Doctor Web’s review of virus activity on mobile devices in 2023
April 17, 2024
At the same time, fraudsters remained highly active. They used all kinds of malicious apps to execute different fraudulent schemes.
Google Play once again was the object of cybercriminals’ interest. During last year, Doctor Web’s virus laboratory discovered over 400 trojan programs on it, with cumulative downloads of at least 428 million.
In addition, our specialists discovered more trojan programs designed to steal crypto currency, and attackers were once again targeting not only Android device users but also those with iOS devices.
PRINCIPAL TRENDS IN 2023
- An increase in ad-displaying trojan activity
- A decrease in banking trojan activity
- The emergence of new Android banking malware targeting Russian and Iranian users
- The emergence of many new threats on Google Play
- Fraudsters remaining highly active
- The emergence of new trojan apps designed to steal crypto currency from users of Android and iOS-based devices
The most notable events of 2023
In May, on Google Play, Doctor Web uncovered over 100 apps containing the built-in SpinOk module. This module positioned itself as a specialized marketing platform that can be embedded into Android games and programs. This instrument was designed to maintain users’ interest in apps with the help of mini games, a system of tasks, and alleged prizes and reward drawings. However, it had spyware functionality and was, therefore, added to the Dr.Web virus database as Android.Spy.SpinOk. The module collected information on files stored on devices and was able to transfer them to malicious actors. It could also substitute and upload clipboard contents to a remote server as well as display advertising banners, such as those shown in the examples below:
In total, the apps discovered to contain Android.Spy.SpinOk were downloaded more than 421 million times. After contacting our company, SpinOk’s developer made corrections to the module. As a result, the 2.4.2 platform version, current at the time of the fix, no longer had the trojan functionality.
In early September, Doctor Web published a study of the Android.Pandora.2 backdoor, which was primarily targeting Spanish-speaking users. A large number of attacks involving this malware were recorded in March 2023. The first modifications of this trojan had been added to the Dr.Web anti-virus database in June 2017. Android.Pandora.2 and its various modifications infect Android-based Smart TV sets and TV boxes via compromised firmware updates and when users install trojan versions of applications used to view pirated video content online. Below are examples of websites that spread this backdoor:
The trojan creates a botnet of infected devices and upon receiving the attackers’ commands can execute DDoS attacks of various types. It can also perform a number of other malicious actions, like installing its own updates and substituting the original system hosts file. The analysis our specialists carried out showed that when creating this backdoor, its authors borrowed from the authors of Linux.Mirai, taking part of its code and using it as the basis for their trojan. In turn, since 2016, Linux.Mirai has been widely used to infect IoT (the “Internet of things”) devices and to perform DDoS attacks on various websites.
That same month, Doctor Web’s malware analysts reported cases where the Android.Spy.Lydia multi-functional spyware trojan was being distributed; these malicious programs were targeting Iranian users. Members of this family are disguised as an online trading platform, and threat actors can command them to perform a number of malicious actions. For example, they can intercept and send SMS, collect data about phonebook contacts, hijack clipboard contents, load phishing websites, etc. Android.Spy.Lydia trojans can be used in different fraudulent schemes and to steal personal data. Moreover, with their help, malicious actors can steal victims’ money.
At the end of September, our company warned users about the increase in cases of fraud using remote administration software for mobile devices. This allowed threat actors to gain full control over users’ Android devices. Posing as credit organizations’ support staff, cybercriminals informed potential victims about “suspicious activity” occurring with their bank accounts and asked them to download a “bank support app”. In reality, the program in question was a remote desktop access tool, and most often it was the RustDesk Remote Desktop app. After this tool was blocked on Google Play, threat actors began distributing it via fraudulent websites. And in some cases, they modified the program to be more convincing. For this, they replaced the icon and the name with those corresponding to a particular bank. Dr.Web anti-virus detects trojan versions of this program as Android.FakeApp.1426.
At the same time, in 2023, Doctor Web’s specialists continued to identify malicious websites through which cybercriminals were distributing fake crypto-wallet software for Android and iOS devices in order to steal crypto currencies.
Statistics
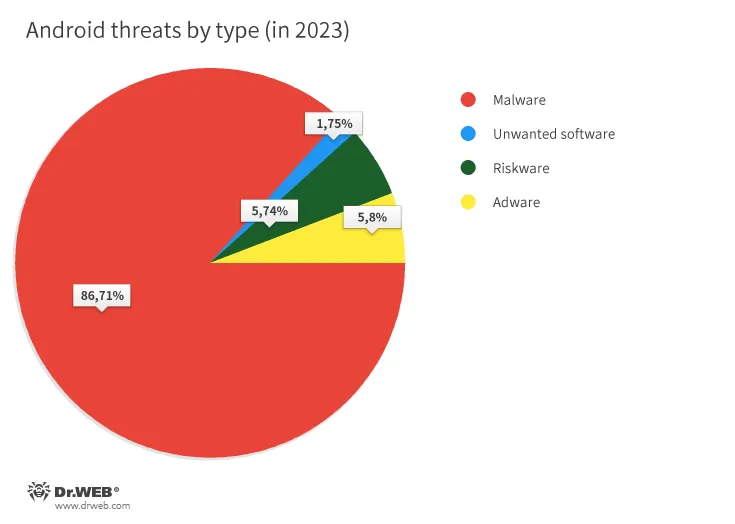
In 2023, with a share of 86.71% of all Dr.Web anti-virus detections, malicious programs were once again the most common Android threats. Adware, with a share of 5.80%, came in second. The third most common Android threats were potentially dangerous programs, or riskware; these were detected on protected devices in 5.74% of cases. And in 1.75% of cases, users encountered unwanted software.
Threat distribution by type, based on the Dr.Web anti-virus detection statistics for mobile devices, is shown in the following diagram:
Malicious programs
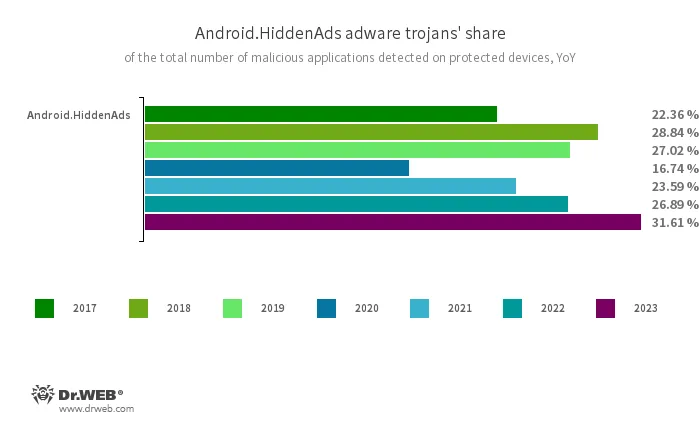
Trojans from the Android.HiddenAds family were the most common malicious Android apps. Their share in the total number of malware detected by Dr.Web anti-virus increased by 4.72 pp, compared to 2022, and was 31.61%.
Android.HiddenAds.3697 was the most active member of the family; it was detected on protected devices in 10.72% of cases. Different variants of this malicious program have remained leaders in terms of number of detections. For example, the Android.HiddenAds.1994 modification was the most widespread in 2021, while the Android.HiddenAds.3018 became the leader in 2022. In 2023, along with Android.HiddenAds.3697, our specialists also found some more modifications of this trojan, including Android.HiddenAds.3597, Android.HiddenAds.3831, Android.HiddenAds.3851, and Android.HiddenAds.3956. It is possible that over time one of them will also be able to take the leading position.
The second most common were Android.Spy trojans, which possess spyware functionality. Compared to 2022, their share in the total volume of malware detected by Dr.Web anti-virus decreased by 14.01 pp. and amounted to 28.22%. The most active among them was Android.Spy.5106. It accounted for 20.80% of all malware detections. And, if we take into account the earlier variants of this trojan—Android.Spy.4498 and Android.Spy.4837, its share was 24.32%, or almost a quarter of all detections.
Ad-displaying trojans from the Android.MobiDash family came in third. Their share in the total volume of malware detections increased by 5.25 pp. and went up to 10.06%.
Malicious programs designed to load and install other apps and capable of running arbitrary code continued to be less active in 2023. For instance, the share of Android.DownLoader trojan family detections decreased by 1.58 pp. to 2.18%, Android.Triada ― by 0.99 pp. to 2.14%, and Android.RemoteCode ― by 0.01 pp. to 2.83%. The share of Android.Mobifun detections decreased by 0.33 pp. to 0.25% and Android.Xiny by 0.21 pp. to 0.27%.
At the same time, the number of attacks using Android.FakeApp malicious fake programs increased. Cybercriminals used these in various fraudulent schemes. Last year, their share in the total number of malware detected by the Dr.Web anti-virus was 1.83%, which is 0.85 pp. higher than the year before.
In 2023, the activity of Android.Locker ransomware trojans decreased. Their share in the total number of malware applications detected came down to 1.15%, from 1.50% the year before. At the same time, the number of Android.Packed detections increased. These are malicious programs of various types that are protected with software packers. The number of their detections increased by 5.22 pp. to 7.98%.
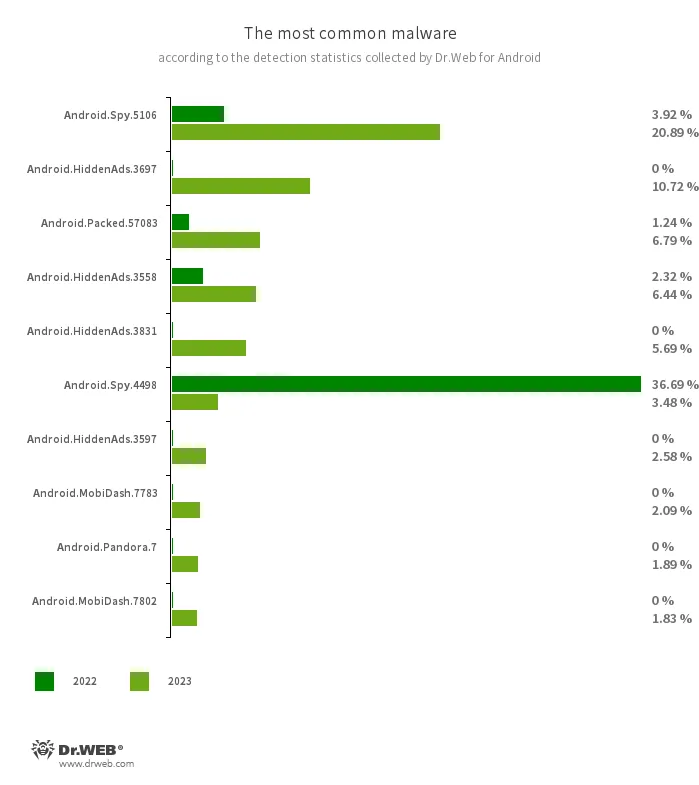
The ten most commonly detected malicious applications in 2023 are shown in the following graph:
- Android.Spy.5106
- Android.Spy.4498
- The detection name for different variants of the trojan that presents itself as modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes containing remotely configurable content.
