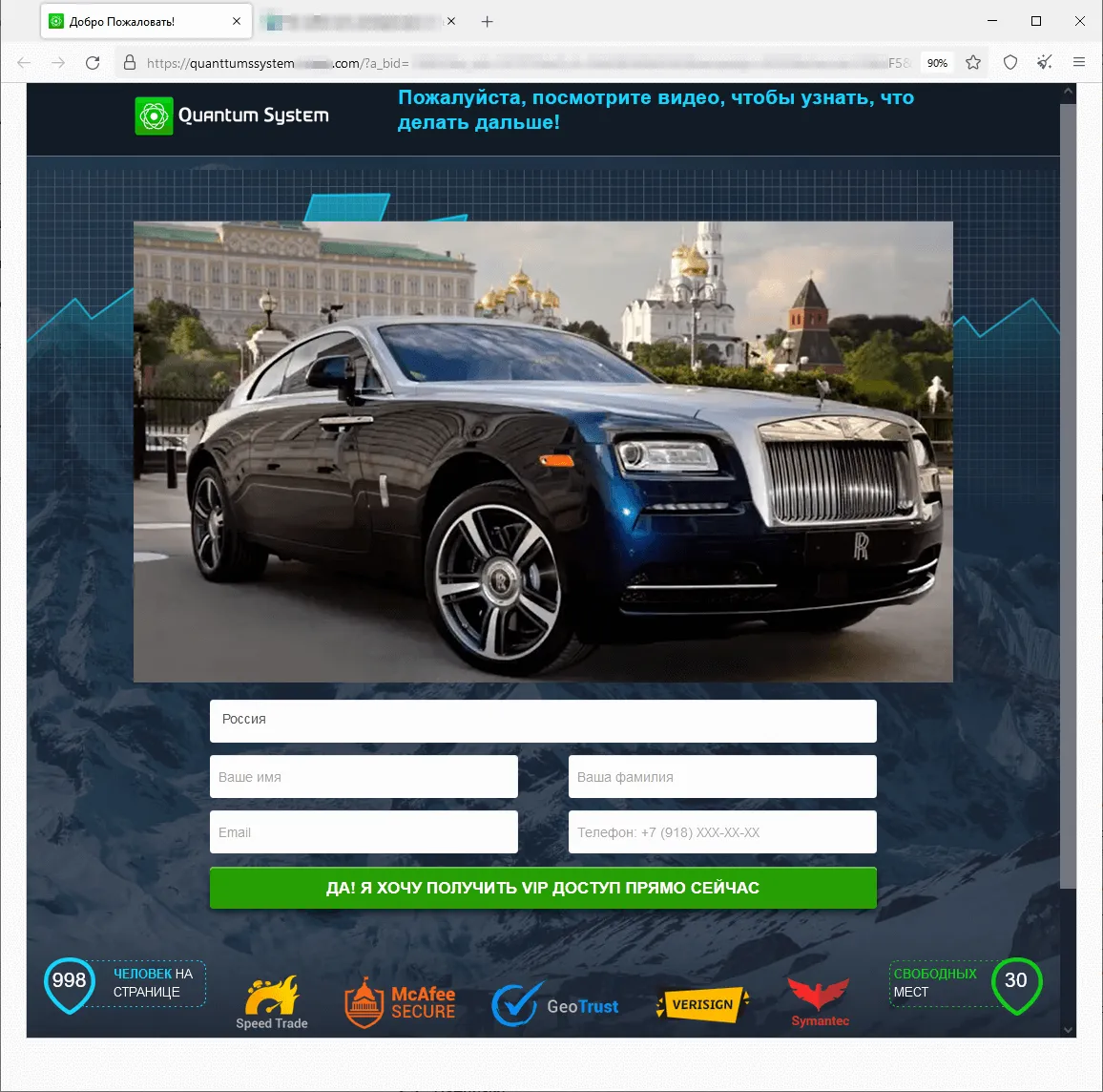
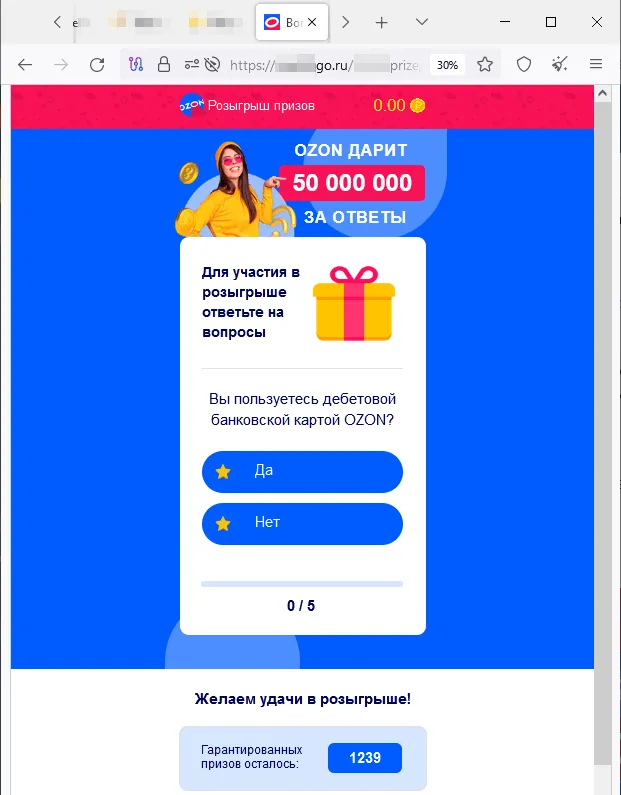
Moreover, threat actors continued to lure potential victims to fraudulent websites that offered them the chance to improve their financial situation. In some cases, they were offered the opportunity to make money via special investing services that supposedly were related to large oil and gas companies. Sometimes they were offered the chance to access some allegedly automated trading systems with “guaranteed” high profits. Also popular once again were variants that involved “receiving” social payments from the government. The phishing scheme in all these websites boils down to users needing to provide their personal information so that some account can be registered for them once they answer several simple questions. And for those variants where they can supposedly receive some payments, they must also pay a “commission” or a “fee” to have what is in reality non-existent money transferred to their bank account.
