Doctor Web’s February 2024 virus activity review
April 1, 2024
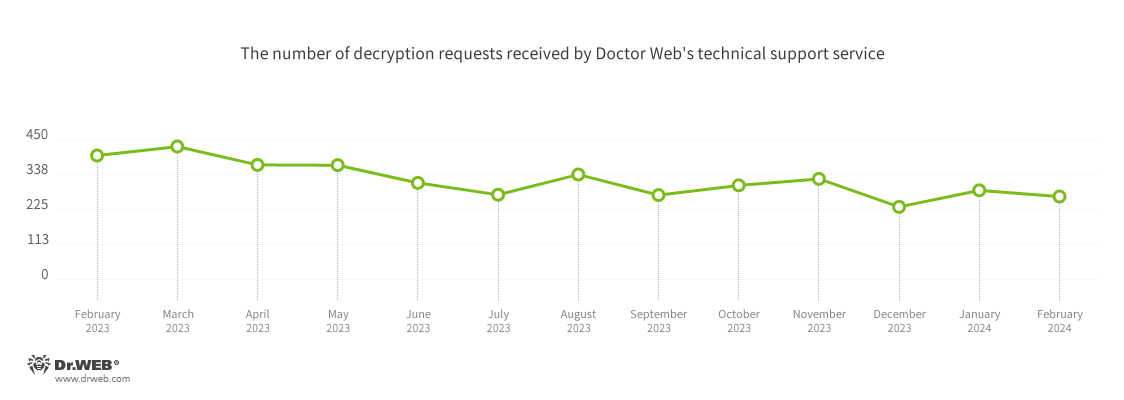
The number of user requests to decrypt files affected by encoder trojans decreased by 7.02%, compared to the previous month. The most common malware behind the ransom attacks were Trojan.Encoder.3953 (18.27% of incidents), Trojan.Encoder.37369 (9.14% of incidents), and Trojan.Encoder.26996 (8.12% of incidents).
In the mobile threats department, Android.HiddenAds adware trojans were again the most commonly detected malware, with highly increased activity.
Principal trends in February
- An increase in the total number of threats detected
- The predominance of malicious scripts and phishing documents in malicious email traffic
- A decrease in the number of user requests to decrypt files affected by encoder trojans
- An increase in the number of Android.HiddenAds adware trojans on protected devices
According to Doctor Web’s statistics service
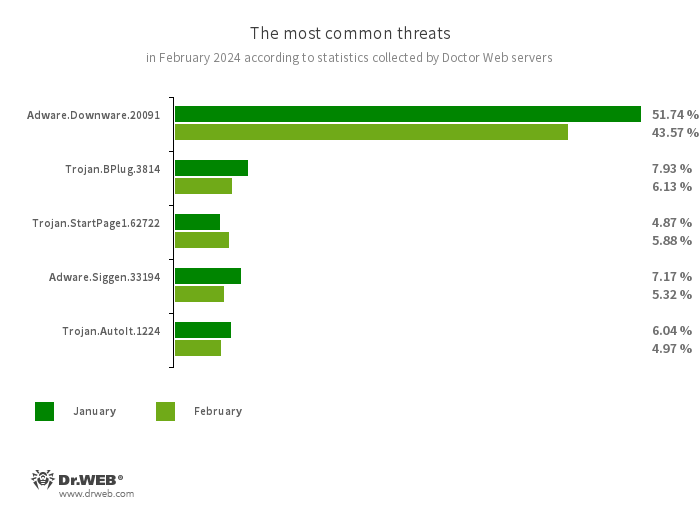
The most common threats in February:
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- Trojan.BPlug.3814
- The detection name for a malicious component of the WinSafe browser extension. This component is a JavaScript file that displays intrusive ads in browsers.
- Trojan.StartPage1.62722
- A malicious program that can modify the home page in the browser settings.
- Adware.Siggen.33194
- The detection name for a freeware browser that was created with an Electron framework and has a built-in adware component. This browser is distributed via various websites and loaded onto users’ computers when they try downloading torrent files.
- Trojan.AutoIt.1224
- The detection name for a packed version of the Trojan.AutoIt.289 malicious app, written in the AutoIt scripting language. This trojan is distributed as part of a group of several malicious applications, including a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs various malicious actions that make it difficult for the main payload to be detected.