- Android.HiddenAds.3697
- Android.HiddenAds.3558
- Android.HiddenAds.3831
- Android.HiddenAds.3597
- Trojan apps designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
- Android.MobiDash.7783
- Android.MobiDash.7802
- These are trojans that display obnoxious ads. They come as a special software module that developers incorporate into applications.
- Android.Pandora.7
- The detection name for malicious programs that download and install the Android.Pandora.2 backdoor trojan. Threat actors often embed such downloaders in Smart TV software oriented toward Spanish-speaking users.
Unwanted software
The most common unwanted program in 2023 was Program.FakeMoney.7; it accounted for 29.90% or almost one third of the total number of detections of threats of this type. It belongs to a family of programs that offer users the opportunity to make money by completing various tasks but do not actually pay out any real rewards.
The leader of 2022, Program.FakeAntiVirus.1, dropped to second place a year later with a share of 19.42% detections. This program simulates anti-virus behavior, detects nonexistent threats and offers Android device owners the opportunity to buy its full version to “fix” supposedly identified problems.
Third place, with a share of 9.46%, is held by programs that are modified via the CloudInject cloud service; Dr.Web anti-virus detects such applications as Program.CloudInject.1. During the modification process, dangerous permissions and obfuscated code are added to them. There is no way of controlling the code’s purpose.
As in the year before, in 2023 users often encountered programs that allow their actions to be monitored and various information to be collected about them. Threat actors can use such apps to spy illegally on Android device owners. Among these programs, the most commonly detected ones were Program.SecretVideoRecorder.1.origin (3.84% of cases), Program.wSpy.1.origin (3.24% of cases), Program.SecretVideoRecorder.2.origin (2.25% of cases), Program.wSpy.3.origin (1.68% of cases), Program.SnoopPhone.1.origin (1.11% of cases), Program.Reptilicus.8.origin (0,98% of cases) and Program.WapSniff.1.origin (0,83% of cases).
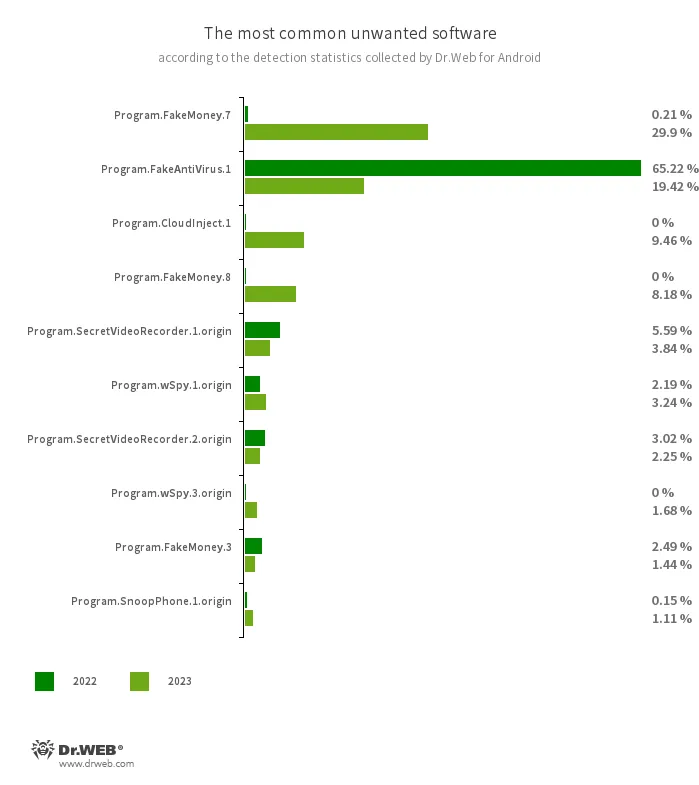
The ten most commonly detected unwanted programs in 2023 are listed in the following graph:
- Program.FakeMoney.7
- Program.FakeMoney.8
- Program.FakeMoney.3
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.CloudInject.1
- The detection name for Android programs that have been modified using the CloudInject cloud service and the eponymous Android utility (the latter was added to the Dr.Web virus database as Tool.CloudInject). Such programs are modified on a remote server; meanwhile, the modders (users) who are interested in such modifications cannot control exactly what will be added to the apps. Moreover, these programs receive a number of dangerous system permissions. Once modification is complete, users can remotely manage these apps. They can block them, display custom dialogs, and track when other software is being installed or removed from a device, etc.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.wSpy.1.origin
- Program.wSpy.3.origin
- These are variants of a commercial spyware app designed to covertly monitor Android device user activity. This program allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to the phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.SnoopPhone.1.origin
- An application designed to monitor the activity of Android device owners. It allows intruders to read SMS, collect call information, track device location, and record the surroundings.
Riskware
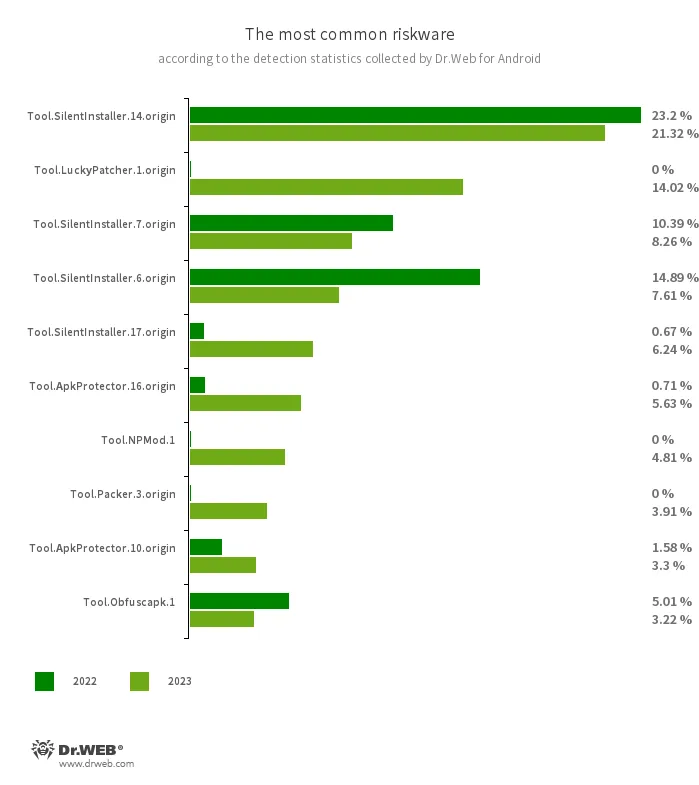
The most commonly detected riskware programs in 2023 were once again the Tool.SilentInstaller utilities, which allow Android apps to run without being installed. They are not malicious, but threat actors can use them for launching malware. These tools accounted for 48.98% or almost half of the potentially dangerous software detections. At the same time, compared to 2022, their share decreased by 17.94 pp. The second most widespread potentially dangerous programs were members of the Tool.LuckyPatcher family of utilities. These can be used to modify Android applications and add special scripts downloaded from the Internet to them. These tools accounted for 14.02% of riskware detections. In third place were apps protected with Tool.ApkProtector packer; the number of their detections increased by 5.33 pp. and reached 10.14%.
At the same time, the number of detections of apps protected with other families of software packers also increased. For instance, the Tool.Packer family’s share increased from 3.58% to 4.47%, and the Tool.Ultima family’s share increased from 0.05% to 1.04%.
Another widespread, potentially dangerous software program was the NP Manager utility. It is designed to modify Android programs and bypass their digital signature verification. To accomplish this, a special module is embedded into them. Dr.Web anti-virus detects such modified apps as Tool.NPMod. The share of such apps was 4.81%.
In contrast, apps modified with the Tool.Obfuscapk obfuscator tool were detected less often, and their share decreased from 5.01% in 2022 to 3.22% in 2023.
The ten most widespread riskware apps detected on protected Android devices in 2023 are shown in the following graph:
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.17.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment in the context of the apps in which they are integrated. The APK files, launched with the help of these platforms, can operate as if they are part of such programs and can also obtain the same permissions.
- Tool.LuckyPatcher.1.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root-access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads specially prepared scripts from the Internet, which can be crafted and added to the common database by any third party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
- Tool.ApkProtector.16.origin
- Tool.ApkProtector.10.origin
- The detection name for Android apps protected by the ApkProtector software packer. This packer is not malicious in itself, but cybercriminals can use it when creating malware and unwanted applications to make it more difficult for anti-virus software to detect them.
- Tool.NPMod.1
- The detection name for Android programs that have been modified using the NP Manager utility. A special module is embedded in such apps, and it allows them to bypass digital signature verification once they have been modified.
- Tool.Packer.3.origin
- The detection name for Android programs whose code is encoded and obfuscated by the NP Manager tool.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android app source code to make reverse engineering more difficult. Cybercriminals use it to protect malicious applications from being detected by anti-virus programs.
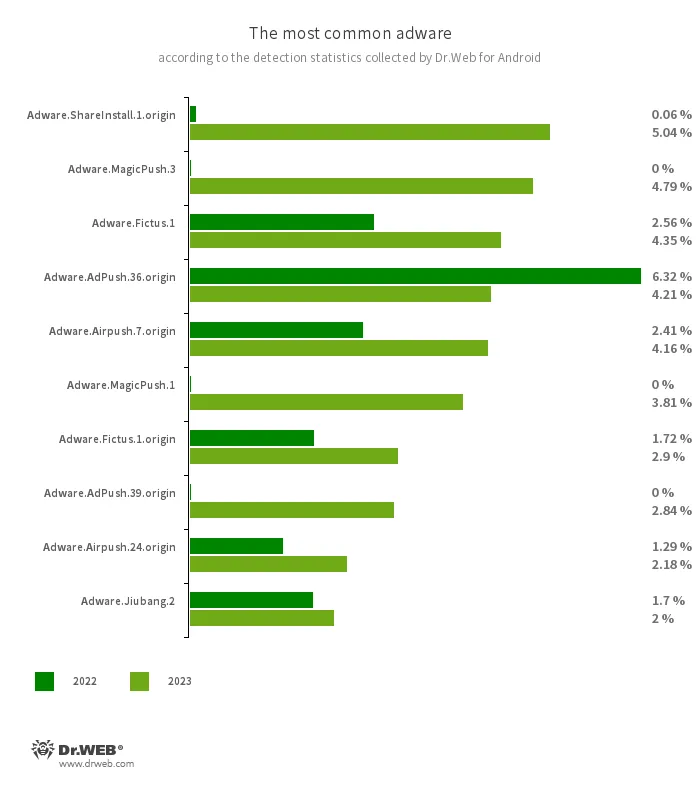
Adware
The most popular adware in 2023 was Adware.Adpush, a family of advertising modules built into some Android apps. They accounted for more than a third of detections — 35.82%; compared to 2022, their share decreased by 24.88 pp. The second most common adware programs were members of the Adware.MagicPush family with a share of 9.58%. Third place was held by Adware.Airpush modules whose share increased by 3.24 pp., and they accounted for 8.59% of detections.