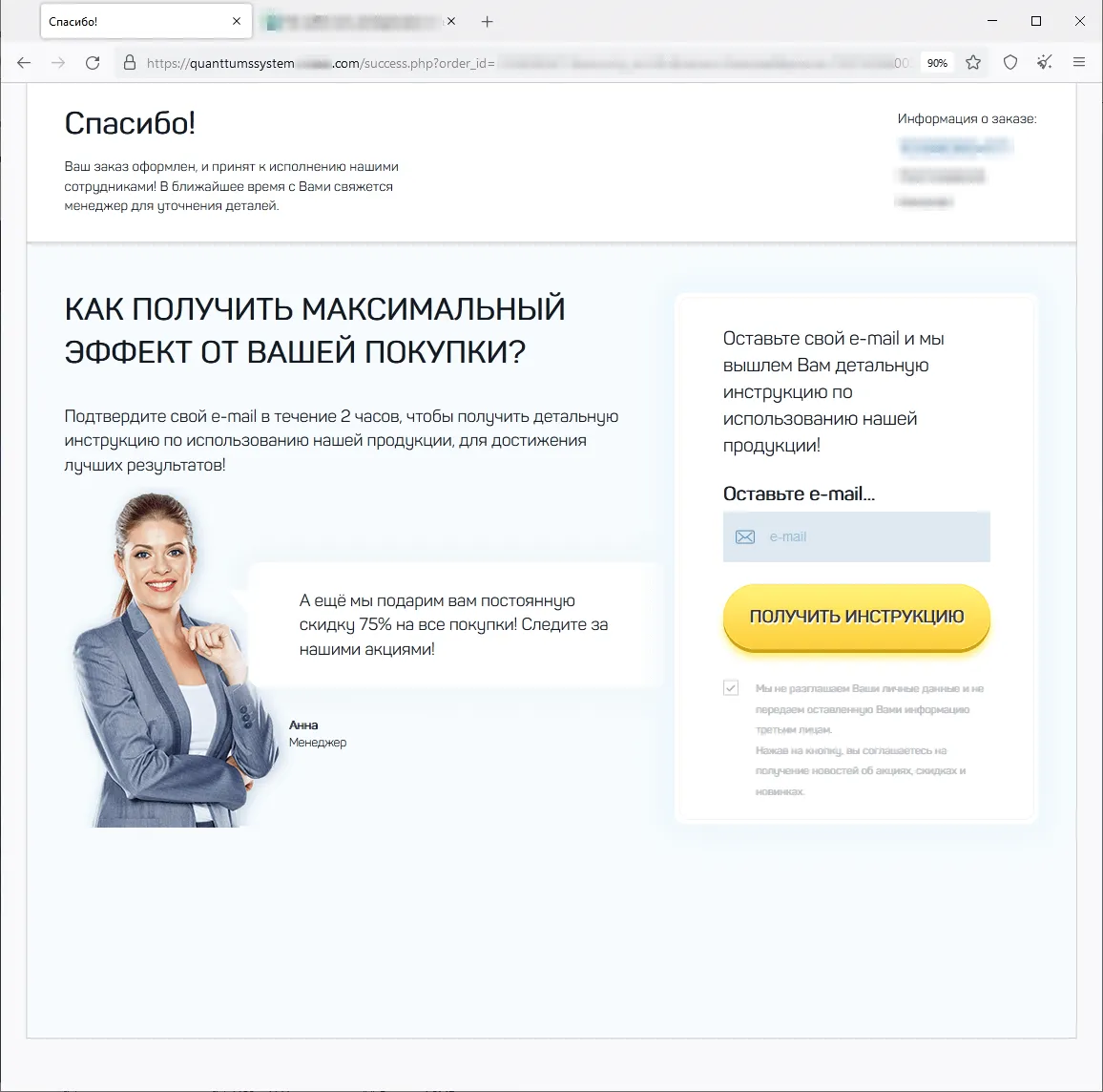
The screenshots below depict examples of the finance-themed fraudulent sites. In the first case, users, allegedly on behalf of large Russian oil and gas company, are offered the opportunity to access an “investing platform”. In the second one, potential victims are lured into accessing an investing service that supposedly has links to a European bank. And in the third case, the visitor of the fraudulent site is offered the chance to access a pseudo-trading “automated system” that goes by names like Quantum UI, Quantum System, etc.
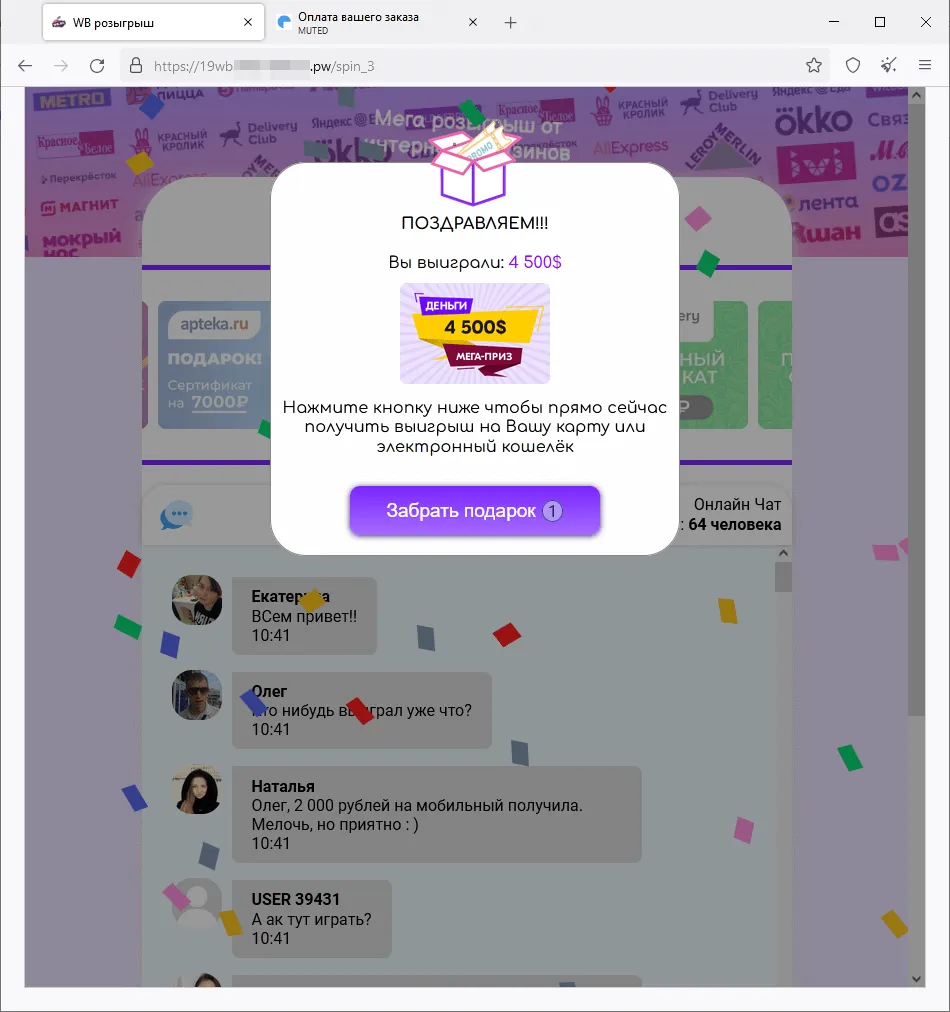
Phishing schemes related to various “promotions”, “bonuses”, and “gifts” were once again popular among fraudsters. Scammers lured potential victims to fake websites of online stores, retailers, online ticket sales offices, etc., where users allegedly could participate in prize draws, receive a gift or bonuses, or buy some product at a better price. Malicious actors would mislead users in an effort to steal their money and bank card information. Examples of such fraudulent websites are shown in the screenshots below.