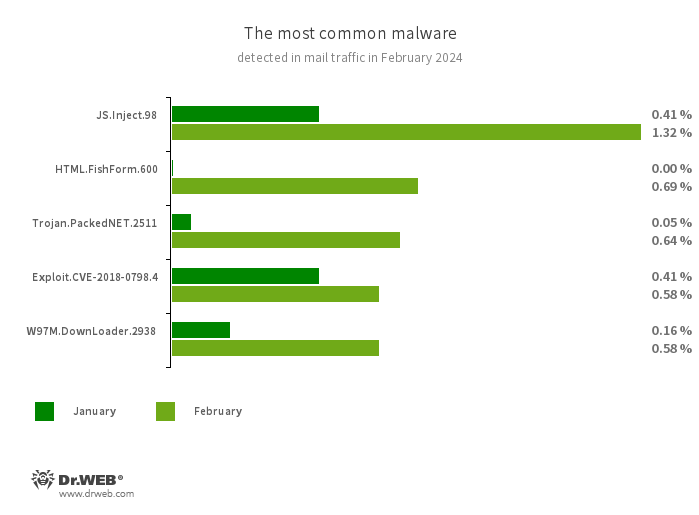
Statistics for malware discovered in email traffic
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- HTML.FishForm.365
- A webpage spread via phishing emails. It is a bogus authorization page that mimics well-known websites. The credentials a user enters on the page are sent to the attacker.
- Trojan.PackedNET.2511
- Malware written in VB.NET and protected with a software packer.
- Exploit.CVE-2018-0798.4
- An exploit designed to take advantage of Microsoft Office software vulnerabilities and allow an attacker to run arbitrary code.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
Encryption ransomware
In February 2024, the number of requests made to decrypt files affected by encoder trojans decreased by 7.02%, compared to January.
The most common encoders of February:
- Trojan.Encoder.3953 — 18.27%
- Trojan.Encoder.35534 — 9.14%
- Trojan.Encoder.26996 — 8.12%
- Trojan.Encoder.29750 — 0.51%
- Trojan.Encoder.37400 — 0.51%
Dangerous websites
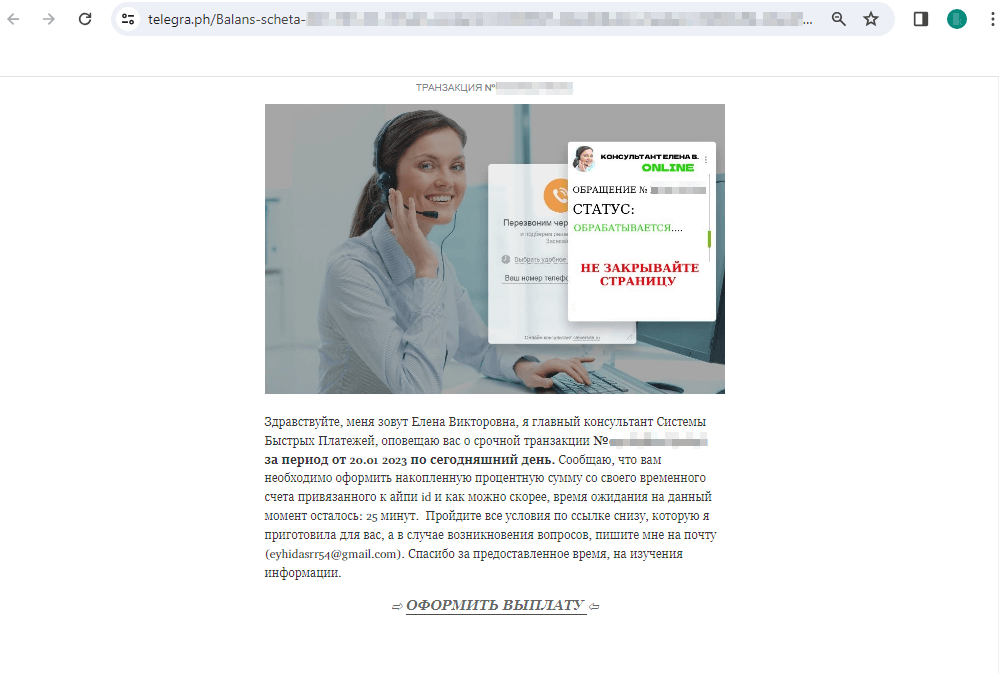
In February 2024, Doctor Web’s Internet analysts continued to identify unwanted websites of various subject matter. For example, sites informing potential victims that some money transfers were allegedly waiting for them were popular with cybercriminals. To “receive” these funds, users must pay a bank transfer “commission”. Links to such websites are distributed in various ways, including via posts on the Telegraph blog platform.