Also among the leaders were representatives of the Adware.ShareInstall family, whose share increased from 0.06% to 5.04%, Adware.Fictus (with growth from 2.58% to 4.41%), Adware.Leadbolt (with growth from 3.31% to 4.37%), Adware.Jiubang (with growth from 2.83% to 3.22%), and Adware.Youmi (with growth from 0.06% to 2.20%).
At the same time, Adware.SspSdk modules, which occupied second place the year before, did not even make it into the top 10 most widespread families in 2023. They accounted for 1.49% of the adware detected on protected devices.
The ten most commonly detected adware apps detected on protected devices in 2023 are shown in the graph below:
- Adware.ShareInstall.1.origin
- An adware module that can be built into Android applications. It displays notifications containing ads on the Android OS lock screen.
- Adware.MagicPush.1
- Adware.MagicPush.3
- An adware module embedded into Android applications. It displays pop-up banners over the OS user interface when such hosting apps are not in use. These banners contain misleading information. Most often, they inform users about suspicious files that have allegedly been discovered, or they offer to block spam for users or to optimize their device’s power consumption. To do this, they ask users to open the corresponding app containing such an adware module. Upon opening the app, users are shown an ad.
- Adware.Fictus.1
- Adware.Fictus.1.origin
- An adware module that malicious actors embed into the cloned versions of popular Android games and applications. Its incorporation is facilitated by a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
- Adware.AdPush.36.origin
- Adware.AdPush.39.origin
- Adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, these modules collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.Airpush.7.origin
- Adware.Airpush.24.origin
- A family of adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.Jiubang.2
- An adware module built into Android programs. It draws advertisement banners over other app windows.
Threats on Google Play
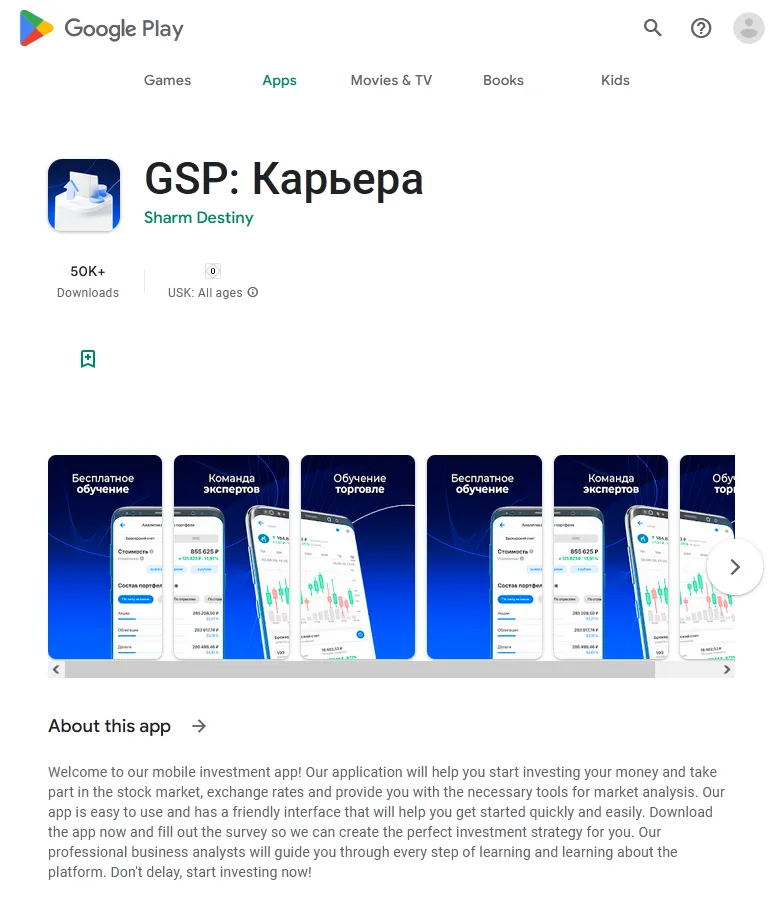
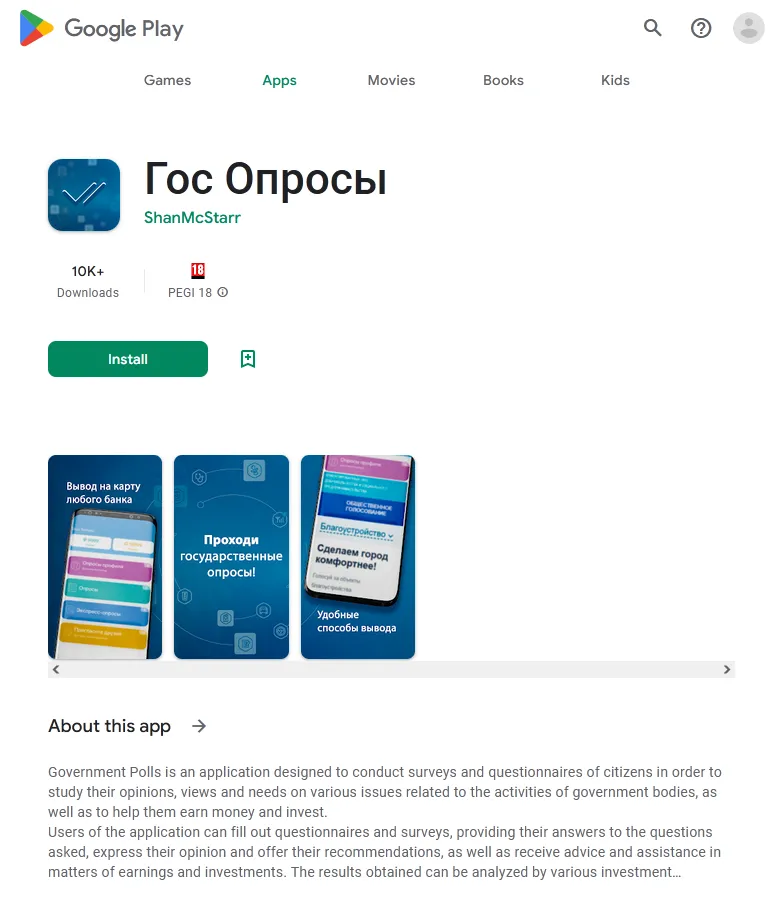
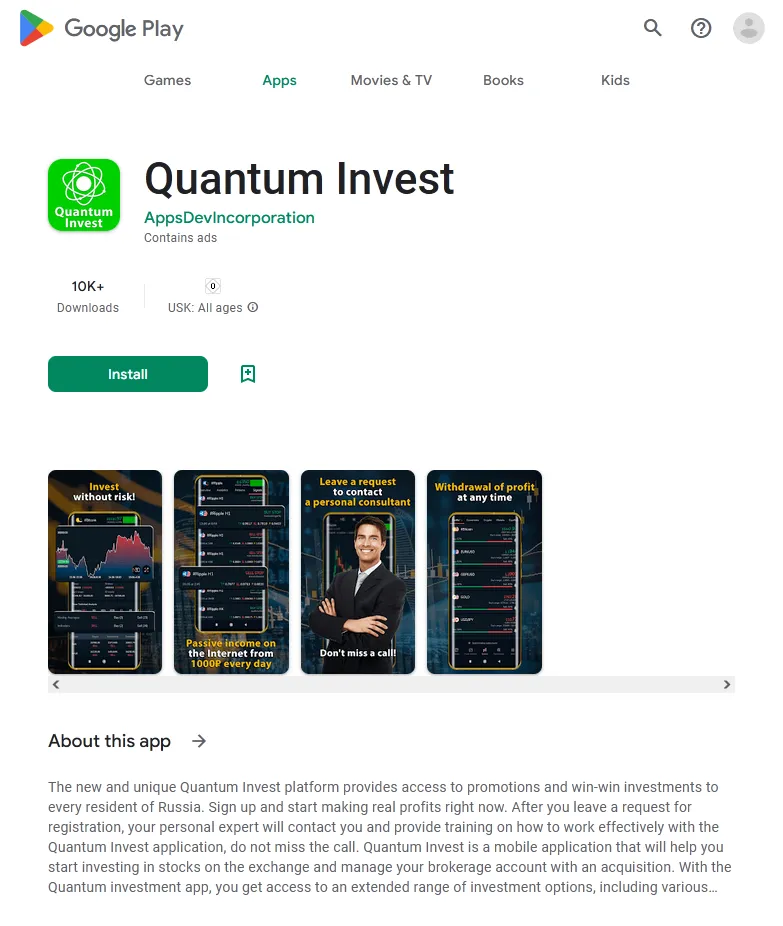
In 2023, Doctor Web’s virus laboratory discovered over 440 malicious programs on Google Play, with an overall download count of at least 428,434,576. Among the many programs containing the built-in Android.Spy.SpinOk trojan module (covered in one of the previous paragraphs), our specialists found hundreds of trojans from the Android.FakeApp family. Used by cybercriminals to execute different fraudulent schemes, these trojans were distributed under the guise of a variety of software. Under certain conditions, they actually could provide the promised functionality, but their primary task was to load target websites when commanded to do so by a remote server.
Many of these trojans were passed off as finance-themed apps, like teaching aids and reference books, programs for home bookkeeping or accessing stock information and trading, apps for participating in surveys, etc.