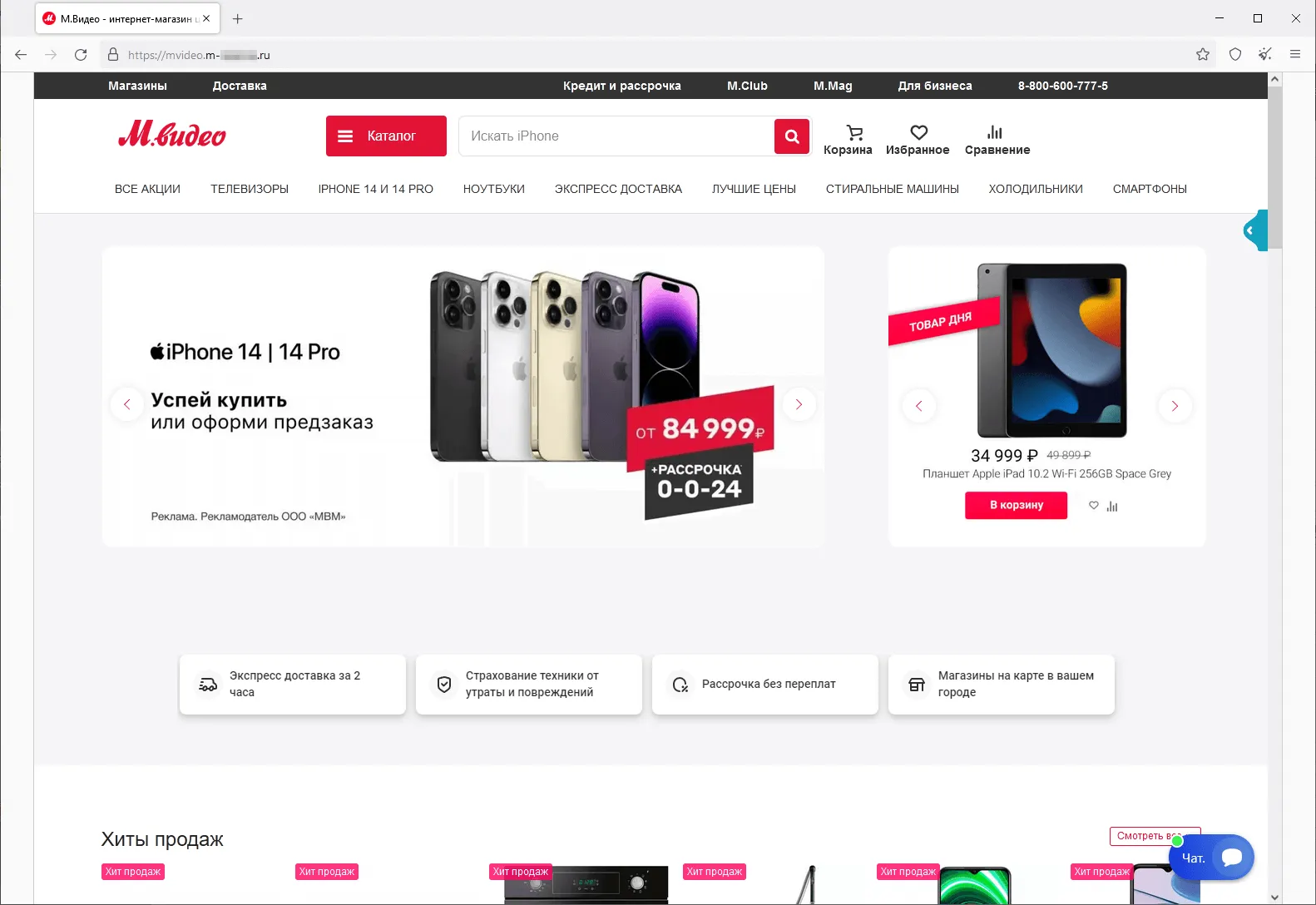
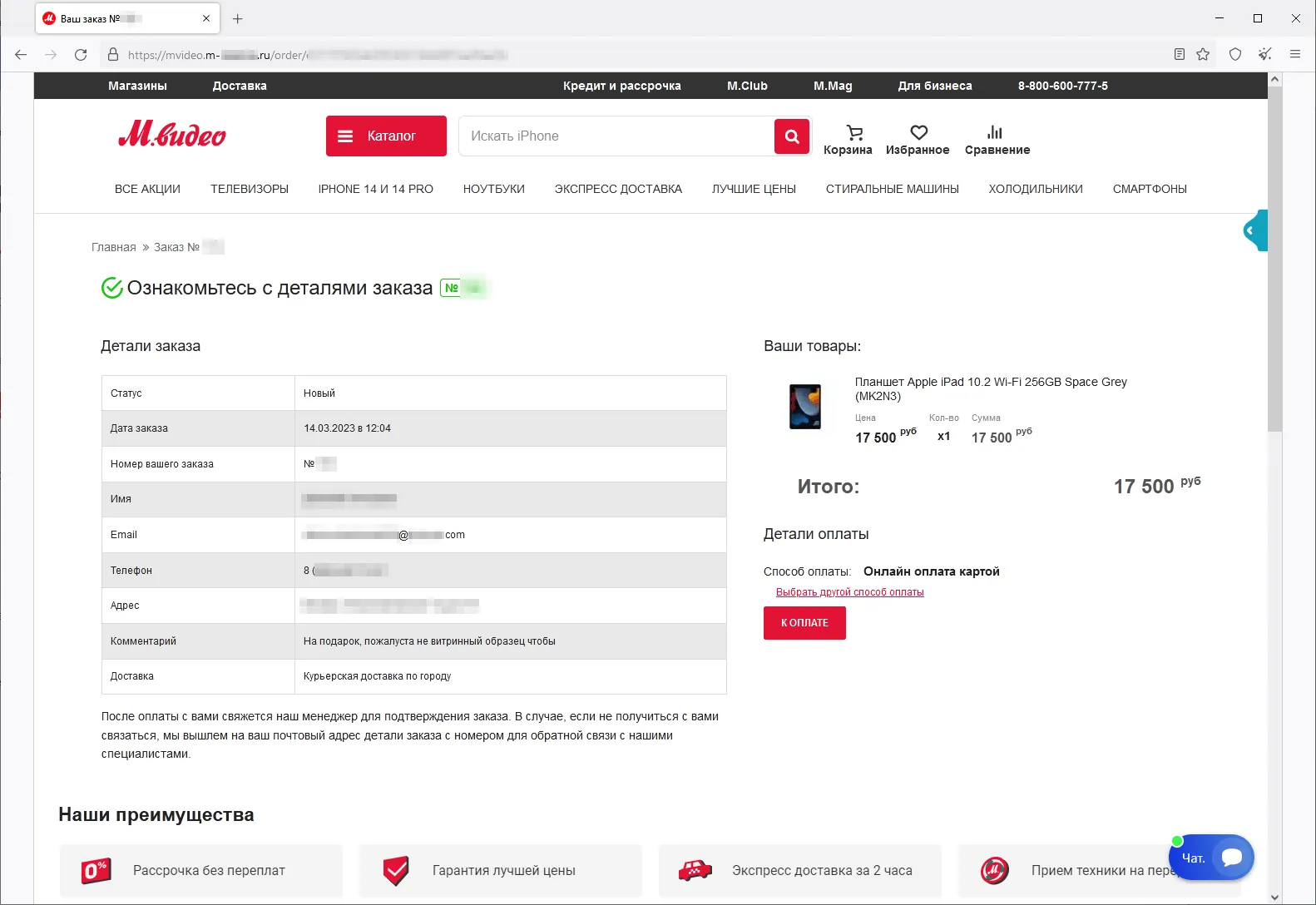
A fake site that imitates the appearance of the real website of one of Russia’s household appliance and electronics stores:
Scammers offer potential victims a commodity for purchase at a discount and ask them to pay with a bank card or by transferring the money via an online bank.