Below is an example of one such publication. Potential victims are asked to “collect” the reward that they supposedly earned after participating in an online store survey:
Upon clicking on the “GET A PAYMENT” (“ОФОРМИТЬ ВЫПЛАТУ”) link, the user is redirected to a scam website of some non-existent “International Payment and Transfer System” (“Международная Система Платежей и Переводов”), where they are supposedly able to receive the promised funds:
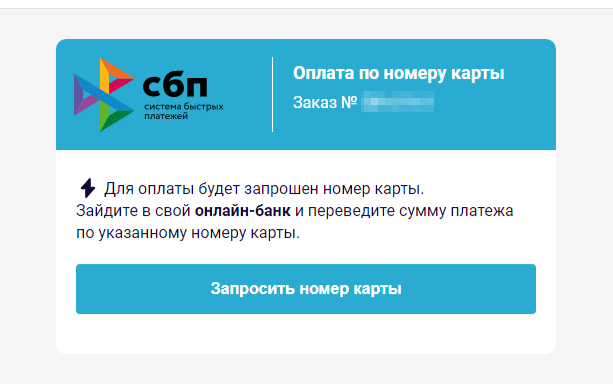
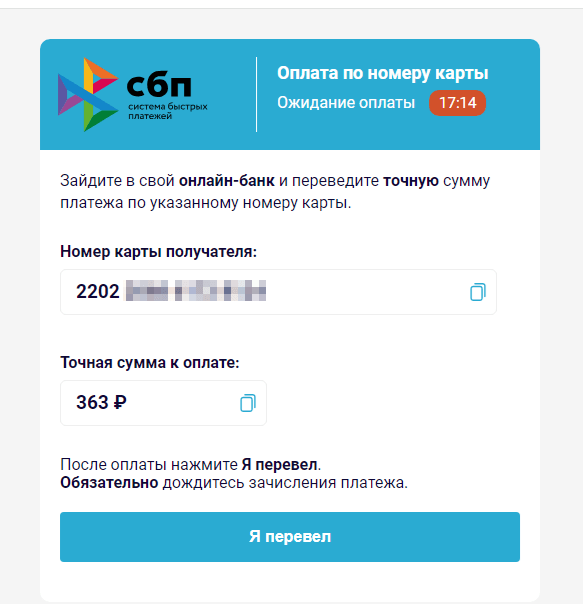
To “receive” the money, the user must first provide personal information, such as their name and email address. Then, they need to pay a “commission” via the legitimate Faster Payments System (“Система быстрых платежей”, “СБП”, or “SBP”) so that the reward, which, in fact, does not exist, can be “transferred” to them. At the same time, scammers ask the victim to pay the “commission” via an online bank, using the specified bank card number; all that while, the Faster Payments System allows transfers only by mobile phone number. In this case, the fraudsters may deliberately be speculating on a money-transfer method that is gaining popularity in Russia, counting on the low financial literacy of users. If the victim agrees to pay the “commission”, they will transfer their own money directly to the scammers’ bank card. However, it is possible that in an attempt to steal users’ money, malicious actors will actually begin using the Faster Payments System in the future.
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web for Android, in February, Android.HiddenAds ad-displaying trojans were most commonly detected once again. Their activity increased by 73.26%, compared to January. At the same time, adware trojans from another family, Android.MobiDash, attacked users 58.85% less often.
The number of Android.Spy spyware trojan detections decreased by 27.33%, while banking trojan detections decreased by 18.77%. Meanwhile, Android.Locker ransomware trojans were detected 29.85% less often.
The following February events involving mobile malware are the most noteworthy:
- A significant increase in the activity of Android.HiddenAds ad-displaying trojans,
- A decrease in the number of banking trojan and spyware trojan attacks,
- An increase in the number of ransomware trojan attacks.
To find out more about the security-threat landscape for mobile devices in February, read our special overview.