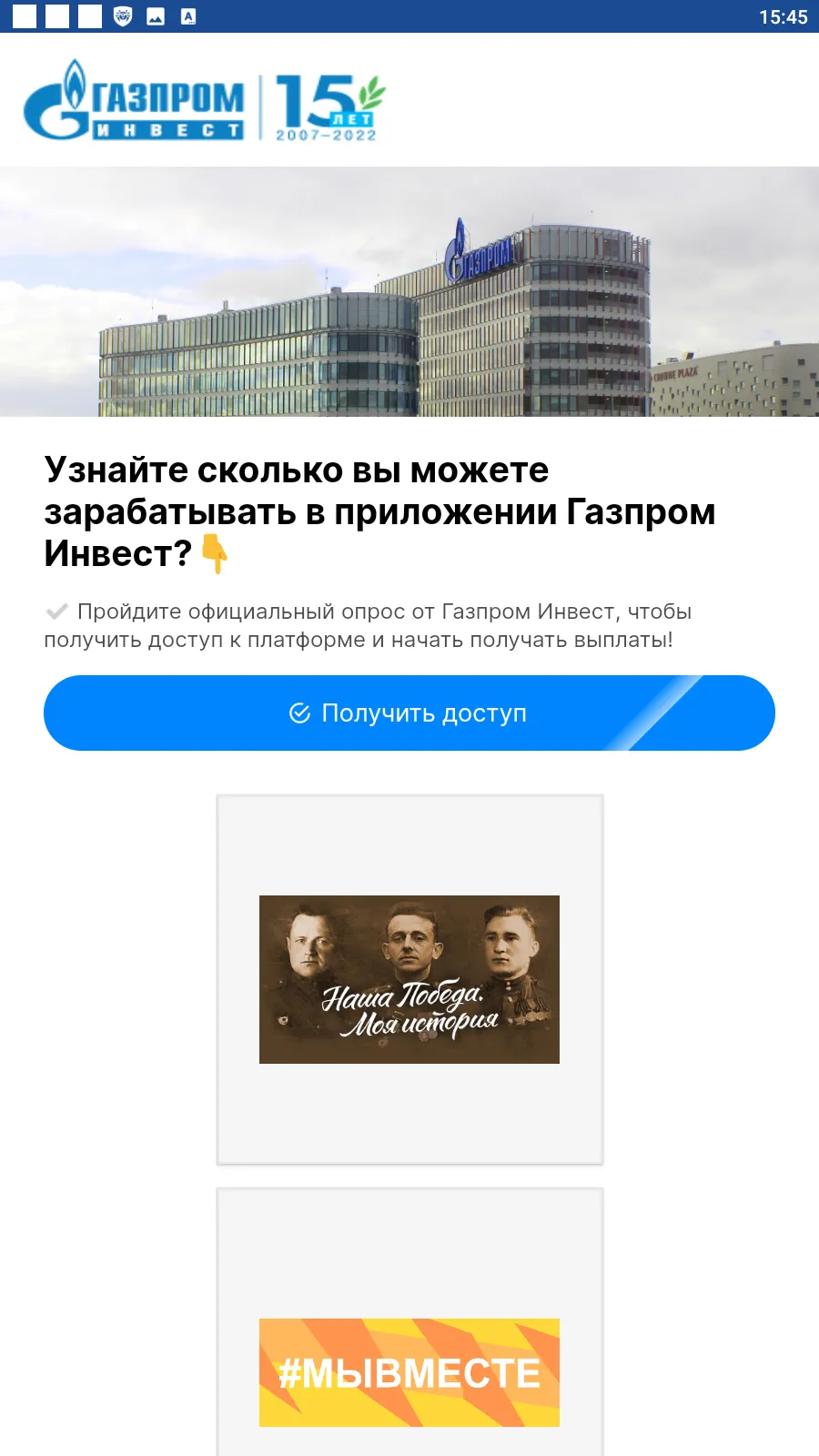
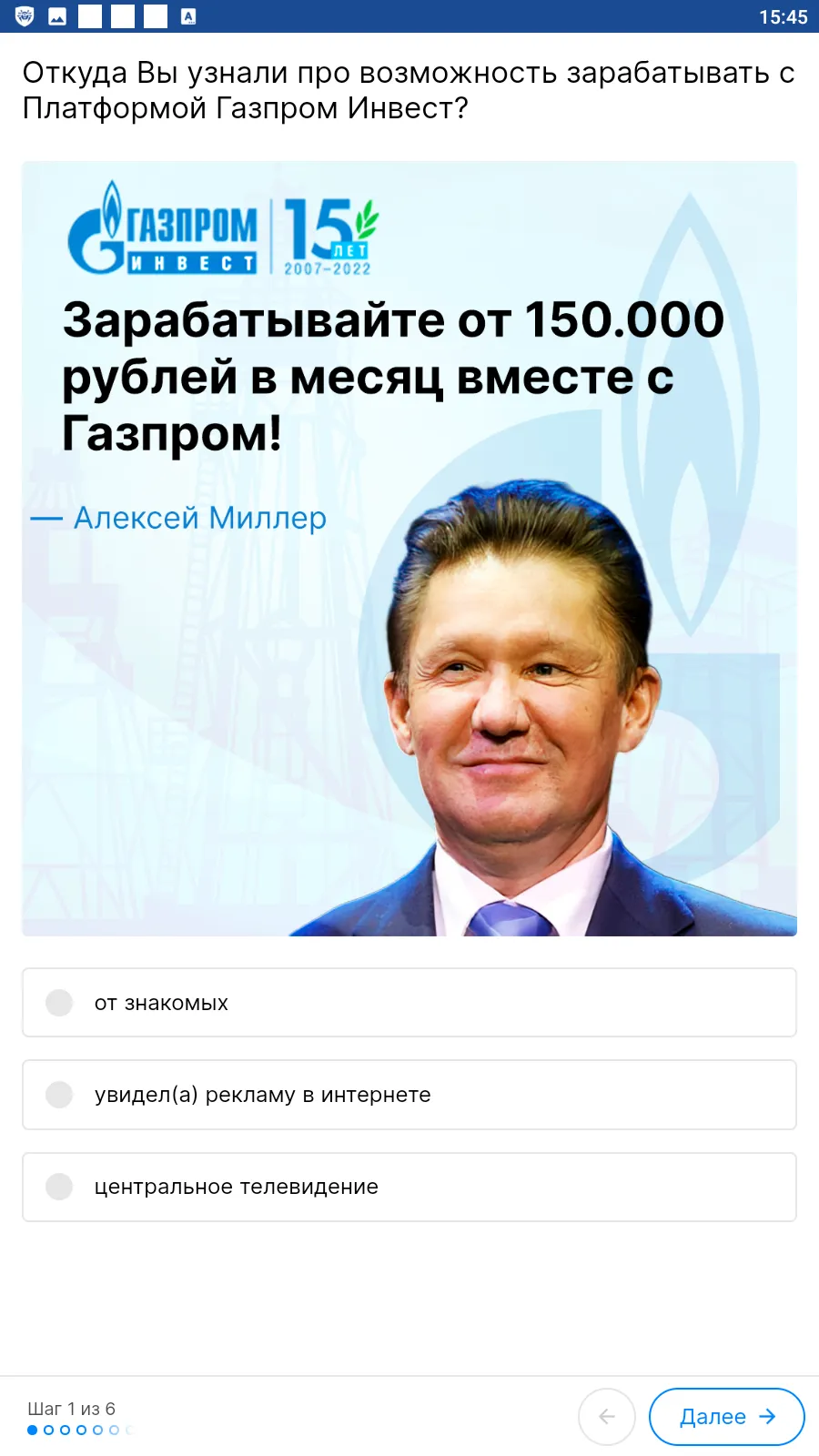
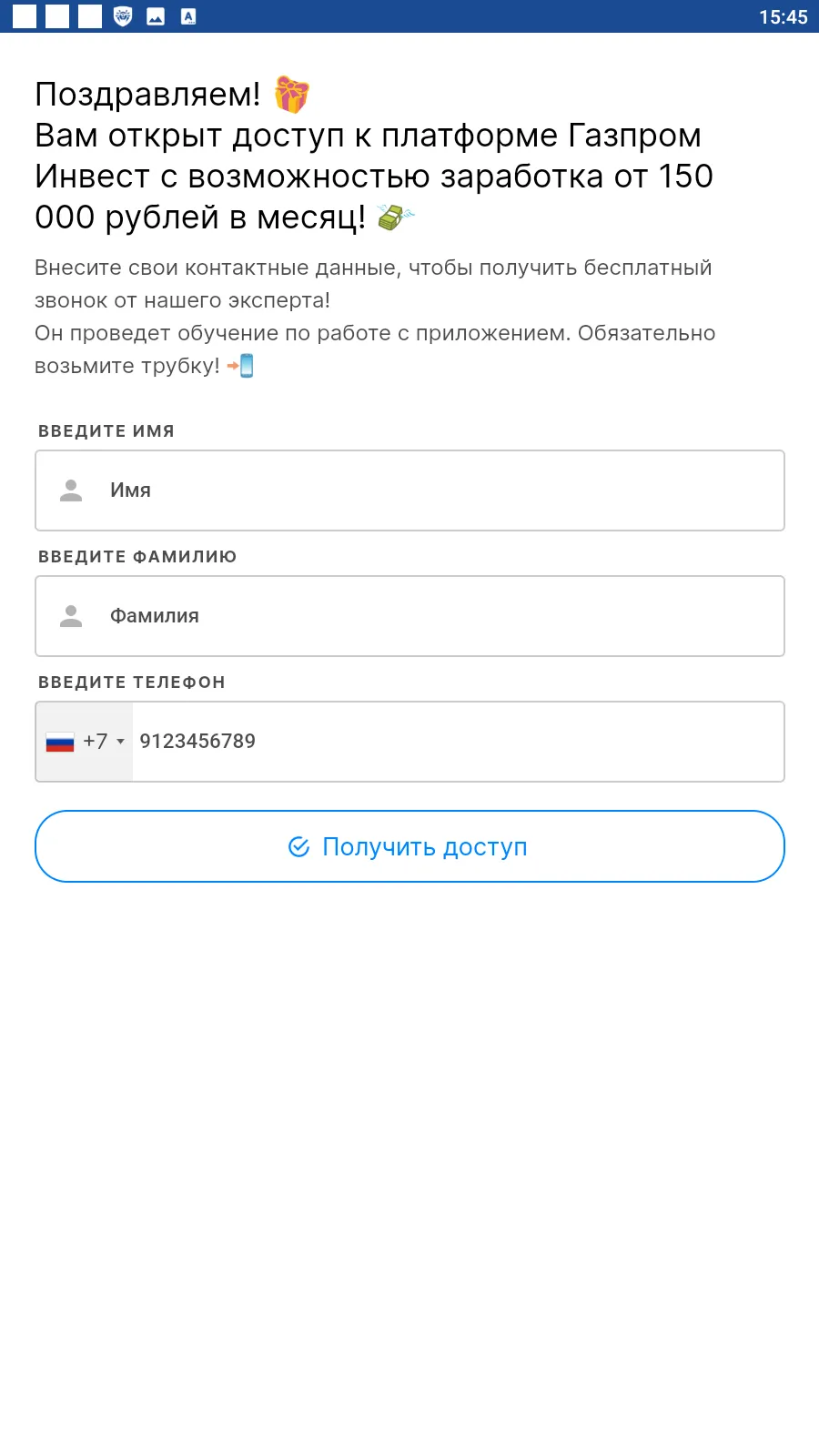
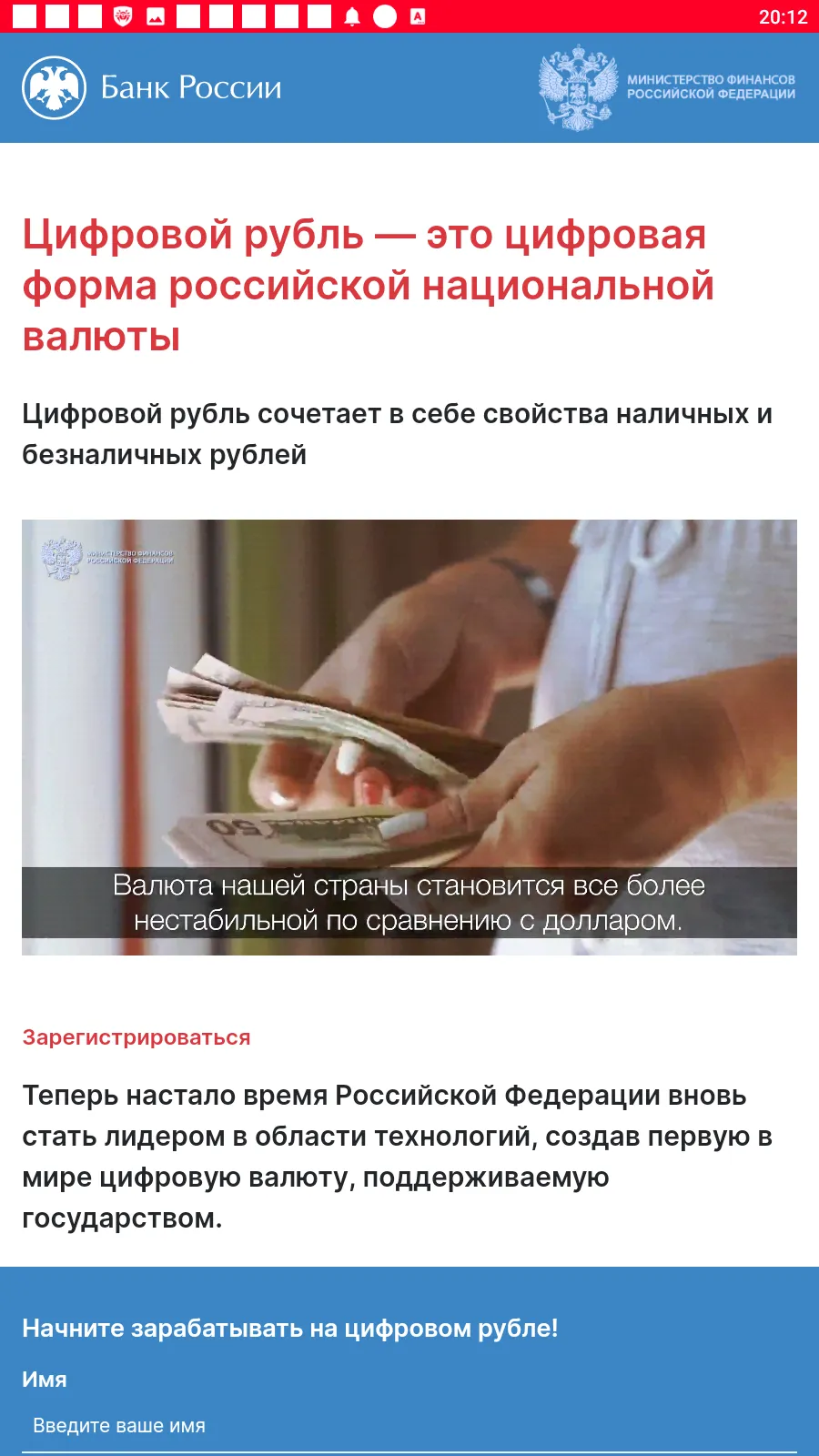
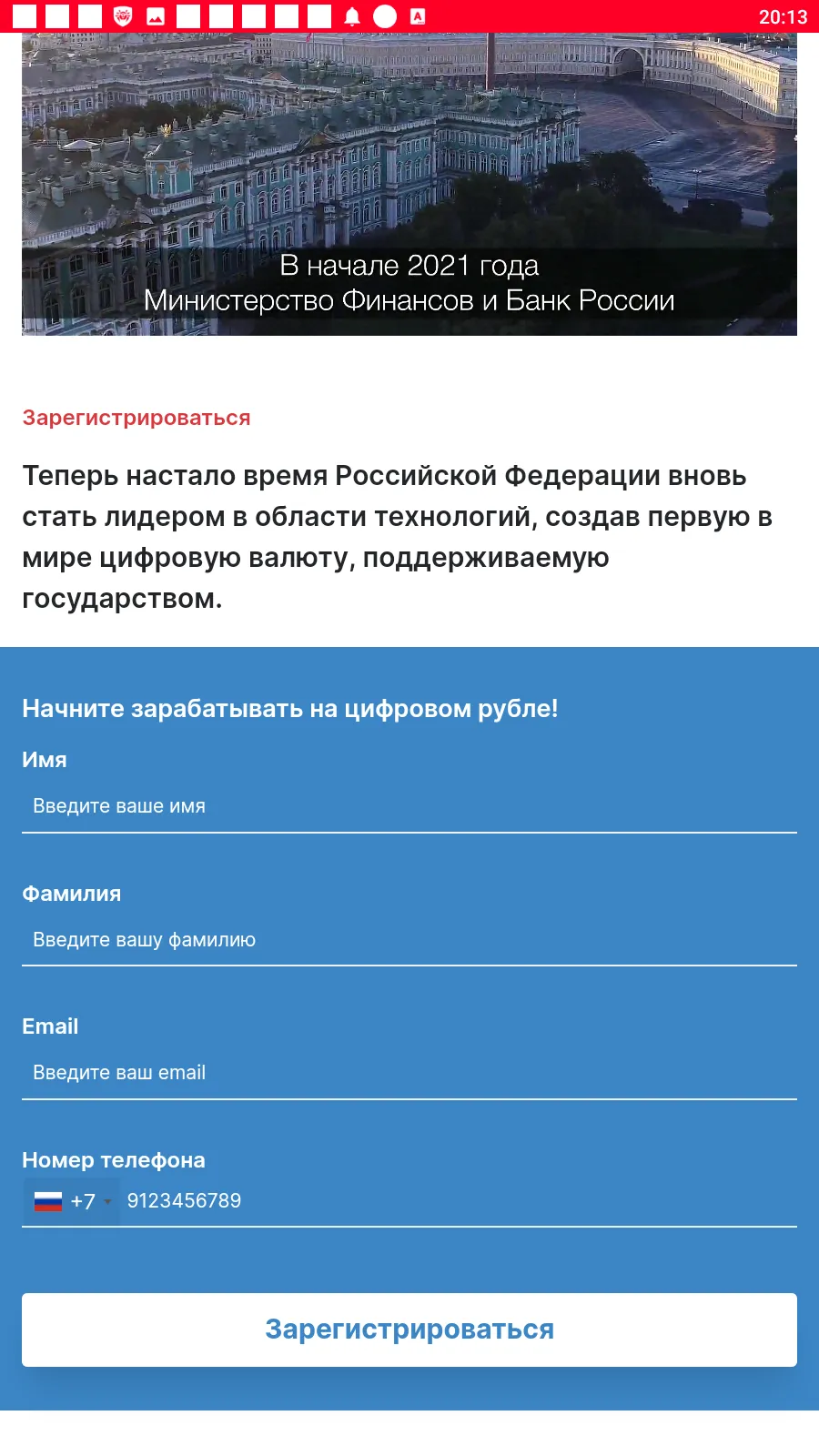
Such fake programs could load fraudulent sites where potential victims were offered, allegedly on behalf of famous companies, an opportunity to make money via investments and crypto-currency trading, and, in some cases, to even receive company shares or government payments — both “as a gift”. To “access” one or another service, users first had to answer several questions and then provide some personal data.
Below are examples of the fraudulent websites these trojans loaded. In the first case, scammers offered users the opportunity to access some investing platform, one supposedly related to a large Russian oil and gas company. In the second case, fraudsters, allegedly on behalf of The Central Bank of the Russian Federation, offered potential victims the chance to start “making money with the Digital ruble”.
Some of these fake apps were distributed under the guise of games; they could load online casino and bookmaker websites.
Examples of how such trojan apps operated as games:
Examples of the bookmaker and online casino websites they loaded:
Other Android.FakeApp trojans were distributed as sports-themed programs, including supposedly official software from legal bookmaker firms, reference books on various sports, apps that provided information about sporting events and matches, programs for reading sports news, and so on.
They could also work as harmless apps (their functionality could, however, differ from what was promised) and load different websites.
Below are examples of how these trojans operated as harmless software: two of them launched as games, while the third one displayed a table containing information about football matches.