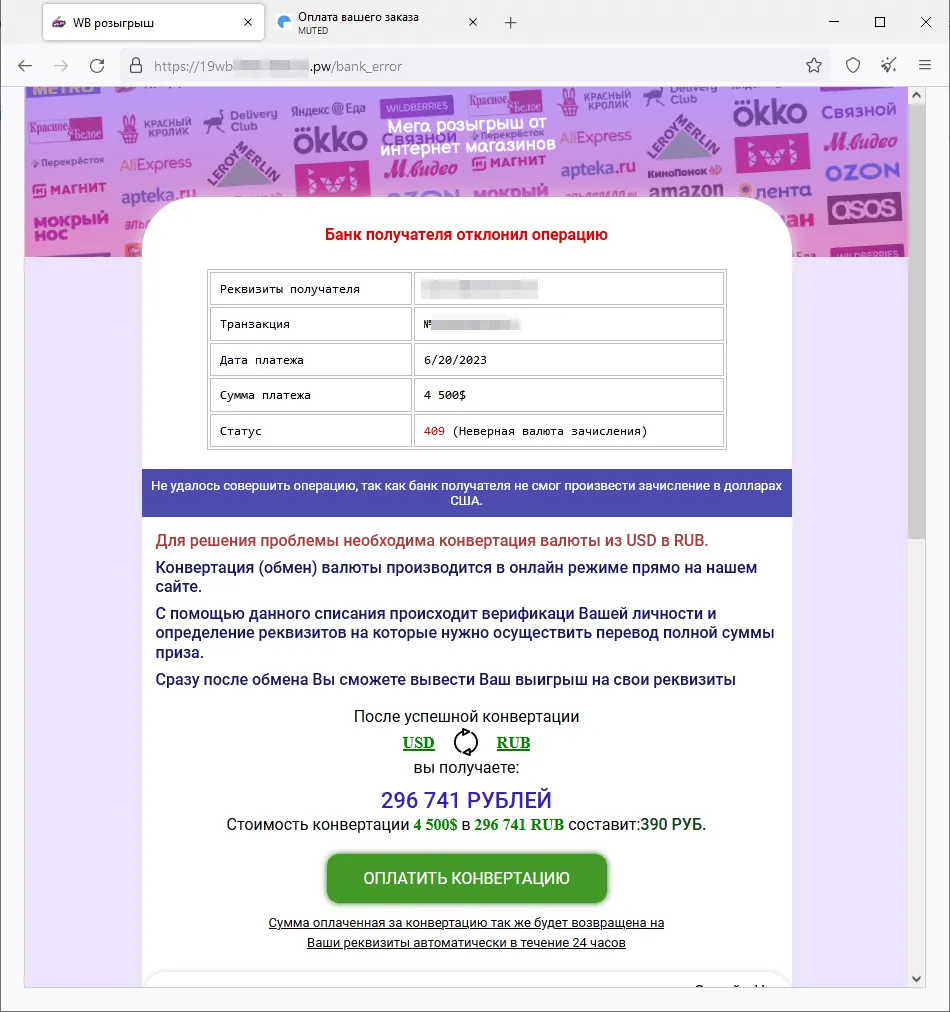
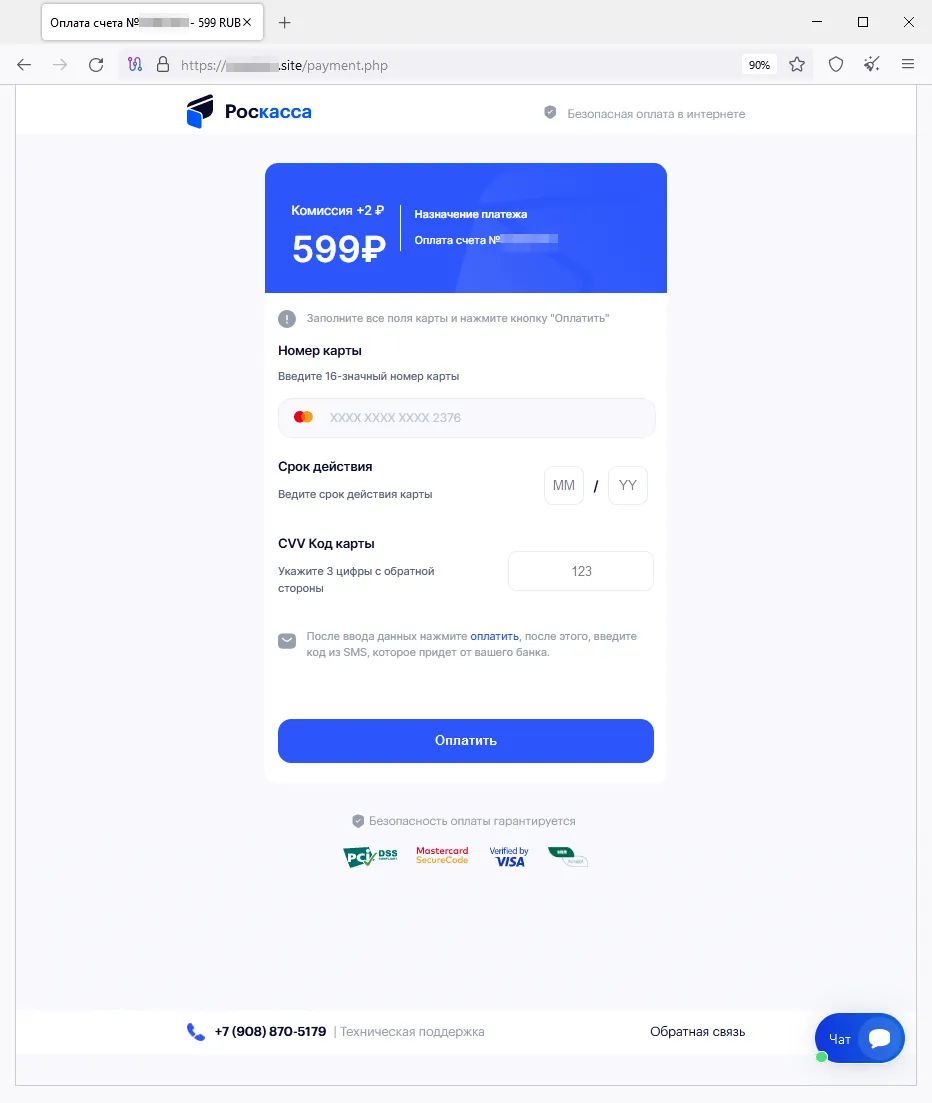
A fraudulent website where visitors are offered, supposedly on behalf of several online stores, the chance to participate in a “prize draw”:
After the potential victim “wins” a large money prize, they allegedly must pay a currency-conversion commission in order to “receive” it.
A bogus Internet resource designed in the style of the official website of one of Russia’s online stores:
To participate in the money prize “draw”, the user is asked to answer several questions. After the website simulates the draw, the victim allegedly wins but must pay a “commission” to receive the winnings.
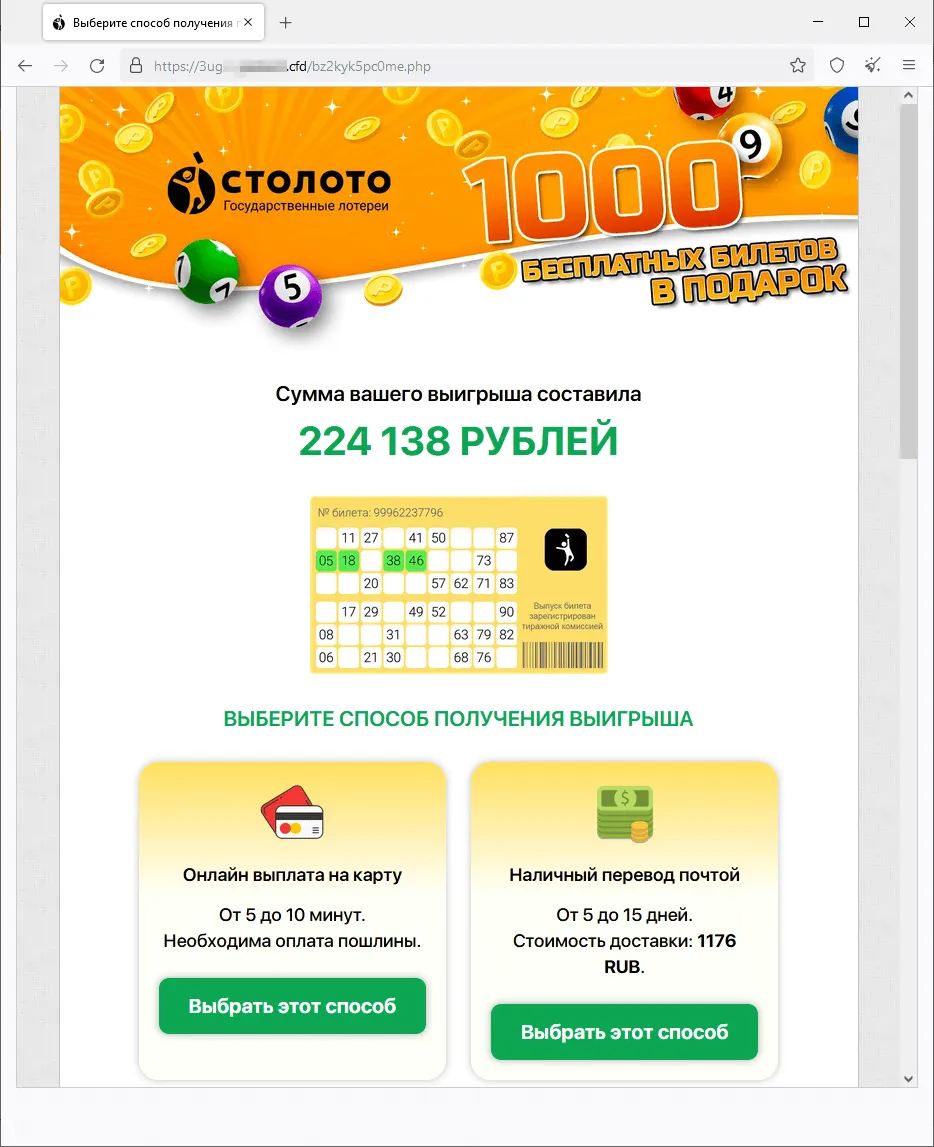
A phishing website that offers visitors “free” lottery tickets:
The user that allegedly won the lottery must pay a “commission” to receive their winnings.
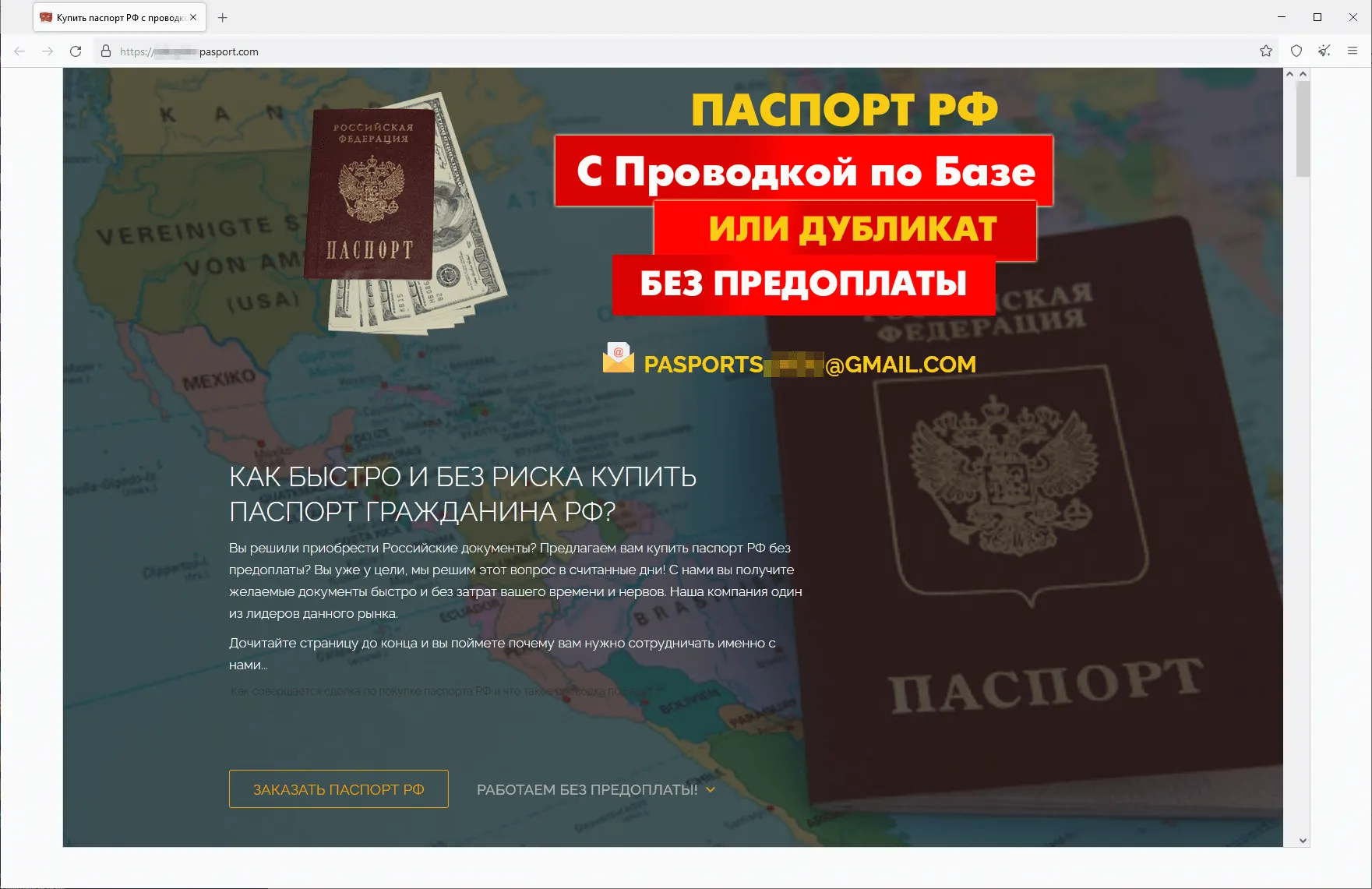
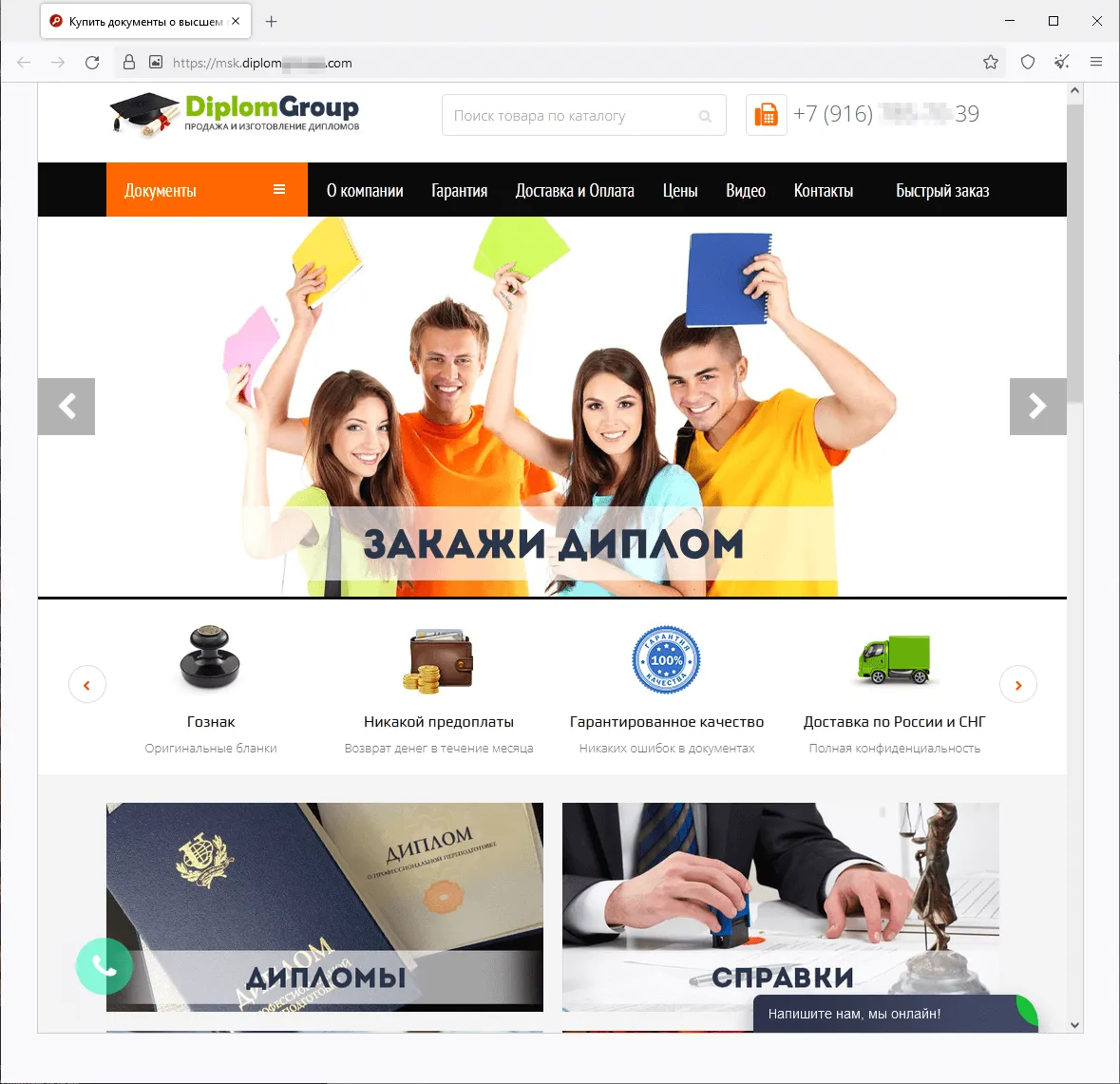
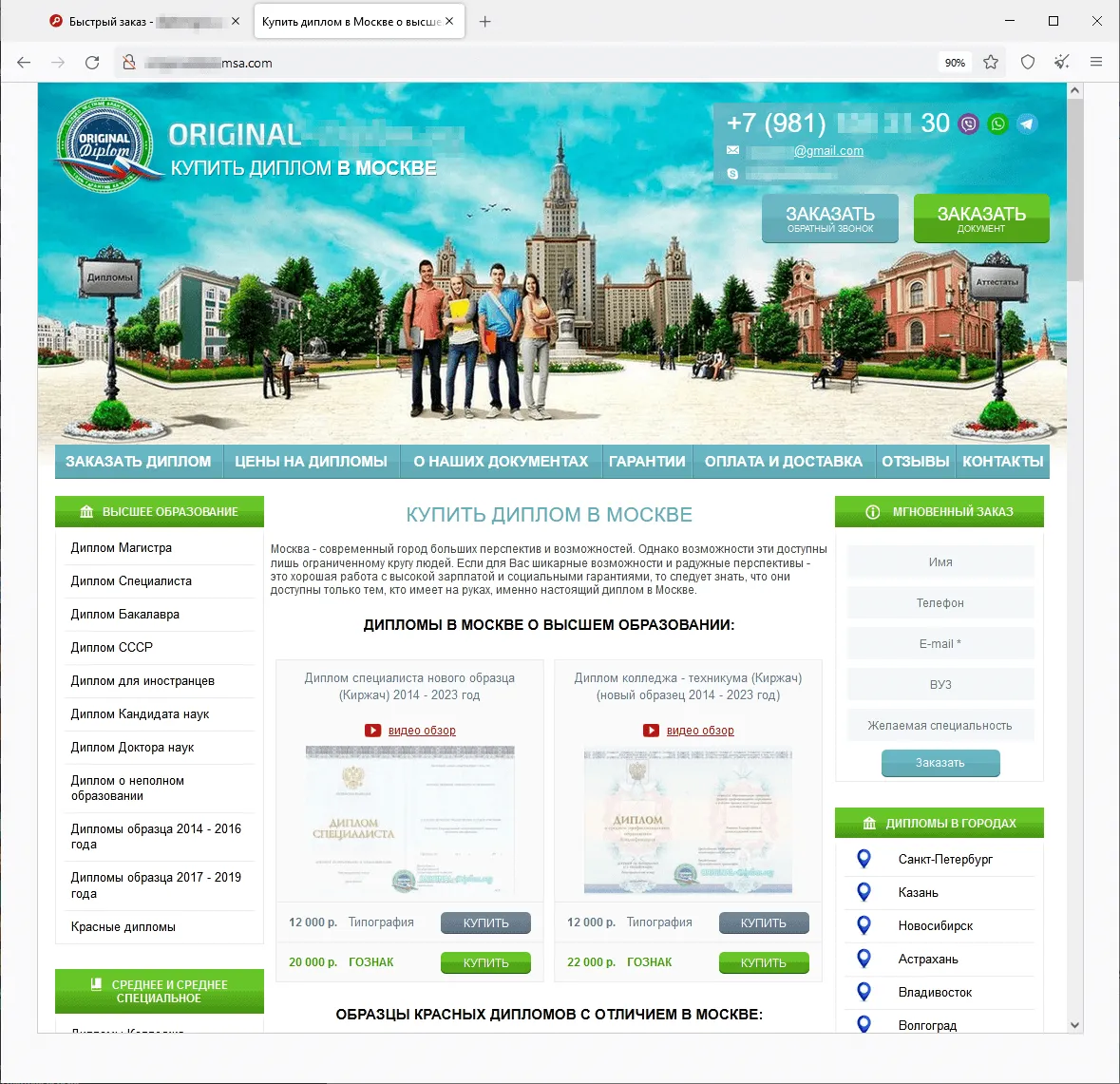
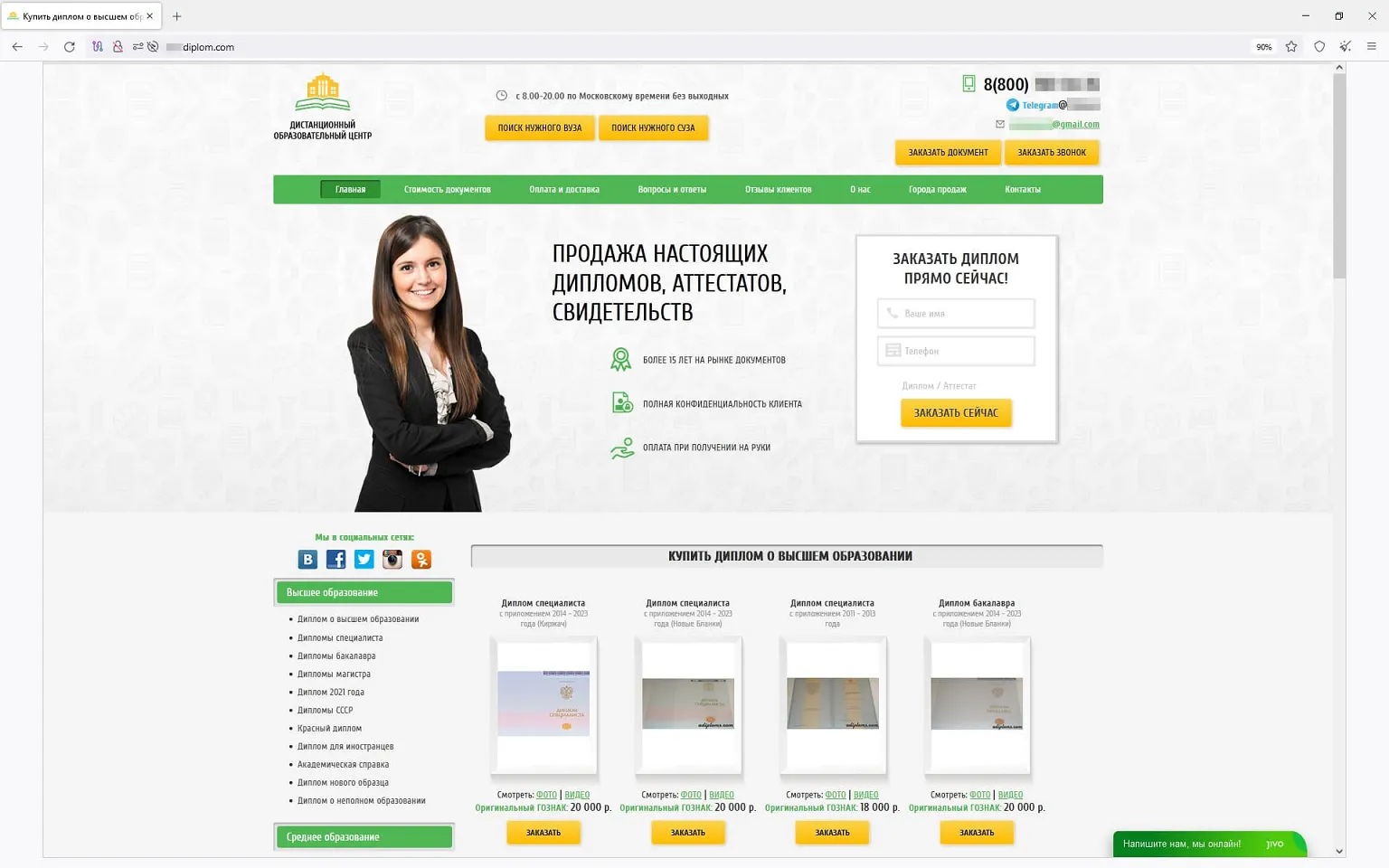
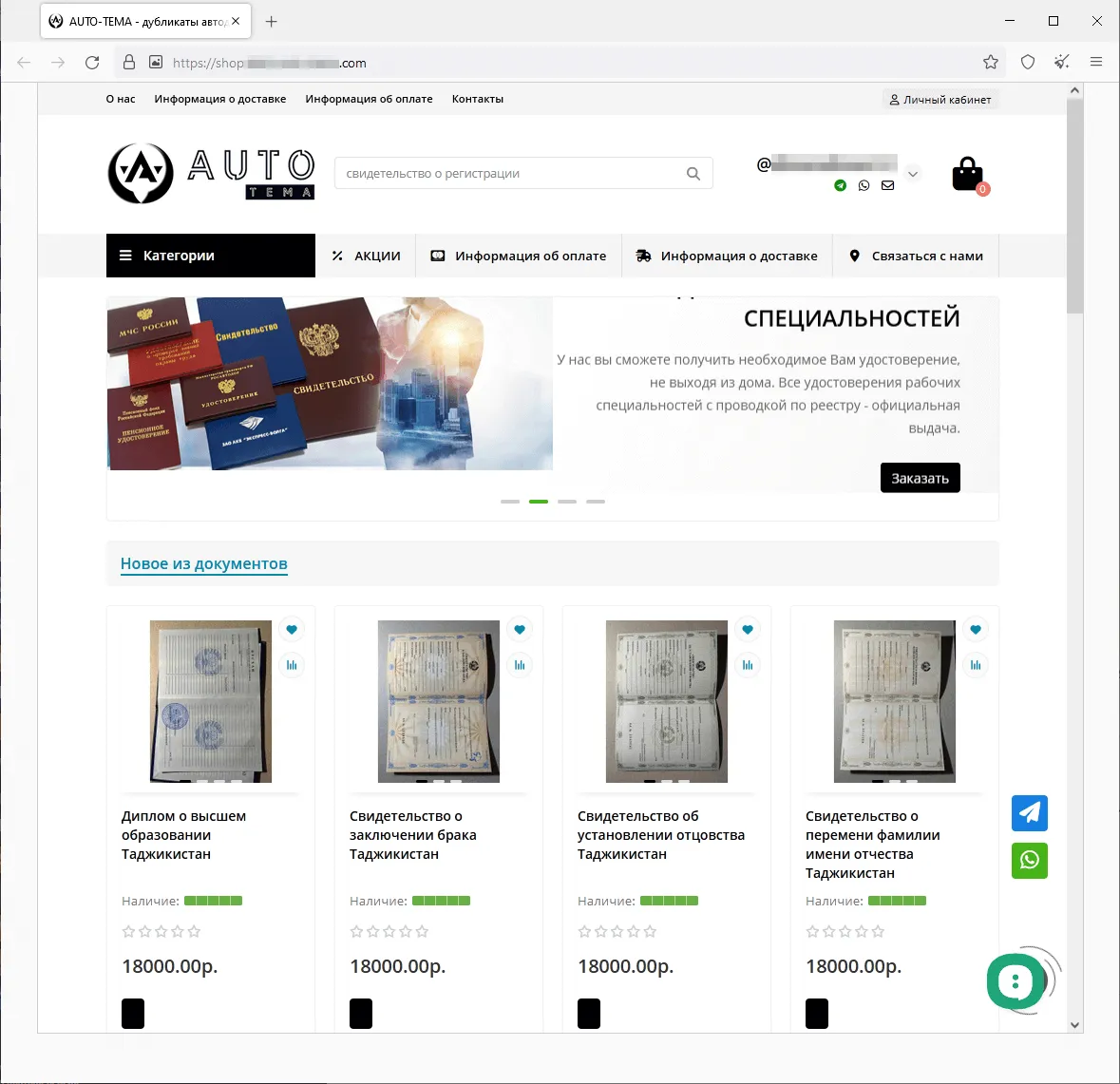
In summer 2023, we observed an increase in the activity of fraudsters using different websites to promote supposedly legal services—services that “help” people recover their lost state-recognized documents of Russia, the CIS (the Commonwealth of Independent States), and other countries, or buy completely new ones. The assortment of items available on such sites included higher education diplomas, driver’s licenses, all sorts of certificates, and so on. Users