The same programs later began loading sites offering bookmaker services:
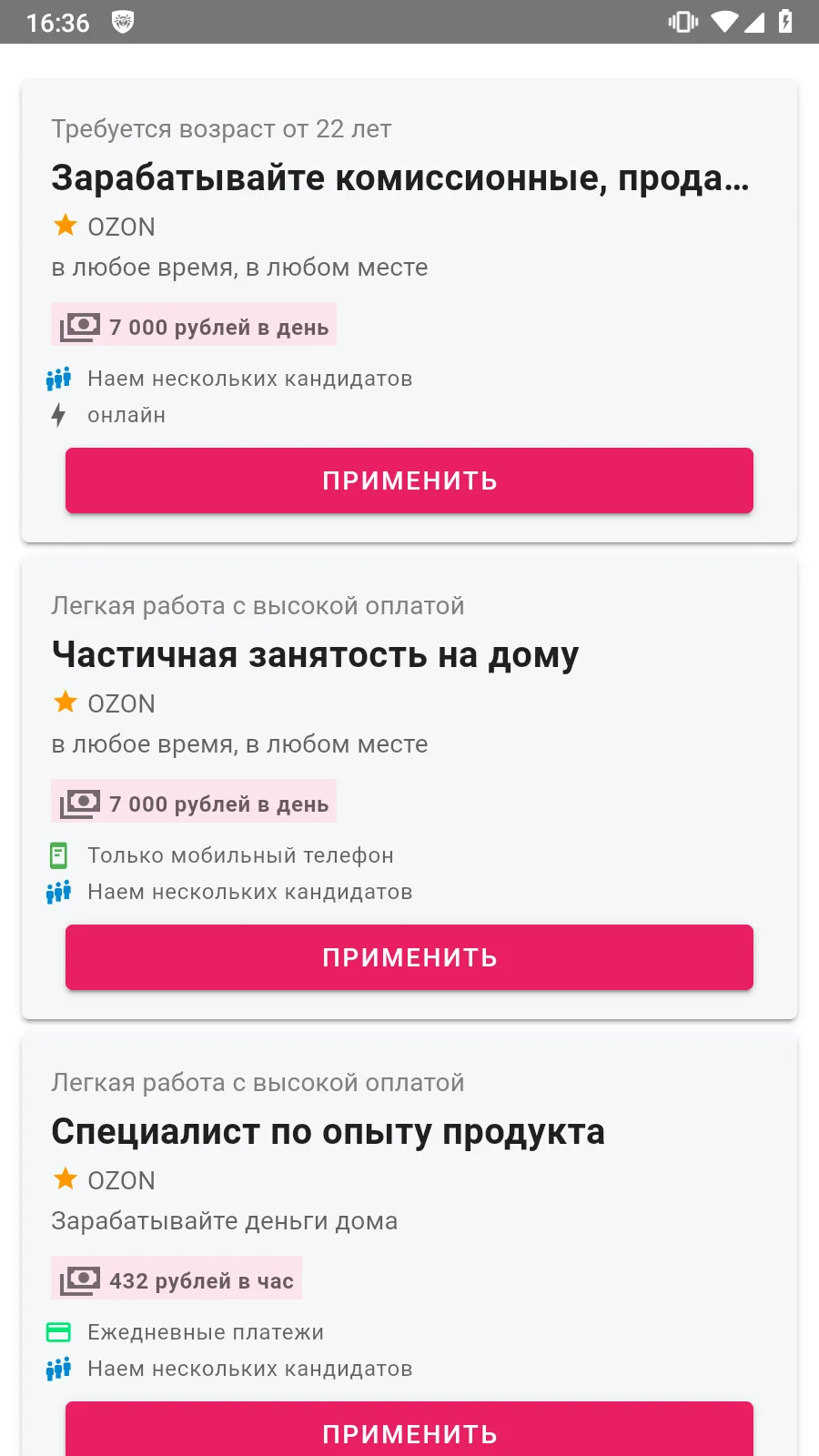
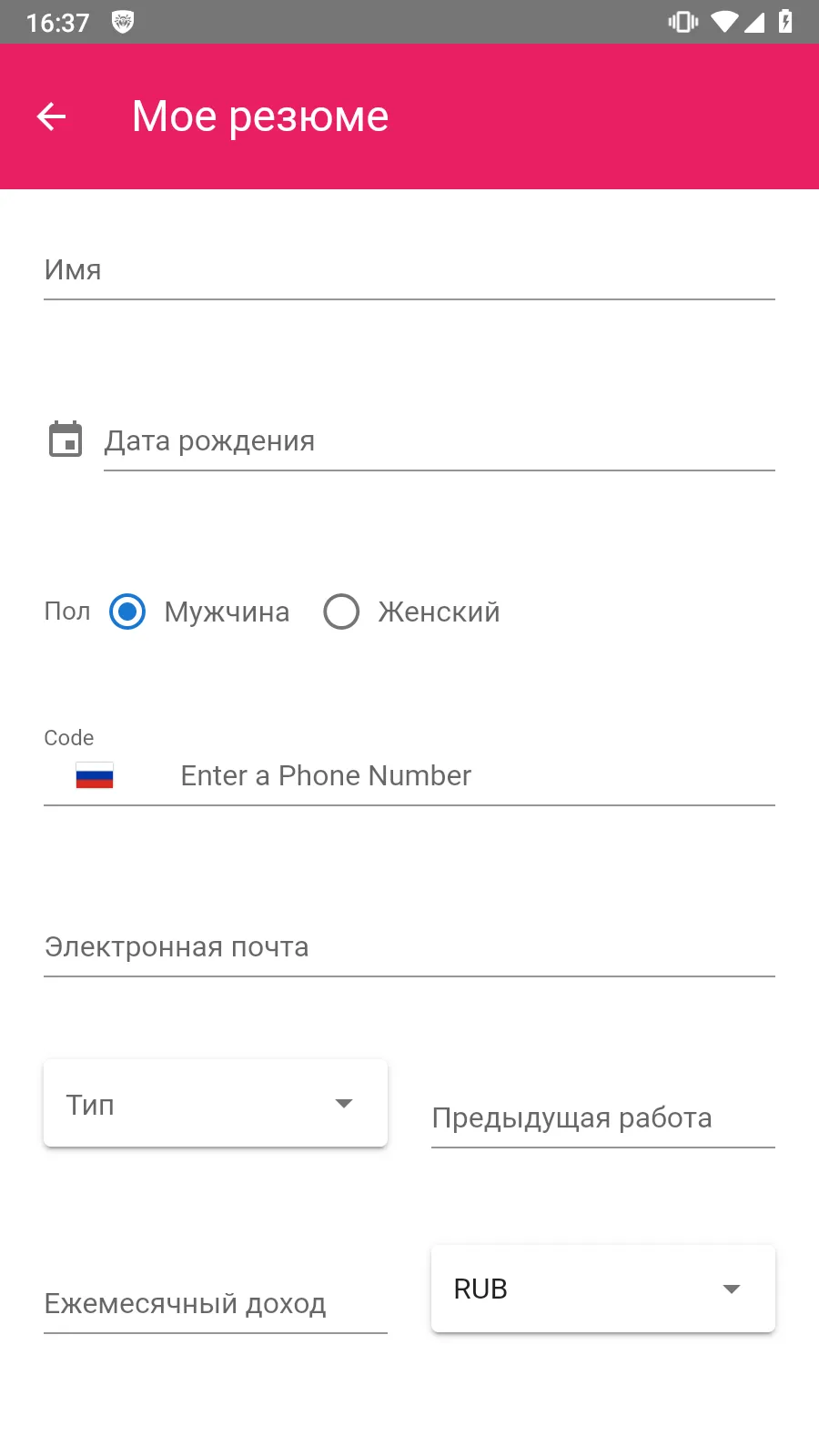
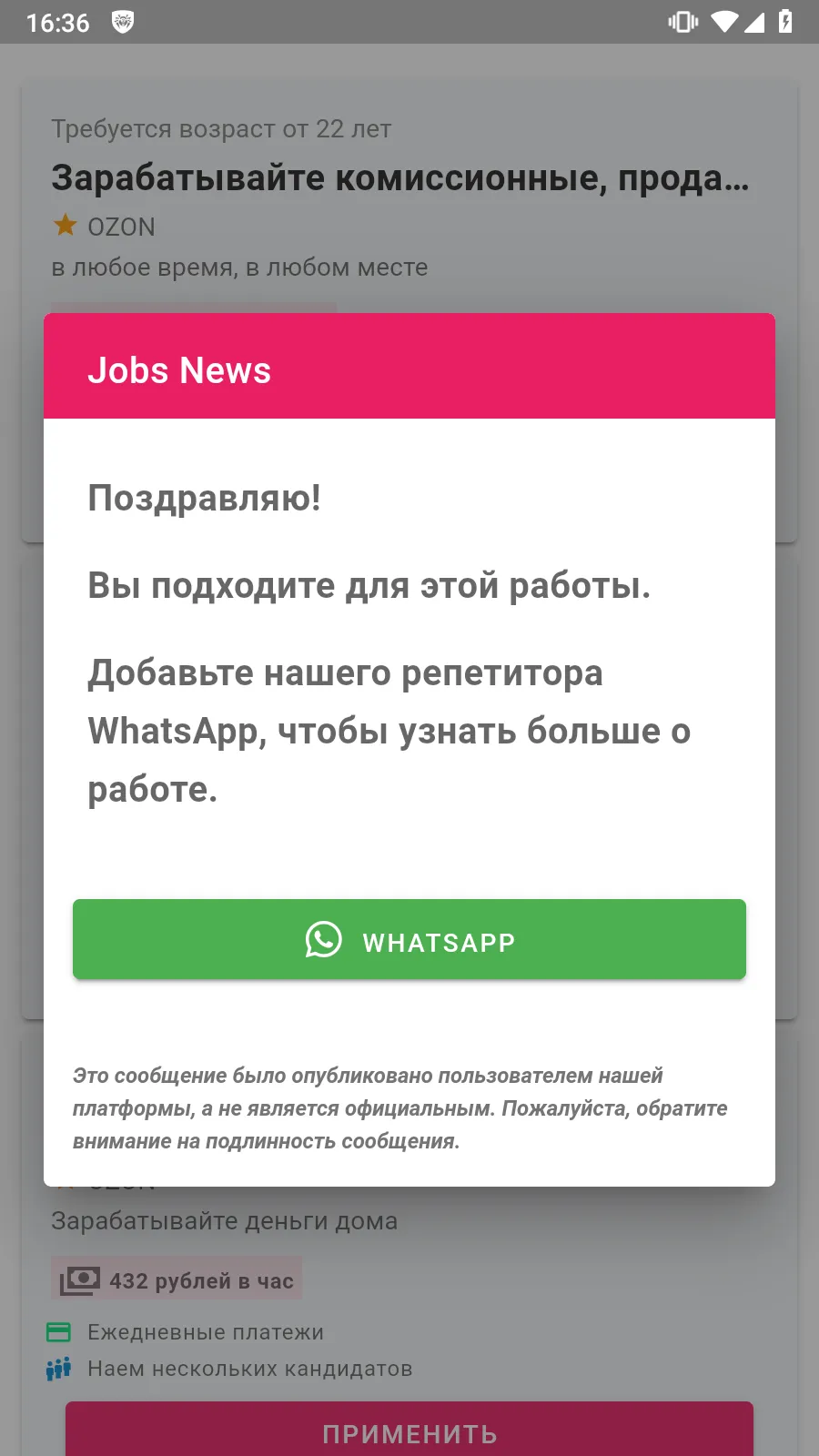
Users installed some fake programs, thinking that they were job-search apps.