who decided to use such dubious services not only risked losing their money when purchasing a non-existent service but also could fall victim to a personal data leak. Moreover, if they actually were to buy such a fake document, they would be breaking the law and could potentially get into trouble with law enforcement agencies. Below are screenshots that show examples of sites that offered these dubious services.
A website that offers the opportunity to purchase the passport of a citizen of the Russian Federation:
Sites that offer for sale higher education diplomas, school qualification papers, certificates, driver’s licenses, and other documents:
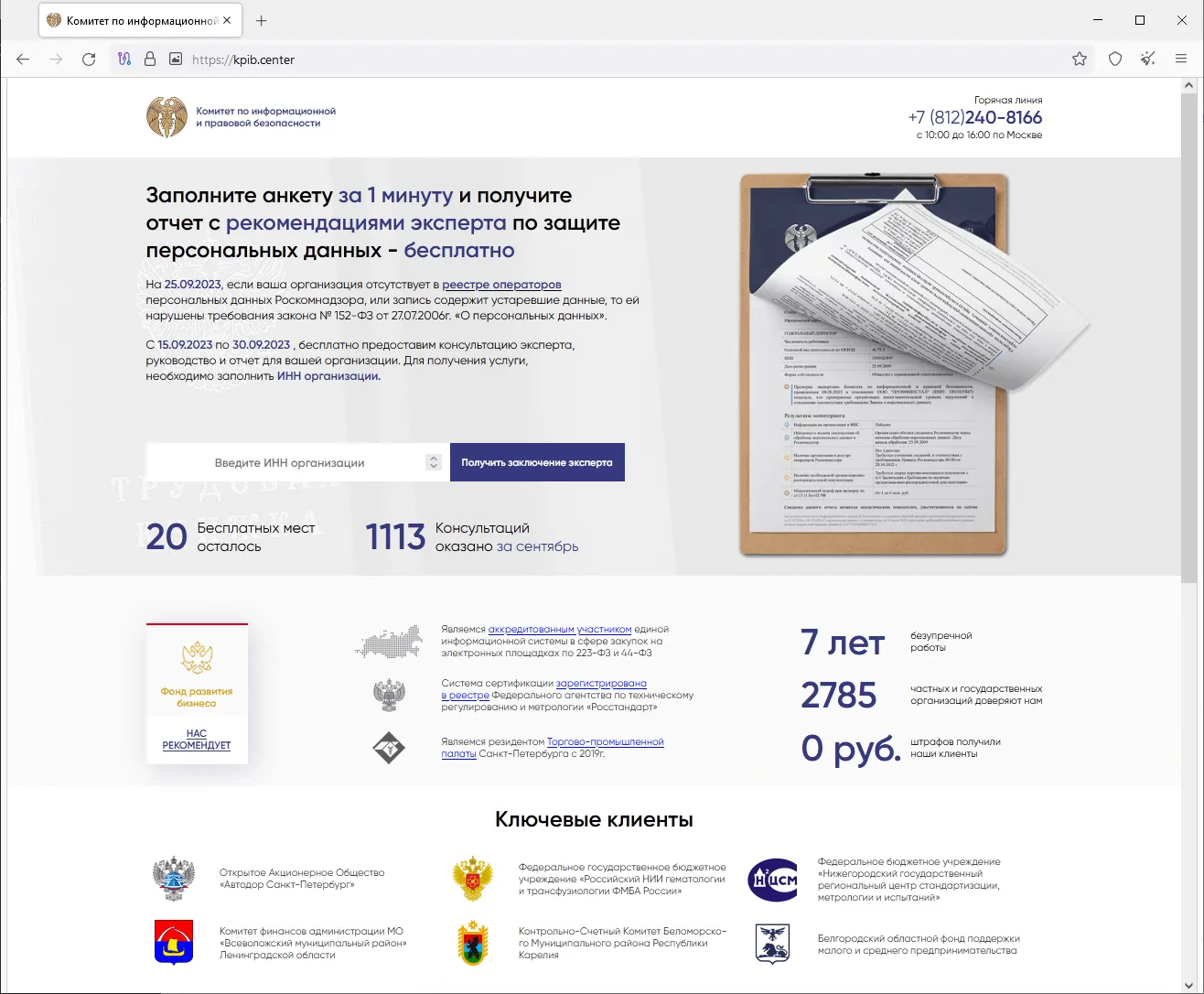
Already in the fall, Doctor Web’s Internet analysts detected a phishing campaign in which cybercriminals were sending out emails masquerading as messages from tax authorities. These messages contained a link to a website where users were offered the opportunity to verify whether companies and organizations were complying with the requirements of the Russian Federation’s law on personal data. For this, users had to take a short survey and then provide personal data “to receive the results and get a free expert consultation”. When users answered the questions, the website requested their phone number and an email address.
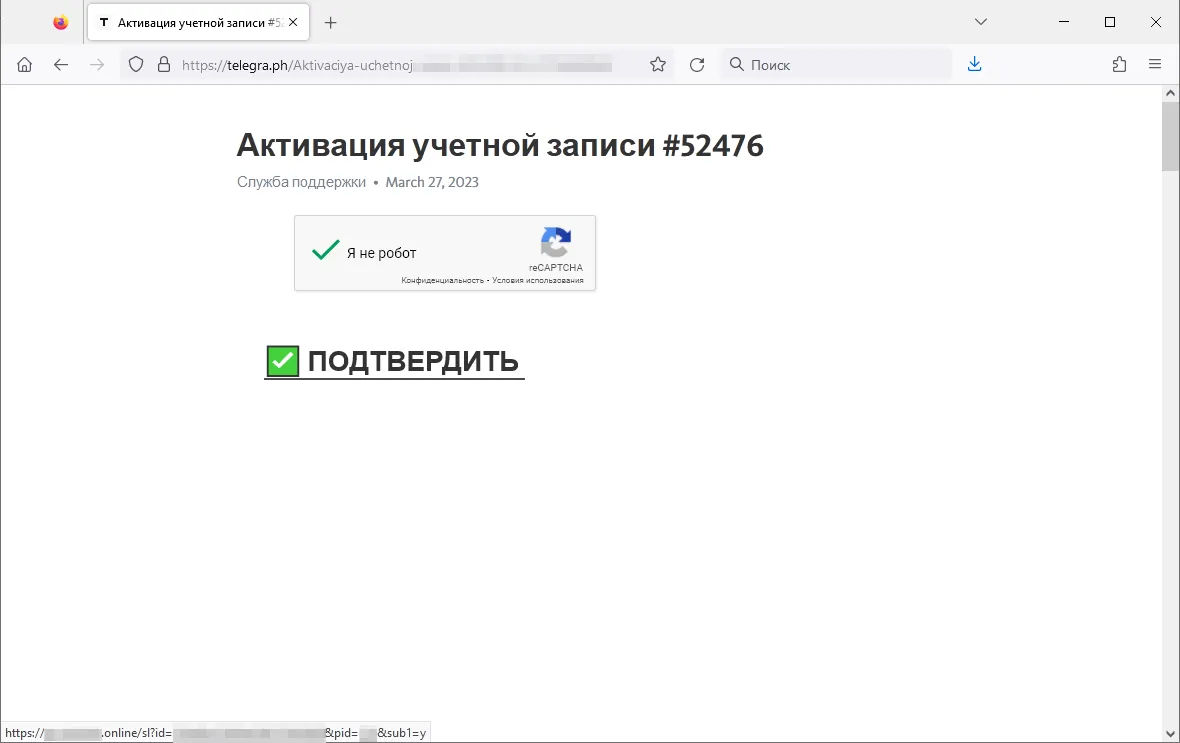
In addition, last year our experts observed an increase in the number of cases of fraudsters using the Telegraph blog platform for fraudulent purposes. Threat actors publish phishing posts on this platform that contain links to various unwanted websites. At the same time, links to these fraudulent posts are first converted through link-shortening services.
An example of such a phishing publication is shown in the screenshot below. The user is asked to activate an account, but when they click on the element containing the text “CONFIRM”, they are redirected to a phishing site.
Mobile devices
According to Dr.Web for Android detection statistics, the most widespread Android malicious apps in 2023 were the Android.HiddenAds ad-displaying trojans, which accounted for 31.61% of all detected malware. And the most active threat was Android.HiddenAds.3697, which was detected in 10.72% of cases. Second place, with a share of 28.22%, was held by Android.Spy trojans with spyware capabilities. Among these, the Android.Spy.5106 trojan was most commonly detected (20.80% of cases). With 10.06% of detections, Android.MobiDash advertizing trojans ranked third.
The most common unwanted program was Program.FakeMoney.7 (29.90% of all unwanted software detections). It offered users the opportunity to make money by completing various tasks but never did actually pay out any real rewards. Accounting for 19.42% of detections, the second most widespread program was Program.FakeAntiVirus.1. It simulated anti-virus behavior, detected nonexistent threats and offered users the opportunity to buy its full version to “fix” problems. In third place, with a share of 9.46%, were programs that were modified via the CloudInject cloud service. Detected by Dr.Web anti-virus as Program.CloudInject.1, such programs have dangerous permissions and obfuscated code added to them, and the purpose of the latter cannot be controlled.
As in the year before, Tool.SilentInstaller utilities again occupied the leading position in the number of potentially dangerous software detections (48.89% of all riskware observed on protected devices). These instruments allow Android programs to launch without being installed and can be used by cybercriminals to run malware. With a share of 14.02%, the second most common riskware programs were Tool.LuckyPatcher tools; these allow Android apps to be modified by adding scripts to them that are loaded from the Internet. In third place, with a share of 10.14%, were programs protected with the Tool.ApkProtector software packer.
The most widespread adware family in 2023 was Adware.Adpush, which accounted for 35.82% of all unwanted adware software detections. With a share of 9.58%, the Adware.MagicPush family was the second most common. Third place, with a share of 8.59%, was held by the Adware.Airpush family of adware modules.
On Google Play throughout 2023, Doctor Web’s malware analysts discovered over 440 malicious programs that had a combined total of at least 428,000,000 downloads. Among the threats detected were over 100 apps containing the built-in Android.Spy.SpinOk trojan module, which implemented spyware functionality. In addition, our virus laboratory detected more than 300 trojans from the Android.FakeApp family—cybercriminals used them to execute various fraudulent schemes. Our specialists also found Android.Proxy.4gproxy trojans that turned infected devices into proxy servers and covertly transmitted third-party traffic through them. Ad-displaying trojans from the Android.HiddenAds family, the spyware trojan Android.Spy.1092.origin, and the Android.CoinSteal.105 cryptocurrency stealer were also among the threats discovered. There were also more trojans from the Android.Subscription family—such trojans subscribe users to paid services. But these were not the only threats with such functionality, as malicious actors again distributed the Android.Joker and Android.Harly trojans.
Compared to 2022, 2023 saw an almost 50% decrease in the number of banking trojans detected on Android. Nevertheless, the geography of their attacks again covered many countries. Moreover, while already known banking trojans were still active, Doctor Web’s malware analysts detected the emergence of new families, many of which were targeting Russian and Iranian users.
At the same time, our experts detected more malicious websites that distribute fake crypto wallets for Android and iOS devices. Such malicious software is used to steal cryptocurrency.
To find out more about the security-threat landscape for mobile devices in 2023, read our special overview.
Prospects and possible trends
The widespread distribution of adware trojans in 2023 showed that making illegal profits is still a priority for cybercriminals. This is confirmed by their active use of trojans created with the AutoIt scripting language. These are used with other malware to make it difficult for the main payload to be detected. Such malware includes trojan miners. So, it is likely that threats that help malicious actors make more money at the expense of their victims will remain in the arsenal of attackers in 2024.
With this being said, despite the decrease in the total number of attacks using banking trojans, the development of this type of threat continues, as evidenced by the emergence of new families. This trend will most likely continue.
Internet fraud will still be a relevant threat. As technology evolves, malicious actors will not only use proven fraudulent schemes but will also implement more techniques, including ones that use neural networks.
We should also expect more mobile threats to emerge, including those that are distributed via official app stores, such as Google Play. At the same time, it is possible that new malware will emerge that targets not only Android-based devices but others, too—iOS devices in particular.
The attack on Openfire software once again demonstrated the importance of installing updates and keeping programs in use up to date. It is possible that in 2024, cybercriminals will launch new attacks using all kinds of exploits; this includes targeted attacks.