Such Android.FakeApp trojan variants display fake vacancy listings that are loaded from bogus websites. When users try to respond to one of the “job offers”, they are asked either to contact the “employer” via messengers like WhatsApp and Telegram or to input their personal data into a special form—allegedly for creating and sending out a resume.
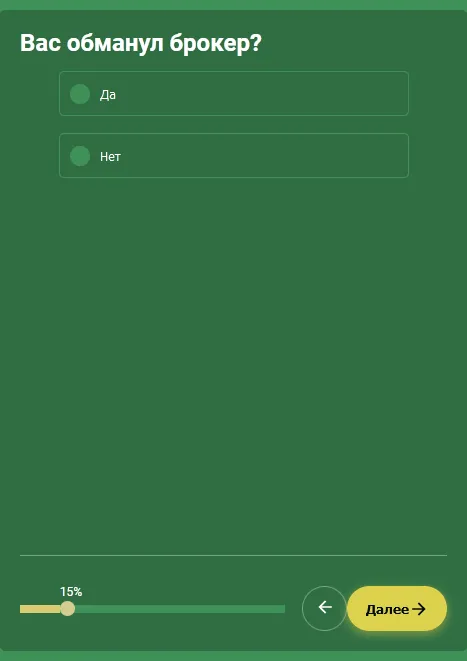
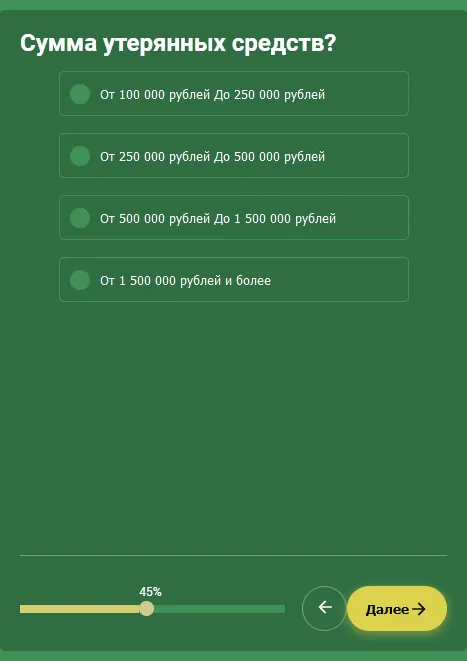
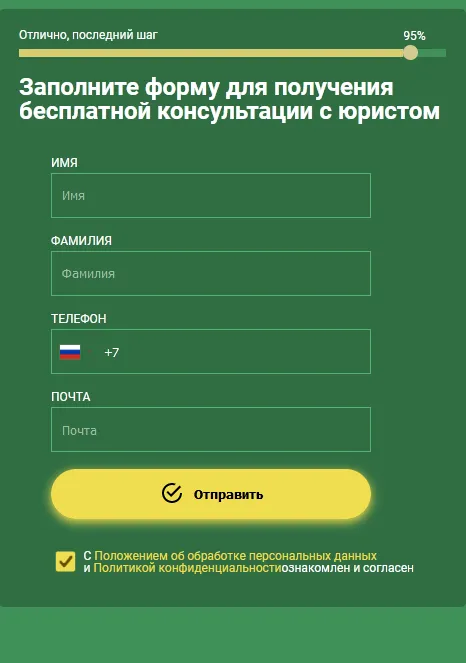
At the same time, in 2023, the topic of Android.FakeApp fake programs, which loaded fraudulent Internet resources, continued to expand. For example, against the backdrop of many years of cybercriminals attempting to lure users to fake financial sites, our specialists noted the emergence of trojan variants that were masquerading as legal programs, like reference books. These supposedly could help victims of “investing” scammers get back lost money. In reality, these apps would load more fraudulent sites that operated according to a well-known scheme. In this case, their visitors had to answer a few questions and then provide some personal data in order to “get a free consultation with a lawyer”.
An example of a “legal assistance” website where victims of investment scams could allegedly consult with a lawyer and get a chance to get their lost money back:
Doctor Web’s virus laboratory also uncovered a number of other malicious programs on Google Play in 2023. Among them were trojans from the new Android.Proxy.4gproxy family that turned infected devices into proxy servers and covertly transmitted third-party traffic through them. A special utility called 4gproxy (added to the Dr.Web virus database as the riskware software Tool.4gproxy) was built into these malicious apps. This utility allows Android devices to be used as proxy servers. It is not malicious in itself and can be used for legitimate purposes. However, in the case of Android.Proxy.4gproxy trojans, the proxy server operation was executed without users’ involvement and their explicit consent.
Moreover, our specialists discovered several new ad-displaying trojans from the Android.HiddenAds family: Android.HiddenAds.3785, Android.HiddenAds.3781, Android.HiddenAds.3786, and Android.HiddenAds.3787. When installed on Android devices, they tried to conceal their presence by replacing their icons on the home screen menu with transparent versions and changing their names so that they were left blank. Additionally, they could also disguise themselves as a Google Chrome web browser by replacing their icons with the corresponding copy. When users clicked on one of these modified icons, the trojans would mislead them by launching the browser and simultaneously continuing to work in the background. Consequently, not only did they make themselves less noticeable, but they also increased their chances of operating longer. If, for some reason, the trojans would stop working, users could restart them, mistakenly thinking that they were launching the browser. Such functionality was previously seen, for example, in the Android.HiddenAds.3766 trojan, which was also distributed via Google Play.
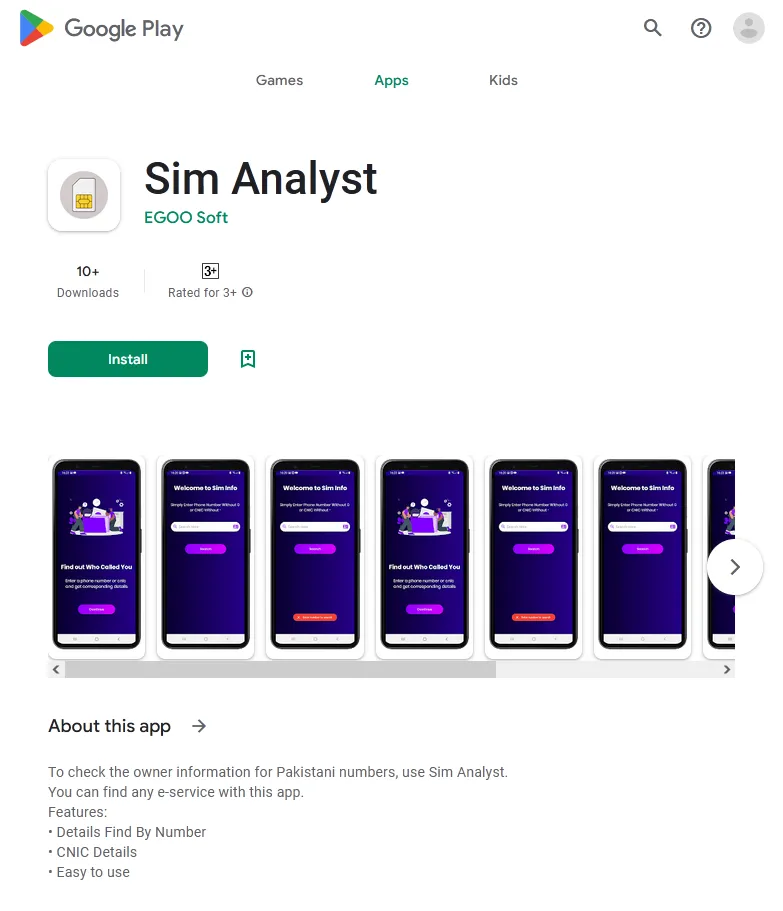
The Android.Spy.1092.origin spyware trojan, which was based on a remote administration tool (or RAT) called AhMyth Android Rat, was another threat our analysts discovered. It was disguised as the Sim Analyst app, which allegedly could help Pakistani users search information about fellow Pakistani cellular network subscribers by entering their mobile phone numbers.
The standard version of the AhMyth Android Rat spyware tool provides rich functionality. For instance, it allows an Android device’s location to be tracked, photos to be taken via the built-in camera and recordings to be made of the surroundings via the microphone. Additionally, it can intercept SMS and obtain information on phone calls and phonebook contacts. However, since apps distributed via Google Play have restricted access to certain sensitive functions, the spyware variant our malware analysts discovered was not so feature-rich. It could track a device’s location, hijack the contents of notifications, and steal various media files, such as photos and videos, and also files that were transferred via messengers and stored locally on a device.
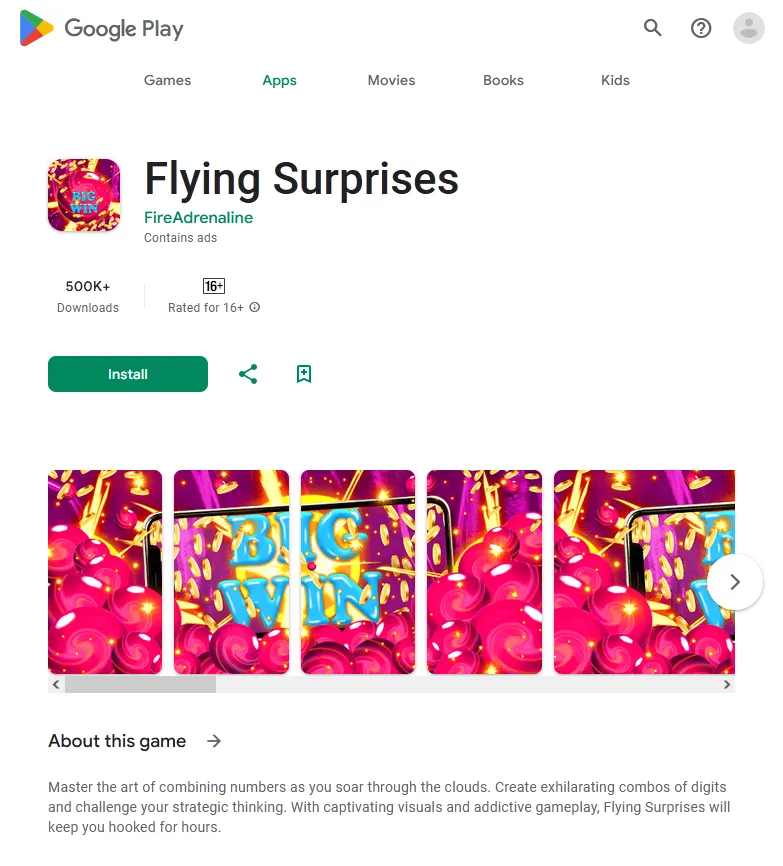
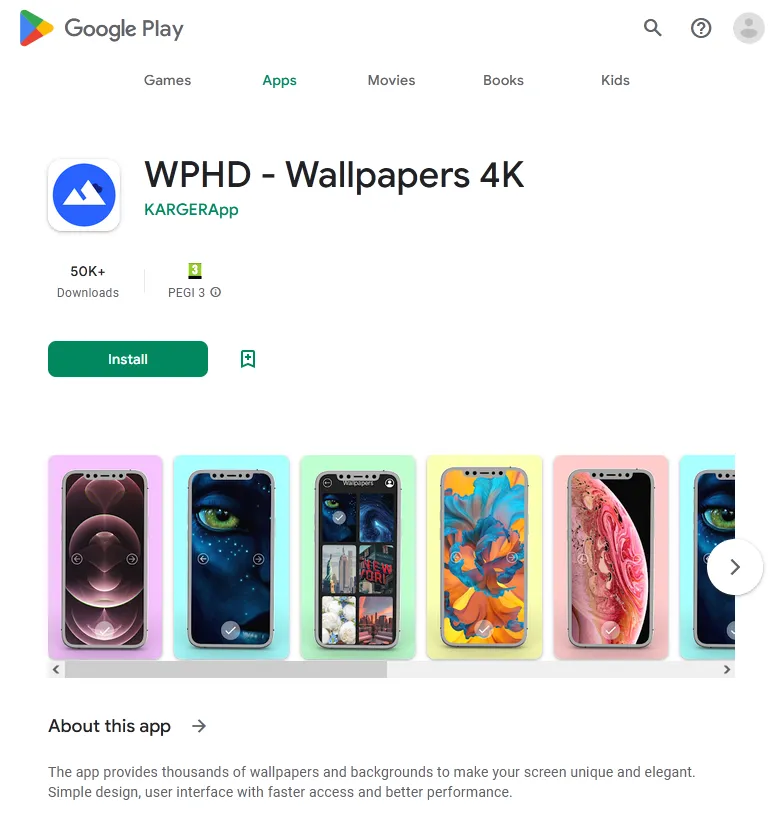
Our specialists also detected the Android.CoinSteal.105 trojan on Google Play. It was designed to steal crypto currency. Attackers tried passing it off as the official application of the P2B crypto exchange (P2B official) by using a similar name: “P2B Trade: Realize The P2Pb2b”.
The first image below depicts the fake app’s page on Google Play, while the second image depicts the page of the genuine software:
At the same time, the phony application was even promoted by crypto bloggers. As a result, it was installed twice as many times as the original.
When launched, Android.CoinSteal.105 would load in WebView the TDS (Traffic Delivery System) website specified by the attackers. This site would then perform a chain of redirects to other Internet resources. For example, it would load the official website of the P2P crypto exchange: https://p2pb2b.com. The trojan would inject JavaScript scripts into it. Using these scripts, it would substitute the crypto-wallet addresses that users entered to withdraw crypto currency. That being said, other sites could potentially have been loaded as well, including fraudulent ones or ones containing ads.
Among the threats on Google Play identified by Doctor Web’s virus laboratory were also some new trojans from the Android.Subscription family—Android.Subscription.19, Android.Subscription.20, and Android.Subscription.21. They were distributed under the guise of harmless apps and loaded websites of affiliate services to subscribe Android device owners to paid services. Such trojans either activate subscriptions automatically or ask potential victims to provide their mobile phone number.
Examples of websites that these malicious apps load to activate paid subscriptions:
At the same time, over the course of 2023, other malicious programs that subscribed users to paid services were also discovered on Google Play. Of particular note are over 20 trojans from the Android.Joker and Android.Harly families. Among them were Android.Joker.1991, Android.Joker.2000, Android.Joker.2117, Android.Joker.2152, Android.Joker.2176, Android.Joker.2217, Android.Harly.13, Android.Harly.25, Android.Harly.66, and Android.Harly.80.
Banking trojans
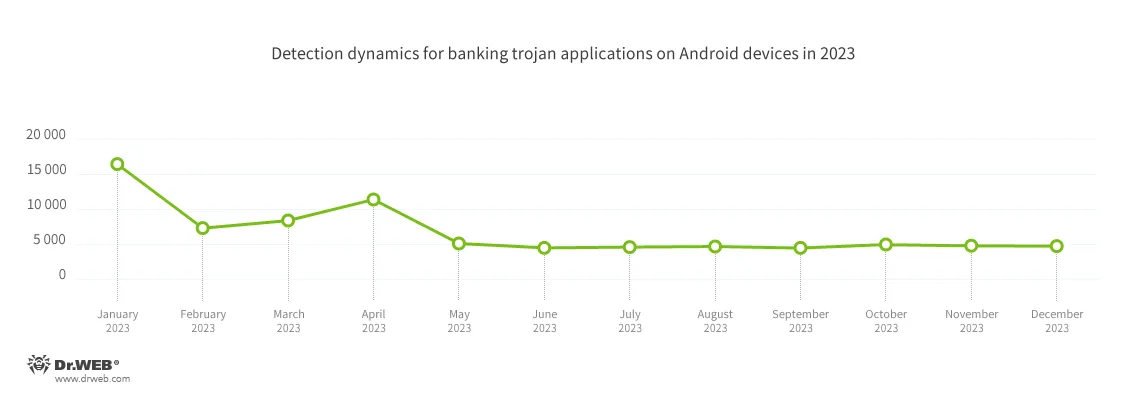
According to detection statistics collected by Dr.Web for Android, the number of banking trojans detected in 2023 decreased by 46.97%, compared to the previous year. With that being said, their share of all the malware detected on protected devices amounted to 3.58%, which is 0.84 pp. less than the year before. The highest banking trojan activity occurred in the first half of the year, with the maximum number of detections occurring in January. After a steep decline in February, their activity began growing again and reached a local peak in April. Following another decline in the number of attacks in May, the number of banking trojans detected remained constant until the end of the year.
The banking trojans most popular with cybercriminals in 2022 also remained active during 2023. For instance, our analysts detected attacks involving families like Anubis (Android.BankBot.670.origin, Android.BankBot.794.origin, Android.BankBot.967.origin), Coper, S.O.V.A. (Android.BankBot.992.origin), Hydra (Android.BankBot.1048.origin), Ermac (Android.BankBot.970.origin, Android.BankBot.1037.origin), and Alien (Android.BankBot.745.origin, Android.BankBot.873.origin, Android.BankBot.1078.origin). Threat actors also distributed malicious programs like Cerberus (Android.BankBot.8705, Android.BankBot.1052.origin), Sharkbot (Android.BankBot.977.origin), and GodFather (Android.BankBot.1064.origin, Android.BankBot.1077.origin).
In Latin America, Banbra (Android.BankBot.1073.origin) banking trojans were widespread again, and users from Brazil also encountered the PixPirate (Android.BankBot.1026.origin) family.
The widespread MoqHao family (Android.Banker.5063, Android.Banker.487.origin, Android.Banker.533.origin, Android.Banker.657.origin), whose attacks encompass many countries, was actively used against Southeast Asian and Asia-Pacific Android users. Meanwhile, South Korean users also encountered different members of the Fakecalls (Android.BankBot.761.origin, Android.BankBot.919.origin, Android.BankBot.1002.origin) and Wroba (Android.Banker.360.origin) families. The Wroba family (Android.BankBot.907.origin) was also used to attack users in Japan. And Android device owners from China were attacked by the Android.Banker.480.origin trojan.
Our specialists, however, also observed new trends in banking trojan attacks, one of the most notable ones being the emergence of new banking malware families, many of which targeted users in Russia. Among them were Android.Banker.5127 and Android.Banker.5273, which were created with the help of the Tasker scheduling app; Android.Banker.597.origin, Android.Banker.592.origin, and Android.Banker.5235, which masqueraded as various services, including — KoronaPay, Дайвинчик 18+ (Daivinchik 18+), Yandex, Rostelecom, and OnlyFans; and numerous other trojans.
Attacks on Russian users also involved the use of Android.Banker.637.origin, Android.Banker.632.origin, Android.Banker.633.origin, and Android.Banker.635.origin—banking trojans that threat actors distributed under the guise of a variety of apps. For example, criminals passed them off as software that was supposedly related to different online streaming services (like STAR), adult-only apps, mods of the VK social network official Android client, and thematic programs based on the series “The Boy’s Word. Blood on the asphalt” (“Слово Пацана. Кровь на асфальте”), which in 2023 gained popularity in Russia and countries of the former USSR, etc.
Also widespread in Russia were the banking trojans Android.BankBot.1062.origin, Android.BankBot.1093.origin, and Android.BankBot.1098.origin. These later expanded the geography of their attacks to include users in Uzbekistan.
At the same time, Doctor Web’s malware analysts noted the emergence of many banking trojans targeting Iranian users. Among them were Android.BankBot.1088.origin, Android.BankBot.14871, Android.BankBot.1083.origin, Android.Banker.5292, Android.Banker.5233, Android.Banker.5276, and Android.Banker.5379. Moreover, malicious actors distributed Tambir Android banking trojans (Android.BankBot.1099.origin), which were designed to attack Turkish Android device owners.
Noticeable activity was also observed from banking trojans of the Rewardsteal banking trojan family (Android.Banker.562.origin, Android.Banker.5138, Android.Banker.5141, Android.Banker.588.origin, Android.Banker.611.origin). Among these, the most common modifications targeted customers of such banks as ICICI Bank, HDFC Bank, SBI, Axis bank, Citi bank, and RBL bank.
Prospects and trends
Since material gain remains the main motivation for cybercriminals, we should expect new malicious programs to emerge that will help them increase their illegal income in 2024. The most likely candidates for this would be more adware trojans, banking malware, and scam and spy apps.
The risk of new malware appearing on Google Play will remain. And it is possible that attackers will more actively use other sources, malicious websites in particular, to distribute Android threats.
We should also highly expect the emergence of new trojans designed to steal crypto currency from both Android device and iOS device owners.
To protect yourself from criminal attacks and to keep your money and personal data safe, we recommend installing Dr.Web anti-virus on all your supported devices. For our part, we at Doctor Web will continue to monitor trends in the cyber-threat landscape and inform our users about important events in the field of information security.